扫描器开发 - 2
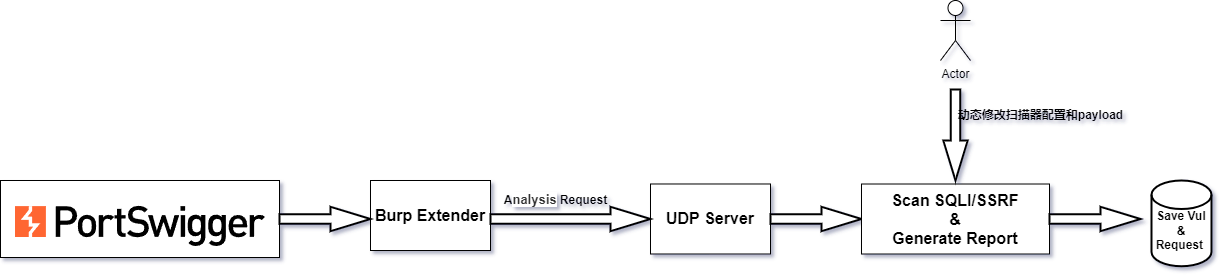
扫描器整体架构图
重复请求去重
使用md5(uri+content_type+params(不包括类似csrftoken参数)+body)
class DeDuplicate(object):
def __init__(self,duplicate_list,logger):
self.duplicate_list = duplicate_list
self.logger = logger
self.duplicate_params = Config.get_instance().get("app.DUPLICATE_PARAMS").split('|')
self.duplicate_length = int(Config.get_instance().get('app.DUPLICATE_LEGNTH'))
self.black_host_list = Config.get_instance().get("app.BLACK_HOSTS").split('|')
def getHash(self,hashString):
m = hashlib.md5(hashString.encode(encoding='utf-8'))
return m.hexdigest() # 转化为16进制打印md5值
def pop_param(self, param_list):
"""
去掉黑名单的headers
:param headers_dict:
:return:
"""
keys = param_list.keys()
for key in list(keys):
if key in self.duplicate_params:
param_list.pop(key)
return param_list
def query(self,request,http):
host = request['host']
#print(host)
#print(self.black_host_list)
if host in self.black_host_list:
self.logger.info('黑名单host, pass')
return False
uri = http.parseUrl(request['full_url'])
content_type = request['content_type']
param_in_body = request['param_in_body']
param_in_url = request['param_in_url']
try:
#self.logger.info(request['body'])
body = json.loads(request['body'])
except:
body = {}
tmpObj = [param_in_body, param_in_url,body]
listobj = list(map(self.pop_param, tmpObj))
hashString = uri + str(content_type) + ''.join([str(i) for i in listobj])
#self.logger.info("----" + hashString)
md5 = self.getHash(hashString)
if md5 in self.duplicate_list:
self.logger.info('重复请求')
return False
elif len(self.duplicate_list)<=self.duplicate_length:
self.duplicate_list.append(md5)
return True
else:
self.duplicate_list.clear()
self.logger.info('exceed max length ,clear md5 list')
self.duplicate_list.append(md5)
return True
数字型SQL注入判断

order by 注入判断

字符型注入(包括单引号、双引号)注入判断

- 双引号字符型注入同理
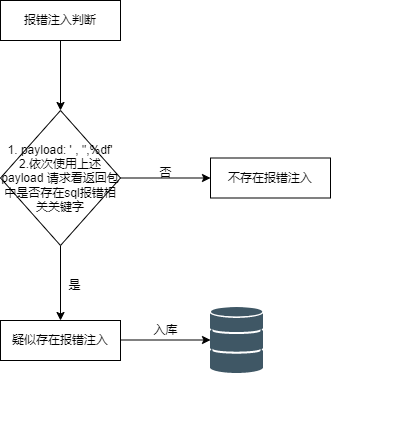
报错注入判断
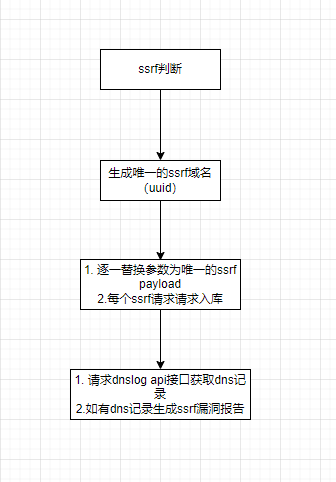
ssrf探测
扫描器配置
[app]
BLACK_HEADERS = content-length|if-modified-since|if-none-match|pragma|cache-control|{发送请求前需要去除的参数}
BLACK_PARAMS = nonce|ts|signature|salt|{不进行漏洞探测的参数}
SSRF_DNSLOG = {DNSLOG}
SSRF_API_KEY = {API_KEY}
PROXY = NO
PROXY_HTTP = http://127.0.0.1:8080
REDIRECT = false
TIMEOUT = 60
REPLACE_STATUS = YES
SSRF_TENCENT = YES
DUPLICATE_PARAMS = nonce|ts|signature|{去重干扰参数}
DUPLICATE_LEGNTH = 5000
BLACK_HOSTS = pingfore.qq.com|www.baidu.com|{不扫描的域名}
[mysql]
HOST = {host}
PORT = {port}
USERNAME = {username}
PASSWD = {pass}
DB = {db_name}
CHARSETS = utf8
[score]
SIMILAR = 0.88
COSINSCORE = 75
[REPLACE]
REGEX = "t":\d{10}|"current":\d{10}|"reqData":".*?"|"skey":".*?"|{使用正则配置需要替换为空的内容,排除动态页面内容干扰注入判断}
实战成果
TSRC 上 95% 以上都是扫描器识别到的注入




 浙公网安备 33010602011771号
浙公网安备 33010602011771号