TCP的三次握手和四次挥手
tcp的报文格式
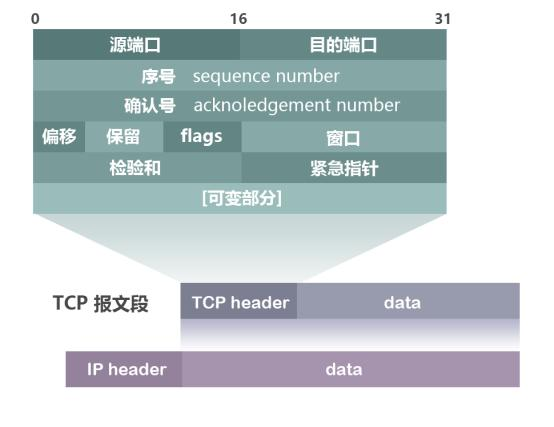
其中比较重要的字段有:
- 序号(sequence number):Seq序号,占32位,用来标识从TCP源端向目的端发送的字节流,发起方发送数据时对此进行标记。
- 确认号(acknowledgement number):Ack序号,占32位,只有ACK标志位为1时,确认序号字段才有效,Ack=Seq+1。
- 标志位(Flags):共6个,即URG、ACK、PSH、RST、SYN、FIN等。具体含义如下:
URG:紧急指针(urgent pointer)有效。
ACK:确认序号有效。
PSH:接收方应该尽快将这个报文交给应用层。
RST:重置连接。
SYN:发起一个新连接。
FIN:释放一个连接。
注意:不要将确认序号Ack与标志位中的ACK搞混了。确认方Ack=发起方Seq+1,两端配对。
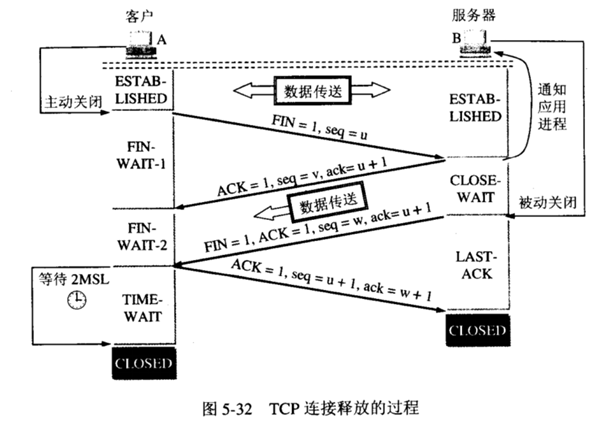
三次握手,四次挥手详细步骤解释
三次握手:
首先Client端发送连接请求报文,Server段接受连接后回复ACK报文,并为这次连接分配资源。Client端接收到ACK报文后也向Server段发生ACK报文,并分配资源,这样TCP连接就建立了。
最初两端的TCP进程都处于CLOSED关闭状态,A主动打开连接,而B被动打开连接。(A、B关闭状态CLOSED——B收听状态LISTEN——A同步已发送状态SYN-SENT——B同步收到状态SYN-RCVD——A、B连接已建立状态ESTABLISHED)
B的TCP服务器进程先创建传输控制块TCB,准备接受客户进程的连接请求。然后服务器进程就处于LISTEN(收听)状态,等待客户的连接请求。若有,则作出响应。
- 第一次握手:A的TCP客户进程也是首先创建传输控制块TCB,然后向B发出连接请求报文段,(首部的同步位SYN=1,初始序号seq=x),(SYN=1的报文段不能携带数据)但要消耗掉一个序号,此时TCP客户进程进入SYN-SENT(同步已发送)状态。
- 第二次握手:B收到连接请求报文段后,如同意建立连接,则向A发送确认,在确认报文段中(SYN=1,ACK=1,确认号ack=x+1,初始序号seq=y),测试TCP服务器进程进入SYN-RCVD(同步收到)状态;
- 第三次握手:TCP客户进程收到B的确认后,要向B给出确认报文段(ACK=1,确认号ack=y+1,序号seq=x+1)(初始为seq=x,第二个报文段所以要+1),ACK报文段可以携带数据,不携带数据则不消耗序号。TCP连接已经建立,A进入ESTABLISHED(已建立连接)。
当B收到A的确认后,也进入ESTABLISHED状态。
四次挥手:
- 假设Client端发起中断连接请求,也就是发送FIN报文。Server端接到FIN报文后,意思是说“我Client端没有数据要发给你了,但是如果你还有数据没有发送完成,则不必急着关闭Socket,可以继续发送数据。所以你先发送ACK,”
- 告诉Client端,你的请求我收到了,但是我还没准备好,请继续你等我的消息”。这个时候Client端就进入FIN_WAIT状态,继续等待Server端的FIN报文。
- 当Server端确定数据已发送完成,则向Client端发送FIN报文,”告诉Client端,好了,我这边数据发完了,准备好关闭连接了”。Client端收到FIN报文后,”就知道可以关闭连接了。
- 但是他还是不相信网络,怕Server端不知道要关闭,所以发送ACK后进入TIME_WAIT状态,如果Server端没有收到ACK则可以重传。“,Server端收到ACK后,”就知道可以断开连接了”。Client端等待了2MSL后依然没有收到回复,则证明Server端已正常关闭,那好,我Client端也可以关闭连接了。
- Ok,TCP连接就这样关闭了!
tcpdump报文举例
#tcpdump -i bond0 tcp and host 10.159.52.8 and 10.159.32.65
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on bond0, link-type EN10MB (Ethernet), capture size 262144 bytes
10:51:18.741495 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [S], seq 211844352, win 42340, options [mss 1460,nop,nop,sackOK,nop,wscale 9], length 0 //4006首先发起标志位为SYN的报文 [S] 请求建立连接
10:51:18.741846 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [S.], seq 3413662952, ack 211844353, win 5840, options [mss 1460,nop,nop,sackOK,nop,wscale 0], length 0
10:51:18.741860 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [.], ack 1, win 83, length 0
10:51:18.742006 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [P.], seq 1:22, ack 1, win 83, length 21
10:51:18.742224 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [.], ack 22, win 5840, length 0
10:51:18.762720 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [P.], seq 1:19, ack 22, win 5840, length 18
10:51:18.762739 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [.], ack 19, win 83, length 0
10:51:18.762930 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [P.], seq 22:1558, ack 19, win 83, length 1536
10:51:18.763210 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [.], ack 1558, win 8760, length 0
10:51:18.763857 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [P.], seq 19:499, ack 1558, win 8760, length 480
10:51:18.763909 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [P.], seq 1558:1582, ack 499, win 83, length 24
10:51:18.765726 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [P.], seq 499:779, ack 1582, win 8760, length 280
10:51:18.766581 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [P.], seq 1582:1854, ack 779, win 83, length 272
10:51:18.806289 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [.], ack 1854, win 11680, length 0
10:51:18.807452 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [P.], seq 779:1371, ack 1854, win 11680, length 592
10:51:18.808490 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [P.], seq 1854:1870, ack 1371, win 83, length 16
10:51:18.808775 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [.], ack 1870, win 11680, length 0
10:51:18.808789 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [P.], seq 1870:1922, ack 1371, win 83, length 52
10:51:18.809605 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [.], ack 1922, win 11680, length 0
10:51:18.809819 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [P.], seq 1371:1423, ack 1922, win 11680, length 52
10:51:18.809844 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [P.], seq 1922:1990, ack 1423, win 83, length 68
10:51:18.810994 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [P.], seq 1423:1491, ack 1990, win 11680, length 68
10:51:18.812655 IP 101d04006.cloud. d04.am12.49972 > 10.159.52.8.ssh: Flags [P.], seq 1990:2634, ack 1491, win 83, length 644
10:51:18.813608 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [P.], seq 1491:1559, ack 2634, win 14600, length 68
10:51:18.854421 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [.], ack 1559, win 83, length 0
10:51:23.906015 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [P.], seq 2634:2782, ack 1559, win 83, length 148
10:51:23.946227 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [.], ack 2782, win 17520, length 0
10:51:23.967757 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [P.], seq 1559:1595, ack 2782, win 17520, length 36
10:51:23.967769 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [.], ack 1595, win 83, length 0
10:51:23.967847 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [P.], seq 2782:2850, ack 1595, win 83, length 68
10:51:23.968231 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [.], ack 2850, win 17520, length 0
10:51:23.969941 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [P.], seq 1595:1647, ack 2850, win 17520, length 52
10:51:23.969997 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [P.], seq 2850:3310, ack 1647, win 83, length 460
10:51:23.977758 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [P.], seq 1647:1771, ack 3310, win 20440, length 124
10:51:24.018422 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [.], ack 1771, win 83, length 0
10:51:24.048297 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [P.], seq 1771:1839, ack 3310, win 20440, length 68
10:51:24.048311 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [.], ack 1839, win 83, length 0
10:51:24.048319 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [P.], seq 1839:1875, ack 3310, win 20440, length 36
10:51:24.048324 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [.], ack 1875, win 83, length 0
10:51:24.048408 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [P.], seq 3310:3382, ack 1875, win 83, length 72
10:51:24.048427 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [P.], seq 3382:3450, ack 1875, win 83, length 68
10:51:24.048453 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [F.], seq 3450, ack 1875, win 83, length 0 //4006端首先发起[F.] 即FIN标志位的报文 请求释放连接
10:51:24.048689 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [.], ack 3451, win 20440, length 0
10:51:24.054160 IP 10.159.52.8.ssh > 101d04006.cloud.d04.am12.49972: Flags [F.], seq 1875, ack 3451, win 20440, length 0
10:51:24.054172 IP 101d04006.cloud.d04.am12.49972 > 10.159.52.8.ssh: Flags [.], ack 1876, win 83, length 0