华为5700三层交换机在生产场景中做策略路由
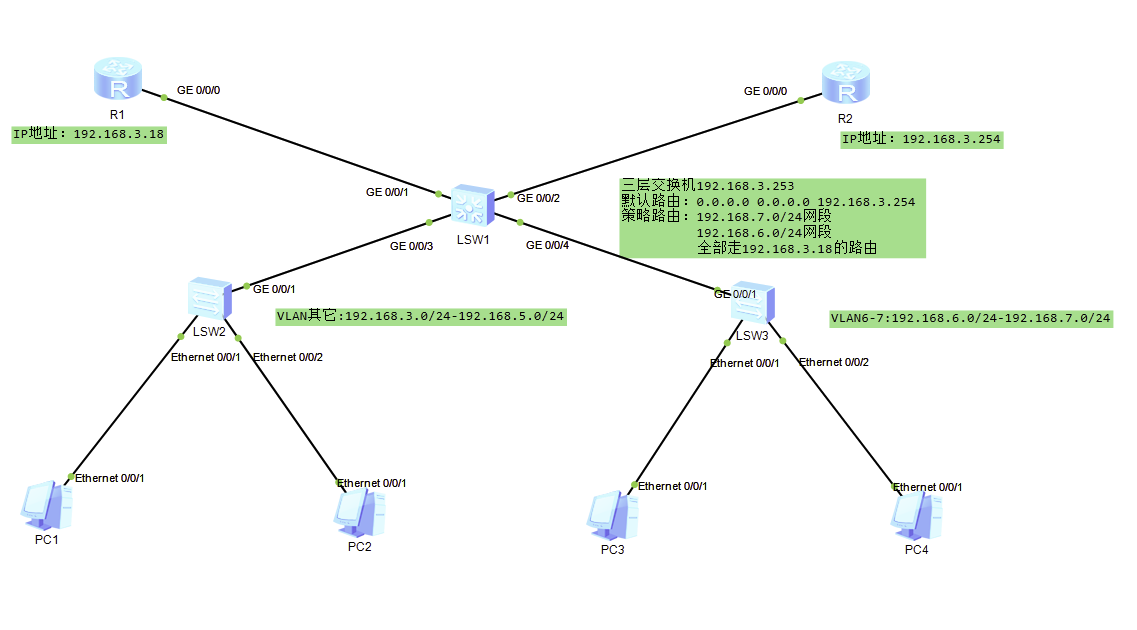
我们在工作中经常会遇到这样的问题,就是有两条线路,一条电信一条移动,一条ADSL一条光纤。诸如此类的。但由于有三层交换机,我们往往把默认路由就指向了某一个出口。
这样我们另外一条线路基本上是闲置的,或者另作它用。这样并没有把线路利用率达到最大。
所以这里我们就需要在三层交换机里做策略路由。
没有做策略的就走我们的默认路由,做了策略的,就走我们指定的吓一跳地址。
大概思路就是先做好ACL,设定好网段走的指向,然后把策略应用到接口上,或者应用到VLAN上。这样,我们指定的某一网段就可以走我们规定的下一跳地址了。
大概拓扑图如图所上。
这里我们就不介绍如何配置单臂路由和trunk了。直接上我在华为5700交换机上已经配置好的配置吧!
<S5720-L3>dis cu !Software Version V200R010C00SPC600 # sysname S5720-L3 # FTP server enable # vcmp role server vcmp domain yiyuan vcmp authentication sha2-256 password %^%#Vt=*@hApLH5ceW4Bh':-RQ*IMG`'j+`E}uCLieQ%%^%# # vlan batch 3 to 13 # stp instance 0 root primary # authentication-profile name default_authen_profile authentication-profile name dot1x_authen_profile authentication-profile name mac_authen_profile authentication-profile name portal_authen_profile authentication-profile name dot1xmac_authen_profile authentication-profile name multi_authen_profile # lacp priority 100 # telnet server enable # dhcp enable # diffserv domain default # radius-server template default # acl number 3009 rule 10 permit ip destination 192.168.0.0 0.0.255.255 acl number 3010 rule 10 permit ip source 192.168.7.0 0.0.0.255 rule 11 permit ip source 192.168.6.0 0.0.0.255 # traffic classifier ecnet operator or if-match acl 3010 traffic classifier innernet operator or if-match acl 3009 # traffic behavior redirect redirect ip-nexthop 192.168.3.18 traffic behavior yunxu permit # traffic policy EcRouter match-order config classifier innernet behavior yunxu classifier ecnet behavior redirect # free-rule-template name default_free_rule # portal-access-profile name portal_access_profile # drop-profile default # ip pool 3 gateway-list 192.168.3.253 network 192.168.3.0 mask 255.255.255.0 excluded-ip-address 192.168.3.1 192.168.3.5 excluded-ip-address 192.168.3.100 192.168.3.130 excluded-ip-address 192.168.3.252 excluded-ip-address 192.168.3.254 lease day 300 hour 0 minute 0 dns-list 192.168.3.1 192.168.3.254 # ip pool 4 gateway-list 192.168.4.254 network 192.168.4.0 mask 255.255.255.0 excluded-ip-address 192.168.4.1 excluded-ip-address 192.168.4.253 lease day 300 hour 0 minute 0 dns-list 192.168.3.1 192.168.3.254 # ip pool 5 gateway-list 192.168.5.254 network 192.168.5.0 mask 255.255.255.0 excluded-ip-address 192.168.5.1 excluded-ip-address 192.168.5.253 lease day 300 hour 0 minute 0 dns-list 192.168.3.1 192.168.3.254 # ip pool 6 gateway-list 192.168.6.254 network 192.168.6.0 mask 255.255.255.0 excluded-ip-address 192.168.6.1 excluded-ip-address 192.168.6.253 lease day 300 hour 0 minute 0 dns-list 192.168.3.1 192.168.3.254 # ip pool 7 gateway-list 192.168.7.254 network 192.168.7.0 mask 255.255.255.0 excluded-ip-address 192.168.7.1 excluded-ip-address 192.168.7.253 lease day 300 hour 0 minute 0 dns-list 192.168.3.1 192.168.3.254 # ip pool 8 gateway-list 192.168.8.254 network 192.168.8.0 mask 255.255.255.0 excluded-ip-address 192.168.8.1 excluded-ip-address 192.168.8.253 lease day 300 hour 0 minute 0 dns-list 192.168.3.1 192.168.3.254 # ip pool 9 gateway-list 192.168.9.254 network 192.168.9.0 mask 255.255.255.0 excluded-ip-address 192.168.9.1 excluded-ip-address 192.168.9.253 lease day 300 hour 0 minute 0 dns-list 192.168.3.1 192.168.3.254 # ip pool 20 # ip pool 11 gateway-list 192.168.11.254 network 192.168.11.0 mask 255.255.255.0 lease day 300 hour 0 minute 0 dns-list 192.168.3.1 192.168.3.254 # ip pool 13 gateway-list 192.168.13.254 network 192.168.13.0 mask 255.255.255.0 excluded-ip-address 192.168.13.1 192.168.13.2 excluded-ip-address 192.168.13.252 192.168.13.253 lease day 300 hour 0 minute 0 dns-list 192.168.3.1 192.168.3.254 # aaa authentication-scheme default authentication-scheme radius authentication-mode radius authorization-scheme default accounting-scheme default local-aaa-user password policy administrator password expire 0 domain default authentication-scheme radius radius-server default domain default_admin authentication-scheme default local-user admin password irreversible-cipher $1a$\0a<Ri;(DK$DeA@5{qo/#)v59SA455C^il`6jL&sF#N4/VTPb'U$ local-user admin privilege level 3 local-user admin service-type telnet terminal local-user huawei password irreversible-cipher $1a$@vX7<1zJ`#$Oz<JS-rSj#3)P9G[2&y)~h'mE6&m:GCEU{!-.E{F$ local-user huawei privilege level 3 local-user huawei ftp-directory flash: local-user huawei service-type ftp # interface Vlanif1 # interface Vlanif3 ip address 192.168.3.253 255.255.255.0 dhcp select global # interface Vlanif4 ip address 192.168.4.254 255.255.255.0 dhcp select global # interface Vlanif5 ip address 192.168.5.254 255.255.255.0 dhcp select global # interface Vlanif6 ip address 192.168.6.254 255.255.255.0 traffic-policy EcRouter inbound dhcp select global # interface Vlanif7 ip address 192.168.7.254 255.255.255.0 traffic-policy EcRouter inbound dhcp select global # interface Vlanif8 ip address 192.168.8.254 255.255.255.0 dhcp select global # interface Vlanif9 ip address 192.168.9.254 255.255.255.0 dhcp select global # interface Vlanif10 # interface Vlanif11 ip address 192.168.11.254 255.255.255.0 dhcp select global # interface Vlanif12 ip address 192.168.12.254 255.255.255.0 # interface Vlanif13 ip address 192.168.13.254 255.255.255.0 dhcp select global # interface MEth0/0/1 # interface Eth-Trunk1 port link-type trunk port trunk allow-pass vlan 2 to 4094 mode lacp max active-linknumber 2 # interface Eth-Trunk2 port link-type trunk port trunk allow-pass vlan 2 to 4094 mode lacp max active-linknumber 2 # interface Eth-Trunk3 port link-type trunk port trunk allow-pass vlan 2 to 4094 mode lacp max active-linknumber 2 # interface Eth-Trunk4 port link-type trunk port trunk allow-pass vlan 2 to 4094 mode lacp max active-linknumber 2 # interface Eth-Trunk5 port link-type trunk port trunk allow-pass vlan 2 to 4094 mode lacp max active-linknumber 2 # interface Eth-Trunk6 port link-type trunk port trunk allow-pass vlan 2 to 4094 mode lacp max active-linknumber 2 # interface Eth-Trunk7 port link-type trunk port trunk allow-pass vlan 2 to 4094 mode lacp max active-linknumber 2 # interface Eth-Trunk8 # interface GigabitEthernet0/0/1 eth-trunk 1 lacp priority 100 # interface GigabitEthernet0/0/2 eth-trunk 1 lacp priority 100 # interface GigabitEthernet0/0/3 eth-trunk 2 lacp priority 100 # interface GigabitEthernet0/0/4 eth-trunk 2 lacp priority 100 # interface GigabitEthernet0/0/5 eth-trunk 3 lacp priority 100 # interface GigabitEthernet0/0/6 eth-trunk 3 lacp priority 100 # interface GigabitEthernet0/0/7 eth-trunk 4 lacp priority 100 # interface GigabitEthernet0/0/8 eth-trunk 4 lacp priority 100 # interface GigabitEthernet0/0/9 eth-trunk 5 lacp priority 100 # interface GigabitEthernet0/0/10 eth-trunk 5 lacp priority 100 # interface GigabitEthernet0/0/11 eth-trunk 6 lacp priority 100 # interface GigabitEthernet0/0/12 eth-trunk 6 lacp priority 100 # interface GigabitEthernet0/0/13 shutdown eth-trunk 7 lacp priority 100 # interface GigabitEthernet0/0/14 shutdown eth-trunk 7 lacp priority 100 # interface GigabitEthernet0/0/15 port link-type access port default vlan 3 # interface GigabitEthernet0/0/16 port link-type access port default vlan 3 # interface GigabitEthernet0/0/17 port link-type access port default vlan 3 # interface GigabitEthernet0/0/18 port link-type access port default vlan 3 # interface GigabitEthernet0/0/19 port link-type access port default vlan 3 # interface GigabitEthernet0/0/20 port link-type access port default vlan 3 # interface GigabitEthernet0/0/21 port link-type access port default vlan 3 # interface GigabitEthernet0/0/22 port link-type access port default vlan 3 # interface GigabitEthernet0/0/23 port link-type access port default vlan 3 # interface GigabitEthernet0/0/24 port link-type access port default vlan 3 # interface GigabitEthernet0/0/25 port link-type access port default vlan 6 # interface GigabitEthernet0/0/26 port link-type access port default vlan 3 # interface GigabitEthernet0/0/27 port link-type access port default vlan 3 # interface GigabitEthernet0/0/28 port link-type access port default vlan 3 # interface GigabitEthernet0/0/29 port link-type access port default vlan 3 # interface GigabitEthernet0/0/30 port link-type access port default vlan 3 # interface GigabitEthernet0/0/31 port link-type access port default vlan 3 # interface GigabitEthernet0/0/32 port link-type access port default vlan 3 # interface GigabitEthernet0/0/33 port link-type access port default vlan 3 # interface GigabitEthernet0/0/34 port link-type access port default vlan 3 # interface GigabitEthernet0/0/35 port link-type access port default vlan 3 # interface GigabitEthernet0/0/36 port link-type access port default vlan 3 # interface GigabitEthernet0/0/37 port link-type access port default vlan 3 # interface GigabitEthernet0/0/38 port link-type access port default vlan 3 # interface GigabitEthernet0/0/39 port link-type access port default vlan 3 # interface GigabitEthernet0/0/40 port link-type access port default vlan 3 # interface GigabitEthernet0/0/41 port link-type access port default vlan 3 # interface GigabitEthernet0/0/42 port link-type access port default vlan 3 # interface GigabitEthernet0/0/43 port link-type access port default vlan 3 # interface GigabitEthernet0/0/44 port link-type access port default vlan 3 # interface GigabitEthernet0/0/45 port link-type access port default vlan 12 # interface GigabitEthernet0/0/46 port link-type access port default vlan 3 # interface GigabitEthernet0/0/47 port link-type access port default vlan 3 # interface GigabitEthernet0/0/48 port link-type access port default vlan 3 # interface GigabitEthernet0/0/49 port link-type access port default vlan 13 # interface GigabitEthernet0/0/50 # interface GigabitEthernet0/0/51 # interface GigabitEthernet0/0/52 # interface NULL0 # ip route-static 0.0.0.0 0.0.0.0 192.168.3.18 preference 30 ip route-static 0.0.0.0 0.0.0.0 192.168.3.254 preference 20 ip route-static 10.0.0.0 255.255.255.0 192.168.3.250 ip route-static 172.0.10.0 255.255.255.252 192.168.3.250 ip route-static 192.168.0.0 255.255.255.0 192.168.3.250 ip route-static 192.168.10.0 255.255.255.0 192.168.3.250 ip route-static 192.168.20.0 255.255.255.0 192.168.3.250 ip route-static 192.168.50.0 255.255.255.0 192.168.3.250 # snmp-agent snmp-agent local-engineid 800007DB03340A98CCA7A0 snmp-agent sys-info version v3 # user-interface maximum-vty 8 user-interface con 0 authentication-mode aaa user-interface vty 0 4 authentication-mode aaa protocol inbound telnet user-interface vty 5 7 user-interface vty 16 20 # port-group bangongshi group-member GigabitEthernet0/0/15 group-member GigabitEthernet0/0/16 group-member GigabitEthernet0/0/17 group-member GigabitEthernet0/0/18 group-member GigabitEthernet0/0/19 group-member GigabitEthernet0/0/20 group-member GigabitEthernet0/0/21 group-member GigabitEthernet0/0/22 group-member GigabitEthernet0/0/23 group-member GigabitEthernet0/0/24 group-member GigabitEthernet0/0/25 group-member GigabitEthernet0/0/26 group-member GigabitEthernet0/0/27 group-member GigabitEthernet0/0/28 group-member GigabitEthernet0/0/29 group-member GigabitEthernet0/0/30 group-member GigabitEthernet0/0/31 group-member GigabitEthernet0/0/32 group-member GigabitEthernet0/0/33 group-member GigabitEthernet0/0/34 group-member GigabitEthernet0/0/35 group-member GigabitEthernet0/0/36 group-member GigabitEthernet0/0/37 group-member GigabitEthernet0/0/38 group-member GigabitEthernet0/0/39 group-member GigabitEthernet0/0/40 group-member GigabitEthernet0/0/41 group-member GigabitEthernet0/0/42 group-member GigabitEthernet0/0/43 group-member GigabitEthernet0/0/44 group-member GigabitEthernet0/0/46 group-member GigabitEthernet0/0/47 group-member GigabitEthernet0/0/48 # port-group chejian1 group-member GigabitEthernet0/0/1 group-member GigabitEthernet0/0/2 # port-group chejian2 group-member GigabitEthernet0/0/3 group-member GigabitEthernet0/0/4 # port-group chejian3 group-member GigabitEthernet0/0/5 group-member GigabitEthernet0/0/6 # port-group chejian4 group-member GigabitEthernet0/0/7 group-member GigabitEthernet0/0/8 # port-group chejian5 group-member GigabitEthernet0/0/9 group-member GigabitEthernet0/0/10 # port-group chejian6 group-member GigabitEthernet0/0/11 group-member GigabitEthernet0/0/12 # port-group chejian7 group-member GigabitEthernet0/0/13 group-member GigabitEthernet0/0/14 # port-group dachi8 group-member GigabitEthernet0/0/49 # dot1x-access-profile name dot1x_access_profile # mac-access-profile name mac_access_profile # return <S5720-L3> <S5720-L3> <S5720-L3>
这里着重指出看一下ACL的配置和策略的应用。
# acl number 3009 rule 10 permit ip destination 192.168.0.0 0.0.255.255 acl number 3010 rule 10 permit ip source 192.168.7.0 0.0.0.255 rule 11 permit ip source 192.168.6.0 0.0.0.255 # traffic classifier ecnet operator or if-match acl 3010 traffic classifier innernet operator or if-match acl 3009 # traffic behavior redirect redirect ip-nexthop 192.168.3.18 traffic behavior yunxu permit # traffic policy EcRouter match-order config classifier innernet behavior yunxu classifier ecnet behavior redirect #
# ip route-static 0.0.0.0 0.0.0.0 192.168.3.18 preference 30 ip route-static 0.0.0.0 0.0.0.0 192.168.3.254 preference 20 ip route-static 10.0.0.0 255.255.255.0 192.168.3.250 ip route-static 172.0.10.0 255.255.255.252 192.168.3.250 ip route-static 192.168.0.0 255.255.255.0 192.168.3.250 ip route-static 192.168.10.0 255.255.255.0 192.168.3.250 ip route-static 192.168.20.0 255.255.255.0 192.168.3.250 ip route-static 192.168.50.0 255.255.255.0 192.168.3.250 #
# interface Vlanif6 ip address 192.168.6.254 255.255.255.0 traffic-policy EcRouter inbound dhcp select global # interface Vlanif7 ip address 192.168.7.254 255.255.255.0 traffic-policy EcRouter inbound dhcp select global #
这里提一下华为ACL的分类
ACL的分类:
(1):按照ACL过滤的报文类型和功能划分
基本acl(2000-2999):只能匹配源ip地址。
高级acl(3000-3999):可以匹配源ip、目标ip、源端口、目标端口等三层和四层的字段。
① 接口ACL(编号1000-----19999)
② 基本ACL(编号2000-----2999)
③ 高级ACL(编号3000-----3999)
④ 二层ACL(编号4000-----4999)
⑤ 自定义ACL(编号5000----5999)
参考一下这篇文章
https://www.q578.com/s-5-2432926-0/
华为交换机+双链路出口参考以下两篇文章
http://t.zoukankan.com/niewd-p-14174326.html
https://www.cnblogs.com/niewd/p/16020723.html
-------------------------------------------------------------------------------------------------
至此结束了!
附上最后的测试结果。
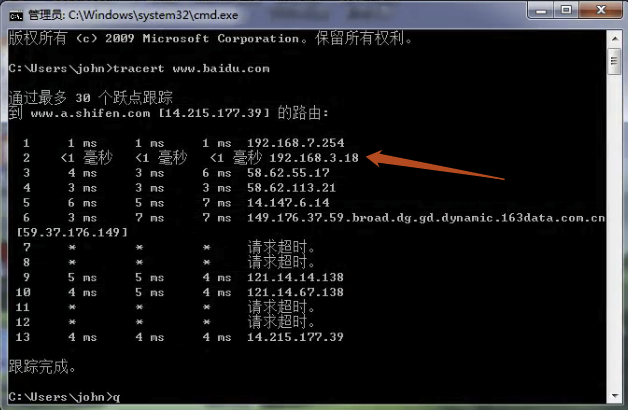
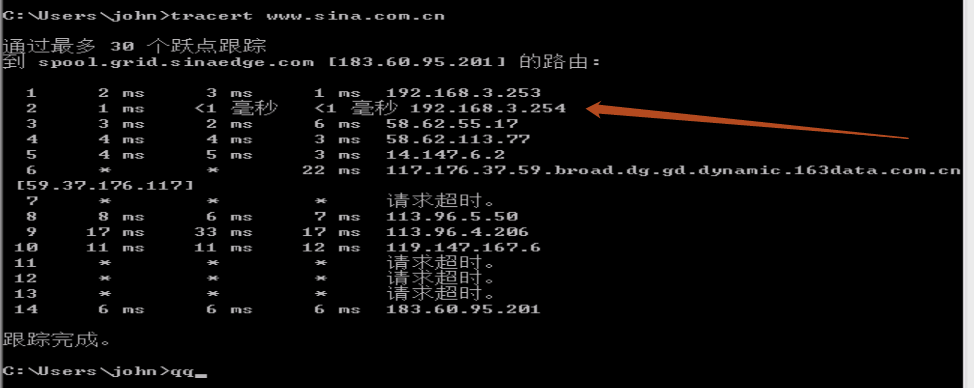
如果是思科的交换机,请参考下面。
https://blog.csdn.net/qq_33468857/article/details/94822669
Switch>en
Switch#conf t
Switch(config)#
Switch(config)#sdm prefer routing
Switch(config)#end
Switch#wri
Switch#reload
Switch(config)#access-list 101 permit ip any 172.30.218.0 0.0.0.255 //101以上是扩展访问控制列表 ;0.0.0.255是通配符 与子网掩码的通配符正好相反
Switch(config)#route-map Gaoxiong permit 10
Switch(config-route-map)#match ip address 101
Switch(config-route-map)#set ip next-hop 123.158.40.2 //符合策略的包转发到的下一跳地址
Switch(config)#interface vlan 1
[Switch(config)#interface gigabitEthernet 0/7 这是直接绑在物理接口上] //很重要!必须绑定在数据入口的接口上才能达到设想的要求。因为数据包在离开的接口上是已经路由过的,不会再走策略路由
[-- Switch(config)#interface vlan 1 -- 或者绑定在VLAN1虚拟接口上也可以]
Switch(config-if)#ip policy route-map GaoXiong
[--如果是绑定在VLAN1虚拟接口上 则要将真实接口放进来--]
Switch(config)#interface gigabitEthernet 1/0/10
Switch(config-if)#switchport mode access
Switch(config-if)#switchport access vlan 1
Switch(config-if)#end
————————————————
版权声明:本文为CSDN博主「neo_will_mvp」的原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接及本声明。
原文链接:https://blog.csdn.net/qq_33468857/article/details/94822669
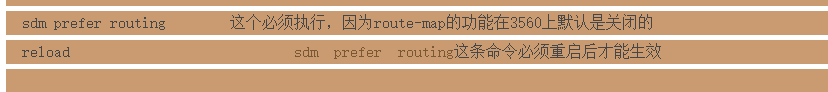
https://blog.csdn.net/a9254778/article/details/9125523
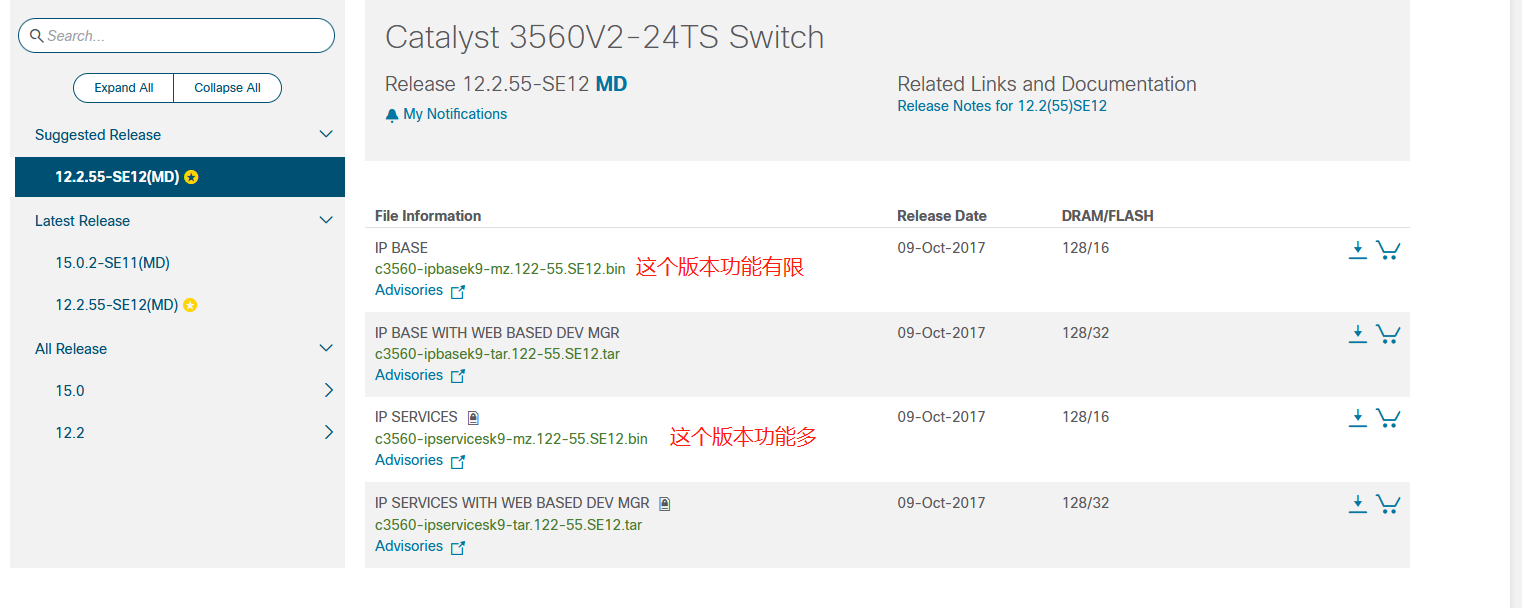
这里特别说明一下,因为我的机器的思科3560 交换机。单固件版本是BASE版本的,这个版本的功能有限,services这个版本功能多。services的版本才支持pbr,也就是策略路由。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号