OpenSSL常用命令
查看证书
openssl x509 -in cacert.pem -text -noout # PEM
openssl x509 -in cacert.der -inform der -text -noout # DER (distinguished encoding rule)
查看私钥
openssl rsa -in cakey.pem -text -noout # PEM
openssl rsa -in cakey.der -inform der -text -noout # DER
查看CSR
openssl req -in ca.csr -text -noout # PEM
openssl req -in ca.csr -inform der -text -noout # DER
转换证书
openssl x509 -in cacert.pem -out cacert.der -outform der
openssl x509 -in cacert.der -inform der -out cacert.pem -outform pem
转换私钥
openssl rsa -in cakey.pem -out cakey.der -outform der
openssl rsa -in cakey.der -inform der -out cakey.pem -outform pem
转换CSR
openssl req -in ca.csr -out ca.csr -outform der
openssl req -in ca.csr -inform der -out ca.csr -outform pem
利用-addext添加扩展
man openssl
查看req子命令
man req man openssl-req
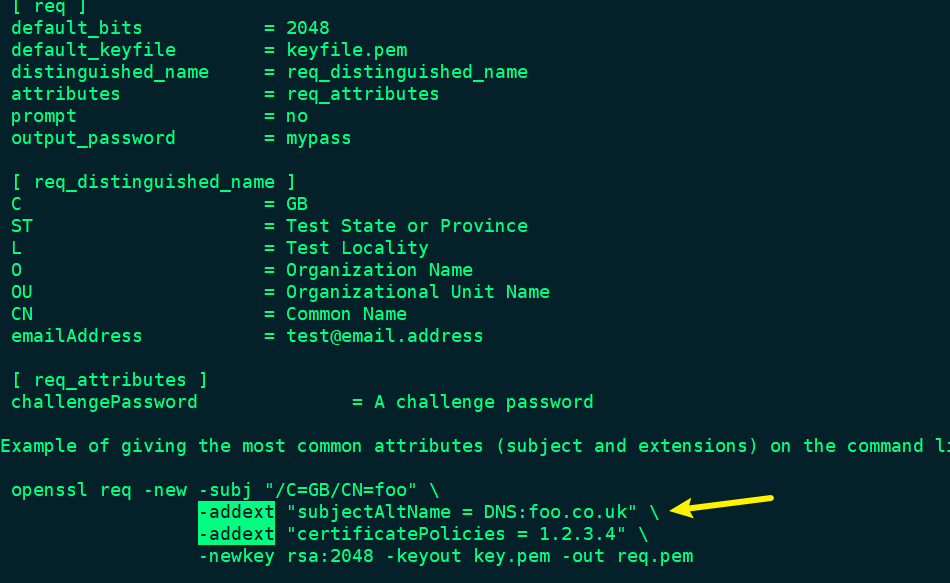
openssl req -new -x509 -nodes -out allusion.crt -days 3650 -sha512 \
-newkey rsa:2048 -keyout allusion.key \
-subj '/C=US/ST=America/L=New York/O=IBM/OU=DevOps/CN=IBM/emailAddress=b@b.co' \
-addext 'subjectAltName=DNS:localhost, IP:127.0.0.1' \
-addext 'certificatePolicies= 1.2.3.4'
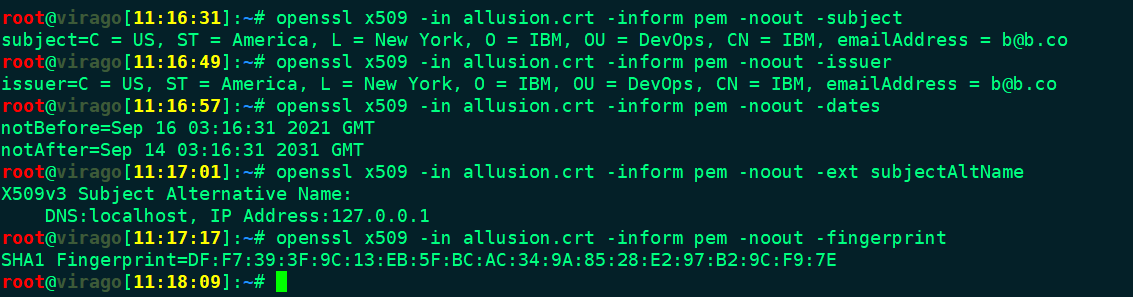
RHEL系生成证书
openssl.cnf

HOME = .
oid_section = new_oids
openssl_conf = default_modules
[ default_modules ]
ssl_conf = ssl_module
[ ssl_module ]
system_default = crypto_policy
[ crypto_policy ]
.include = /etc/crypto-policies/back-ends/opensslcnf.config
[ new_oids ]
tsa_policy1 = 1.2.3.4.1
tsa_policy2 = 1.2.3.4.5.6
tsa_policy3 = 1.2.3.4.5.7
[ ca ]
default_ca = CA_default # The default ca section
[ CA_default ]
dir = /etc/pki/CA # Where everything is kept
certs = $dir/certs # Where the issued certs are kept
crl_dir = $dir/crl # Where the issued crl are kept
database = $dir/index.txt # database index file.
#unique_subject = no # Set to 'no' to allow creation of several certs with same subject.
new_certs_dir = $dir/newcerts # default place for new certs.
certificate = $dir/cacert.pem # The CA certificate
serial = $dir/serial # The current serial number
crlnumber = $dir/crlnumber # the current crl number must be commented out to leave a V1 CRL
crl = $dir/crl.pem # The current CRL
private_key = $dir/private/cakey.pem # The private key
x509_extensions = usr_cert # The extensions to add to the cert
name_opt = ca_default # Subject Name options
cert_opt = ca_default # Certificate field options
default_days = 365 # how long to certify for
default_crl_days = 30 # how long before next CRL
default_md = sha256 # use SHA-256 by default
preserve = no # keep passed DN ordering
policy = policy_match
[ policy_match ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ policy_anything ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ req ]
default_bits = 2048
default_md = sha256
default_keyfile = privkey.pem
distinguished_name = req_distinguished_name
attributes = req_attributes
x509_extensions = v3_ca # The extensions to add to the self signed cert
string_mask = utf8only
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_default = CN
countryName_min = 2
countryName_max = 2
stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = Apparition
localityName = Locality Name (eg, city)
localityName_default = Abdication
0.organizationName = Organization Name (eg, company)
0.organizationName_default = IBM
organizationalUnitName = Organizational Unit Name (eg, section)
organizationalUnitName_default = DevOps
commonName = Common Name (eg, your name or your server\'s hostname)
commonName_max = 64
emailAddress = Email Address
emailAddress_max = 64
emailAddress_default = admin@ibm.com
[ req_attributes ]
challengePassword = A challenge password
challengePassword_min = 1
challengePassword_max = 20
unstructuredName = An optional company name
[ usr_cert ]
basicConstraints = CA:FALSE
nsComment = "OpenSSL Generated Certificate"
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid, issuer
[ v3_req ]
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
[ v3_ca ]
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always, issuer
basicConstraints = critical, CA:true
[ crl_ext ]
authorityKeyIdentifier = keyid:always
[ proxy_cert_ext ]
basicConstraints = CA:FALSE
nsComment = "OpenSSL Generated Certificate"
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid, issuer
proxyCertInfo = critical, language:id-ppl-anyLanguage, pathlen:3, policy:foo
[ tsa ]
default_tsa = tsa_config1 # the default TSA section
[ tsa_config1 ]
dir = /etc/pki/CA # TSA root directory
serial = $dir/tsaserial # The current serial number (mandatory)
crypto_device = builtin # OpenSSL engine to use for signing
signer_cert = $dir/tsacert.pem # The TSA signing certificate (optional)
certs = $dir/cacert.pem # Certificate chain to include in reply (optional)
signer_key = $dir/private/tsakey.pem # The TSA private key (optional)
signer_digest = sha256 # Signing digest to use. (Optional)
default_policy = tsa_policy1 # Policy if request did not specify it (optional)
other_policies = tsa_policy2, tsa_policy3 # acceptable policies (optional)
digests = sha1, sha256, sha384, sha512 # Acceptable message digests (mandatory)
accuracy = secs:1, millisecs:500, microsecs:100 # (optional)
clock_precision_digits = 0 # number of digits after dot. (optional)
ordering = yes # Is ordering defined for timestamps? (optional, default: no)
tsa_name = yes # Must the TSA name be included in the reply? (optional, default: no)
ess_cert_id_chain = no # Must the ESS cert id chain be included? (optional, default: no)
ess_cert_id_alg = sha256 # algorithm to compute certificate identifier (optional, default: sha1)
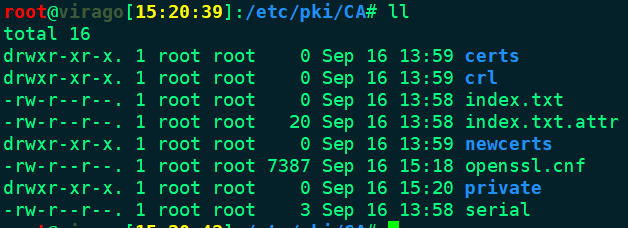
Prepare directory & files
mkdir -pv /etc/pki/CA/{certs,newcerts,private,csr}
touch index.txt
echo 'unique_subject = no' > index.txt.attr
ehco 01 > serial
Prepare rootCA
openssl genrsa -des3 -out private/cakey.pem 2048
openssl req -new -x509 -nodes -days 3650 -key private/cakey.pem -out cacert.pem \
-subj '/C=CN/ST=Apparition/L=Abdication/O=IBM/OU=DevOps/CN=rootCA/emailAddress=admin@ibm.com/'
openssl req -new -x509 -nodes -days 3650 -key private/cakey.pem -out cacert.pem -config openssl.cnf
Generate secondaryCA
openssl genrsa -des3 -out private/secondaryCA.key 2048
openssl rsa -in private/secondaryCA.key -out private/secondaryCA.key
openssl req -new -key private/secondaryCA.key -out csr/secondaryCA.csr \
-subj '/C=CN/ST=Apparition/L=Abdication/O=IBM/OU=DevOps/CN=secondaryCA/emailAddress=admin@ibm.com/'
openssl ca -in csr/secondaryCA.csr -out certs/secondaryCA.crt -days 3650 \
-cert cacert.pem -keyfile private/cakey.pem \
-config openssl.cnf -extensions v3_ca
Generate server certificate
openssl req -new -nodes -newkey rsa:2048 -keyout private/server.key -out csr/server.csr \
-subj '/C=CN/ST=Apparition/L=Abdication/O=IBM/OU=DevOps/CN=server/emailAddress=admin@ibm.com/'
openssl ca -in csr/server.csr -out certs/server.crt -days 3650 \
-cert certs/secondaryCA.crt -keyfile private/secondaryCA.key \
-config openssl.cnf
Revoke server certificate
echo 01 > crlnumber
openssl ca -revoke certs/server.crt -cert cacert.pem -keyfile private/cakey.pem -config openssl.cnf
# generate crl
openssl ca -gencrl -out crl.crl -cert cacert.pem -keyfile private/cakey.pem -config openssl.cnf
openssl crl -in crl.crl -text -noout
pkcs12证书
cat certs/secondaryCA cacert.pem > ca-chain.crt # 不包含CA证书链 openssl pkcs12 -export \ -in certs/server.crt -inkey private/server.key -nodes \ -out server.pfx -passout pass:123321 # 包含CA证书链 openssl pkcs12 -export -chain -CAca ca-chain.crt \ -in certs/server.crt -inkey private/server.key -nodes \ -out server.pfx -passout pass:123321 openssl pkcs12 -in ca-bundle.p12 -nocerts -nodes -out ca.key # 提取ca私钥 openssl pkcs12 -in ca-bundle.p12 -clcerts -nokeys -out ca.crt # 仅输出ca证书 openssl pkcs12 -in ca-bundle.p12 -info -noout



 浙公网安备 33010602011771号
浙公网安备 33010602011771号