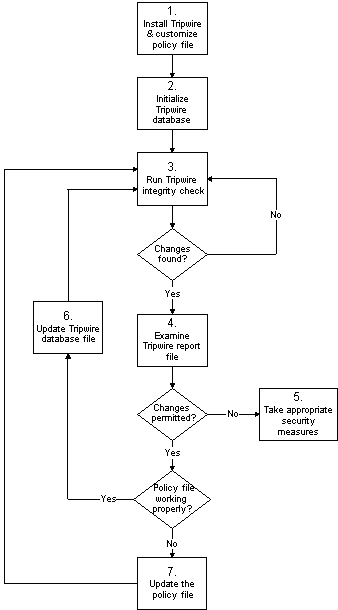
Contents
1. Install Tripwire
2. Initializing the Database
3. Run a Tripwire integrity check
4. Printing Reports
5. Take appropriate security measures
6. Updating the Database after an Integrity Check
7. Updating the Policy File
8. Signing the Configuration File
9. Run tripwire from cron
10. Check if tripwire can send E-Mails
Details to the Tripwire Policies can be found in the Policy Guide
Overview
Tripwire software can help to ensure the integrity of critical system files and directories by identifying all changes made to them. Tripwire configuration options include the ability to receive alerts via email if particular files are altered and automated integrity checking via a cron job. Using Tripwire for intrusion detectionand damage assessment helps you keep track of system changes and can speed the recovery from a break-in by reducing the number of files you must restore to repair the system.
Tripwire compares files and directories against a baseline database of file locations, dates modified, and other data. It generates the baseline by taking a snapshot of specified files and directories in a known secure state. (For maximum security, Tripwire should be installed and the baseline created before the system is at risk from intrusion.) After creating the baseline database, Tripwire compares the current system to the baseline and reports any modifications, additions, or deletions.
Install Tripwire and customize the policy file — If not already done, install the tripwire RPM or download source from www.tripwire.org. Then, customize the sample configuration (/etc/tripwire/twcfg.txt) and policy (/etc/tripwire/twpol.txt) files and run the configuration script (/etc/tripwire/twinstall.sh).
Configuration file: /etc/tripwire/twcfg.txt
Usually it is not necessary to edit this file. The setting you may need to modify is MAILNOVIOLATIONS. By default this is set to true, which will send out an email everytime an integrity check is run. Setting MAILNOVIOLATIONS=false will cause Tripwire to only send an email if there is a violation.
Policy file: /etc/tripwire/twpol.txt
Most is already done, however there may be some files to check which doesn't exist in the filesystem, uncomment them. Add your own files which should be checked.
Tripwire can email someone if a specific type of rule in the policy file is violated.# Tripwire Binaries
(
rulename = "Tripwire Binaries",
severity = $(SIG_HI),
emailto = martin dot zahn at akadia dot ch
)
Run the configuration script (/etc/tripwire/twinstall.sh).
# twinstall.sh
When initializing its database, Tripwire builds a collection of filesystem objects based on the rules in the policy file. This database serves as the baseline for integrity checks.
To initialize the Tripwire database, use the following command:
# tripwire --init
The The /var/lib/tripwire directory contains the Tripwire database of your system's files (*.twd) and a report directory where Tripwire reports are stored. The Tripwire reports, named host_name-date_of_report-time_of_report.twr, detail the differences between the Tripwire database and your actual system files.
3. Run a Tripwire integrity check
When running an integrity check, Tripwire compares the current, actual filesystem objects with their properties as recorded in its database. Violations are printed to standard output and saved in a report file that can be accessed later by twprint.
An email configuration option in the policy file even allows particular email addresses to be sent notices when certain integrity violations occur.
To run an integrity check, use the following command:
# tripwire --check
The twprint -m r command will display the contents of a Tripwire report in clear text. You must tell twprint which report file to display.
A twprint command for printing Tripwire reports looks similar to the following (all on one line):
# twprint -m r --twrfile /var/lib/tripwire/report/<name>.twr
The -m r option in the command tells twprint to decode a Tripwire report. The --twrfile option tells twprint to use a specific Tripwire report file.
The name of the Tripwire report that you want to see includes the name of the host that Tripwire checked to generate the report, plus the creation date and time. You can review previously saved reports at any time. Simply type ls /var/lib/tripwire/report to see a list of Tripwire reports.
5. Take appropriate security measures
If monitored files have been altered inappropriately, you can either replace the originals from backups or reinstall the program.
6. Updating the Database after an Integrity Check
If you run an integrity check and Tripwire finds violations, you will first need to determine whether the violations discovered are actual security breaches or the product of authorized modifications. If you recently installed an application or edited critical system files, Tripwire will (correctly) report integrity check violations. In this case, you should update your Tripwire database so those changes are no longer reported as violations. However, if unauthorized changes are made to system files that generate integrity check violations, then you should restore the original file from a backup or reinstall the program.
To update your Tripwire database to accept the violations found in a report, you must specify the report you wish to use to update the database. When issuing the command to integrate those valid violations into your database, be sure to use the most recent report.
Type the following command (all on one line), where name is the name of the report to be used:
# tripwire --update --twrfile /var/lib/tripwire/report/<name>.twr
Tripwire will show you the particular report using the default text editor (specified in the Tripwire configuration file on the EDITOR line). This is your chance to deselect files that you do not wish to be updated in the Tripwire database. It is important that you only allow authorized integrity violations to be changed in the database.
All proposed updates to the Tripwire database start with a [x] before the file name. If you want to specifically exclude a valid violation from being added to the Tripwire database, remove the x from the box. To accept any files with an x beside them as changes, write the file in the editor and quit the text editor. This signals to Tripwire to alter its database and not report these files as violations.
For example, the default text editor for Tripwire is vi. To write the file with vi and make the changes to the Tripwire database when updating with a specific report, type :wq in vi's command mode and press [Enter]. You will be asked to enter your local passphrase. Then, a new database file will be written to include the valid violations.
After a new Tripwire database is written, the newly authorized integrity violations will no longer show up as warnings when the next integrity check is run.
If you want to actually change the files Tripwire records in its database or modify the severity in which violations are reported, you need to edit your Tripwire policy file.
First, make whatever changes are necessary to the sample policy file (/etc/tripwire/twpol.txt). A common change to this policy file is to comment out any files that do not exist on your system so that they will not generate a file not found error in your Tripwire reports. For example, if your system does not have a /etc/smb.conf file, you can tell Tripwire not to try to look for it by commenting out its line in twpol.txt:
# /etc/smb.conf -> $(SEC_CONFIG) ;
Next, you must tell Tripwire to generate a new /etc/tripwire/tw.pol signed file and then generate an updated database file based on this policy information. Assuming /etc/tripwire/twpol.txt is the edited policy file, use this command:
# twadmin --create-polfile -S site.key /etc/tripwire/twpol.txt
You will be asked for the site passphrase. Then, the twpol.txt file will be parsed and signed.
It is important that you update the Tripwire database after creating a new /etc/tripwire/tw.pol file. The most reliable way to accomplish this is to delete your current Tripwire database and create a new database using the new policy file.
If your Tripwire database file is named /var/lib/tripwire/paragon.twd, type this command:
# rm /var/lib/tripwire/paragon.twd
Then type the command to create a new database:
# tripwire --init
A new database will be created according to the instructions in the new policy file. To make sure the database was correctly changed, run the first integrity check manually and view the contents of the resulting report. See the section called Running an Integrity Check and the section called Printing Reports for specific instructions on these points.
8. Signing the Configuration File
The text file with the configuration file changes (commonly /etc/tripwire/twcfg.txt) must be signed to replace the /etc/tripwire/tw.cfg and be used by Tripwire when it runs its integrity check. Tripwire will not recognize any configuration changes until the configuration text file is correctly signed and used to replace the /etc/tripwire/tw.pol file.
If your altered configuration text file is /etc/tripwire/twcfg.txt, type this command to sign it, replacing the current /etc/tripwire/tw.pol file:
# twadmin --create-cfgfile -S site.key /etc/tripwire/twcfg.txt
Since the configuration file does not not alter any Tripwire policies or files tracked by the application, it is not necessary to regenerate the database of monitored system files.
You can run a Tripwire integrity check daily by inserting the following commands in the script /etc/cron.daily/tripwire-check:
#!/bin/sh
HOST_NAME=`uname -n`
if [ ! -e /var/lib/tripwire/${HOST_NAME}.twd ]; then
echo "Error: Tripwire database for ${HOST_NAME} not found"
echo "Run "/etc/tripwire/twinstall.sh" and/or "tripwire --init""
else
test -f /etc/tripwire/tw.cfg && /usr/sbin/tripwire --check
fi
10. Check if tripwire can send E-Mails
Tripwire can email someone if a specific type of rule in the policy file is violated. To configure Tripwire to do this, you first have to know the email address of the person to be contacted if a particular integrity violation occurs, plus the name of the rule you would like to monitor. Note that on large systems with multiple administrators, you can have different sets of people notified for certain violations and no one notified for minor violations.
Once you know who to notify and what to notify them about, add an emailto= line to the rule directive section of each rule. Do this by adding a comma after the severity= line and putting emailto= on the next line, followed by the email addresses to send the violation reports for that rule. Multiple emails will be sent if more than one email address is specified and they are separated by a semi-colon.
(
rulename = "Networking Programs",
severity = $(SIG_HI),
emailto = akadia-adm@akadia.com
)
Sending Test Email Messages
To make sure that Tripwire's email notification configuration can actually send email correctly, use the following command:
/usr/sbin/tripwire --test --email akadia-adm@akadia.com
A test email will immediately be sent to the email address by the tripwire program.




 浙公网安备 33010602011771号
浙公网安备 33010602011771号