wfuzz 过滤参数检测、目录探测、字典爆破
/usr/share/wfuzz
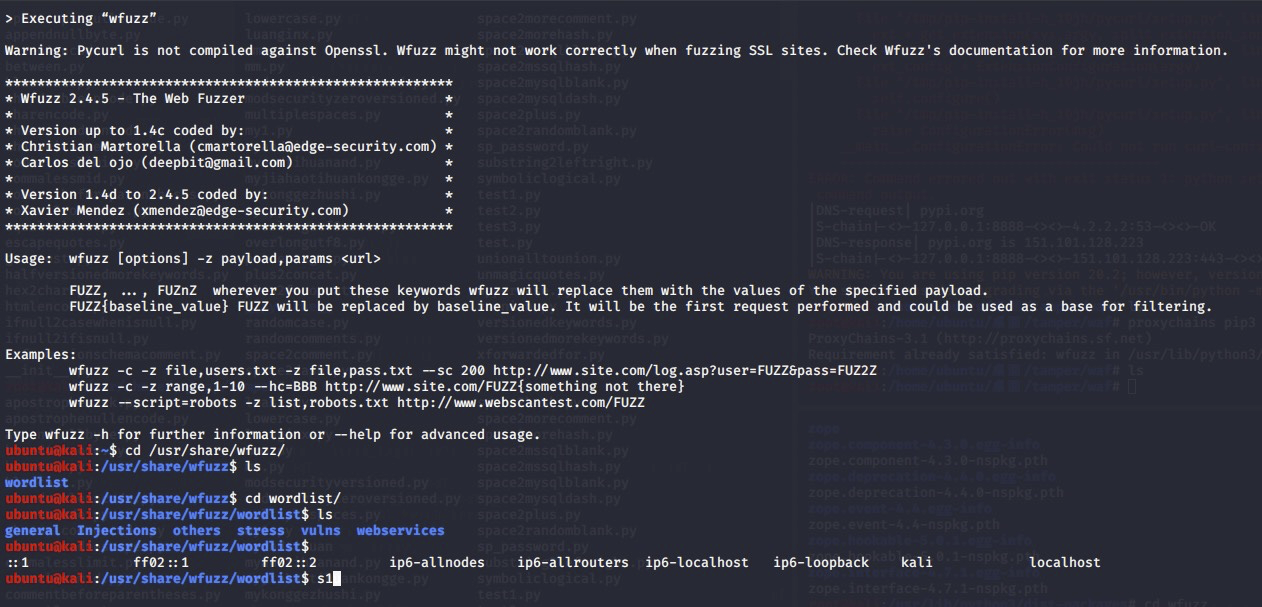
目录结构
ubuntu@kali:/usr/share$ tree wfuzz/
wfuzz/
└── wordlist
├── general
│ ├── admin-panels.txt
│ ├── big.txt
│ ├── catala.txt
│ ├── common.txt
│ ├── euskera.txt
│ ├── extensions_common.txt
│ ├── http_methods.txt
│ ├── medium.txt
│ ├── megabeast.txt
│ ├── mutations_common.txt
│ ├── spanish.txt
│ └── test.txt
├── Injections
│ ├── All_attack.txt
│ ├── bad_chars.txt
│ ├── SQL.txt
│ ├── Traversal.txt
│ ├── XML.txt
│ └── XSS.txt
├── others
│ ├── common_pass.txt
│ └── names.txt
├── stress
│ ├── alphanum_case_extra.txt
│ ├── alphanum_case.txt
│ ├── char.txt
│ ├── doble_uri_hex.txt
│ ├── test_ext.txt
│ └── uri_hex.txt
├── vulns
│ ├── apache.txt
│ ├── cgis.txt
│ ├── coldfusion.txt
│ ├── dirTraversal-nix.txt
│ ├── dirTraversal.txt
│ ├── dirTraversal-win.txt
│ ├── domino.txt
│ ├── fatwire_pagenames.txt
│ ├── fatwire.txt
│ ├── frontpage.txt
│ ├── iis.txt
│ ├── iplanet.txt
│ ├── jrun.txt
│ ├── netware.txt
│ ├── oracle9i.txt
│ ├── sharepoint.txt
│ ├── sql_inj.txt
│ ├── sunas.txt
│ ├── tests.txt
│ ├── tomcat.txt
│ ├── vignette.txt
│ ├── weblogic.txt
│ └── websphere.txt
└── webservices
├── ws-dirs.txt
└── ws-files.txt
7 directories, 51 fileUsage: wfuzz [options] -z payload,params <url> FUZZ, ..., FUZnZ wherever you put these keywords wfuzz will replace them with the values of the specified payload. FUZZ{baseline_value} FUZZ will be replaced by baseline_value. It will be the first request performed and could be used as a base for filtering. Options: -h/--help : This help --help : Advanced help --filter-help : Filter language specification --version : Wfuzz version details -e <type> : List of available encoders/payloads/iterators/printers/scripts
参数说明:
Usage: wfuzz [options] -z payload,params <url>
FUZZ, ..., FUZnZ wherever you put these keywords wfuzz will replace them with the values of the specified payload.
FUZZ{baseline_value} FUZZ will be replaced by baseline_value. It will be the first request performed and could be used as a base for filtering.
Options:
-h/--help : This help
--help : Advanced help
--filter-help : Filter language specification
--version : Wfuzz version details
-e <type> : List of available encoders/payloads/iterators/printers/scripts
--recipe <filename> : Reads options from a recipe. Repeat for various recipes.
--dump-recipe <filename> : Prints current options as a recipe
--oF <filename> : Saves fuzz results to a file. These can be consumed later using the wfuzz payload.
-c : Output with colors 带颜色显示
-v : Verbose information.
-f filename,printer : Store results in the output file using the specified printer (raw printer if omitted). 输出到文件的格式,格式有raw,json,csv,magictree,html,txt
-o printer : Show results using the specified printer.
--interact : (beta) If selected,all key presses are captured. This allows you to interact with the program.
--dry-run : Print the results of applying the requests without actually making any HTTP request.
--prev : Print the previous HTTP requests (only when using payloads generating fuzzresults)
--efield <expr> : Show the specified language expression together with the current payload
--field <expr> : Do not show the payload but only the specified language expression
-p addr : Use Proxy in format ip:port:type. Repeat option for using various proxies.
Where type could be SOCKS4,SOCKS5 or HTTP if omitted.
-t N : Specify the number of concurrent connections (10 default) 设置线程 默认10
-s N : Specify time delay between requests (0 default) 请求间隔时间
-R depth : Recursive path discovery being depth the maximum recursion level. 递归深度,探测目录 递归深度为1也就是说当发现某一个目录存在的时候,在存在目录下再递归一次字典 -R 1(深度为1)
-L,--follow : Follow HTTP redirections
--ip host:port : Specify an IP to connect to instead of the URL's host in the format ip:port
-Z : Scan mode (Connection errors will be ignored).
--req-delay N : Sets the maximum time in seconds the request is allowed to take (CURLOPT_TIMEOUT). Default 90.
--conn-delay N : Sets the maximum time in seconds the connection phase to the server to take (CURLOPT_CONNECTTIMEOUT). Default 90.
-A, --AA, --AAA : Alias for --script=default,verbose,discovery -v -c
--no-cache : Disable plugins cache. Every request will be scanned.
--script= : Equivalent to --script=default
--script=<plugins> : Runs script's scan. <plugins> is a comma separated list of plugin-files or plugin-categories
--script-help=<plugins> : Show help about scripts.
--script-args n1=v1,... : Provide arguments to scripts. ie. --script-args grep.regex="<A href=\"(.*?)\">"
-u url : Specify a URL for the request.
-m iterator : Specify an iterator for combining payloads (product by default)
-z payload : Specify a payload for each FUZZ keyword used in the form of name[,parameter][,encoder]. 设置payload 比如:字典。-z file,1.txt(以文件形式,导入1.txt) -z range,1-10(以范围形式,1到10) -z list,1-2-3-10(列表形式,1,2,3,10)
A list of encoders can be used, ie. md5-sha1. Encoders can be chained, ie. md5@sha1.
Encoders category can be used. ie. url
Use help as a payload to show payload plugin's details (you can filter using --slice)
--zP <params> : Arguments for the specified payload (it must be preceded by -z or -w).
--zD <default> : Default parameter for the specified payload (it must be preceded by -z or -w).
--zE <encoder> : Encoder for the specified payload (it must be preceded by -z or -w).
--slice <filter> : Filter payload's elements using the specified expression. It must be preceded by -z.
-w wordlist : Specify a wordlist file (alias for -z file,wordlist). 指定使用字典
-V alltype : All parameters bruteforcing (allvars and allpost). No need for FUZZ keyword.
-X method : Specify an HTTP method for the request, ie. HEAD or FUZZ 设定请求方法 -X GET
-b cookie : Specify a cookie for the requests. Repeat option for various cookies. 设定cookie -b “cookie=”
-d postdata : Use post data (ex: "id=FUZZ&catalogue=1") 设定POST -d “uname=FUZZ&passwd=FUZZ”
-H header : Use header (ex:"Cookie:id=1312321&user=FUZZ"). Repeat option for various headers. 参数来指定HTTP请求的请求头,多次指定多次使用 -H “User-Agent: firfox”
--basic/ntlm/digest auth : in format "user:pass" or "FUZZ:FUZZ" or "domain\FUZ2Z:FUZZ"
--hc/hl/hw/hh N[,N]+ : Hide responses with the specified code/lines/words/chars (Use BBB for taking values from baseline) 过滤状态码 --hc 503:隐藏响应码为503的 --hl 20:隐藏响应信息行数为20行的 --hw 30:隐藏响应信息中字数为30的 --hh 50:隐藏响应信息中字符数为50的
--sc/sl/sw/sh N[,N]+ : Show responses with the specified code/lines/words/chars (Use BBB for taking values from baseline) 需要显示的状态码 --sc 405:显示响应码405
--ss/hs regex : Show/hide responses with the specified regex within the content
--filter <filter> : Show/hide responses using the specified filter expression (Use BBB for taking values from baseline)
--prefilter <filter> : Filter items before fuzzing using the specified expression.
检测过滤参数payload:
sudo wfuzz -w Injections/SQL.txt -u http://xxx.xxx.xxx.xxx/get.php?id=FUZZ -c -f ./1.txt
结果如下:
ID:测试时的请求序号; Response:HTTP响应码; Lines:响应信息中的行数; Word:响应信息中的字数; Chars:响应信息中的字符数; Payload:当前使用的payload。
$ sudo wfuzz -w Injections/SQL.txt -u http://xxx.xxx.xxx.xxx/get.php?id=FUZZ -c -f ./1.txt Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information. ******************************************************** * Wfuzz 2.4.5 - The Web Fuzzer * ******************************************************** Target: http://xxx.xxx.xxx.xxx/get.php?id=FUZZ Total requests: 130 =================================================================== ID Response Lines Word Chars Payload =================================================================== 000000001: 200 12 L 18 W 168 Ch "or" 000000002: 200 12 L 18 W 169 Ch "and" 000000005: 200 12 L 18 W 167 Ch "=" 000000004: 200 18 L 27 W 242 Ch "" 000000007: 200 18 L 27 W 243 Ch """ 000000009: 200 18 L 27 W 243 Ch "-" 000000010: 200 18 L 27 W 244 Ch "--" 000000003: 200 18 L 27 W 242 Ch "" 000000008: 200 18 L 27 W 242 Ch "#" 000000006: 200 18 L 27 W 243 Ch "'" 000000011: 200 12 L 17 W 167 Ch "'%20--" 000000013: 200 12 L 17 W 167 Ch "'%20;" 000000012: 200 18 L 27 W 246 Ch "--';" 000000014: 200 12 L 18 W 167 Ch "=%20'" 000000015: 200 12 L 18 W 167 Ch "=%20;" 000000016: 200 12 L 18 W 167 Ch "=%20--" 000000019: 200 12 L 17 W 167 Ch "\x3D%20\x3B'" 000000017: 200 18 L 27 W 246 Ch "\x23" 000000018: 200 18 L 27 W 246 Ch "\x27" 000000020: 200 12 L 17 W 167 Ch "\x3D%20\x27" 000000021: 200 12 L 17 W 167 Ch "\x27\x4F\x52 SELECT *" 000000022: 200 12 L 17 W 167 Ch "\x27\x6F\x72 SELECT *" 000000023: 200 12 L 18 W 168 Ch "'or%20select *" 000000026: 200 12 L 18 W 167 Ch "'%20or%20''='" 000000027: 200 12 L 18 W 167 Ch "'%20or%20'x'='x" 000000028: 200 12 L 18 W 167 Ch ""%20or%20"x"="x"
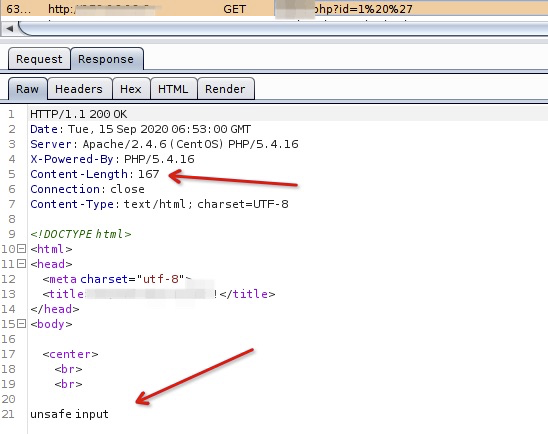
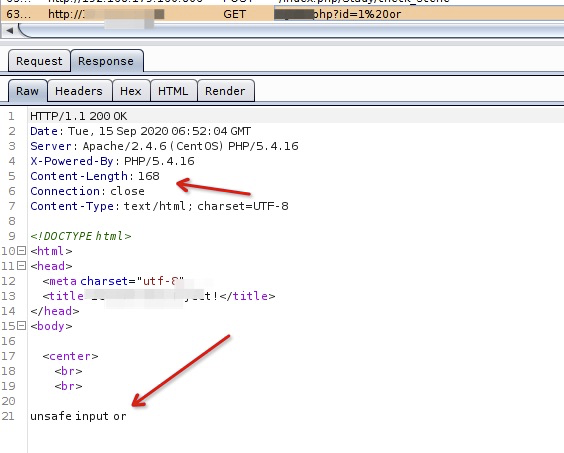
通过字节长度判断过滤的参数:

wfuzz目录探测
wfuzz -c -z file,/home/dir.txt -R 2 -f 2.html,html http://xxx.xxx/FUZZ
-c:是否选择带颜色输出,这是个人选择。
-z:payload / wordlist - 您希望它使用的列表。
-hs:忽略包含无效的响应,在这个实例中,h是隐藏的,而s实际上是这个实例中的regex开关
-d:发送请求
FUZZ:fuzz的部分
公用目录探测
$ wfuzz -w wordlist/general/common.txt http://testphp.vulnweb.com/FUZZ
查找常见文件
$ wfuzz -w wordlist/general/common.txt http://testphp.vulnweb.com/FUZZ.php
输出2.html在当前目录
find -name 2.html //在当前目录及子目录下查找文件
然后使用命令默认程序打开2.html
xdg-open 2.html //默认程序打开指定文件,注意路径,该命令需普通用户执行
一次探测多个fuzz
wfuzz -z file,1.txt -z file,2.txt http://www.xxx.com/FUZZ/FUZ2Z.html
//wfuzz -w 字典1 -w 字典2 -w 字典3 URL/FUZZ/FUZ2Z.FUZ3Z
wfuzz -c -z file,users.txt -z file,pass.txt --sc 200 http://www.site.com/log.asp?user=FUZZ&pass=FUZ2Z wfuzz -c -z range,1-10 --hc=BBB http://www.site.com/FUZZ{something not there} wfuzz --script=robots -z list,robots.txt http://www.webscantest.com/FUZZ
wfuzz字典爆破
wfuzz.py -c -z file,users.txt -z file,pass.txt — sc 200 http://www.site.com/log.asp?user=FUZZ&pass=FUZ2Z
wfuzz代理
//http、socks4、socks5代理,及多个代理示例
$ wfuzz -z file,wordlist/general/common.txt -p localhost:8080 http://testphp.vulnweb.com/FUZZ $ wfuzz -z file,wordlist/general/common.txt -p localhost:2222:SOCKS5 http://testphp.vulnweb.com/FUZZ $ wfuzz -z file,wordlist/general/common.txt -p localhost:8080 -p localhost:9090 http://testphp.vulnweb.com/FUZZ
详情见官方文档:https://wfuzz.readthedocs.io/en/latest/user/basicusage.html#fuzzing-paths-and-files
posted on 2020-09-15 14:12 Ra7ing安全实验室 阅读(2563) 评论(0) 收藏 举报


 浙公网安备 33010602011771号
浙公网安备 33010602011771号