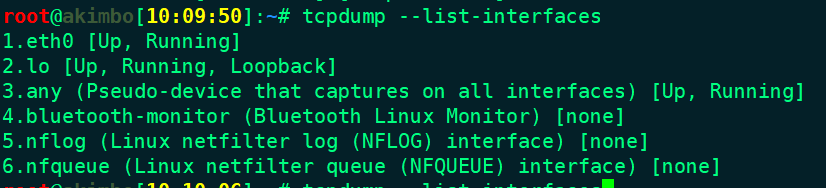
Instrument: tcpdump
- --list-interfaces 列出可用接口
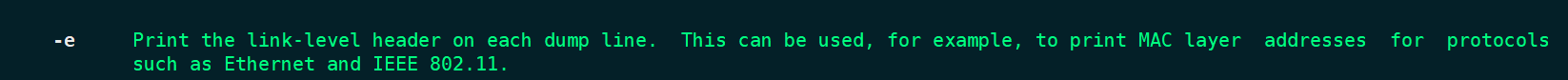
- -e
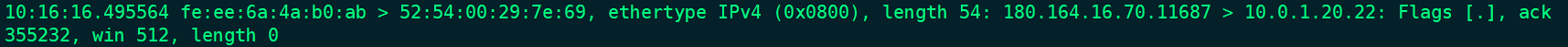
包含链路层mac
- tcpdump -i interface -nc 10 ether dst MAC 使用MAC地址进行抓包,加入ether修饰
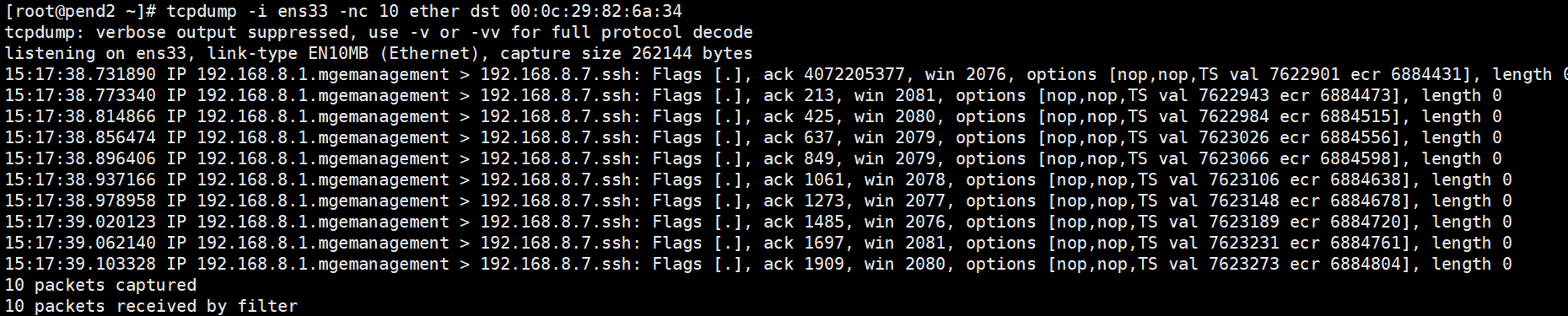
win表示发送方窗口大小,ack213表示对序列号213的包进行响应
Flags表示tcp的标志位信息
. ACK S SYN F FIN P PUSH R RSTtcpdump 支持逻辑运算
-
not and ortcpdump -i ens33 -nvc 10 not ether host 00:0c:29:82:6a:34
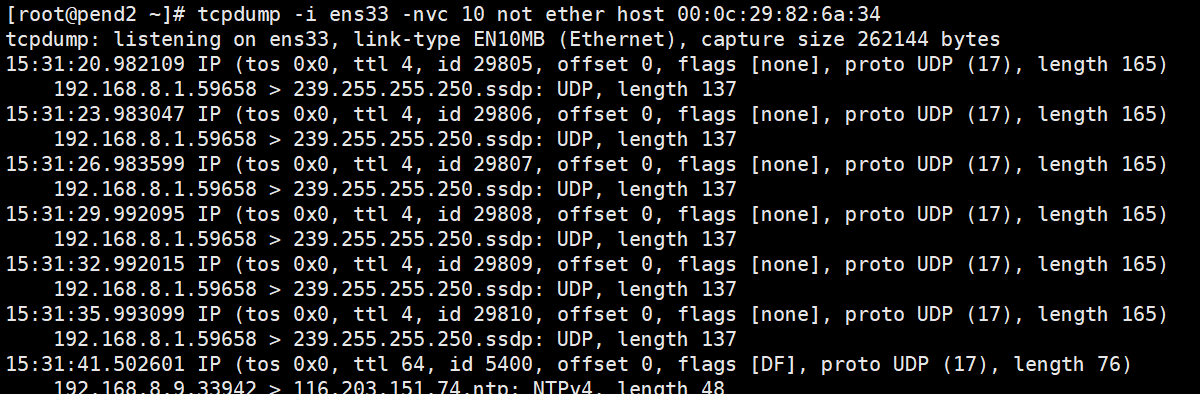
- tcpdump -i ens33 -X broadcast 广播包的抓取
- tcpdump -i ens33 -nvc 10 ip broadcast UDP进行的广播包
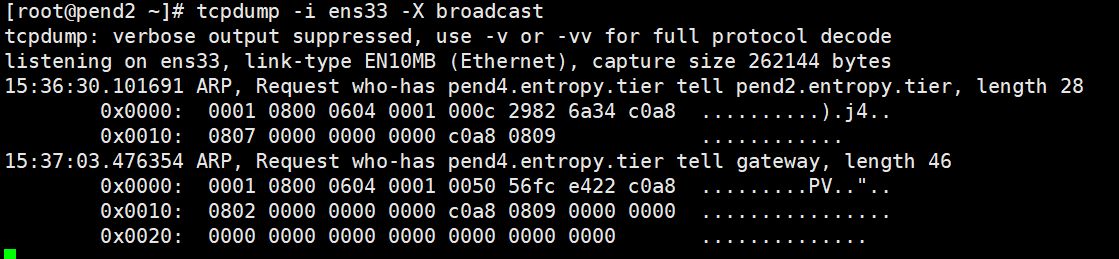
- tcpdump -i ens33 -nvc 10 ip multicast 多播包抓取
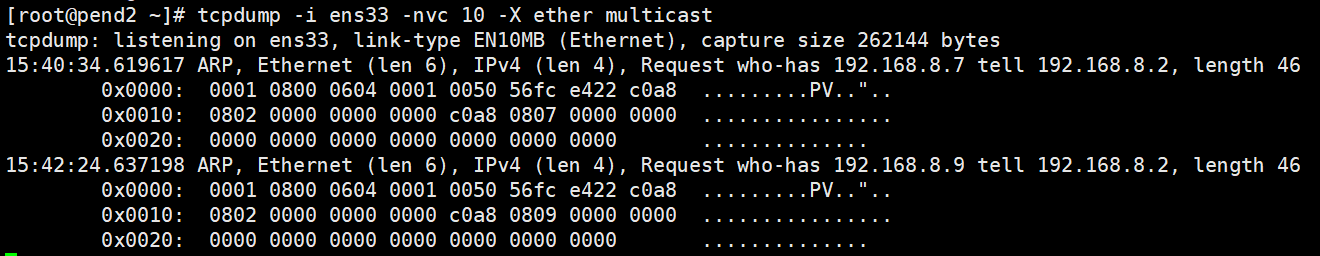
- tcpdump -i ens33 -nvc 10 dst net 192.168.8.0/24 and tcp and ip and src port 8080
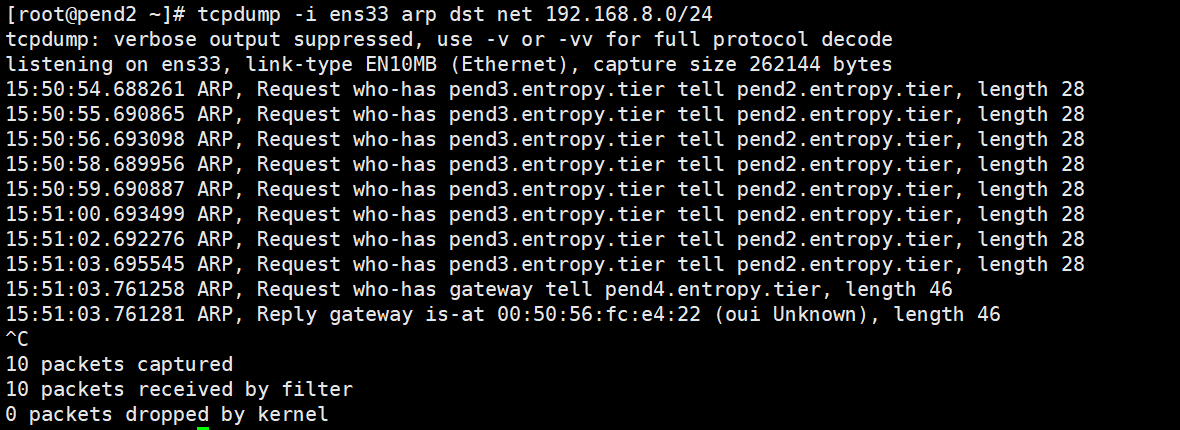
[root@pend2 ~]# tcpdump -i ens33 -nvc 10 dst net 192.168.8.0/24 and ip proto '\tcp' and src port 8080 tcpdump: listening on ens33, link-type EN10MB (Ethernet), capture size 262144 bytes 15:46:56.412210 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 60) 192.168.8.7.webcache > 192.168.8.1.10464: Flags [S.], cksum 0x9187 (incorrect -> 0xc48e), seq 2953867736, ack 2874435796, win 28960, options [mss 1460,sackOK,TS val 8642153 ecr 9380586,nop,wscale 7], length 0 15:46:56.414122 IP (tos 0x0, ttl 64, id 44978, offset 0, flags [DF], proto TCP (6), length 52) 192.168.8.7.webcache > 192.168.8.1.10464: Flags [.], cksum 0x917f (incorrect -> 0x6258), ack 307, win 235, options [nop,nop,TS val 8642155 ecr 9380590], length 0 15:46:56.456616 IP (tos 0x0, ttl 64, id 44979, offset 0, flags [DF], proto TCP (6), length 1581) 192.168.8.7.webcache > 192.168.8.1.10464: Flags [P.], cksum 0x9778 (incorrect -> 0x0e28), seq 1:1530, ack 307, win 235, options [nop,nop,TS val 8642198 ecr 9380590], length 1529: HTTP, length: 1529 HTTP/1.1 403 Forbidden Date: Sat, 04 Jul 2020 07:46:56 GMT X-Content-Type-Options: nosniff Set-Cookie: JSESSIONID.4dc69a9a=node0xq21sxjijqq7e9iekqtmn4ub1.node0; Path=/; HttpOnly Expires: Thu, 01 Jan 1970 00:00:00 GMT Content-Type: text/html;charset=utf-8 X-Hudson: 1.395 X-Jenkins: 2.235.1 X-Jenkins-Session: 95aeabfd X-You-Are-Authenticated-As: anonymous X-You-Are-In-Group-Disabled: JENKINS-39402: use -Dhudson.security.AccessDeniedException2.REPORT_GROUP_HEADERS=true or use /whoAmI to diagnose X-Required-Permission: hudson.model.Hudson.Read X-Permission-Implied-By: hudson.security.Permission.GenericRead X-Permission-Implied-By: hudson.model.Hudson.Administer Content-Length: 793 Server: Jetty(9.4.27.v20200227) <html><head><meta http-equiv='refresh' content='1;url=/login?from=%2F'/><script>window.location.replace('/login?from=%2F');</script></head><body style='background-color:white; color:white;'> Authentication required <!-- You are authenticated as: anonymous Groups that you are in: Permission you need to have (but didn't): hudson.model.Hudson.Read ... which is implied by: hudson.security.Permission.GenericRead ... which is implied by: hudson.model.Hudson.Administer --> </body></html> [!http] 15:46:56.514246 IP (tos 0x0, ttl 64, id 44981, offset 0, flags [DF], proto TCP (6), length 52) 192.168.8.7.webcache > 192.168.8.1.10464: Flags [.], cksum 0x917f (incorrect -> 0x59eb), ack 728, win 243, options [nop,nop,TS val 8642255 ecr 9380689], length 0 15:46:56.584110 IP (tos 0x0, ttl 64, id 44982, offset 0, flags [DF], proto TCP (6), length 1696) 192.168.8.7.webcache > 192.168.8.1.10464: Flags [P.], cksum 0x97eb (incorrect -> 0x534f), seq 1530:3174, ack 728, win 243, options [nop,nop,TS val 8642325 ecr 9380689], length 1644: HTTP, length: 1644 HTTP/1.1 200 OK Date: Sat, 04 Jul 2020 07:46:56 GMT X-Content-Type-Options: nosniff Content-Type: text/html;charset=utf-8 Expires: 0 Cache-Control: no-cache,no-store,must-revalidate X-Hudson: 1.395 X-Jenkins: 2.235.1 X-Jenkins-Session: 95aeabfd X-Frame-Options: sameorigin Content-Encoding: gzip X-Instance-Identity: MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAm4q5JmYrPCHXIARHK7WOVJAKV6p2oQwE6VXJoxAd511wAw7UHc/eyuJjkZenTv83WumXZh9YTw30NZEck04C8/Nl8An0tcZtityzuWOYk/KN7hHBKg9KDa3h7krLZ2JL6Q0RY4a/NUOuCFNudnJHLMvcFOfzujOb7oMgKodt+mkVSdMMiMG9L7dsetpOR3fTDoOUZmLXy9+dOjuCu0Z2nTZkWnNVMT9gjcAHdAnjGZs+LHIGZqXn82HCzBFpZ3Vx7XeU/8c77uCV7hS9rTlmRh60Dhu4JYQNg3WWQH+d3vrkANXjFWRGEQfnVYHipSSBSrNw3Jo1WjhqPWZFt+uTrwIDAQAB Content-Length: 866 Server: Jetty(9.4.27.v20200227) 15:46:56.596696 IP (tos 0x0, ttl 64, id 44984, offset 0, flags [DF], proto TCP (6), length 52) 192.168.8.7.webcache > 192.168.8.1.10464: Flags [.], cksum 0x917f (incorrect -> 0x5132), ack 1149, win 252, options [nop,nop,TS val 8642338 ecr 9380765], length 0 15:46:56.596956 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 60) 192.168.8.7.webcache > 192.168.8.1.10466: Flags [S.], cksum 0x9187 (incorrect -> 0x79ab), seq 2796501852, ack 2497448090, win 28960, options [mss 1460,sackOK,TS val 8642338 ecr 9380770,nop,wscale 7], length 0 15:46:56.597004 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 60) 192.168.8.7.webcache > 192.168.8.1.10467: Flags [S.], cksum 0x9187 (incorrect -> 0x7a1b), seq 4193343063, ack 1964161461, win 28960, options [mss 1460,sackOK,TS val 8642338 ecr 9380770,nop,wscale 7], length 0 15:46:56.601560 IP (tos 0x0, ttl 64, id 35198, offset 0, flags [DF], proto TCP (6), length 52) 192.168.8.7.webcache > 192.168.8.1.10467: Flags [.], cksum 0x917f (incorrect -> 0x176b), ack 428, win 235, options [nop,nop,TS val 8642342 ecr 9380773], length 0 15:46:56.601632 IP (tos 0x0, ttl 64, id 58491, offset 0, flags [DF], proto TCP (6), length 52) 192.168.8.7.webcache > 192.168.8.1.10466: Flags [.], cksum 0x917f (incorrect -> 0x16fb), ack 428, win 235, options [nop,nop,TS val 8642342 ecr 9380773], length 0 10 packets captured 10 packets received by filter 0 packets dropped by kernel - tcpdump -i ens33 arp dst net 192.168.8.0/24 进行arp报文抓取
- 常用组合条件
dst host ip src host ip host ip dst net cidr src net cidr net cidr - HTTP报文抓取 -A Print each packet (minus its link level header) in ASCII. Handy for capturing web pages.
tcpdump -i lo port 80 -s0 -A





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· SQL Server 2025 AI相关能力初探
· Linux系列:如何用 C#调用 C方法造成内存泄露
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 单元测试从入门到精通
· 上周热点回顾(3.3-3.9)
· winform 绘制太阳,地球,月球 运作规律