山石防火墙Hillsonte+Linux6.9+Linux7.4 IP协议双栈应用
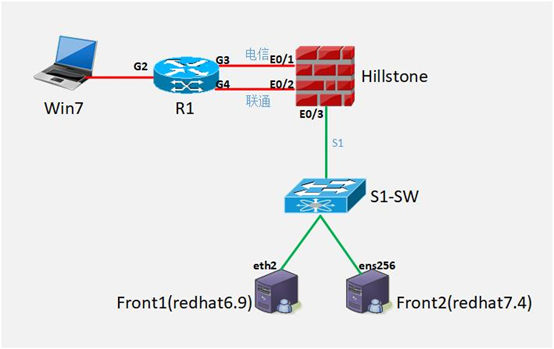
一、模拟网络拓扑
本次实验是模拟测试IPv4toIPv4映射配置、IPv6toIPv6映射配置
模拟两条运营商线路,通过山石防火墙将内部linux服务器(Redhat6.9\Redhat7.4)的SSH服务双栈地址,映射至公网
二、IPv6地址信息
1、 运营商分配地址
|
序号 |
运营商 |
IPv4地址 |
IPv6地址 |
|
1 |
电信 |
网间网:202.98.224.1/30网关 |
2409::2/127网关 |
|
2 |
联通 |
58.22.96.0/28 |
2301::/64 |
2、 内部ip分配
win7:
172.16.10.2/24
IPv6:2202::2/64
R1:
G2:172.16.10.1/24
IPv6: 2202::1/64
G3:202.98.224.1/30
IPv6: 2409::2/127
G4:58.22.96.1/28
IPv6: 2301::1/64
Hillstone:
E0/1: 202.98.224.2/30
IPv6: 2409::3/127
E0/2: 58.22.96.2/28
IPv6: 2301::1/64
E0/3:172.16.110.254/24
IPv6:FEC0::1/96
Tip:服务器与防火墙互联的IPv6地址段,从FEC0::/10(类似ipv4私网地址段)的站点本地地址取96掩码地址使用,可用范围:
FEC0::-FEC0::FFFF:FFFF/96
Front1:
eth2:172.16.110.4/24
IPv6:FEC0::4/96
Front2:
ens256:172.16.110.5/24
IPv6:FEC0::5/96
三、设备IP配置
1、 win7
IPv4地址配置
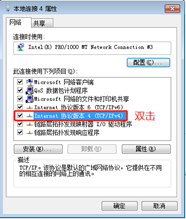
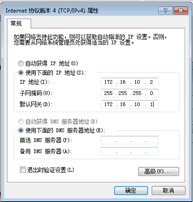
验证:ipconfig、route print
IPv6地址配置
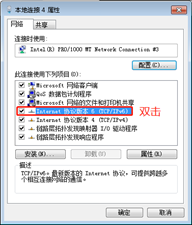
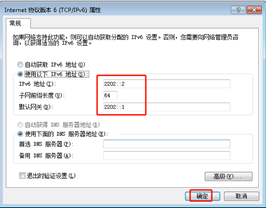
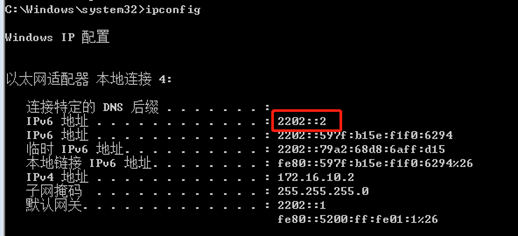
验证:ipconfig、route print -6
ipconfig:查看网卡配置
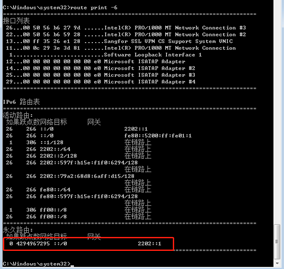
route print -6: 查看IPv6路由信息
2、 R1
R1(config)# ipv6 unicast-routing /开启ipv6路由转发
R1(config)# interface GigabitEthernet2 /配置接口IP地址
R1(config-if)#ip address 172.16.10.1 255.255.255.0 /IPv4地址配置
R1(config-if)#ipv6 address 2202::1/64 /IPv6地址配置
R1(config-if)#end
R1(config)# interface GigabitEthernet3
R1(config-if)# ip address 202.98.224.1 255.255.255.252
R1(config-if)# ipv6 address 2409::2/127
R1(config-if)#end
R1(config)# interface GigabitEthernet4
R1(config-if)# ip address 58.22.96.1 255.255.255.240
R1(config-if)# ipv6 address 2301::1/64
R1(config-if)#end
路由配置:
R1(config)#ip route 202.98.110.0 255.255.255.240 202.98.224.2 name DianXin
R1(config)#ipv6 route 2409:E0::/64 2409::3 name DianXin
验证:
show ip interface brief 查看接口IPv4地址
show ip route 查看IPv4路由
ping X.X.X.X 测试接口连通性
show ipv6 interface brief 查看接口IPv6地址
show ipv6 route 查看IPv6路由
ping ipv6 XXXX::2 Ping IPv6连通性
3、 Hillstone防火墙
山石防火墙在配置IPv6时,web界面可配置接口IPv6地址、IPv6路由、IPv6策略,但web界面配置不了NAT映射,本次全部采用命令行的形式配置。
山石防火墙配置接口IPv6地址
SG-6000(config)# interface ethernet0/1
zone "untrust"
ip address 202.98.224.2 255.255.255.252
description "电信"
ipv6 enable
ipv6 address 2409::3/127
no reverse-route
exit
SG-6000(config)# interface ethernet0/2
zone "untrust"
ip address 58.22.96.2 255.255.255.240
description "联通"
ipv6 enable
ipv6 address 2301::2/64
no reverse-route
exit
SG-6000(config)# interface ethernet0/3
zone "trust"
ip address 172.16.110.254 255.255.255.0
description "S1"
ipv6 enable
ipv6 address FEC0::1/64
manage ping
exit
SG-6000(config)# service "TCP-8222" /定义端口,NAT时调用
tcp dst-port 8222
SG-6000(config)# ip vrouter trust-vr /进入虚拟路由器模式(路由、nat配置)
SG-6000(config-vrouter)#
ip route 0.0.0.0/0 202.98.224.1 /配置IPv4路由,电信为主
ip route 0.0.0.0/0 58.22.96.1 10 /配置IPv4路由,联通为备,管理距离10
ipv6 route ::/0 2409::2 /配置IPv6路由,电信为主
ipv6 route ::/0 2301::1 10 /配置IPv6路由,联通为备,管理距离10
地址转换,将front1和Front2的SSH分别映射到电信和联通的8222端口
ip vroute "trust-vr"
dnatrule from address-book "Any" to ip 202.98.110.1 service "TCP-8222" trans-to ip 172.16.110.4 port 22
dnatrule from address-book "Any" to ip 202.98.110.2 service "TCP-8222" trans-to ip 172.16.110.5 port 22
dnatrule from address-book "Any" to ip 58.22.96.3 service "TCP-8222" trans-to ip 172.16.110.4 port 22
dnatrule from address-book "Any" to ip 58.22.96.4 service "TCP-8222" trans-to ip 172.16.110.5 port 22
dnatrule from ipv6-any to ip 2409:E0::1/128 service "TCP-8222" trans-to ip FEC0::4/128 port 22
dnatrule from ipv6-any to ip 2409:E0::2/128 service "TCP-8222" trans-to ip FEC0::5/128 port 22
dnatrule from ipv6-any to ip 2301::3/128 service "TCP-8222" trans-to ip FEC0::4/128 port 22
dnatrule from ipv6-any to ip 2301::4/128 service "TCP-8222" trans-to ip FEC0::5/128 port 22
配置安全策略
定义地址簿,配置安全策略时调用
address "电信-202.98.110.1"
ip 202.98.110.1/32
exit
address "电信-202.98.110.2"
ip 202.98.110.2/32
exit
address "联通-58.22.96.3"
ip 58.22.96.3/32
exit
address "联通-58.22.96.4"
ip 58.22.96.4/32
exit
address "电信-2409:E0::1" ipv6
ip 2409:E0::1/128
exit
address "电信-2409:E0::2" ipv6
ip 2409:E0::2/128
exit
address "联通-2301::3" ipv6
ip 2301::3/128
exit
address "联通-2301::4" ipv6
ip 2031::4/128
exit
安全策略配置
rule id 1
action permit
src-zone "untrust"
dst-zone "trust"
src-addr "Any"
dst-addr "联通-58.22.96.3"
dst-addr "联通-58.22.96.4"
dst-addr "电信-202.98.110.1"
dst-addr "电信-202.98.110.2"
service "TCP-8222"
name "untrust-to-trust"
exit
rule id 2
action permit
src-zone "untrust"
dst-zone "trust"
src-addr "IPv6-any"
dst-addr "电信-2409:E0::1"
dst-addr "电信-2409:E0::2"
dst-addr "联通-2301::3"
dst-addr "联通-2301::4"
service "TCP-8222"
name "untrust-to-trust-ipv6"
exit
4、 Front1(Redhat6.9)
在CentOS/Redhat 6 and 7版本中, ipv6默认是开启的。可通过
ifconfig | grep inet6 验证
网卡配置IP地址及网关:
vim /etc/sysconfig/network-scripts/ifcfg-eth2
|
DEVICE=eth2 HWADDR=00:50:56:B6:91:C1 TYPE=Ethernet UUID=50411ea2-4db5-4fcb-92e5-544dbb5769de ONBOOT=yes NM_CONTROLLED=yes BOOTPROTO=static IPADDR=172.16.110.4 NETMASK=255.255.255.0 GATEWAY=172.16.110.254 IPV6INIT=yes IPV6ADDR=fec0::4/96 IPV6_DEFAULTGW=fec0::1 |
配置完成后,重启网卡服务:
service network restart
验证:
ifconfig /查看网卡ip信息
route -n /查看IPv4路由
route -n -A inet6 /查看IPv6路由
ping6 fec0::1 /ping IPv6网关测试
5、 Front2(Redhat7.4)
|
TYPE=Ethernet PROXY_METHOD=none BROWSER_ONLY=no BOOTPROTO=statc DEFROUTE=yes IPV4_FAILURE_FATAL=no IPV6INIT=yes IPV6_AUTOCONF=yes IPV6_DEFROUTE=yes IPV6_FAILURE_FATAL=no IPV6_ADDR_GEN_MODE=stable-privacy NAME=ens256 UUID=55073c2e-8345-46fa-9d62-71639709c82c DEVICE=ens256 ONBOOT=yes IPADDR=172.16.110.5 NETMASK=255.255.255.0 GATEWAY=172.16.110.254 IPV6ADDR=fec0::5/96 IPV6_DEFAULTGW=fec0::1 |
vim /etc/sysconfig/network-scripts/ifcfg-ens256
配置完成后,重启网卡服务:
systemctl restart network
验证:
ifconfig /查看网卡ip信息
route -n /查看IPv4路由
route -n -A inet6 /查看IPv6路由
ping6 fec0::1 /ping IPv6网关测试



