SDRAM反汇编文件
本文主要介绍一个简单的使用SDRAM器件时,地址之间的映射关系以及启动代码的关系
首先,看一个汇编文件,是启动代码。
@*************************************************************************
@ File:head.S
@ 功能:设置SDRAM,将程序复制到SDRAM,然后跳到SDRAM继续执行
@*************************************************************************
.equ MEM_CTL_BASE, 0x48000000
.equ SDRAM_BASE, 0x30000000
.text
.global _start
_start:
bl disable_watch_dog @ 关闭WATCHDOG,否则CPU会不断重启
bl memsetup @ 设置存储控制器
bl copy_steppingstone_to_sdram @ 复制代码到SDRAM中
ldr pc, =on_sdram @ 跳到SDRAM中继续执行
on_sdram:
ldr sp, =0x34000000 @ 设置堆栈
bl main
halt_loop:
b halt_loop
disable_watch_dog:
@ 往WATCHDOG寄存器写0即可
mov r1, #0x53000000
mov r2, #0x0
str r2, [r1]
mov pc, lr @ 返回
copy_steppingstone_to_sdram:
@ 将Steppingstone的4K数据全部复制到SDRAM中去
@ Steppingstone起始地址为0x00000000,SDRAM中起始地址为0x30000000
mov r1, #0
ldr r2, =SDRAM_BASE
mov r3, #4*1024
1:
ldr r4, [r1],#4 @ 从Steppingstone读取4字节的数据,并让源地址加4
str r4, [r2],#4 @ 将此4字节的数据复制到SDRAM中,并让目地地址加4
cmp r1, r3 @ 判断是否完成:源地址等于Steppingstone的未地址?
bne 1b @ 若没有复制完,继续
mov pc, lr @ 返回
memsetup:
@ 设置存储控制器以便使用SDRAM等外设
mov r1, #MEM_CTL_BASE @ 存储控制器的13个寄存器的开始地址
adrl r2, mem_cfg_val @ 这13个值的起始存储地址
add r3, r1, #52 @ 13*4 = 54
1:
ldr r4, [r2], #4 @ 读取设置值,并让r2加4
str r4, [r1], #4 @ 将此值写入寄存器,并让r1加4
cmp r1, r3 @ 判断是否设置完所有13个寄存器
bne 1b @ 若没有写成,继续
mov pc, lr @ 返回
.align 4
mem_cfg_val:
@ 存储控制器13个寄存器的设置值
.long 0x22011110 @ BWSCON
.long 0x00000700 @ BANKCON0
.long 0x00000700 @ BANKCON1
.long 0x00000700 @ BANKCON2
.long 0x00000700 @ BANKCON3
.long 0x00000700 @ BANKCON4
.long 0x00000700 @ BANKCON5
.long 0x00018005 @ BANKCON6
.long 0x00018005 @ BANKCON7
.long 0x008C07A3 @ REFRESH
.long 0x000000B1 @ BANKSIZE
.long 0x00000030 @ MRSRB6
.long 0x00000030 @ MRSRB7
以及一个Makefile
sdram.bin : head.S leds.c
arm-linux-gcc -c -o head.o head.S
arm-linux-gcc -c -o leds.o leds.c
arm-linux-ld -Ttext 0x30000000 head.o leds.o -o sdram_elf
arm-linux-objcopy -O binary -S sdram_elf sdram.bin
arm-linux-objdump -D -m arm sdram_elf > sdram.dis
clean:
rm -f sdram.dis sdram.bin sdram_elf *.o
还有它的反汇编文件
sdram_elf: file format elf32-littlearm
Disassembly of section .text:
30000000 <_start>:
30000000: eb000005 bl 3000001c <disable_watch_dog>
30000004: eb000010 bl 3000004c <memsetup>
30000008: eb000007 bl 3000002c <copy_steppingstone_to_sdram>
3000000c: e59ff090 ldr pc, [pc, #144] ; 300000a4 <mem_cfg_val+0x34>
30000010 <on_sdram>:
30000010: e3a0d30d mov sp, #872415232 ; 0x34000000
30000014: eb000033 bl 300000e8 <main>
30000018 <halt_loop>:
30000018: eafffffe b 30000018 <halt_loop>
3000001c <disable_watch_dog>:
3000001c: e3a01453 mov r1, #1392508928 ; 0x53000000
30000020: e3a02000 mov r2, #0
30000024: e5812000 str r2, [r1]
30000028: e1a0f00e mov pc, lr
3000002c <copy_steppingstone_to_sdram>:
3000002c: e3a01000 mov r1, #0
30000030: e3a02203 mov r2, #805306368 ; 0x30000000
30000034: e3a03a01 mov r3, #4096 ; 0x1000
30000038: e4914004 ldr r4, [r1], #4
3000003c: e4824004 str r4, [r2], #4
30000040: e1510003 cmp r1, r3
30000044: 1afffffb bne 30000038 <copy_steppingstone_to_sdram+0xc>
30000048: e1a0f00e mov pc, lr
3000004c <memsetup>:
3000004c: e3a01312 mov r1, #1207959552 ; 0x48000000
30000050: e28f2018 add r2, pc, #24
30000054: e1a00000 nop ; (mov r0, r0)
30000058: e2813034 add r3, r1, #52 ; 0x34
3000005c: e4924004 ldr r4, [r2], #4
30000060: e4814004 str r4, [r1], #4
30000064: e1510003 cmp r1, r3
30000068: 1afffffb bne 3000005c <memsetup+0x10>
3000006c: e1a0f00e mov pc, lr
30000070 <mem_cfg_val>:
30000070: 22011110 andcs r1, r1, #4
30000074: 00000700 andeq r0, r0, r0, lsl #14
30000078: 00000700 andeq r0, r0, r0, lsl #14
3000007c: 00000700 andeq r0, r0, r0, lsl #14
30000080: 00000700 andeq r0, r0, r0, lsl #14
30000084: 00000700 andeq r0, r0, r0, lsl #14
30000088: 00000700 andeq r0, r0, r0, lsl #14
3000008c: 00018005 andeq r8, r1, r5
30000090: 00018005 andeq r8, r1, r5
30000094: 008c07a3 addeq r0, ip, r3, lsr #15
30000098: 000000b1 strheq r0, [r0], -r1
3000009c: 00000030 andeq r0, r0, r0, lsr r0
300000a0: 00000030 andeq r0, r0, r0, lsr r0
300000a4: 30000010 andcc r0, r0, r0, lsl r0
300000a8: e1a00000 nop ; (mov r0, r0)
300000ac: e1a00000 nop ; (mov r0, r0)
300000b0 <wait>:
300000b0: e52db004 push {fp} ; (str fp, [sp, #-4]!)
300000b4: e28db000 add fp, sp, #0
300000b8: e24dd00c sub sp, sp, #12
300000bc: e50b0008 str r0, [fp, #-8]
300000c0: ea000002 b 300000d0 <wait+0x20>
300000c4: e51b3008 ldr r3, [fp, #-8]
300000c8: e2433001 sub r3, r3, #1
300000cc: e50b3008 str r3, [fp, #-8]
300000d0: e51b3008 ldr r3, [fp, #-8]
300000d4: e3530000 cmp r3, #0
300000d8: 1afffff9 bne 300000c4 <wait+0x14>
300000dc: e28bd000 add sp, fp, #0
300000e0: e8bd0800 pop {fp}
300000e4: e12fff1e bx lr
300000e8 <main>:
300000e8: e92d4800 push {fp, lr}
300000ec: e28db004 add fp, sp, #4
300000f0: e24dd008 sub sp, sp, #8
300000f4: e3a03000 mov r3, #0
300000f8: e50b3008 str r3, [fp, #-8]
300000fc: e59f304c ldr r3, [pc, #76] ; 30000150 <main+0x68>
30000100: e3a02c15 mov r2, #5376 ; 0x1500
30000104: e5832000 str r2, [r3]
30000108: ea000000 b 30000110 <main+0x28>
3000010c: e1a00000 nop ; (mov r0, r0)
30000110: e59f003c ldr r0, [pc, #60] ; 30000154 <main+0x6c>
30000114: ebffffe5 bl 300000b0 <wait>
30000118: e59f3038 ldr r3, [pc, #56] ; 30000158 <main+0x70>
3000011c: e51b2008 ldr r2, [fp, #-8]
30000120: e1a02202 lsl r2, r2, #4
30000124: e1e02002 mvn r2, r2
30000128: e5832000 str r2, [r3]
3000012c: e51b3008 ldr r3, [fp, #-8]
30000130: e2833001 add r3, r3, #1
30000134: e50b3008 str r3, [fp, #-8]
30000138: e51b3008 ldr r3, [fp, #-8]
3000013c: e3530008 cmp r3, #8
30000140: 1afffff1 bne 3000010c <main+0x24>
30000144: e3a03000 mov r3, #0
30000148: e50b3008 str r3, [fp, #-8]
3000014c: eaffffef b 30000110 <main+0x28>
30000150: 56000050 undefined instruction 0x56000050
30000154: 00007530 andeq r7, r0, r0, lsr r5
30000158: 56000054 undefined instruction 0x56000054
Disassembly of section .ARM.attributes:
00000000 <.ARM.attributes>:
0: 00002541 andeq r2, r0, r1, asr #10
4: 61656100 cmnvs r5, r0, lsl #2
8: 01006962 tsteq r0, r2, ror #18
c: 0000001b andeq r0, r0, fp, lsl r0
10: 00543405 subseq r3, r4, r5, lsl #8
14: 01080206 tsteq r8, r6, lsl #4
18: 04120109 ldreq r0, [r2], #-265 ; 0x109
1c: 01150114 tsteq r5, r4, lsl r1
20: 01180317 tsteq r8, r7, lsl r3
24: Address 0x00000024 is out of bounds.
Disassembly of section .comment:
00000000 <.comment>:
0: 3a434347 bcc 10d0d24 <SDRAM_BASE-0x2ef2f2dc>
4: 74632820 strbtvc r2, [r3], #-2080 ; 0x820
8: 312d676e teqcc sp, lr, ror #14
c: 312e362e teqcc lr, lr, lsr #12
10: 2e342029 cdpcs 0, 3, cr2, cr4, cr9, {1}
14: 00332e34 eorseq r2, r3, r4, lsr lr
反汇编文件中,最左边的数字,表示的是应该位于哪个地址。中间是对应指令的机器码。右边则是汇编指令。
1 为什么反汇编文件中“应该运行”地址都是3打头的呢?
因为这是与链接脚本也就是makefile中的 -Ttext有关系
2 整个程序运行的顺序应该是这样的: 首先CPU自动从外接的nandflash中的前4K数据复制到SRAM中(假设从nandflash启动)。然后CPU跳转到SRAM中0地址运行。这一段代码完成的工作包括了关看门狗、时钟、初始化SDRAM、拷贝代码从SRAM到SDRAM(实际上很多时候是从NandFlash拷贝到SDRAM),最后跳转到SDRAM中执行。
3 什么时候跳到SDRAM中执行,怎么确定跳转的地址。
汇编代码中是如下图所示

而对应的反汇编代码是

其中的“ldr pc, [pc, #144]”
这里是将当前的PC值加144(十进制)。
而此时PC的值是多少呢,当然是0x00000014 + 8
(1) 为什么是0x00000014不是0x30000014呢,因为此时还在SRAM中运行而非SDRAM,虽然链接地址指定该条语句应该位于0x30000014但是真正运行的地址并不是由此链接而确定。
(2) 为什么 是加8
这里可以参考ARM指令系统的介绍,正常模式下是+8
所以这条语句是将0x14+8+144=0xA4,而0x000000A4的内容如下图
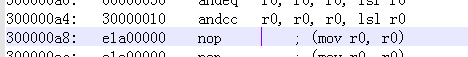
可以看到是30000010,换而言之,此时PC值 等于了0X3000010位于SDRAM中,那此地址上的内容是什么呢,别忘了,我们刚把些代码复制到了SDRAM中。此时的代码如上上图所示。
就此,恢复正常工作,此时程序所谓的“应该运行地址”才等于了“实际运行地址”
关于链接地址问题,可参见另外一篇相关的博客。


