Clair镜像扫描社区版持续探索
Clair地址
https://github.com/quay/clair/blob/master/Documentation/running-clair.md
claricli地址
https://github.com/joelee2012/claircli
-
安装配置
mkdir $PWD/clair_config curl -L https://raw.githubusercontent.com/coreos/clair/master/config.yaml.sample -o $PWD/clair_config/config.yaml docker run -d -e POSTGRES_PASSWORD="" -p 5432:5432 postgres docker run --net=host -d -p 6060-6061:6060-6061 -v $PWD/clair_config:/config quay.io/coreos/clair:latest -config=/config/config.yaml
启动后clair会下载漏洞库然后放到postgres数据库中。需要等待一段时间,fetching结束
[root@mirror ~]# docker logs -f 0a4aa93eb96b {"Event":"running database migrations","Level":"info","Location":"pgsql.go:216","Time":"2020-01-27 07:48:23.835691"} {"Event":"database migration ran successfully","Level":"info","Location":"pgsql.go:223","Time":"2020-01-27 07:48:23.840739"} {"Event":"notifier service is disabled","Level":"info","Location":"notifier.go:77","Time":"2020-01-27 07:48:23.840913"} {"Event":"starting main API","Level":"info","Location":"api.go:52","Time":"2020-01-27 07:48:23.840946","port":6060} {"Event":"starting health API","Level":"info","Location":"api.go:85","Time":"2020-01-27 07:48:23.841310","port":6061} {"Event":"updater service started","Level":"info","Location":"updater.go:83","Time":"2020-01-27 07:48:23.841383","lock identifier":"07fb180b-49f7-4f40-80ca-013b6587807a"} {"Event":"Handled HTTP request","Level":"info","Location":"router.go:57","Time":"2020-01-27 07:50:09.745914","elapsed time":361665425,"method":"DELETE","remote addr":"192.168.56.108:56760","request uri":"/v1/layers/sha256:bc9ab73e5b14b9fbd3687a4d8c1f1360533d6ee9ffc3f5ecc6630794b40257b7","status":"404"} {"Event":"failed to write response","Level":"warning","Location":"routes.go:94","Time":"2020-01-27 07:54:46.354907","error":"http: Handler timeout"} {"Event":"Handled HTTP request","Level":"info","Location":"router.go:57","Time":"2020-01-27 07:54:46.354942","elapsed time":276604498860,"method":"POST","remote addr":"192.168.56.108:56762","request uri":"/v1/layers","status":"201"} {"Event":"updating vulnerabilities","Level":"info","Location":"updater.go:192","Time":"2020-01-27 07:55:54.897757"} {"Event":"fetching vulnerability updates","Level":"info","Location":"updater.go:239","Time":"2020-01-27 07:55:54.897791"} {"Event":"Start fetching vulnerabilities","Level":"info","Location":"ubuntu.go:85","Time":"2020-01-27 07:55:54.897816","package":"Ubuntu"} {"Event":"Start fetching vulnerabilities","Level":"info","Location":"alpine.go:52","Time":"2020-01-27 07:55:54.921575","package":"Alpine"} {"Event":"Start fetching vulnerabilities","Level":"info","Location":"debian.go:63","Time":"2020-01-27 07:55:54.943595","package":"Debian"} {"Event":"Start fetching vulnerabilities","Level":"info","Location":"oracle.go:119","Time":"2020-01-27 07:55:54.944000","package":"Oracle Linux"} {"Event":"Start fetching vulnerabilities","Level":"info","Location":"rhel.go:92","Time":"2020-01-27 07:55:54.944082","package":"RHEL"} {"Event":"finished fetching","Level":"info","Location":"updater.go:253","Time":"2020-01-27 07:56:25.455733","updater name":"alpine"} {"Event":"finished fetching","Level":"info","Location":"updater.go:253","Time":"2020-01-27 07:57:55.854087","updater name":"rhel"} {"Event":"could not unmarshal Debian's JSON","Level":"error","Location":"debian.go:115","Time":"2020-01-27 08:01:06.093947","error":"read tcp 10.0.3.15:34708-\u003e23.111.9.35:443: read: connection reset by peer"} {"Event":"an error occured when fetching update","Level":"error","Location":"updater.go:246","Time":"2020-01-27 08:01:06.094057","error":"updater/fetchers: could not parse","updater name":"debian"}
-
安装claircli
curl "https://bootstrap.pypa.io/get-pip.py" -o "get-pip.py" python get-pip.py pip install claircli
-
扫描
[root@mirror images]# claircli -c http://mirror.redhat.ren:6060 docker.io/debian:9.5 2020-01-27 15:28:12,685|INFO|*****************************1****************************** 2020-01-27 15:28:12,686|INFO|Analyzing <Image: docker.io/debian:9.5> 2020-01-27 15:28:17,951|INFO|Push layer [1/1]: sha256:bc9ab73e5b14b9fbd3687a4d8c1f1360533d6ee9ffc3f5ecc6630794b40257b7 2020-01-27 15:28:47,134|INFO|Fetch vulnerabilities for <Image: docker.io/debian:9.5> 2020-01-27 15:28:47,207|INFO|Defcon1 : 0 2020-01-27 15:28:47,207|INFO|Critical : 0 2020-01-27 15:28:47,208|INFO|High : 0 2020-01-27 15:28:47,208|INFO|Medium : 0 2020-01-27 15:28:47,208|WARNING|Low : 26 2020-01-27 15:28:47,208|WARNING|Negligible : 42 2020-01-27 15:28:47,208|WARNING|Unknown : 30 2020-01-27 15:28:47,208|INFO|Generate html report for docker.io/debian:9.5 2020-01-27 15:28:47,265|INFO|Location: /root/images/clair-docker.io_debian_9.5.html 2020-01-27 15:28:47,265|INFO|============================================================ 2020-01-27 15:28:47,265|INFO| CLAIR ANALYSIS REPORTS: (1) IN TOTAL 2020-01-27 15:28:47,265|INFO|============================================================ 2020-01-27 15:28:47,266|ERROR|IMAGES WITH DETECTED VULNERABILITIES (1) 2020-01-27 15:28:47,266|ERROR|docker.io/debian:9.5
会在当前目录生成一个html文件,打开文件是一个报告。

-
离线扫描
在线环境下把数据都下载好,然后备份和恢复postgres数据库(在离线环境的postgres中)
pg_dump -h localhost -U postgres postgres > postgres.data
#基于docker cp 把data文件拷贝出来,然后拷贝到目的的容器中
#恢复数据
psql -h localhost -U postgres -d postgres < /postgres.data
root@db9486caa384:/# psql -h localhost -U postgres -d postgres < /postgres.data SET SET SET SET SET set_config ------------ (1 row) SET SET SET SET CREATE TYPE ALTER TYPE CREATE TYPE ALTER TYPE SET SET CREATE TABLE ALTER TABLE ......
启动clair如常
docker run --net=host -d -p 6060-6061:6060-6061 -v $PWD/clair_config:/config quay.io/coreos/clair:latest -config=/config/config.yaml
然后扫描本地镜像
[root@mirror ~]# claircli -c http://mirror.redhat.ren:6060 -l 192.168.56.108 mirror.redhat.ren/admin/tomcat:latest 2020-01-28 21:04:37,389|INFO|Starting local http server 2020-01-28 21:04:37,424|INFO|Local http server serving at port: 14314 2020-01-28 21:04:37,426|INFO|*****************************1****************************** 2020-01-28 21:04:37,426|INFO|Analyzing <Image: mirror.redhat.ren/admin/tomcat:latest> 2020-01-28 21:05:09,241|INFO|Push layer [1/11]: 8693c46878e0d0517532d9b1ea31ffbc23ba701c43ebf82d9ecd138cf898f487 2020-01-28 21:05:09,743|INFO|Push layer [2/11]: 9d69425a0fe81b1ce88b04e3ca63679c8f1646fb3a13f55787e9c88c115c07ae 2020-01-28 21:05:09,846|INFO|Push layer [3/11]: b4a98f921e2418946eaab03f3812ca01f5fbd52b69a31952cf0922a5160f805b 2020-01-28 21:05:09,897|INFO|Push layer [4/11]: fa5f03c842d20196817bc410ad55ba16c8a110167c68b12566e4d573d7dc5a1a 2020-01-28 21:05:09,923|INFO|Push layer [5/11]: 16a4d2a6a17d1ae4dea154f4b5e3963cc44d692d557b870807234183ee001750 2020-01-28 21:05:12,215|INFO|Push layer [6/11]: b2c0ffaebb919d289598e78efafe118d4bb8127ffac833d5e27ca34375f4689d 2020-01-28 21:05:12,260|INFO|Push layer [7/11]: 4ef4bec3c7a09988cc2dc25fc8e745b81e1449794e35287dcd0d64ce8575b3b2 2020-01-28 21:05:12,292|INFO|Push layer [8/11]: c444b941df6cf078379bbc2c81a1ba58a1adb941a7fe3a4767fa08b8ff412903 2020-01-28 21:05:12,329|INFO|Push layer [9/11]: 45e5acc6a43952d622274e904ae4596d7af3218c5ba196c986b66809096a8869 2020-01-28 21:05:12,362|INFO|Push layer [10/11]: 0d31824d0cfc60d1fe9ee262c9dbafd192dc153c1279faba1b9a04c36620f550 2020-01-28 21:05:12,866|INFO|Push layer [11/11]: 33b14cc3bdef0ae89a9eecd7d9cfd7e1ba294a0206c36dbd311b2efc74aa0072 2020-01-28 21:05:12,886|INFO|Fetch vulnerabilities for <Image: mirror.redhat.ren/admin/tomcat:latest> 2020-01-28 21:05:12,912|INFO|Defcon1 : 0 2020-01-28 21:05:12,912|INFO|Critical : 0 2020-01-28 21:05:12,912|INFO|High : 0 2020-01-28 21:05:12,912|INFO|Medium : 0 2020-01-28 21:05:12,912|WARNING|Low : 30 2020-01-28 21:05:12,912|WARNING|Negligible : 65 2020-01-28 21:05:12,912|WARNING|Unknown : 90 2020-01-28 21:05:12,913|INFO|Generate html report for mirror.redhat.ren/admin/tomcat:latest 2020-01-28 21:05:13,127|INFO|Location: /root/clair-mirror.redhat.ren_admin_tomcat_latest.html 2020-01-28 21:05:13,158|INFO|============================================================ 2020-01-28 21:05:13,158|INFO| CLAIR ANALYSIS REPORTS: (1) IN TOTAL 2020-01-28 21:05:13,158|INFO|============================================================ 2020-01-28 21:05:13,158|ERROR|IMAGES WITH DETECTED VULNERABILITIES (1) 2020-01-28 21:05:13,158|ERROR|mirror.redhat.ren/admin/tomcat:latest
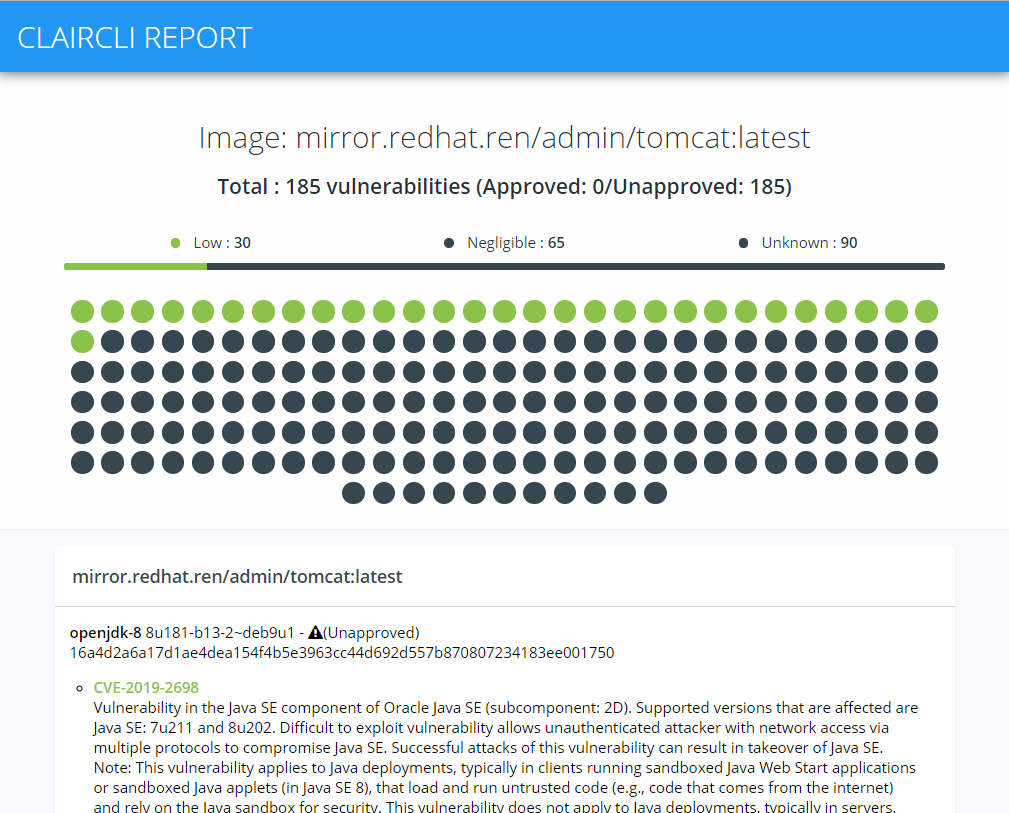
扫描私有镜像库暂时还有点问题,需要继续研究。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号