Let’s Encrypt申请泛域名证书
域名分为主域名 test.com 和泛域名 *.test.com
如果又很多子域名,每个都要配置证书。
这也太麻烦了。
所以这次我们来学习 如何搞泛域名证书。
申请证书
执行证书生成命令,
过程中根据命令提示,去云服务商后台增加一条dns,并将certbot生成的参数填写到dns配置的相关位置(不要执行一下代码)。
certbot certonly -d *.dingshaohua.com --manual --preferred-challenges dns
按照提示,在你的域名服务商处,添加对应的 DNS TXT 解析记录
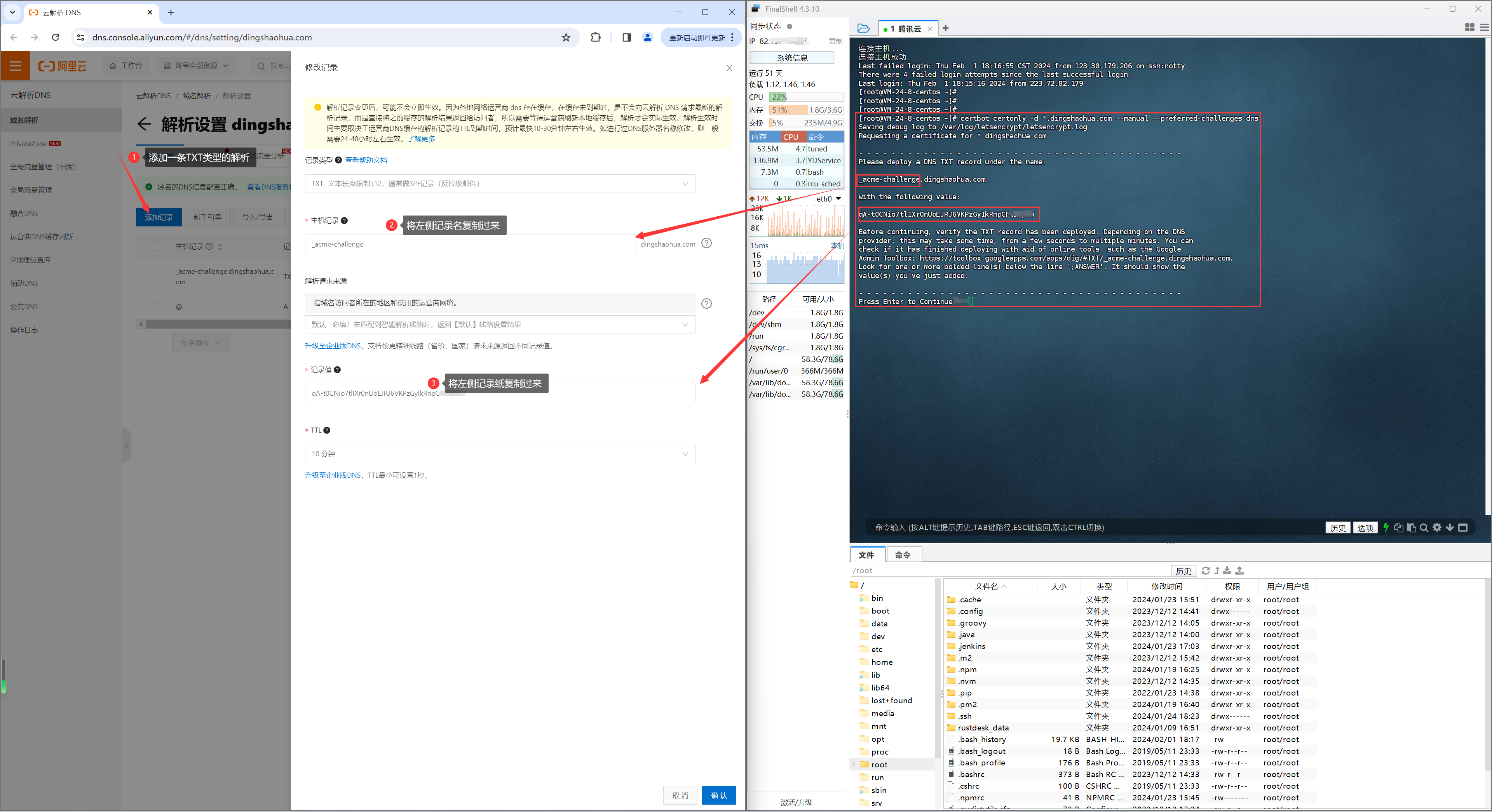
为什么certbot 需要你在云服务商增加dns,还不是为了证明这个域名是你所有权的
再回车继续,证书就生成了。
Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/dingshaohua.com/fullchain.pem
Key is saved at: /etc/letsencrypt/live/dingshaohua.com/privkey.pem
This certificate expires on 2024-05-01.
These files will be updated when the certificate renews.
NEXT STEPS:
- This certificate will not be renewed automatically. Autorenewal of --manual certificates requires the use of an authentication hook script (--manual-auth-hook) but one was not provided. To renew this certificate, repeat this same certbot command before the certificate's expiry date.
通配符证书只是针对二级域名
注意 Let’s encrypt通配符证书只是针对二级域名,并不能针对主域名,如*.dingshaohua.com和dingshaohua.com 被认为是两个域名,在申请的时候需要注意都要申请(不用担心 生成的证书仍然只有一个 不会有几个域名就会有几个) (执行这个!!!)。
certbot certonly -d "*.dingshaohua.com" -d "dingshaohua.com" --manual --preferred-challenges dns
使用证书
首先,你需要在域名服务商处,提前配置好域名解析(这个跟证书无关,就算是http方式访问你也的配置)。
其次,在nginx配置配置,比如 我有两个域名想使用这个证书dingshaohua.com、a.dingshaohua.com,那么配置如下即可
# dingshaohua.com
server {
listen 80;
server_name dingshaohua.com;
rewrite ^(.*) https://$server_name$1 permanent;
}
server {
# nginx使用虚拟主机来配置站点:每个虚拟主机使用server { } 来配置
# listen用来配置监听端口,server_name为虚拟主机服务名称
listen 443 ssl;
server_name dingshaohua.com;
# 证书位置
ssl_certificate /etc/letsencrypt/live/dingshaohua.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/dingshaohua.com/privkey.pem;
#证书校验(通用)
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
# 路由
location / {
root /home/webroot/book-ding;
try_files $uri $uri/ /index.html;
}
}
# a.dingshaohua.com
server {
listen 80;
server_name a.dingshaohua.com;
rewrite ^(.*) https://$server_name$1 permanent;
}
server {
listen 443 ssl;
server_name a.dingshaohua.com;
ssl_certificate /etc/letsencrypt/live/dingshaohua.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/dingshaohua.com/privkey.pem;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
root /home/abc;
}
}
续签
# 根据提示处理
certbot certonly -d *.klvchen.com --manual --preferred-challenges dns
# 或
certbot renew
# 或
certbot renew --quiet
一些参考阅读
certbot命令参数含义
https://blog.csdn.net/neizhiwang/article/details/105605967
https://www.4spaces.org/217.html
https://zhuanlan.zhihu.com/p/627526278
什么是通配符证书
https://www.zhihu.com/question/602288859/answer/3109842778
证明Let’s encrypt通配符证书只是针对二级域名,并不能针对主域名
https://cloud.tencent.com/developer/article/1915432?areaId=106001
https://weibo.com/6916341052/JhAkDDNik
https://www.5288z.com/2267.html
https://blog.csdn.net/owenzhang24/article/details/122234156


