k8s笔记0528-基于KUBERNETES构建企业容器云手动部署集群记录-3
k8s笔记0528-基于KUBERNETES构建企业容器云手动部署集群记录-4
1.部署Kubernetes API服务部署
0.准备软件包
[root@linux-node1 ~]# cd /usr/local/src/kubernetes
[root@linux-node1 bin]# cp kube-apiserver kube-controller-manager kube-scheduler /opt/kubernetes/bin/
[root@linux-node1 bin]#
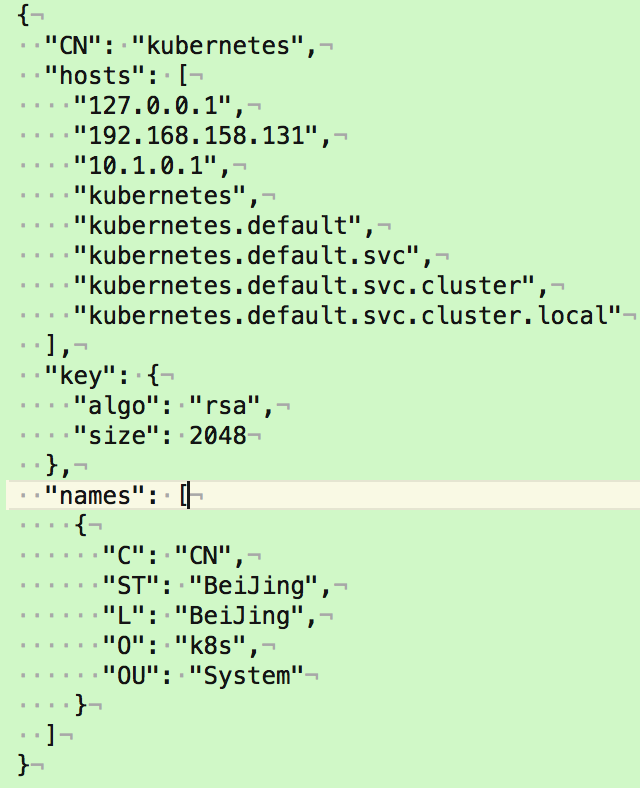
1.创建生成CSR的 JSON 配置文件
[root@linux-node1 src]# vim kubernetes-csr.json
{
"CN": "kubernetes",
"hosts": [
"127.0.0.1",
"192.168.158.131",
"10.1.0.1",
"kubernetes",
"kubernetes.default",
"kubernetes.default.svc",
"kubernetes.default.svc.cluster",
"kubernetes.default.svc.cluster.local"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "k8s",
"OU": "System"
}
]
}
2.生成 kubernetes 证书和私钥
[root@linux-node1 ssl]# cfssl gencert -ca=/opt/kubernetes/ssl/ca.pem \
> -ca-key=/opt/kubernetes/ssl/ca-key.pem \
> -config=/opt/kubernetes/ssl/ca-config.json \
> -profile=kubernetes kubernetes-csr.json | cfssljson -bare kubernetes
2018/05/28 19:55:07 [INFO] generate received request
2018/05/28 19:55:07 [INFO] received CSR
2018/05/28 19:55:07 [INFO] generating key: rsa-2048
2018/05/28 19:55:08 [INFO] encoded CSR
2018/05/28 19:55:08 [INFO] signed certificate with serial number 429355562738175455059700866326001085874406504869
2018/05/28 19:55:08 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for
websites. For more information see the Baseline Requirements for the Issuance and Management
of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);
specifically, section 10.2.3 ("Information Requirements").
[root@linux-node1 ssl]# ll
total 52
-rw-r--r-- 1 root root 291 May 28 15:43 ca-config.json
-rw-r--r-- 1 root root 1001 May 28 15:44 ca.csr
-rw-r--r-- 1 root root 208 May 28 15:43 ca-csr.json
-rw------- 1 root root 1675 May 28 15:44 ca-key.pem
-rw-r--r-- 1 root root 1359 May 28 15:44 ca.pem
-rw-r--r-- 1 root root 1062 May 28 16:50 etcd.csr
-rw-r--r-- 1 root root 289 May 28 16:49 etcd-csr.json
-rw------- 1 root root 1679 May 28 16:50 etcd-key.pem
-rw-r--r-- 1 root root 1436 May 28 16:50 etcd.pem
-rw-r--r-- 1 root root 1245 May 28 19:55 kubernetes.csr
-rw-r--r-- 1 root root 437 May 28 19:00 kubernetes-csr.json
-rw------- 1 root root 1679 May 28 19:55 kubernetes-key.pem
-rw-r--r-- 1 root root 1610 May 28 19:55 kubernetes.pem
[root@linux-node1 src]# cp kubernetes*.pem /opt/kubernetes/ssl/
[root@linux-node1 ssl]# cp kubernetes*.pem /opt/kubernetes/ssl/
[root@linux-node1 ssl]# scp kubernetes*.pem 192.168.158.132:/opt/kubernetes/ssl/
kubernetes-key.pem 100% 1679 1.6MB/s 00:00
kubernetes.pem 100% 1610 1.8MB/s 00:00
[root@linux-node1 ssl]# scp kubernetes*.pem 192.168.158.133:/opt/kubernetes/ssl/
kubernetes-key.pem 100% 1679 1.7MB/s 00:00
kubernetes.pem 100% 1610 1.7MB/s 00:00
[root@linux-node1 ssl]#
3.创建 kube-apiserver 使用的客户端 token 文件
[root@linux-node1 ~]# head -c 16 /dev/urandom | od -An -t x | tr -d ' '
ad6d5bb607a186796d8861557df0d17f
[root@linux-node1 ~]# vim /opt/kubernetes/ssl/ bootstrap-token.csv
ad6d5bb607a186796d8861557df0d17f,kubelet-bootstrap,10001,"system:kubelet-bootstrap"
[root@linux-node1 ssl]# cat /opt/kubernetes/ssl/bootstrap-token.csv
ad6d5bb607a186796d8861557df0d17f,kubelet-bootstrap,10001,"system:kubelet-bootstrap"
4.创建基础用户名/密码认证配置
[root@linux-node1 ~]# vim /opt/kubernetes/ssl/basic-auth.csv
admin,admin,1
readonly,readonly,2
5.部署Kubernetes API Server
[root@linux-node1 ~]# vim /usr/lib/systemd/system/kube-apiserver.service
[Unit]
Description=Kubernetes API Server
Documentation=https://github.com/GoogleCloudPlatform/kubernetes
After=network.target
[Service]
ExecStart=/opt/kubernetes/bin/kube-apiserver \
--admission-control=NamespaceLifecycle,LimitRanger,ServiceAccount,DefaultStorageClass,ResourceQuota,NodeRestriction \
--bind-address=192.168.56.11 \
--insecure-bind-address=127.0.0.1 \
--authorization-mode=Node,RBAC \
--runtime-config=rbac.authorization.k8s.io/v1 \
--kubelet-https=true \
--anonymous-auth=false \
--basic-auth-file=/opt/kubernetes/ssl/basic-auth.csv \
--enable-bootstrap-token-auth \
--token-auth-file=/opt/kubernetes/ssl/bootstrap-token.csv \
--service-cluster-ip-range=10.1.0.0/16 \
--service-node-port-range=20000-40000 \
--tls-cert-file=/opt/kubernetes/ssl/kubernetes.pem \
--tls-private-key-file=/opt/kubernetes/ssl/kubernetes-key.pem \
--client-ca-file=/opt/kubernetes/ssl/ca.pem \
--service-account-key-file=/opt/kubernetes/ssl/ca-key.pem \
--etcd-cafile=/opt/kubernetes/ssl/ca.pem \
--etcd-certfile=/opt/kubernetes/ssl/kubernetes.pem \
--etcd-keyfile=/opt/kubernetes/ssl/kubernetes-key.pem \
--etcd-servers=https://192.168.158.131:2379,https://192.168.158.132:2379,https://192.168.158.133:2379 \
--enable-swagger-ui=true \
--allow-privileged=true \
--audit-log-maxage=30 \
--audit-log-maxbackup=3 \
--audit-log-maxsize=100 \
--audit-log-path=/opt/kubernetes/log/api-audit.log \
--event-ttl=1h \
--v=2 \
--logtostderr=false \
--log-dir=/opt/kubernetes/log
Restart=on-failure
RestartSec=5
Type=notify
LimitNOFILE=65536
[Install]
WantedBy=multi-user.target
6.启动API Server服务
[root@linux-node1 ~]# systemctl daemon-reload
[root@linux-node1 ssl]# systemctl enable kube-apiserver
Created symlink from /etc/systemd/system/multi-user.target.wants/kube-apiserver.service to /usr/lib/systemd/system/kube-apiserver.service.
[root@linux-node1 ~]# systemctl start kube-apiserver
查看API Server服务状态
[root@linux-node1 ssl]# systemctl status kube-apiserver
[0m kube-apiserver.service - Kubernetes API Server
Loaded: loaded (/usr/lib/systemd/system/kube-apiserver.service; enabled; vendor preset: disabled)
Active: active (running) since Mon 2018-05-28 22:21:23 CST; 32s ago
Docs: https://github.com/GoogleCloudPlatform/kubernetes
Main PID: 14217 (kube-apiserver)
CGroup: /system.slice/kube-apiserver.service
14217 /opt/kubernetes/bin/kube-apiserver --admission-control=NamespaceLifecycle,LimitRanger,Serv...
May 28 22:21:15 linux-node1.example.com systemd[1]: Starting Kubernetes API Server...
May 28 22:21:15 linux-node1.example.com kube-apiserver[14217]: Flag --admission-control has been deprecated...n.
May 28 22:21:15 linux-node1.example.com kube-apiserver[14217]: Flag --insecure-bind-address has been deprec...n.
May 28 22:21:18 linux-node1.example.com kube-apiserver[14217]: [restful] 2018/05/28 22:21:18 log.go:33: [re...pi
May 28 22:21:18 linux-node1.example.com kube-apiserver[14217]: [restful] 2018/05/28 22:21:18 log.go:33: [re...i/
May 28 22:21:20 linux-node1.example.com kube-apiserver[14217]: [restful] 2018/05/28 22:21:20 log.go:33: [re...pi
May 28 22:21:20 linux-node1.example.com kube-apiserver[14217]: [restful] 2018/05/28 22:21:20 log.go:33: [re...i/
May 28 22:21:23 linux-node1.example.com systemd[1]: Started Kubernetes API Server.
Hint: Some lines were ellipsized, use -l to show in full.
[root@linux-node1 ssl]# netstat -ntlp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 192.168.158.131:6443 0.0.0.0:* LISTEN 14217/kube-apiserve
tcp 0 0 192.168.158.131:2379 0.0.0.0:* LISTEN 13541/etcd
tcp 0 0 127.0.0.1:2379 0.0.0.0:* LISTEN 13541/etcd
tcp 0 0 192.168.158.131:2380 0.0.0.0:* LISTEN 13541/etcd
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN 14217/kube-apiserve
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 895/sshd
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 1105/master
tcp6 0 0 :::22 :::* LISTEN 895/sshd
tcp6 0 0 ::1:25 :::* LISTEN 1105/master
[root@linux-node1 ssl]#
部署Controller Manager服务
[root@linux-node1 ~]# vim /usr/lib/systemd/system/kube-controller-manager.service
[Unit]
Description=Kubernetes Controller Manager
Documentation=https://github.com/GoogleCloudPlatform/kubernetes
[Service]
ExecStart=/opt/kubernetes/bin/kube-controller-manager \
--address=127.0.0.1 \
--master=http://127.0.0.1:8080 \
--allocate-node-cidrs=true \
--service-cluster-ip-range=10.1.0.0/16 \
--cluster-cidr=10.2.0.0/16 \
--cluster-name=kubernetes \
--cluster-signing-cert-file=/opt/kubernetes/ssl/ca.pem \
--cluster-signing-key-file=/opt/kubernetes/ssl/ca-key.pem \
--service-account-private-key-file=/opt/kubernetes/ssl/ca-key.pem \
--root-ca-file=/opt/kubernetes/ssl/ca.pem \
--leader-elect=true \
--v=2 \
--logtostderr=false \
--log-dir=/opt/kubernetes/log
Restart=on-failure
RestartSec=5
[Install]
WantedBy=multi-user.target
3.启动Controller Manager
[root@linux-node1 ~]# systemctl daemon-reload
root@linux-node1 ssl]# systemctl enable kube-controller-manager
Created symlink from /etc/systemd/system/multi-user.target.wants/kube-controller-manager.service to /usr/lib/systemd/system/kube-controller-manager.service.
[root@linux-node1 scripts]# systemctl start kube-controller-manager
[root@linux-node1 ssl]# netstat -ntlp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 192.168.158.131:6443 0.0.0.0:* LISTEN 14217/kube-apiserve
tcp 0 0 192.168.158.131:2379 0.0.0.0:* LISTEN 13541/etcd
tcp 0 0 127.0.0.1:2379 0.0.0.0:* LISTEN 13541/etcd
tcp 0 0 127.0.0.1:10252 0.0.0.0:* LISTEN 14271/kube-controll
tcp 0 0 192.168.158.131:2380 0.0.0.0:* LISTEN 13541/etcd
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN 14217/kube-apiserve
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 895/sshd
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 1105/master
tcp6 0 0 :::22 :::* LISTEN 895/sshd
tcp6 0 0 ::1:25 :::* LISTEN 1105/master
4.查看服务状态
[root@linux-node1 scripts]# systemctl status kube-controller-manager
部署Kubernetes Scheduler
[root@linux-node1 ~]# vim /usr/lib/systemd/system/kube-scheduler.service
[Unit]
Description=Kubernetes Scheduler
Documentation=https://github.com/GoogleCloudPlatform/kubernetes
[Service]
ExecStart=/opt/kubernetes/bin/kube-scheduler \
--address=127.0.0.1 \
--master=http://127.0.0.1:8080 \
--leader-elect=true \
--v=2 \
--logtostderr=false \
--log-dir=/opt/kubernetes/log
Restart=on-failure
RestartSec=5
[Install]
WantedBy=multi-user.target
2.部署服务
[root@linux-node1 ~]# systemctl daemon-reload
[[root@linux-node1 ssl]# systemctl enable kube-scheduler
Created symlink from /etc/systemd/system/multi-user.target.wants/kube-scheduler.service to /usr/lib/systemd/system/kube-scheduler.service.
[root@linux-node1 scripts]# systemctl start kube-scheduler
[root@linux-node1 ssl]# systemctl status kube-scheduler
[0m kube-scheduler.service - Kubernetes Scheduler
Loaded: loaded (/usr/lib/systemd/system/kube-scheduler.service; enabled; vendor preset: disabled)
Active: active (running) since Mon 2018-05-28 22:31:56 CST; 9s ago
Docs: https://github.com/GoogleCloudPlatform/kubernetes
Main PID: 14341 (kube-scheduler)
CGroup: /system.slice/kube-scheduler.service
14341 /opt/kubernetes/bin/kube-scheduler --address=127.0.0.1 --master=...
May 28 22:31:56 linux-node1.example.com systemd[1]: Started Kubernetes Scheduler.
May 28 22:31:56 linux-node1.example.com systemd[1]: Starting Kubernetes Scheduler...
[root@linux-node1 ssl]#
部署kubectl 命令行工具
1.准备二进制命令包
[root@linux-node1 ssl]# cd /usr/local/src/kubernetes/client/bin/
[root@linux-node1 bin]# ls
kubectl
[root@linux-node1 bin]# cp kubectl /opt/kubernetes/bin/
[root@linux-node1 bin]# cd /usr/local/src/ssl/
[root@linux-node1 ssl]# ll
total 52
-rw-r--r-- 1 root root 291 May 28 15:43 ca-config.json
-rw-r--r-- 1 root root 1001 May 28 15:44 ca.csr
-rw-r--r-- 1 root root 208 May 28 15:43 ca-csr.json
-rw------- 1 root root 1675 May 28 15:44 ca-key.pem
-rw-r--r-- 1 root root 1359 May 28 15:44 ca.pem
-rw-r--r-- 1 root root 1062 May 28 16:50 etcd.csr
-rw-r--r-- 1 root root 289 May 28 16:49 etcd-csr.json
-rw------- 1 root root 1679 May 28 16:50 etcd-key.pem
-rw-r--r-- 1 root root 1436 May 28 16:50 etcd.pem
-rw-r--r-- 1 root root 1245 May 28 19:55 kubernetes.csr
-rw-r--r-- 1 root root 437 May 28 19:00 kubernetes-csr.json
-rw------- 1 root root 1679 May 28 19:55 kubernetes-key.pem
-rw-r--r-- 1 root root 1610 May 28 19:55 kubernetes.pem
[root@linux-node1 ssl]#
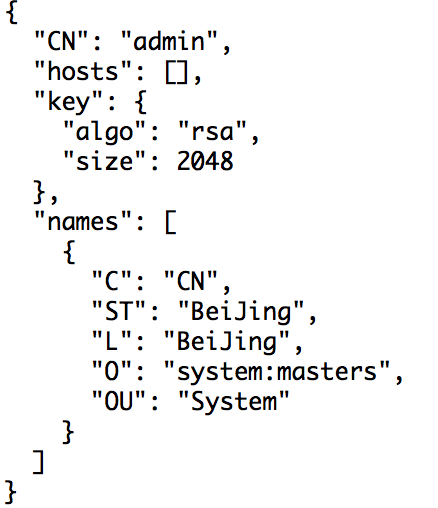
2.创建 admin 证书签名请求
[root@linux-node1 ~]# cd /usr/local/src/ssl/
[root@linux-node1 ssl]# vim admin-csr.json
{
"CN": "admin",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "system:masters",
"OU": "System"
}
]
}
3.生成 admin 证书和私钥:
[root@linux-node1 ssl]# cfssl gencert -ca=/opt/kubernetes/ssl/ca.pem \
> -ca-key=/opt/kubernetes/ssl/ca-key.pem \
> -config=/opt/kubernetes/ssl/ca-config.json \
> -profile=kubernetes admin-csr.json | cfssljson -bare admin
2018/05/28 22:38:14 [INFO] generate received request
2018/05/28 22:38:14 [INFO] received CSR
2018/05/28 22:38:14 [INFO] generating key: rsa-2048
2018/05/28 22:38:15 [INFO] encoded CSR
2018/05/28 22:38:15 [INFO] signed certificate with serial number 179251497463658016603079534231975727820629158502
2018/05/28 22:38:15 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for
websites. For more information see the Baseline Requirements for the Issuance and Management
of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org);
specifically, section 10.2.3 ("Information Requirements").
[root@linux-node1 ssl]#
[root@linux-node1 ssl]# ls -l admin*
-rw-r--r-- 1 root root 1009 May 28 22:38 admin.csr
-rw-r--r-- 1 root root 229 May 28 22:37 admin-csr.json
-rw------- 1 root root 1675 May 28 22:38 admin-key.pem
-rw-r--r-- 1 root root 1399 May 28 22:38 admin.pem
[root@linux-node1 ssl]#
[root@linux-node1 ssl]# cp admin*.pem /opt/kubernetes/ssl/
[root@linux-node1 ssl]# ls -l /opt/kubernetes/ssl/
total 48
-rw------- 1 root root 1675 May 28 22:39 admin-key.pem
-rw-r--r-- 1 root root 1399 May 28 22:39 admin.pem
-rw-r--r-- 1 root root 34 May 28 20:01 basic-auth.csv
-rw-r--r-- 1 root root 84 May 28 20:00 bootstrap-token.csv
-rw-r--r-- 1 root root 291 May 28 15:47 ca-config.json
-rw-r--r-- 1 root root 1001 May 28 15:47 ca.csr
-rw------- 1 root root 1675 May 28 15:47 ca-key.pem
-rw-r--r-- 1 root root 1359 May 28 15:47 ca.pem
-rw------- 1 root root 1679 May 28 16:55 etcd-key.pem
-rw-r--r-- 1 root root 1436 May 28 16:55 etcd.pem
-rw------- 1 root root 1679 May 28 19:56 kubernetes-key.pem
-rw-r--r-- 1 root root 1610 May 28 19:56 kubernetes.pem
4.设置集群参数
[root@linux-node1 ssl]# kubectl config set-cluster kubernetes \
> --certificate-authority=/opt/kubernetes/ssl/ca.pem \
> --embed-certs=true \
> --server=https://192.168.158.131:6443
Cluster "kubernetes" set.
5.设置客户端认证参数
[root@linux-node1 ssl]# kubectl config set-credentials admin \
> --client-certificate=/opt/kubernetes/ssl/admin.pem \
> --embed-certs=true \
> --client-key=/opt/kubernetes/ssl/admin-key.pem
User "admin" set.
6.设置上下文参数
[[root@linux-node1 ssl]# kubectl config set-context kubernetes \
> --cluster=kubernetes \
> --user=admin
Context "kubernetes" created.
7.设置默认上下文
[[root@linux-node1 ssl]# kubectl config use-context kubernetes
Switched to context "kubernetes".
[root@linux-node1 ssl]#
8.使用kubectl工具
[root@linux-node1 ssl]# kubectl get cs
NAME STATUS MESSAGE ERROR
controller-manager Healthy ok
scheduler Healthy ok
etcd-0 Healthy {"health": "true"}
etcd-2 Healthy {"health": "true"}
etcd-1 Healthy {"health": "true"}

