Microsoft Exchange Server CVE-2022-41040 & CVE-2022-41082 Nmap检测脚本
CVE-2022-41040 Microsoft Exchange Server权限提升漏洞
CVE-2022-41082 Microsoft Exchange Server 远程执行代码漏洞

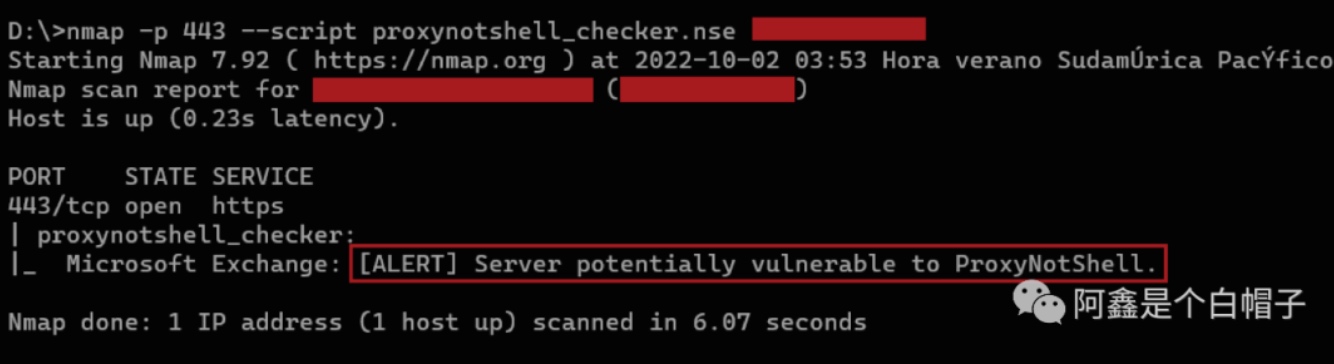
一个Nmap 脚本可扫描可能易受#ProxyNotShell影响的服务器(基于 Microsoft 推荐的 URL 阻止规则)
local http = require "http"
local shortport = require "shortport"
local stdnse = require "stdnse"
local string = require "string"
description = [[
Check for Microsoft Exchange servers potentially vulnerable to ProxyNotShell (CVE-2022-40140 & CVE-2022-41082).
References:
https://www.gteltsc.vn/blog/warning-new-attack-campaign-utilized-a-new-0day-rce-vulnerability-on-microsoft-exchange-server-12715.html
https://msrc-blog.microsoft.com/2022/09/29/customer-guidance-for-reported-zero-day-vulnerabilities-in-microsoft-exchange-server/
https://doublepulsar.com/proxynotshell-the-story-of-the-claimed-zero-day-in-microsoft-exchange-5c63d963a9e9
]]
-- @usage
-- nmap --script proxynotshell_checker.nse -p443 <host>
author = "Germán Fernández (1ZRR4H)"
license = "GPLv3"
categories = {"default", "discovery", "safe"}
portrule = shortport.http
local function CheckVuln(host,port)
payload = "/autodiscover/autodiscover.json?a@foo.var/owa/&Email=autodiscover/autodiscover.json?a@foo.var&Protocol=XYZ&FooProtocol=Powershell"
local options = {header={}}
options["redirect_ok"] = false
options["header"]["User-Agent"] = 'User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:105.0) Gecko/20100101 Firefox/105.0'
response = http.get(host,port,payload,options)
if (response.status == 302) and (response.header['x-feserver'] ~= nil) then
return "Vulnerable to ProxyShell and potentially to ProxyNotShell (mitigation not applied)."
elseif (response.status ~= 302) and (response.header['x-feserver'] ~= nil) then
return "Potentially vulnerable to ProxyNotShell (mitigation not applied)."
elseif (response.status == 401) then
return "Not Vulnerable (resource requires basic authentication)."
elseif (response.status == 404) then
return "Not Vulnerable (affected resource not found)."
elseif (response.status == 403) then
return "Not Vulnerable (access to resource is blocked)."
elseif (response.status == 500) then
return "Not Vulnerable (internal server error)."
else
return "Not vulnerable or not a valid server."
end
end
action = function(host, port)
local response = stdnse.output_table()
response["Microsoft Exchange"] = CheckVuln(host,port)
return response
end
https://github.com/CronUp/Vulnerabilidades

posted on 2022-10-03 11:56 Ra7ing安全实验室 阅读(1014) 评论(0) 编辑 收藏 举报


