第五届“强网杯”全国网络安全挑战赛 青少年专项赛选拔赛WP
misc
签到
直接截图
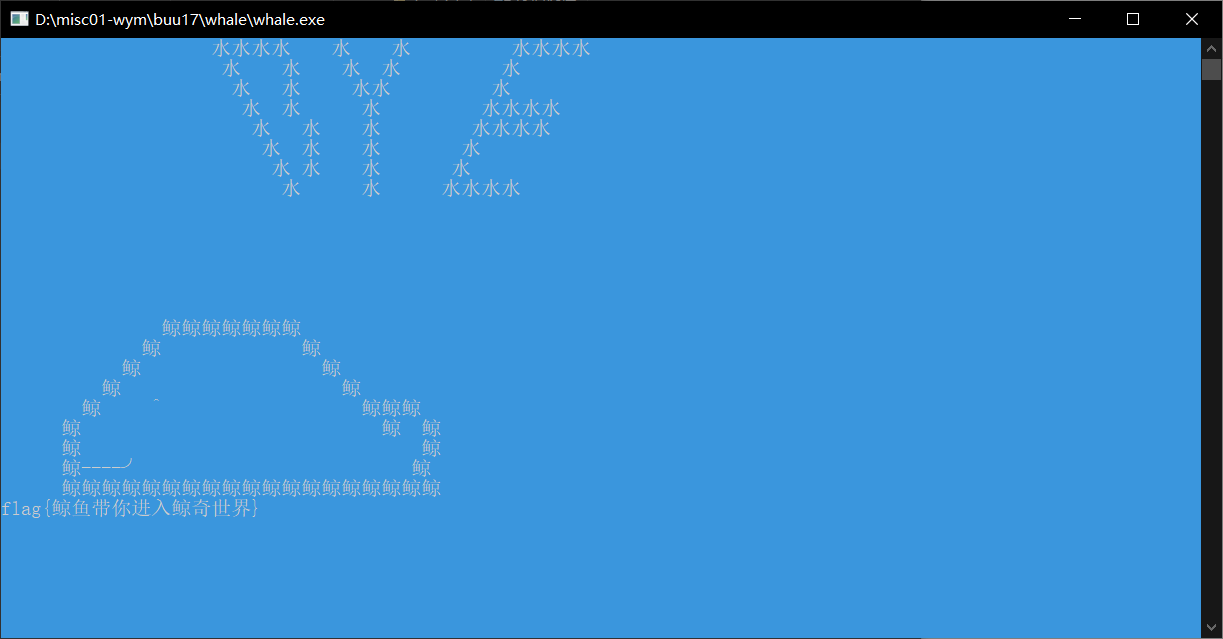
拼图
垃圾题目,用之前比赛的脚本,但是拼出来明明觉得是flag,但是就是不对
#!/usr/bin/python
# -*- coding: UTF-8 -*-
import cv2
from PIL import Image
import numpy as np
import os
import shutil
import threading
# 读取目标图片
source = cv2.imread(r"D:\misc01-wym\buu17\flag\1\1.jpg")
# 拼接结果
target = Image.fromarray(np.zeros(source.shape, np.uint8))
# 图库目录
dirs_path = r"D:\misc01-wym\buu17\flag\1\png"
# 差异图片存放目录
dst_path = r"D:\misc01-wym\buu17\flag\1"
def match(temp_file):
# 读取模板图片
template = cv2.imread(temp_file)
# 获得模板图片的高宽尺寸
theight, twidth = template.shape[:2]
# 执行模板匹配,采用的匹配方式cv2.TM_SQDIFF_NORMED
result = cv2.matchTemplate(source, template, cv2.TM_SQDIFF_NORMED)
# 归一化处理
cv2.normalize(result, result, 0, 1, cv2.NORM_MINMAX, -1)
# 寻找矩阵(一维数组当做向量,用Mat定义)中的最大值和最小值的匹配结果及其位置
min_val, max_val, min_loc, max_loc = cv2.minMaxLoc(result)
target.paste(Image.fromarray(template), min_loc)
return abs(min_val)
class MThread(threading.Thread):
def __init__(self, file_name):
threading.Thread.__init__(self)
self.file_name = file_name
def run(self):
real_path = os.path.join(dirs_path, k)
rect = match(real_path)
if rect > 6e-10:
print(rect)
shutil.copy(real_path, dst_path)
count = 0
dirs = os.listdir(dirs_path)
threads = []
for k in dirs:
if k.endswith('png'):
count += 1
print("processing on pic" + str(count))
mt = MThread(k)
mt.start()
threads.append(mt)
else:
continue
# 等待所有线程完成
for t in threads:
t.join()
target.show()
target.save(r"D:\misc01-wym\buu17\flag\1")
得到
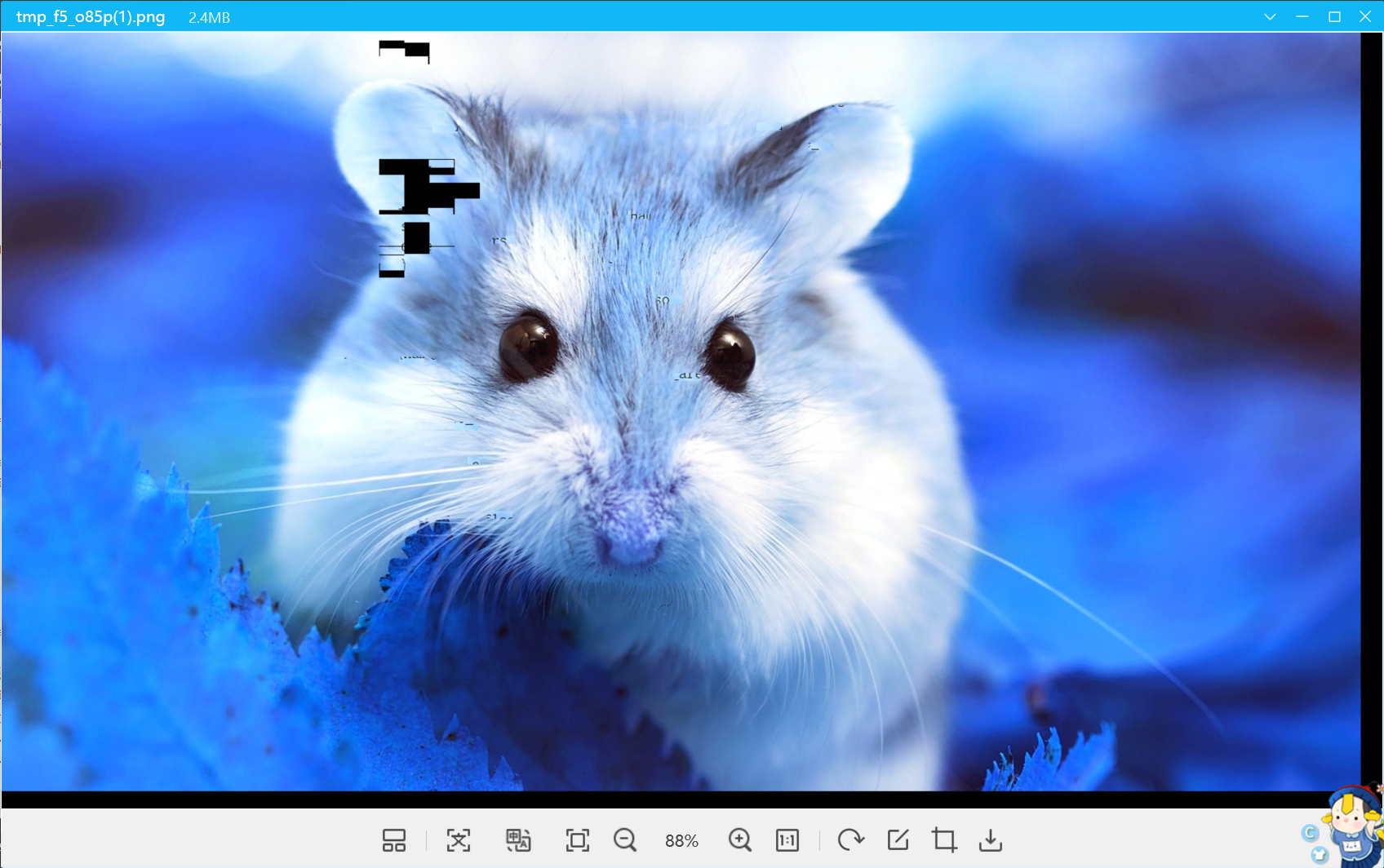
然后参考一下,手橹
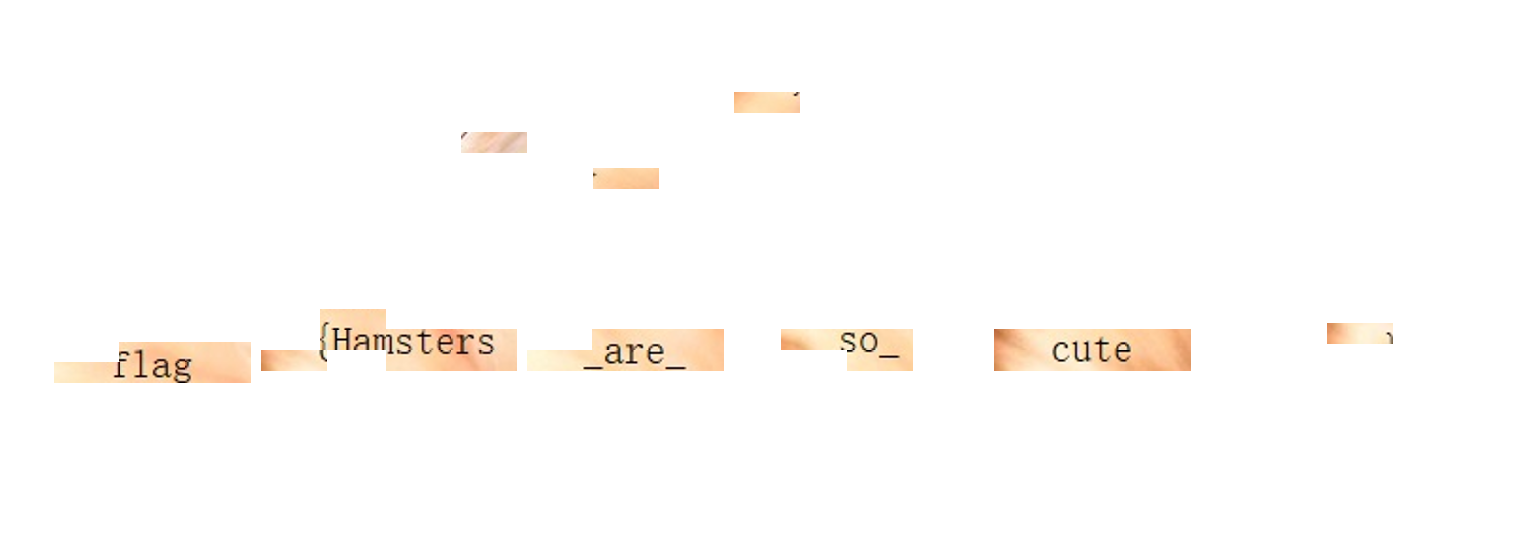
但是flag是错误的,等到比赛完再去看吧
迷人的表情
首先,用军刀中的magic检查一下base64代码
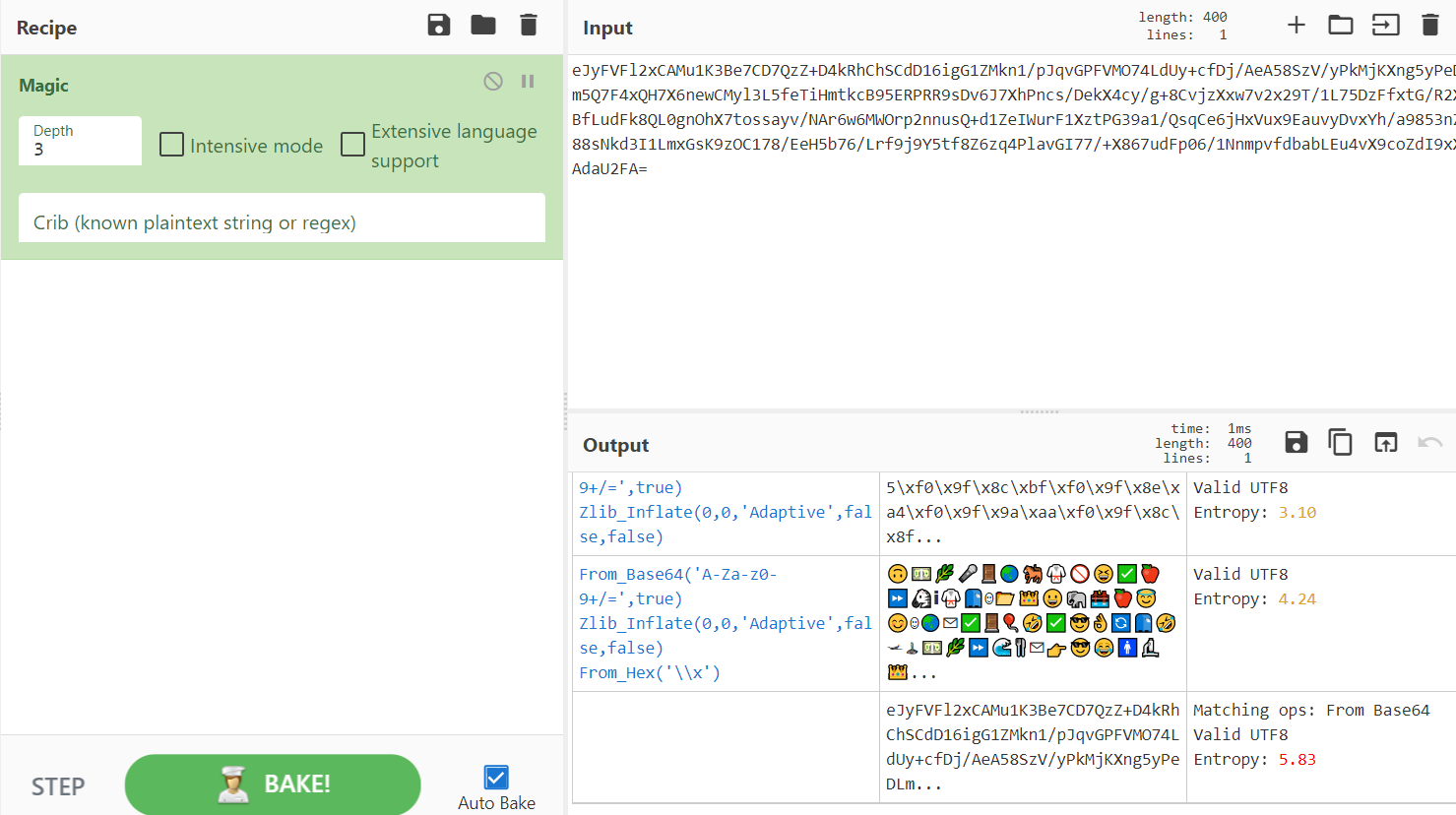
然后发现是emoji加密
但是剩下那张图片没有一点提示信息,就没思路了
Crypto
cyrpto1
小指数+共模攻击
直接套之前的脚本,完事
代码删了
crypto2
n1和n2有公因子
n1=20663949646446787716947370247427064802032290773674573417491154934657966734874241036307633567695175131014840617208051931753476223149652427133485160771068994073566431652969243962290116898345337189704974833817335135391974497754670322430159624252007005736522065638860351992074099453212550475552692645688800084354832716662142860413158369020005830095049988807931794736876563293916525328174812726514626029103506607813186690909585870115364600969148482617083817273910020722354923244093624032174432568413187131385994452769295894606345768596899824635672699945050103814681553981019917552667794514804359500108947102234376726009329
n2=23260834024376640092536888922041147168387702014814910549469730354688848760379274203088716649609675449936234732528778557041701524981200368996310064584479657042098426164366286670115392015865853892816983885530312074073396422301009513106258655315791720535737587913264728919869055970993613641008348186263870234072422880033882864603438907070864271470483691729705421547143623305055532339107777314310976947392833395180922324243244784018964736826235018388498516438612962123562977736924674510730898077787055367234786519915374446506561992135856904927351307275140543635152771670410211235702283822782412971646092584646758107766061
c1=20522772249591436865905796103232542494211695376973377722875606678999899690405480809231671346489821878050354380591999935960795888483664473952207298504196203830543208477229162177648586683957831016664569242538775928728009699300145355818417233892295367828930893733774091897666206696635744262884229680137381841581000794056156842812583057103472764486608022028638288161256424936523444974815727764620634174112474612238992061186937613171878635903455700636894570504376153482600057655480654731180740098435209814585459376319844315388048636156465832997913885636776523217188604040216732137108997444787157007665652718553013424347649
c2=18715009944766815149492560645051626329204114049927707292306481018724323433701970253541495090244787378826569549885480491764057526828531429033378143426272248940256432423939977805246742287886281853484696625486522535042794403288199393432900065504766428665320682811338887618389589263597065738414638013423594446322359052784842619755053094028050245325637698678444632860097510081832077842610716042473697478416213915805481704537884611126069907812621750817901278803326304784057145916721693930579344441283586458621033705530309835431139751025999089707480829034535026967779441379062426254038310930863215188888662357133997908688736
e=65537
from gmpy2 import *
from Crypto.Util.number import *
p=gcd(n1,n2)
q1=n1//p
q2=n2//p
phi1=(p-1)*(q1-1)
phi2=(p-1)*(q2-1)
print(long_to_bytes(pow(c1,inverse(e,phi1),n1))+long_to_bytes(pow(c2,inverse(e,phi2),n2)))
Re
Lihua's for
放入ida
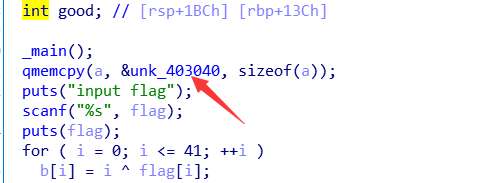
点这个,然后把值提取一下,然后异或一下,然后就是flag了
web
看什么看,不会
总结
比赛恶心的恶心,简单的简单,没有什么体验,题目描述太少,最后一年了,感觉进决赛有点困难,难受,要是两个misc有点提示,可能都出了



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 从 HTTP 原因短语缺失研究 HTTP/2 和 HTTP/3 的设计差异
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· winform 绘制太阳,地球,月球 运作规律
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· AI 智能体引爆开源社区「GitHub 热点速览」
· 写一个简单的SQL生成工具