Kong安装教程(v1.0.2)
使用的软件
- Unbuntu 虚拟机(有自己的服务器更好)
- PostgreSQL
- kong
- kong-dashboard
- docker
- spring boot
安装 PostgreSQL
kong 需要使用到数据库,目前支持PostgreSQL和Cassandran ,我选择大象数据库,安装过程省略,可以参考这篇文章。
Ubuntu PostgreSQL安装和配置
安装完后建一个kong的用户、密码为kong、建一个kong 数据库:
sudo -u postgres psql 进入,提示符变成: postgres=#
postgres=# create user kong with password 'kong'; CREATE ROLE postgres=# CREATE DATABASE kong OWNER kong; CREATE DATABASE postgres=#
至此,PostgreSQL已经安装和配置好了。
安装kong
下载kong的源文件,下载地址:https://getkong.org/install/ubuntu/
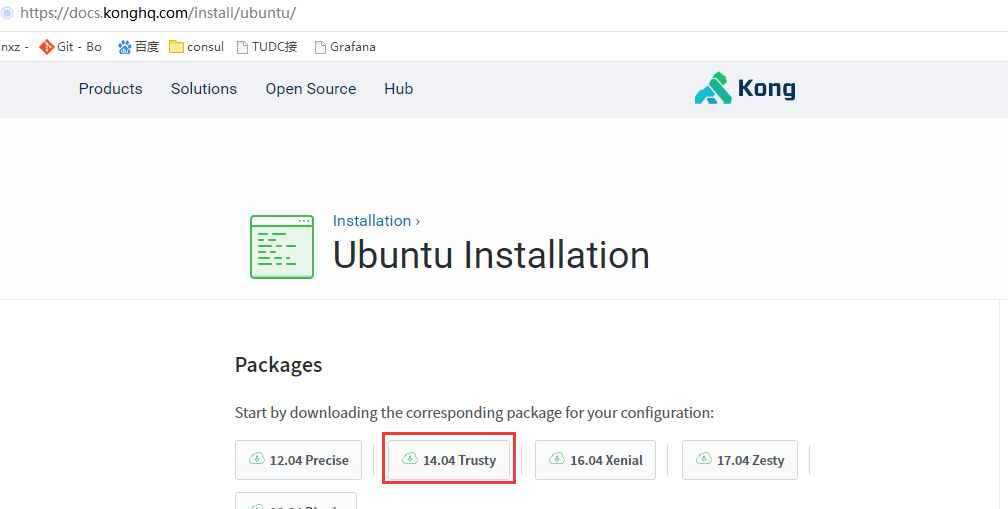
下载完成之后会有这样一个文件kong-community-edition-0.11.0.*.deb,cd到这个文件的目录:
$ sudo apt-get update $ sudo apt-get install openssl libpcre3 procps perl $ sudo dpkg -i kong-community-edition-1.0.2.*.deb
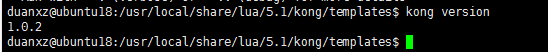
查看kong的版本:
kong version
配置kong
配置文档在这里:
https://getkong.org/docs/0.9.x/configuration/
复制配置文件:
$ cp /etc/kong/kong.conf.default /etc/kong/kong.conf
配置文件(Kong将使用默认设置进行操作。启动时,Kong会查找可能包含配置文件的几个默认位置):
cat /etc/kong/kong.conf
cat /etc/kong.conf
打开配置文件,里面可以修改很多配置,修改数据库连接,用户名、密码
pg_host = 127.0.0.1 # The PostgreSQL host to connect to. pg_port = 5432 # The port to connect to. pg_user = kong # The username to authenticate if required. pg_password = kong # The password to authenticate if required. pg_database = kong
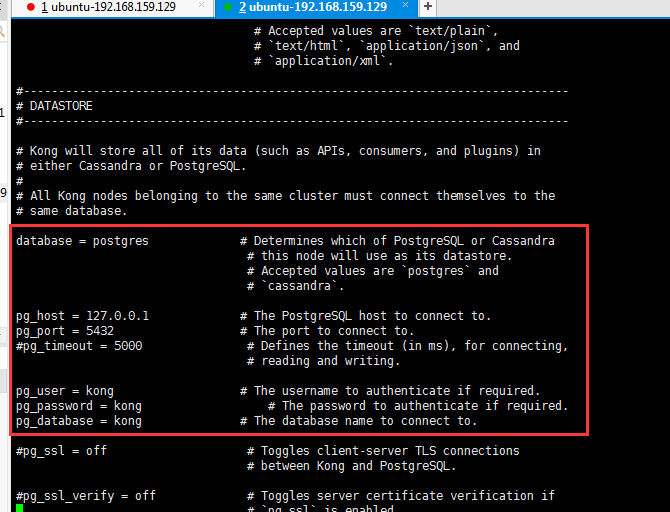
数据库配置(上面已经有了)
kong连数据库,需要我们在pg上建立密码为kong的kong用户,数据库名也为kong
su - postgres//进入数据库 -bash-4.2$ psql postgres=# CREATE USER kong WITH PASSWORD 'kong'; CREATE DATABASE kong OWNER kong;//建立数据库以及用户
修改kong配置
进入/usr/local/share/lua/5.1/kong/templates目录,修改kong_defaults.lua里的pg_password=kong,保存
初始化数据库,执行以下整合命令:
$ kong migrations up -c /etc/kong/kong.conf.default
出错:
Error: /usr/local/share/lua/5.1/kong/cmd/start.lua:28: [postgres error] could not retrieve current migrations: [postgres error] 致命错误: 用户 "kong" Ident 认证失败
解决方法:
vi /var/lib/pgsql/9.6/data/pg_hba.conf
修改
把这个配置文件中的认证 METHOD的ident修改为trust,可以实现用账户和密码来访问数据库,
即解决psql: 致命错误: 用户 "postgres" Ident 认证失败 这个问题)
第五步:重启postgresql服务器使设置生效
#service postgresql-9.6 restart
再重试上面的migrations指令。
好像高版本是使用:
kong migrations bootstrap
执行好后,数据库会生成很多表,这些是默认但kong数据表,后续可以自定义插件,重新migrations,会生成自定义表
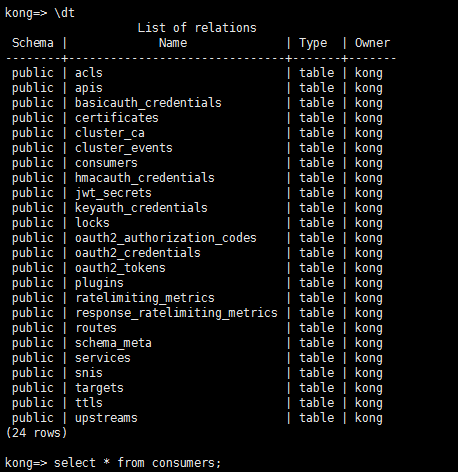
启动kong :
kong start -c /etc/kong/kong.conf --vv
默认情况下,KONG监听的端口为:
· 8000:此端口是KONG用来监听来自客户端传入的HTTP请求,并将此请求转发到上有服务器;(kong根据配置的规则转发到真实的后台服务地址。)
· 8443:此端口是KONG用来监听来自客户端传入的HTTPS请求的。它跟8000端口的功能类似,转发HTTPS请求的。可以通过修改配置文件来禁止它;
· 8001:Admin API,通过此端口,管理者可以对KONG的监听服务进行配置,插件设置、API的增删改查、以及负载均衡等一系列的配置都是通过8001端口进行管理;
· 8444:通过此端口,管理者可以对HTTPS请求进行监控;
最后、浏览器访问IP:8000,如果出现{"message":"no API found with those values"}
注意点:如果有防火墙的话,最好先关掉防火墙。
kong的日志
[root@localhost logs]# pwd /usr/local/kong/logs [root@localhost logs]# ll 总用量 184 -rw-r--r--. 1 root root 28358 2月 22 18:55 access.log -rw-r--r--. 1 root root 63986 2月 22 18:32 admin_access.log -rw-r--r--. 1 root root 91335 2月 22 18:09 error.log [root@localhost logs]# tail -50f error.log
示例:
打开浏览器访问:localhost:8001,浏览器显示了一大串关于kong的json字符串,则启动成功。
curl -i http://localhost:8001/
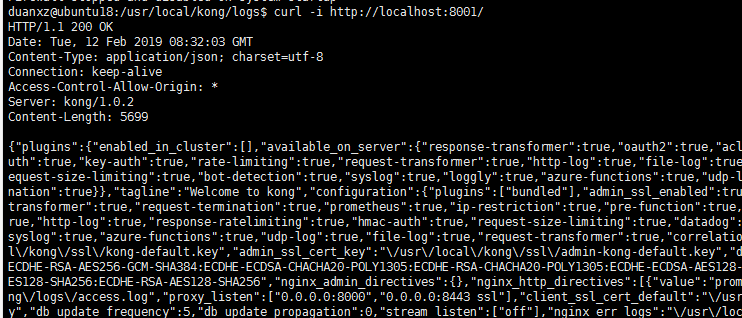
管理端口用rest api对api进行操作,文档地址:https://getkong.org/docs/0.8.x/admin-api
接口接入kong测试
下面的所有admin api操作,如果成功会写入postgreSQL中,下面是按照官方的demo操作的,所有操作都是成功的。数据落地到数据库的,查询见《Ubuntu PostgreSQL安装和配置》的第七章节。
示例1:服务转发
1. Add your Service using the Admin API
Issue the following cURL request to add your first Service (pointing to the baidu) to Kong:
curl -i -X POST \ --url http://localhost:8001/services/ \ --data 'name=baidu-service' \ --data 'url=http://www.baidu.com'
You should receive a response similar to:
HTTP/1.1 201 Created Date: Wed, 13 Feb 2019 03:48:38 GMT Content-Type: application/json; charset=utf-8 Connection: keep-alive Access-Control-Allow-Origin: * Server: kong/1.0.2 Content-Length: 258 { "host": "www.baidu.com", "created_at": 1550029718, "connect_timeout": 60000, "id": "be1ea866-c4b4-46ac-9c92-ff821fb317ab", "protocol": "http", "name": "baidu-service", "read_timeout": 60000, "port": 80, "path": null, "updated_at": 1550029718, "retries": 5, "write_timeout": 60000 }
2. Add a Route for the Service
curl -i -X POST \ --url http://localhost:8001/services/baidu-service/routes \ --data 'hosts[]=baidu.com'
The answer should be similar to:
HTTP/1.1 201 Created Date: Wed, 13 Feb 2019 03:51:19 GMT Content-Type: application/json; charset=utf-8 Connection: keep-alive Access-Control-Allow-Origin: * Server: kong/1.0.2 Content-Length: 346 { "created_at": 1550029879, "methods": null, "id": "d813af89-13fe-4d94-945f-d5bbf4c56a28", "service": { "id": "be1ea866-c4b4-46ac-9c92-ff821fb317ab" }, "name": null, "hosts": ["baidu.com"], "updated_at": 1550029879, "preserve_host": false, "regex_priority": 0, "paths": null, "sources": null, "destinations": null, "snis": null, "protocols": ["http", "https"], "strip_path": true }
Kong is now aware of your Service and ready to proxy requests.
3. Forward your requests through Kong
Issue the following cURL request to verify that Kong is properly forwarding requests to your Service. Note that by default Kong handles proxy requests on port :8000:
curl -i -X GET \ --url http://localhost:8000/ \ --header 'Host: baidu.com'
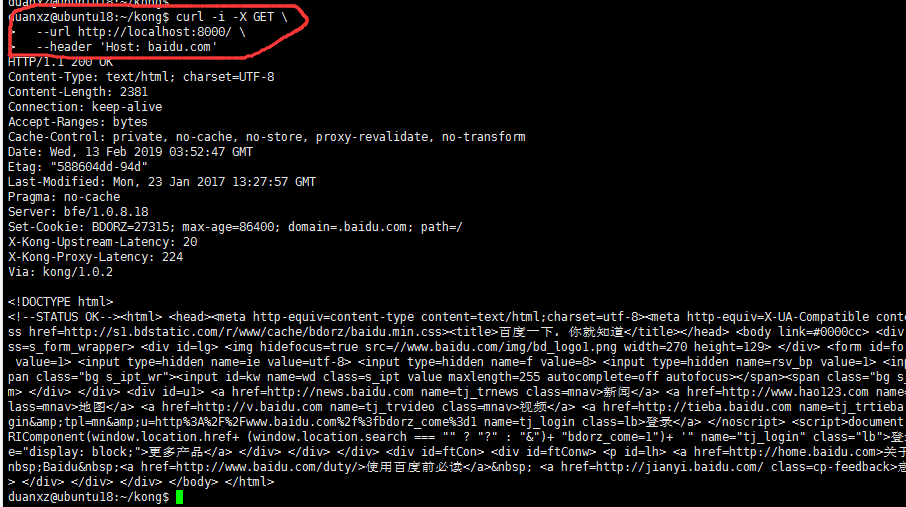
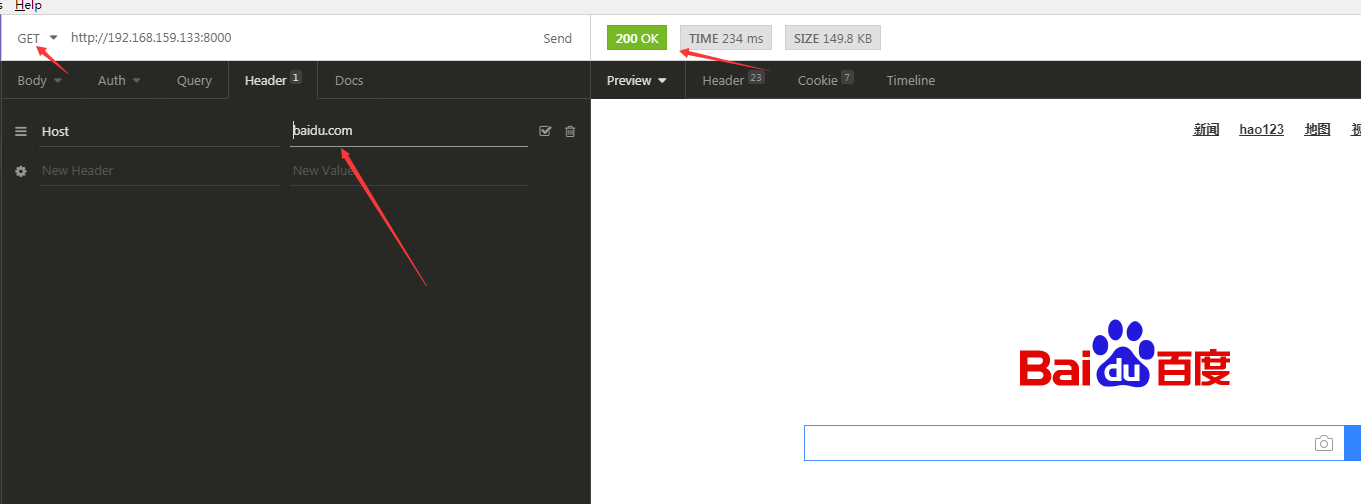
A successful response means Kong is now forwarding requests made to http://localhost:8000 to the url we configured in step #1, and is forwarding the response back to us. Kong knows to do this through the header defined in the above cURL request:
kong完美的实现了接口转发~
注意注册时,'hosts', 'uris' or 'methods'三个参数至少有一个必须指定。
示例2:Enabling Plugins
1. Configure the key-auth plugin
To configure the key-auth plugin for the Service you configured in Kong, issue the following cURL request:
curl -i -X POST \ --url http://localhost:8001/services/example-service/plugins/ \ --data 'name=key-auth'
Note: This plugin also accepts a config.key_names parameter, which defaults to ['apikey']. It is a list of headers and parameters names (both are supported) that are supposed to contain the apikey during a request.
2. Verify that the plugin is properly configured
Issue the following cURL request to verify that the key-auth plugin was properly configured on the Service:
curl -i -X GET \ --url http://localhost:8000/ \ --header 'Host: example.com'
Since you did not specify the required apikey header or parameter, the response should be 401 Unauthorized:
duanxz@ubuntu18:~/kong$ curl -i -X GET \ > --url http://localhost:8000/ \ > --header 'Host: example.com' HTTP/1.1 401 Unauthorized Date: Wed, 13 Feb 2019 04:13:09 GMT Content-Type: application/json; charset=utf-8 Connection: keep-alive WWW-Authenticate: Key realm="kong" Content-Length: 41 Server: kong/1.0.2 {"message":"No API key found in request"}
配置好了 key-auth plugin。
示例3:Consumer
配置好了 key-auth plugin后,lets learn how to add consumers to your Service so we can continue proxying requests through Kong。
1. Create a Consumer through the RESTful API
Lets create a user named Jason by issuing the following request:
curl -i -X POST \ --url http://localhost:8001/consumers/ \ --data "username=Jason"
You should see a response similar to the one below:
HTTP/1.1 201 Created Content-Type: application/json Connection: keep-alive { "custom_id": null, "created_at": 1550031667, "username": "Jason", "id": "f23dfd0f-6a43-444d-b628-6137cbdb1e6e" }
Congratulations! You’ve just added your first consumer to Kong.
Note: Kong also accepts a custom_id parameter when creating consumers to associate a consumer with your existing user database.
2. Provision key credentials for your Consumer
Now, we can create a key for our recently created consumer Jason by issuing the following request:
curl -i -X POST \ --url http://localhost:8001/consumers/Jason/key-auth/ \ --data 'key=ENTER_KEY_HERE'
返回:
HTTP/1.1 201 Created Date: Wed, 13 Feb 2019 04:22:30 GMT Content-Type: application/json; charset=utf-8 Connection: keep-alive Access-Control-Allow-Origin: * Server: kong/1.0.2 Content-Length: 149 { "key": "ENTER_KEY_HERE", "created_at": 1550031750, "consumer": { "id": "f23dfd0f-6a43-444d-b628-6137cbdb1e6e" }, "id": "6d6c4792-f295-4f2a-9941-9357d17240d1" }
3. Verify that your Consumer credentials are valid
We can now issue the following request to verify that the credentials of our Jason Consumer is valid:
curl -i -X GET \ --url http://localhost:8000 \ --header "Host: example.com" \ --header "apikey: ENTER_KEY_HERE"
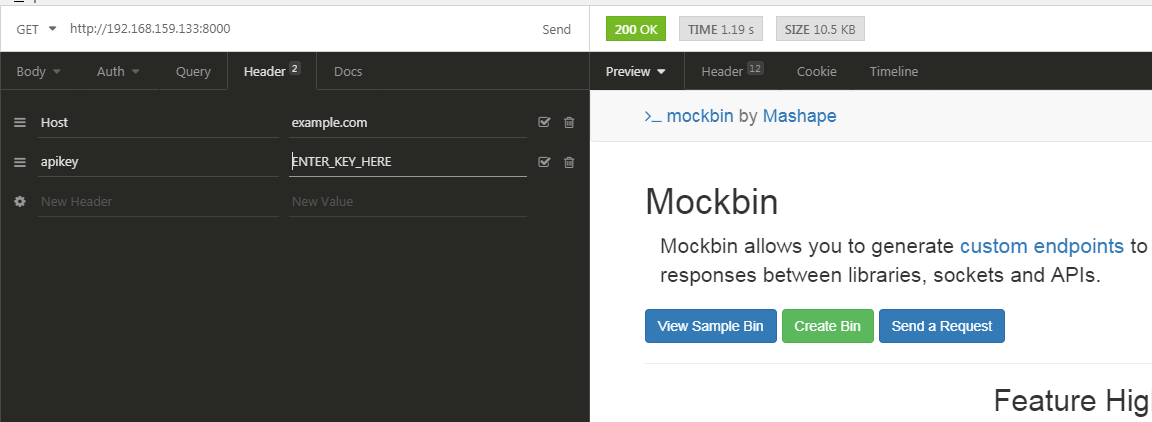
Next Steps
Now that we’ve covered the basics of adding Services, Routes, Consumers and enabling Plugins, feel free to read more on Kong in one of the following documents:
Questions? Issues? Contact us on one of the Community Channels for help!
遇到的问题
如果本机可以访问8000端口,远程机器无法通过ip:8000访问kong,估计是防火墙的问题
CentOS7使用firewalld打开关闭防火墙与端口 1、firewalld的基本使用 启动: systemctl start firewalld 关闭: systemctl stop firewalld 查看状态: systemctl status firewalld 开机禁用 : systemctl disable firewalld 开机启用 : systemctl enable firewalld
ERROR: module ‘socket’ not found:No LuaRocks module found for socket
启动的时候:
# ./bin/kong start -c ./kong.conf
...
ERROR: ./kong/globalpatches.lua:63: module 'socket' not found:No LuaRocks module found for socket
...
这是因为编译kong之后,重新编译了luarocks,并且将luarocks安装在了其它位置。重新编译kong之后解决。
ERROR: function to_regclass(unknown) does not exist (8)
创建数据库的时候:
# kong migrations up -c ./kong.conf
...
[postgres error] could not retrieve current migrations: [postgres error] ERROR: function to_regclass(unknown) does not exist (8)
...
这是因为PostgreSQL的版本太低了,to_regclass在PostgreSQL 9.4及以上的版本中才存在。
yum install https://download.postgresql.org/pub/repos/yum/9.6/redhat/rhel-7-x86_64/pgdg-centos96-9.6-3.noarch.rpm
yum install postgresql96
yum install postgresql96-server
nginx: [emerg] unknown directive “real_ip_header” in /usr/local/kong/nginx-kong.conf:73
nginx: [emerg] unknown directive "real_ip_header" in /usr/local/kong/nginx-kong.conf:73
这是因为编译的openresty的时候,没有指定--with-http_realip_module,重新编译安装:
./configure --with-pcre-jit --with-http_ssl_module --with-http_realip_module --with-http_stub_status_module --with-http_v2_module
make -j2
make install //默认安装在/usr/local/bin/openresty
export PATH=/usr/local/openresty/bin:$PATH