StrongSwan
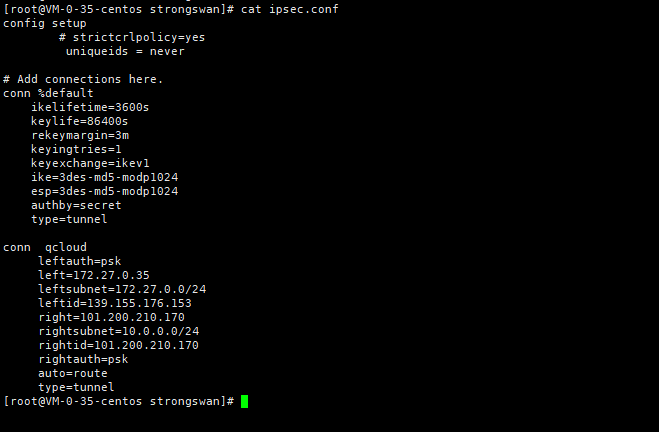
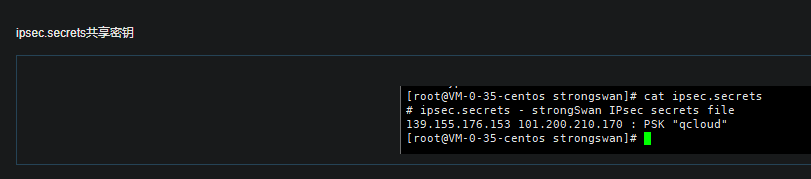
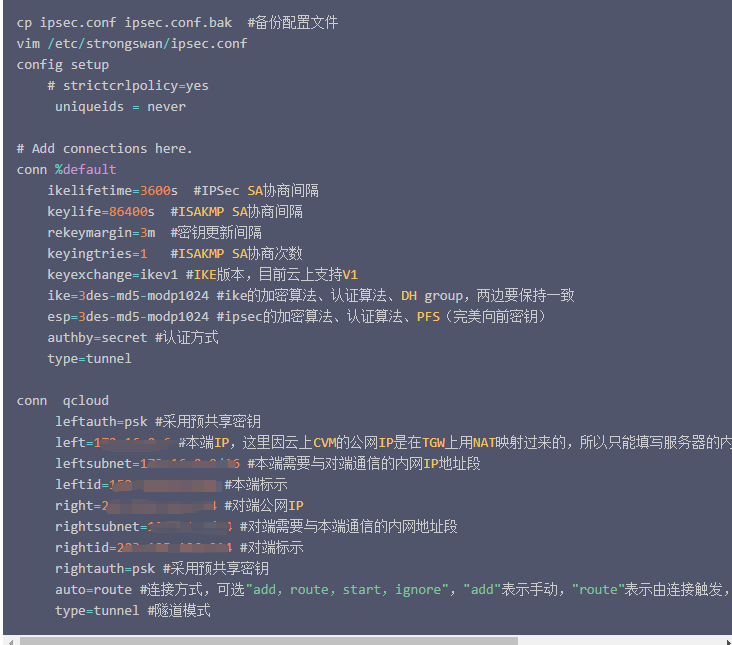
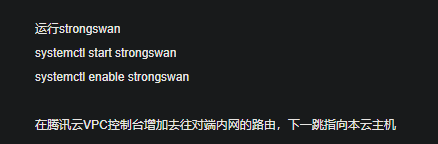
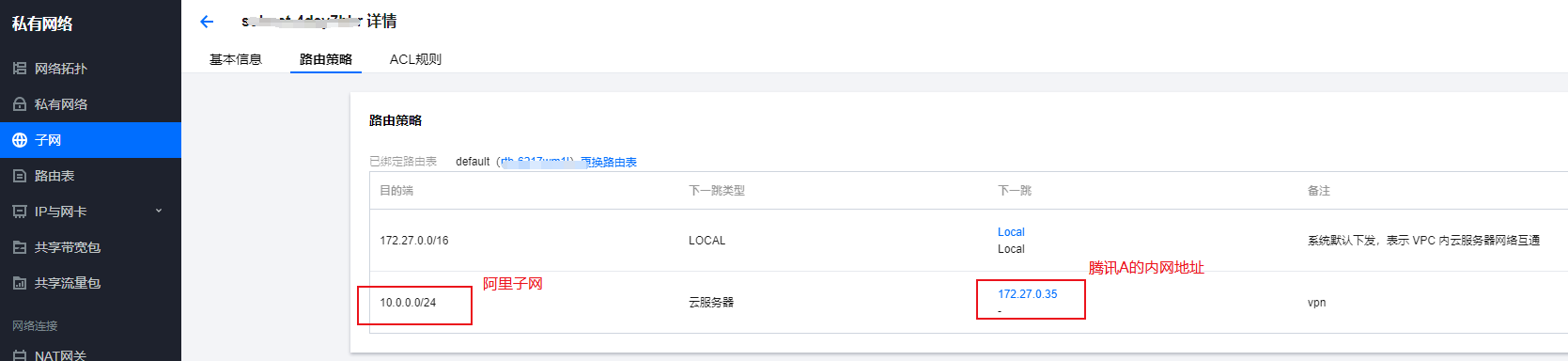
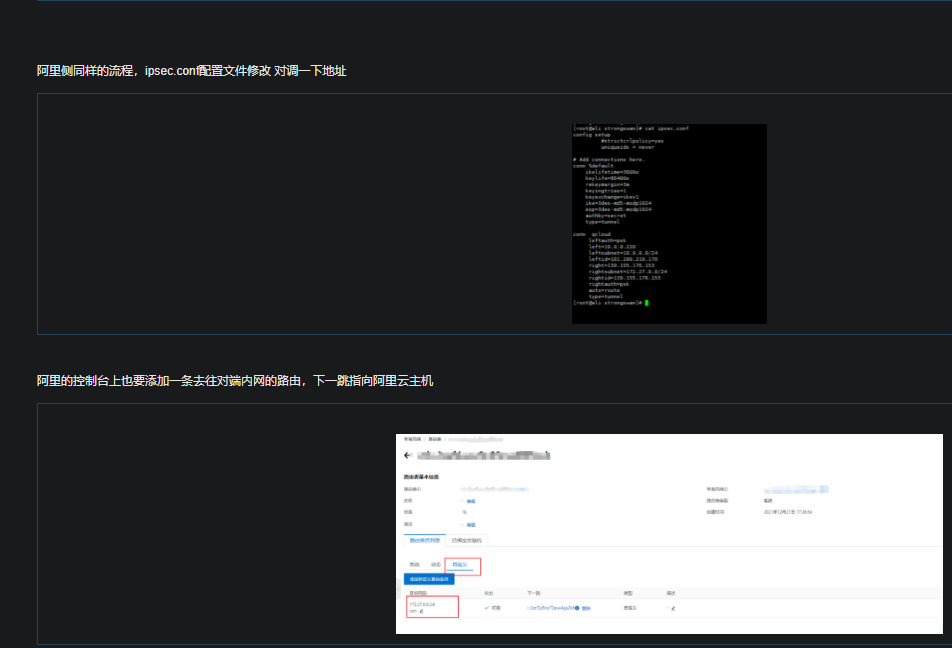
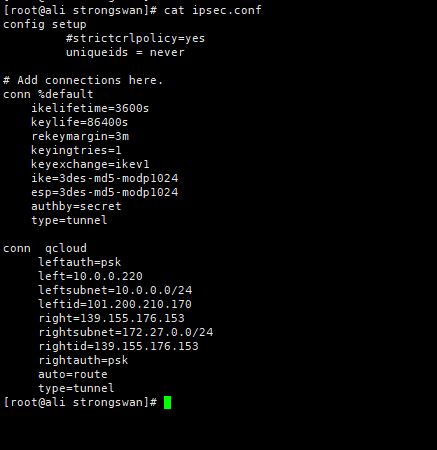
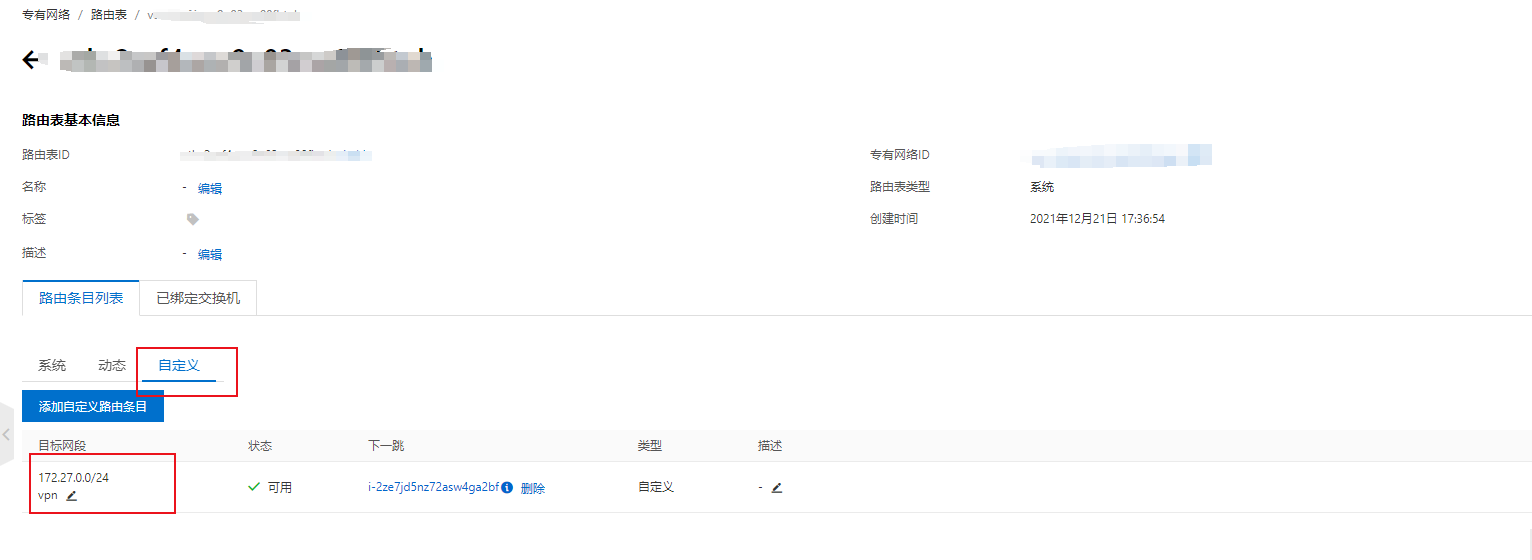
StrongSwan: #------------------------------------------------------------------------------------------------------------- ####################################### ####################################### #------------------------------------------------------------------------------------------------------------- #------------------------------------------------------------------------------------------------------------- # Operations #------------------------------------------------------------------------------------------------------------- IPSec监听在UDP的500和4500两个端口,其中500是用来IKE密钥交换协商,4500的NAT-T是nat穿透的。 ip xfrm policy # 查看路由策略 #------------------------------------------------------------------------------------------------------------- # Compile #------------------------------------------------------------------------------------------------------------- Download: https://www.strongswan.org/download.html Install: https://wiki.strongswan.org/projects/strongswan/wiki/InstallationDocumentation ####################################### ####################################### apt install libgdm-dev libssl-dev libgmp-dev libsystemd-dev ####################################### Configure ####################################### --disable-charon --disable-stoke --disable-scepclient # disable starter, ipsec and the stroke backend ./configure --prefix=/usr/local/strongswan --sysconfdir=/etc/strongswan \ --enable-systemd --enable-shared --enable-openssl --enable-charon --enable-cmd --enable-swanctl \ --with-piddir=/run/strongswan \ --with-charon-udp-port=500 \ --with-charon-natt-port=4500 ####################################### PATH ####################################### cat <<'EOF' > /etc/profile.d/strongswan.sh export STRONGSWAN_HOME=/usr/local/strongswan export PATH=$PATH:$STRONGSWAN_HOME/bin:$STRONGSWAN_HOME/sbin EOF ####################################### ipsec systemd Unit ####################################### cat <<EOF > /etc/systemd/system/strongswan.service [Unit] Description=strongSwan IPsec IKEv1/IKEv2 daemon using ipsec.conf After=network-online.target [Service] ExecStart=/usr/local/strongswan/sbin/ipsec start --nofork ExecReload=/usr/local/strongswan/sbin/ipsec reload StandardOutput=journal Restart=on-abnormal [Install] WantedBy=multi-user.target EOF ####################################### swanctl systemd Unit ####################################### cat <<EOF > /etc/systemd/system/strongswan.service [Unit] Description=strongSwan IPsec IKEv1/IKEv2 daemon using swanctl After=network-online.target [Service] Type=notify ExecStart=/usr/local/strongswan/sbin/charon-systemd ExecStartPost=/usr/local/strongswan/sbin/swanctl --load-all --noprompt ExecReload=/usr/local/strongswan/sbin/swanctl --reload ExecReload=/usr/local/strongswan/sbin/swanctl --load-all --noprompt Restart=on-abnormal [Install] WantedBy=multi-user.target Alias=strongswan-swanctl.service EOF ####################################### Kernel Parameters ####################################### ####################################### Kernel Parameters ####################################### ####################################### Kernel Parameters ####################################### cat <<EOF > /etc/sysctl.d/strongswan.conf #配置转发,默认是0 net.ipv4.ip_forward = 1 #关闭重定向,防止恶意用户可以使用IP重定向来修改远程主机中的路由表 net.ipv4.conf.all.accept_redirects = 0 net.ipv4.conf.all.send_redirects = 0 EOF sysctl --load #------------------------------------------------------------------------------------------------------------- # prerequisites #------------------------------------------------------------------------------------------------------------- RSA认证(PSK跳过) cp cacert.pem /etc/strongswan/ipsec.d/cacerts/ cp server.crt /etc/strongswan/ipsec.d/certs/ cp server.key /etc/strongswan/ipsec.d/private/ cp client.crt /etc/strongswan/ipsec.d/certs/ cp client.key /etc/strongswan/ipsec.d/private/ 101.34.169.85 1.117.55.126 101.35.29.179 #------------------------------------------------------------------------------------------------------------- # /etc/strongswan/ipsec.conf #------------------------------------------------------------------------------------------------------------- ####################################### IKEv1 ####################################### config setup uniqueids=yes | no | never | replace | keep # 允许单账号多终端同时登录 charondebug="ike 2, knl 2, cfg 2, net 2, esp 2, dmn 2, mgr 2" # "all" strictcrlpolicy=yes | ifuri | no cachecrls=no | yes # cached in /etc/ipsec.d/crls/ under a unique file name derived from the certification authority's public key conn %default authby=psk # pubkey | rsasig | ecdsasig | psk | secret | never | xauthpsk | xauthrsasig auto=ignore | add | route | Start # Start The Connection by Default type=tunnel # Type Of Connection. tunnel | transport | transport_proxy | passthrough | drop leftauth=psk rightauth=psk compress=no forceencaps=yes | no # force UDP encapsulation for ESP packets even if no NAT situation is detected fragmentation=yes | accept | force | no # whether to use IKE fragmentation ## IKE ## ike=aes128-sha256-modp3072 # encryption-integrity[-prf]-dhgroup keyexchange=ikev2 # ike | ikev1 | ikev2 ikelifetime=24h # lifetime of keying channel of a connection (ISAKMP or IKE SA) keyingtries=3 # attempts made to negotiate a connection. %forever esp=aes128-sha256-modp3072 # encryption-integrity[-dhgroup][-esnmode] lifetime=2h # a connection (a set of encryption/authentication keys for user packets) last reauth=yes # rekeying of an IKE_SA should also reauthenticate the peer rekey=yes # whether a connection should be renegotiated when it is about to expire ## XAuth ## xauth=server | client # role in the XAuth protocol if activated by authby=xauthpsk or authby=xauthrsasig xauth_identity=<default IKEv1 identify> # identity/username the client uses to reply to an XAuth request ## CA ## also=<name> # includes ca section <name> auto=ignore | add # currently can have either the value ignore (the default) or add cacert=<path> # a path to CA certificate relative to /etc/ipsec.d/cacerts or as an absolute path ## EAP ## eap_identity=<id> | %identify # defines the identity the client uses to reply to an EAP Identity request ## DPD ## Dead Peer Detection dpdaction=none | clear | hold | restart # default is none which disables the active sending of DPD messages. dpddelay=30s dpdtimeout=150s # after which all connections to a peer are deleted in case of inactivity conn site-to-site ## left ## left=192.168.1.1 # NAT场景填内网IP. <ip address> | <fqdn> | %any | <range> | <subnet> leftallowany=yes # making it behave as %any. no leftauth=psk leftca= # distinguished name of a certificate authority. %same leftcert=left.crt # leftcert sets leftid to the distinguished name of the certificate's subject leftid=1.1.1.1 # left participant should be identified for authentication. NAT中填公网IP地址 leftsendcert=ifasked # never | no | ifasked | always | yes leftsubnet=192.168.1.0/24 # private subnet behind the left participant, expressed as network/netmask ## right ## righ=172.16.1.1 | %any righallowany=yes righauth=psk | eap-mschapv2 righca= righcert= rightdns=8.8.8.8,8.8.4.4 righid=2.2.2.2 righsendcert=ifasked righsubnet=172.16.1.0/24 conn ios_cert_authentication # 证书认证 ## phase 1 ## keyexchange=ikev1 ## left ## left=%defaultroute leftauth=pubkey leftsubnet=0.0.0.0/0 leftcert=server.crt ## right ## right=%any rightauth=pubkey rightauth2=xauth rightsourceip=10.31.2.0/24 rightcert=client.crt conn android_xauth_psk # 预共享密钥认证 ## phase 1 ## keyexchange=ikev1 ## left ## left=%defaultroute leftauth=psk leftsubnet=0.0.0.0/0 ## right ## right=%any rightauth=psk rightauth2=xauth rightsourceip=10.31.2.0/24 conn networkmanager-strongswan ## phase 1 ## keyexchange=ikev2 ## left ## left=%defaultroute leftauth=pubkey leftsubnet=0.0.0.0/0 leftcert=server.cert ## right ## right=%any rightauth=pubkey rightsourceip=10.31.2.0/24 rightcert=client.crt leftcert=server.crt leftsendcert=always leftsubnet=10.0.0.0/16 right=%any rightid=%any rightauth=eap-mschapv2 rightsourceip=192.168.0.0/24 rightdns=8.8.8.8 # DNS to be assigned to clients rightsendcert=never eap_identity=%identity # defines the identity the client uses to reply to an EAP Identity request. #------------------------------------------------------------------------------------------------------------- # /etc/strongswan/ipsec.secrets #------------------------------------------------------------------------------------------------------------- : RSA server.key : PSK "YourPSK" UserName1 %any : XAUTH "Password1" UserName2 %any : XAUTH "Password2" UserName1 %any : EAP "Password1" UserName2 %any : EAP "Password2" #本地公网出口IP #对端公网出口IP #双方约定的秘钥 47.101.219.25 116.236.134.26 : PSK 'perpetual' # site-to-site : PSK "YourPSK" <=> %any %any : PSK "YourPSK" Host Peer : METHOD <server.key|PSK|Password> <password_of_server.key> #------------------------------------------------------------------------------------------------------------- # /etc/strongswan/strongswan.conf #------------------------------------------------------------------------------------------------------------- charon { filelog { /var/log/strongswanlog { append = no default = 1 flush_line = yes ike_name = yes time_format = %b %e %T } } load_modular = yes compress=yes plugins { include strongswan.d/charon/*.conf } dns1=8.8.8.8 dns2=8.8.4.4 } include strongswan.d/*.conf





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 单元测试从入门到精通
· 上周热点回顾(3.3-3.9)
· winform 绘制太阳,地球,月球 运作规律