Centos7_CA认证
说明:
CA主机 :172.16.0.133
Client 主机 : 172.16.0.132
/etc/pki/tls目录下面文件含义:
Cert.pem 软连接到certs/ca-bundle.crt
certs 该服务器证书存放目录
ca-bundle.crt 内置信任证书
pricate 证书密钥存放目录
openssl.cnf openssl的CA主配置文件
不用自己做证书,然后颁发。直接颁发证书
可实现https访问
1 openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/httpd/ssl.key -out /etc/httpd/ssl.crt 2 cat /etc/httpd/ssl.crt >> /etc/pki/tls/certs/ca-bundle.crt
1 为CA提供所需的目录及文件
(1)所需目录,如果无,则创建
1 /etc/pki/CA/certs/ 存放Ca签署(颁发)过的数字证书 2 /etc/pki/CA/crl/ 吊销的证书 3 /etc/pki/CA/newcerts/ (证书备份目录) 4 /etc/pki /CA/ private/ 用于存放ca私钥
(2)所需文件
1 [root@centos7 ~]# touch /etc/pki/CA/serial #序列号文件 2 [root@centos7 ~]# touch /etc/pki/CA/index.txt #数据库文件
(3)
1 [root@centos7 ~]# echo 01 > /etc/pki/CA/serial #维护ca的序列号
2 生成私钥
1 [root@centos7 ~]#(umask 077; openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048)
3·生成自签证书
1 [root@centos7~]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem -days 365
4 在client上进行如下操作
(1)创建放置私钥,证书的文件夹
1 [root@CentOS7 ~]# mkdir /etc/httpd/ssl
(2)生成自己的私钥
1 [root@CentOS7~]#(umask 077; openssl genrsa -out /etc/httpd/ssl/httpd.key 2048)
(3)请CA为自己生成公钥
1 [root@CentOS7 ~]#openssl req -new -key /etc/httpd/ssl/httpd.key -out /etc/httpd/ssl/httpd.csr -days 365
(4)把生成的公钥发送给CA
1 [root@CentOS7~]#scp /etc/httpd/ssl/httpd.csr root@172.16.0.133:/tmp/
5 在CA主机上为client签证
1 [root@centos7 ~]# openssl ca -in /tmp/httpd.csr -out /etc/pki/CA/certs/httpd.crt -days 365 2 Using configuration from /etc/pki/tls/openssl.cnf 3 Check that the request matches the signature 4 Signature ok 5 Certificate Details: 6 Serial Number: 1 (0x1) 7 Validity 8 Not Before: Jun 3 02:54:23 2017 GMT 9 Not After : Jun 3 02:54:23 2018 GMT 10 Subject: 11 countryName = CN 12 stateOrProvinceName = BeiJing 13 organizationName = Company 14 organizationalUnitName = OPS 15 commonName = www.test.com 16 X509v3 extensions: 17 X509v3 Basic Constraints: 18 CA:FALSE 19 Netscape Comment: 20 OpenSSL Generated Certificate 21 X509v3 Subject Key Identifier: 22 5D:A9:5A:90:29:F3:3A:7F:76:BE:21:78:14:80:E5:FB:5E:03:D8:D9 23 X509v3 Authority Key Identifier: 24 keyid:9E:1E:F3:84:4D:D0:79:E2:BD:DD:A8:50:29:6C:BA:0C:21:60:CA:96 25 Certificate is to be certified until Jun 3 02:54:23 2018 GMT (365 days) 26 Sign the certificate? [y/n]:y 27 28 1 out of 1 certificate requests certified, commit? [y/n]y 29 Write out database with 1 new entries(出现这段才是颁发证书成功) 30 Data Base Updated
6 把签署的证书发给client
1 [root@centos7~]#scp /etc/pki/CA/certs/httpd.crt root@172.16.10.132:/etc/httpd/ssl/
7 把CA的证书发给client
1 [root@serverB ~]scp /etc/pki/CA/cacert.pem root@172.16.0.132:/etc/httpd/ssl/
8 在client上导入CA的证书(cacert.pem)
1 cat /etc/httpd/ssl/cacert.pem >> /etc/pki/tls/certs/ca-bundle.crt
为保险建议也把CA颁发的.crt证书也导入
HTTPS配置
9 修改配置文件/etc/httpd/conf.d/virthost.conf
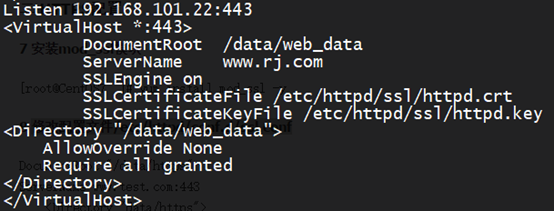
模板可在/etc/httpd/conf.d/ssl.conf 里找粘贴修改路径就好了
我的头怎么跟机关枪似的,
突突突~突突突的



