bridge fdb vxlan nolearning
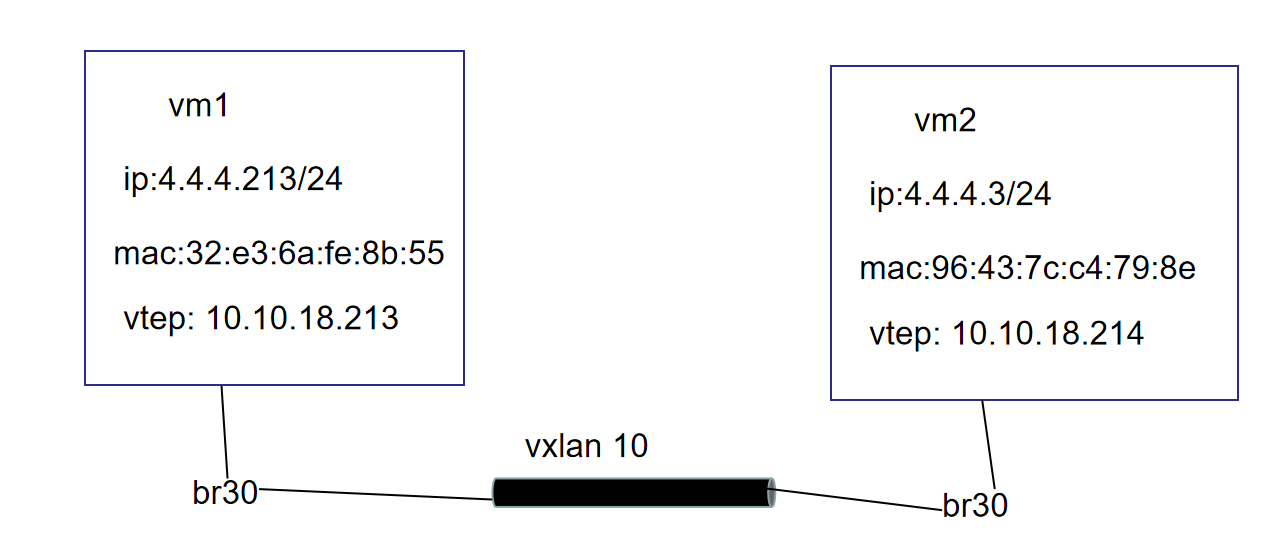
现在把vxlan类型改为:
10.10.18.213节点上
ip link add vxlan10 type vxlan id 10 local 10.10.18.213 dstport 4789 nolearning
10.10.18.214节点上
ip link add vxlan10 type vxlan id 10 local 10.10.18.214 dstport 4789 nolearning
[root@evpn2 ~]# bridge fdb show | grep vxlan10 6e:99:e1:80:f3:f6 dev dev vxlan10 vlan 1 master br30 permanent 6e:99:e1:80:f3:f6 dev dev vxlan10 master br30 permanent [root@evpn2 ~]# ip netns exec host3 ping 4.4.4.213 PING 4.4.4.213 (4.4.4.213) 56(84) bytes of data. ^C --- 4.4.4.213 ping statistics --- 2 packets transmitted, 0 received, 100% packet loss, time 49ms 无法ping通 [root@evpn2 ~]# bridge fdb add 00:00:00:00:00:00 dev vxlan10 dst 10.10.18.213 [root@evpn2 ~]# ip netns exec host3 ping 4.4.4.213 PING 4.4.4.213 (4.4.4.213) 56(84) bytes of data. ^C --- 4.4.4.213 ping statistics --- 2 packets transmitted, 0 received, 100% packet loss, time 39ms
还是无法ping通 在10.10.18.213节点上添加 [root@evpn2 ~]# bridge fdb add 00:00:00:00:00:00 dev vxlan10 dst 10.10.18.214 [root@evpn2 ~]# ip netns exec host3 ping 4.4.4.213 PING 4.4.4.213 (4.4.4.213) 56(84) bytes of data. 64 bytes from 4.4.4.213: icmp_seq=1 ttl=64 time=0.616 ms 64 bytes from 4.4.4.213: icmp_seq=2 ttl=64 time=0.346 ms 64 bytes from 4.4.4.213: icmp_seq=3 ttl=64 time=0.443 ms ^C --- 4.4.4.213 ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 120ms rtt min/avg/max/mdev = 0.346/0.468/0.616/0.113 ms
ping 通了 在10.10.18.213节点上 [root@evpn2 ~]# bridge fdb show | grep vxlan10 96:43:7c:c4:79:8e dev dev vxlan10 master br30 e6:84:f8:05:8f:0e dev dev vxlan10 vlan 1 master br30 permanent e6:84:f8:05:8f:0e dev dev vxlan10 master br30 permanent 00:00:00:00:00:00 dev dev vxlan10 dst 10.10.18.214 self permanent 在10.10.18.214节点上 [root@evpn2 ~]# bridge fdb show | grep vxlan10 6e:99:e1:80:f3:f6 dev dev vxlan10 vlan 1 master br30 permanent 6e:99:e1:80:f3:f6 dev dev vxlan10 master br30 permanent 00:00:00:00:00:00 dev dev vxlan10 dst 10.10.18.213 self permanent
[root@evpn2 ~]# ip netns exec host3 ip n
4.4.4.254 dev eth0 lladdr 26:01:66:a5:9c:cc STALE
4.4.4.1 dev eth0 FAILED
4.4.4.213 dev eth0 lladdr 32:e3:6a:fe:8b:55 STALE
开启nolearning之后10.10.18.213节点后fdb不会学习到这条条目
96:43:7c:c4:79:8e dev dev vxlan10 dst 10.10.18.214 self
开启nolearning之后10.10.18.214节点后fdb不会学习到这条条目
32:e3:6a:fe:8b:55 dev dev vxlan10 dst 10.10.18.213 self
10.10.18.213节点上 tcpdump
[root@evpn2 ~]# ip netns exec host3 tcpdump -i eth0 -eennvv
tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
11:34:13.789816 96:43:7c:c4:79:8e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 4.4.4.213 tell 4.4.4.3, length 28
11:34:13.789840 32:e3:6a:fe:8b:55 > 96:43:7c:c4:79:8e, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 4.4.4.213 is-at 32:e3:6a:fe:8b:55, length 28
11:34:13.790134 96:43:7c:c4:79:8e > 32:e3:6a:fe:8b:55, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 9834, offset 0, flags [DF], proto ICMP (1), length 84)
4.4.4.3 > 4.4.4.213: ICMP echo request, id 7195, seq 1, length 64
11:34:13.790158 32:e3:6a:fe:8b:55 > 96:43:7c:c4:79:8e, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 61347, offset 0, flags [none], proto ICMP (1), length 84)
4.4.4.213 > 4.4.4.3: ICMP echo reply, id 7195, seq 1, length 64
11:34:14.828132 96:43:7c:c4:79:8e > 32:e3:6a:fe:8b:55, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 9863, offset 0, flags [DF], proto ICMP (1), length 84)
4.4.4.3 > 4.4.4.213: ICMP echo request, id 7195, seq 2, length 64
11:34:14.828160 32:e3:6a:fe:8b:55 > 96:43:7c:c4:79:8e, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 61400, offset 0, flags [none], proto ICMP (1), length 84)
4.4.4.213 > 4.4.4.3: ICMP echo reply, id 7195, seq 2, length 64
11:34:15.867882 96:43:7c:c4:79:8e > 32:e3:6a:fe:8b:55, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 9903, offset 0, flags [DF], proto ICMP (1), length 84)
4.4.4.3 > 4.4.4.213: ICMP echo request, id 7195, seq 3, length 64
11:34:15.867909 32:e3:6a:fe:8b:55 > 96:43:7c:c4:79:8e, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 61492, offset 0, flags [none], proto ICMP (1), length 84)
4.4.4.213 > 4.4.4.3: ICMP echo reply, id 7195, seq 3, length 64
11:34:16.908304 96:43:7c:c4:79:8e > 32:e3:6a:fe:8b:55, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 9943, offset 0, flags [DF], proto ICMP (1), length 84)
4.4.4.3 > 4.4.4.213: ICMP echo request, id 7195, seq 4, length 64
11:34:16.908329 32:e3:6a:fe:8b:55 > 96:43:7c:c4:79:8e, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 61585, offset 0, flags [none], proto ICMP (1), length 84)
4.4.4.213 > 4.4.4.3: ICMP echo reply, id 7195, seq 4, length 64
11:34:17.948213 96:43:7c:c4:79:8e > 32:e3:6a:fe:8b:55, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 10018, offset 0, flags [DF], proto ICMP (1), length 84)
4.4.4.3 > 4.4.4.213: ICMP echo request, id 7195, seq 5, length 64
11:34:17.948241 32:e3:6a:fe:8b:55 > 96:43:7c:c4:79:8e, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 61607, offset 0, flags [none], proto ICMP (1), length 84)
4.4.4.213 > 4.4.4.3: ICMP echo reply, id 7195, seq 5, length 64
^C
12 packets captured
12 packets received by filter
0 packets dropped by kernel


