网络补充
1. 网卡配置(ip,dns)
- 目标:
-
- 修改网卡的名字为eth0.
- 修改网卡配置文件,ip,dns,网关,子网掩码.(物理机,虚拟机(私有云))
- 公有云自动获取即可,服务器数量巨大自动获取.
1.1 网卡命名
结论: 工作有需求的时候再去修改. 做好记录,后面使用的时候参考即可.
# 网卡命名规则:
ens33 ensxxxxp
eth0 <统一修改为eth0 eth1 eth2 .... 形式.修改网卡名字为eth0(方案)
方法01:安装系统的时候修改 net.ifnames=0 biosdevname=0 红帽类系统,ubt版本20.04版本及之前
方法02:安装完成系统修改系统启动的配置文件,网卡配置文件.
1.1.1 方法01:安装完成系统
麒麟系统
查看代码
# 方法01:安装完成系统
[root@Kylin-V10-sp3 ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:8c:ff:3d brd ff:ff:ff:ff:ff:ff
inet 10.0.0.36/24 brd 10.0.0.255 scope global noprefixroute ens33
valid_lft forever preferred_lft forever
inet6 fe80::3596:15a7:b72a:6fee/64 scope link noprefixroute
valid_lft forever preferred_lft forever
[root@Kylin-V10-sp3 ~]#
# 第1步: 修改/boot/grub2/grub.cfg配置 (麒麟系统是 linux后面即可)
linux开头的行后面添加 net.ifnames=0 biosdevname=0 或者执行 sed -ri.bak '/\t+linux/s#$# net.ifnames=0 biosdevname=0#g' /boot/grub2/grub.cfg
#修改之后检查内容
[root@Kylin-V10-sp3 ~]# grep -n .*linux.*0$ /boot/grub2/grub.cfg
104: linux /vmlinuz-4.19.90-52.22.v2207.ky10.x86_64 root=/dev/mapper/klas-root ro resume=/dev/mapper/klas-swap rd.lvm.lv=klas/root rd.lvm.lv=klas/swap rhgb quiet crashkernel=1024M,high audit=0 net.ifnames=0 biosdevname=0
118: linux /vmlinuz-0-rescue-6853e90e34234ee78f85b3b8b3fdc032 root=/dev/mapper/klas-root ro resume=/dev/mapper/klas-swap rd.lvm.lv=klas/root rd.lvm.lv=klas/swap rhgb quiet crashkernel=1024M,high audit=0
[root@Kylin-V10-sp3 ~]#
# 第2步: 修改网卡配置文件.
1)修改网卡配置文件中NAME和DEVICE两个部分 (vim修改)
2)网卡配置文件名字改为eth0(mv 修改)
[root@Kylin-V10-sp3 /boot/grub2]# vim /etc/sysconfig/network-scripts/ifcfg-ens33
[root@Kylin-V10-sp3 /boot/grub2]#
[root@Kylin-V10-sp3 /boot/grub2]# cd /etc/sysconfig/network-scripts/
[root@Kylin-V10-sp3 /etc/sysconfig/network-scripts]# ls
ifcfg-ens33
[root@Kylin-V10-sp3 /etc/sysconfig/network-scripts]#
[root@Kylin-V10-sp3 /etc/sysconfig/network-scripts]# mv ifcfg-ens33 ifcfg-eth0
[root@Kylin-V10-sp3 /etc/sysconfig/network-scripts]#
# 修改后结果:
[root@Kylin-V10-sp3 /etc/sysconfig/network-scripts]# grep -n eth0 /etc/sysconfig/network-scripts/ifcfg-eth0
12:NAME=eth0
14:DEVICE=eth0
[root@Kylin-V10-sp3 /etc/sysconfig/network-scripts]#
# 重启Linux.
[root@Kylin-V10-sp3 /etc/sysconfig/network-scripts]# reboot
[root@Kylin-V10-sp3 ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:8c:ff:3d brd ff:ff:ff:ff:ff:ff
inet 10.0.0.36/24 brd 10.0.0.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet6 fe80::15a8:d444:56ed:ae7c/64 scope link noprefixroute
valid_lft forever preferred_lft forever
[root@Kylin-V10-sp3 ~]# centos系统
# 方法01:安装完成系统
# 第1步: 修改/boot/grub2/grub.cfg配置
搜索linux16开头的行,在这行结尾加上 net.ifnames=0 biosdevname=0
#修改之后检查内容
[root@oldboy-king-v3 ~]# grep -n linux16 /boot/grub2/grub.cfg
# 其他参考麒麟20.04修改方法
# 1. 修改grub
sed -i '/linux.*vmlinuz/s#$#biosdevname=0 net.ifnames=0#g' /boot/grub/grub.cfg
# 2. 修改网卡配置文件
sed -i 's#ens33#eth0#g' /etc/netplan/00-installer-config.yaml
# 3. 重启ubt22.04修改方法
#1.修改/boot/grub/grub.cfg
170,189,226行,增加biosdevname=0 net.ifnames=0
[root@ubuntu2204 ~]# awk '$1~/linux/{print NR,$0}' /boot/grub/grub.cfg
170 linux /vmlinuz-5.15.0-121-generic root=/dev/mapper/ubuntu--vg-ubuntu--lv ro
189 linux /vmlinuz-5.15.0-121-generic root=/dev/mapper/ubuntu--vg-ubuntu--lv ro
207 linux /vmlinuz-5.15.0-121-generic root=/dev/mapper/ubuntu--vg-ubuntu--lv ro recovery nomodeset dis_ucode_ldr
226 linux /vmlinuz-5.15.0-119-generic root=/dev/mapper/ubuntu--vg-ubuntu--lv ro
244 linux /vmlinuz-5.15.0-119-generic root=/dev/mapper/ubuntu--vg-ubuntu--lv ro recovery nomodeset dis_ucode_ldr
[root@ubuntu2204 ~]#
[root@ubuntu2204 ~]# sed -i '/linux.*vmlinuz/s#$# biosdevname=0 net.ifnames=0#g' /boot/grub/grub.cfg
#2.修改网卡配置文件内容
sed -i 's#ens33#eth0#g' /etc/netplan/00-installerconfig.yaml
#3.重启系统1.1.2 方法02:安装系统的时候修改
安装系统的时候选择第1个然后按tab键. 在最后写入 net.ifnames=0 biosdevname=0
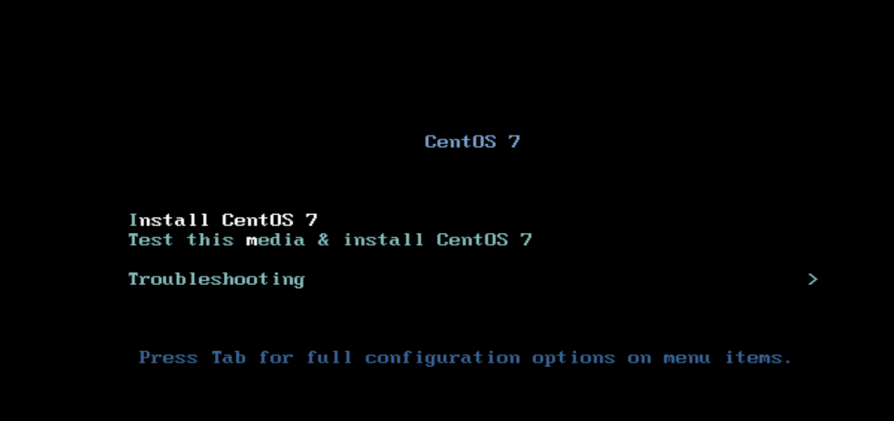
选择install 然后安装tab键,行尾输入 net.ifnames=0 biosdevname=0
1.2 网卡配置文件 ⭐⭐⭐⭐⭐
物理机,虚拟化(虚拟机)需要改或配置。
公有云保持默认即可。(DHCP自动获取)
#配置文件
红帽类系统:/etc/sysconfig/network-scripts/ifcfg-eth0 或 ifcfg-ens33
debian/ubt: /etc/netplan/xxxx.yaml
debian/ubt:其他文件。。。
#生效
systemctl restart network #centos
ifdown ens33 && ifup ens33 #kylin
netplay apply #ubt/debiancentos,麒麟,红帽系列系统
# /etc/sysconfig/network-scripts/ifcfg-eth0
[root@oldboy-test-video ~]# cat /etc/sysconfig/networkscripts/ifcfg-eth0
#网络类型,就是一个Ethernet 以太网
TYPE=Ethernet
PROXY_METHOD=none #none/static 手动、固定ip
#dhcp 自动获取
BROWSER_ONLY=no
#获取ip的方法
#none/static 手动配置ip
#dhcp 自动获取ip
BOOTPROTO=none
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=stable-privacy
#网卡名字
NAME=eth0
#设备名字
DEVICE=eth0
#每个设备1个唯一的id号,全球唯一.
UUID=c21147b3-6922-4a3a-b7c6-09f6de870496
#网卡是否开机是否自启动,网卡重启后是否自启动
#reboot
#systemctl restart network
ONBOOT=yes
#ip地址
IPADDR=10.0.0.200
#PREFIX或NETMASK子网掩码:控制局域网中最多有多少台机器.
PREFIX=24
#网关
GATEWAY=10.0.0.2
#DNS1,DNS2
DNS1=223.5.5.5
DNS2=223.6.6.6
IPV6_PRIVACY=no网卡配置文件核心指标:
# 核心: BOOTPROTO,ONBOOT,IPADDR,PREFIX,GATEWAY,DNS
#获取ip的方法
#none/static 手动配置ip
#dhcp 自动获取ip
BOOTPROTO=none
#网卡名字
NAME=eth0
#设备名字
DEVICE=eth0
#网卡是否开机是否自启动,网卡重启后是否自启动
#reboot
#systemctl restart network
ONBOOT=yes
#ip地址
IPADDR=10.0.0.36
#PREFIX或NETMASK子网掩码:控制局域网中最多有多少台机器.
PREFIX=24
#网关
GATEWAY=10.0.0.2
#DNS1,DNS2
DNS1=223.5.5.5
DNS2=223.6.6.6iP地址计算器:https://ipv4calc.bmcx.com/
DNS大全: https://dnsdaquan.com/#
# 阿里云 DNS
223.5.5.5
223.6.6.6
114
114.114.114.114
114.114.115.115
# 谷歌DNS
8.8.8.8
8.8.4.4⚠ DNS地址的选择:授权默认的;如果没有默认的,选择当前网络环境的(找运营商);最后再使用公共DNS.
- DNS配置文件
- 网卡配置文件DNS1 DNS2 优先.重启网卡后会覆盖/etc/resolv.conf文件
- /etc/resolv.conf 实时生效.
- ubt网卡配置文件
cat /etc/netplan/00-installer-config.yaml
# This is the network config written by 'subiquity'
network:
ethernets:
eth0: #网卡名字
addresses:
- 10.0.0.37/24 #ip/子网掩码 10.0.0.202/24
nameservers:
addresses:
- 223.5.5.5 #dns1
- 223.6.6.6 #dns2
search: []
routes:
- to: default
via: 10.0.0.2 #默认网关
version: 2
#网卡配置文件生效
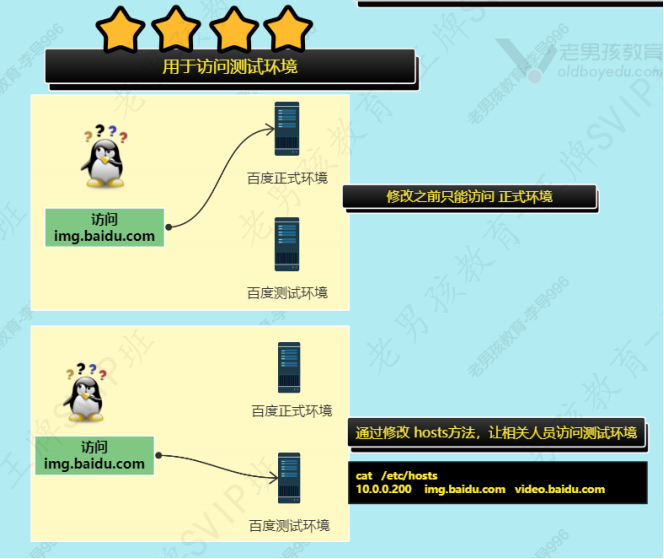
netplan apply1.3 hosts文件 ⭐⭐⭐⭐⭐
经常用于搭建网站,配置临时域名解析域名或主机名对应的ip.
解析为对应的ip. 类似于DNS.
# linux:/etc/hosts
# windows: c:\windows\system32\drivers\etc\hosts
# window键+r输入drivers 然后找etc hosts
# 主要用于访问测试环境
[root@Kylin-V10-sp3 ~]# vim /etc/hosts
[root@Kylin-V10-sp3 ~]#
[root@Kylin-V10-sp3 ~]# ping qq.com
PING qq.com (10.0.0.36) 56(84) bytes of data.
64 bytes from qq.com (10.0.0.36): icmp_seq=1 ttl=64 time=0.119 ms
64 bytes from qq.com (10.0.0.36): icmp_seq=2 ttl=64 time=0.092 ms
64 bytes from qq.com (10.0.0.36): icmp_seq=3 ttl=64 time=0.098 ms
^C
--- qq.com ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2036ms
rtt min/avg/max/mdev = 0.092/0.103/0.119/0.011 ms
[root@Kylin-V10-sp3 ~]# ^C
[root@Kylin-V10-sp3 ~]#
[root@Kylin-V10-sp3 ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
10.0.0.36 qq.com
[root@Kylin-V10-sp3 ~]# 子网掩码计算器:https://tool.520101.com/wangluo/ipjisuan/#google_vignette
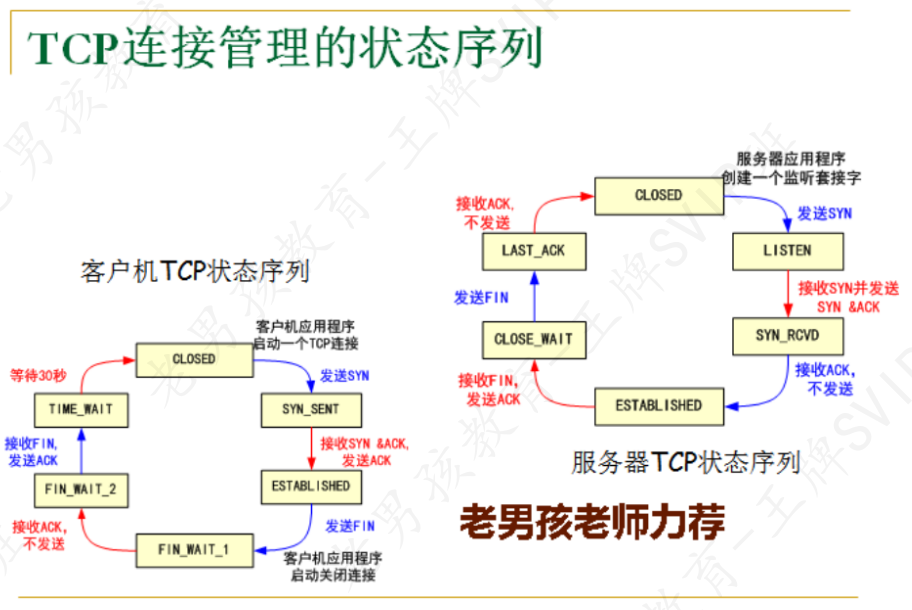
2. TCP 11种状态 ⭐⭐⭐⭐
目标: 掌握tcp三次握手,四次挥手的时候客户端,服务端常见状态.
Tcp3次握手,4次挥手的时候需要经历一个过程,在建立连接和断开连接的时候,服
务端和客户端就有一些状态.1
最容易理解的状态:CLOSED(关闭),establish(建立连接).
3次握手4次挥手状态:https://www.processon.com/view/link/6245136a5653bb072bce3259
2.1 三次握手的状态

TCP三次握手状态转换简单说明:
01.准备:首先,建立连接之前服务器和客户端的状态都为CLOSED。
02.准备:服务器创建socket后开始监听(启动服务),变为LISTEN状态。
03.客户端:SYN请求,客户端请求建立连接,向服务器发送SYN报文,客户端的状态变为SYN_SENT。
04.服务端:服务器收到客户端的报文(SYN)后向客户端发送ACK和SYN报文,此时服务器的状态变为SYN_RCVD(recevide)(收到了客户端发送的SYN请求)。
05.客户端然后,客户端收到ACK、SYN,就向服务器发送ACK,客户端状态变为ESTABLISHED
06.服务端服务器收到客户端的ACK后也变为ESTABLISHED。此时3次握手完成,连接建立!
2.2 四次挥手的状态
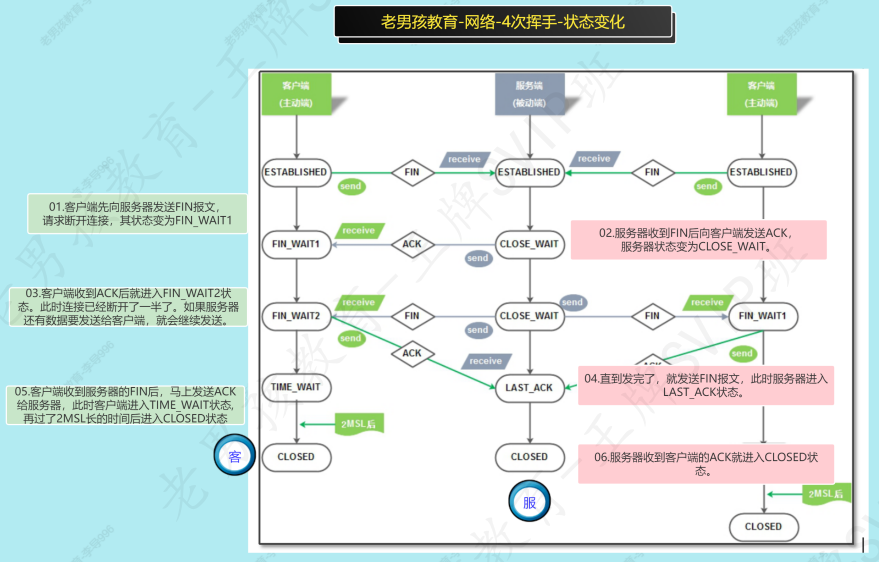
四次挥手中:
客户端:发出FIN请求这一方.
服务端:接收请求的.
01.客户端:客户端先向服务器发送FIN报文,请求断开连接,其状态变为FIN_WAIT1。
02.服务端:服务器收到FIN后向客户端发送ACK,服务器状态变为CLOSE_WAIT。
03.客户端:客户端收到ACK后就进入FIN_WAIT2状态。此时连接已经断开了一半了。如果服务器还有数据要发送给客户端,就会继续发送。
04.服务端:直到发完了,就发送FIN报文,此时服务器进入LAST_ACK状态。
05.客户端:客户端收到服务器的FIN后,马上发送ACK给服务器,此时客户端进入TIME_WAIT状态,再过了2MSL长的时间后进入CLOSED状态。
06.服务端:服务器收到客户端的ACK就进入CLOSED状态。
2.3 第11种状态补充
CLOSING状态表示:
客户端发了FIN,但客户端在FIN_WAIT1状态时没有收到服务器的ACK确认字段,却收到了服务器的FIN字段,这种情况发生在服务器发送的ACK丢包的时候,因为网络传输有时会有意外。
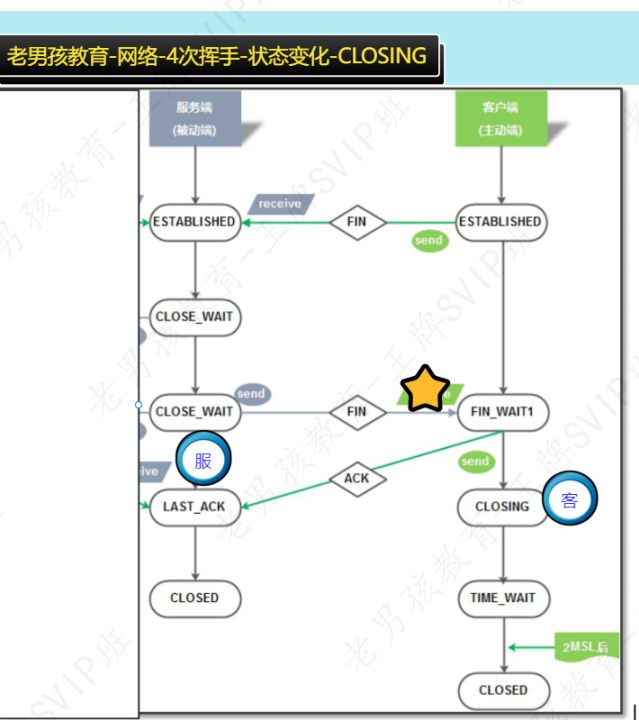

2.4 11种状态小结
核心必会: CLOSED,ESTABLISHED,LISTEN监听,TIME_WAIT,CLOSE_WAIT
逐渐掌握: FIN_WAIT1,FIN_WAIT2,CLOSING,SYN_SENT,LAST_ACK
3. 网络管理命令 ⭐⭐⭐⭐⭐
检查端口:telnet,ss,netstat,nmap,nc(net cat)....
查看连接情况:ss -ant
网络速度与程序占用情况
DNS解析:dig
追踪命令:tracert(windows), traceroute (linux)
加入到系统巡检脚本中:
################系统的网络信息#####################
1.ip地址
2.系统开放哪些端口
3.统计下每一种连接状态
4.哪些端口占用的带宽速度.
5.检查系统配置的DNS
6.显示路由追踪(www.baidu.com).
################系统的网络信息#####################
yum install -y net-tools lsof nethogs iftop telnet nc nmap3.1 检查端口
端口是否开启.
端口是否能访问(连接).
ss/netstat
3.1.1 检查是否存在22端口
我们可以连接这台服务器。
查看代码
# 方法01 推荐
[root@Kylin-V10-sp3 ~]# ss -lntup |grep 22
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:* users:(("sshd",pid=854,fd=5))
tcp LISTEN 0 128 [::]:22 [::]:* users:(("sshd",pid=854,fd=6))
[root@Kylin-V10-sp3 ~]#
[root@Kylin-V10-sp3 ~]# ss -lntu
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 127.0.0.1:323 0.0.0.0:*
udp UNCONN 0 0 [::1]:323 [::]:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 10 127.0.0.1:25 0.0.0.0:*
tcp LISTEN 0 128 [::]:22 [::]:*
[root@Kylin-V10-sp3 ~]#
# -p表示显示端口对应的进程的信息。
[root@Kylin-V10-sp3 ~]# ss -lntup
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 127.0.0.1:323 0.0.0.0:* users:(("chronyd",pid=738,fd=6))
udp UNCONN 0 0 [::1]:323 [::]:* users:(("chronyd",pid=738,fd=7))
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:* users:(("sshd",pid=854,fd=5))
tcp LISTEN 0 10 127.0.0.1:25 0.0.0.0:* users:(("sendmail",pid=1286,fd=6))
tcp LISTEN 0 128 [::]:22 [::]:* users:(("sshd",pid=854,fd=6))
[root@Kylin-V10-sp3 ~]#
[root@Kylin-V10-sp3 ~]# ss -lntup | grep -w ssh
[root@Kylin-V10-sp3 ~]#
[root@Kylin-V10-sp3 ~]# ss -lntup | grep -w sshd
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:* users:(("sshd",pid=854,fd=5))
tcp LISTEN 0 128 [::]:22 [::]:* users:(("sshd",pid=854,fd=6))
[root@Kylin-V10-sp3 ~]#
#grep -w 精确过滤. grep -w 22
# 方法02
[root@Kylin-V10-sp3 ~]# netstat -lntup |grep -w 22
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 854/sshd: /usr/sbin
tcp6 0 0 :::22 :::* LISTEN 854/sshd: /usr/sbin
[root@Kylin-V10-sp3 ~]#
# 方法03
[root@Kylin-V10-sp3 ~]# lsof -i :22
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
sshd 854 root 5u IPv4 26990 0t0 TCP *:ssh (LISTEN)
sshd 854 root 6u IPv6 26992 0t0 TCP *:ssh (LISTEN)
sshd 1199 root 5u IPv4 29892 0t0 TCP Kylin-V10-sp3:ssh->10.0.0.1:64370 (ESTABLISHED)
sshd 1221 root 5u IPv4 29892 0t0 TCP Kylin-V10-sp3:ssh->10.0.0.1:64370 (ESTABLISHED)
sshd 1570 root 5u IPv4 35514 0t0 TCP Kylin-V10-sp3:ssh->10.0.0.1:54940 (ESTABLISHED)
sshd 1580 root 5u IPv4 35514 0t0 TCP Kylin-V10-sp3:ssh->10.0.0.1:54940 (ESTABLISHED)
[root@Kylin-V10-sp3 ~]#
[root@Kylin-V10-sp3 ~]# lsof -ni :22
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
sshd 854 root 5u IPv4 26990 0t0 TCP *:ssh (LISTEN)
sshd 854 root 6u IPv6 26992 0t0 TCP *:ssh (LISTEN)
sshd 1199 root 5u IPv4 29892 0t0 TCP 10.0.0.36:ssh->10.0.0.1:64370 (ESTABLISHED)
sshd 1221 root 5u IPv4 29892 0t0 TCP 10.0.0.36:ssh->10.0.0.1:64370 (ESTABLISHED)
sshd 1570 root 5u IPv4 35514 0t0 TCP 10.0.0.36:ssh->10.0.0.1:54940 (ESTABLISHED)
sshd 1580 root 5u IPv4 35514 0t0 TCP 10.0.0.36:ssh->10.0.0.1:54940 (ESTABLISHED)
[root@Kylin-V10-sp3 ~]#
[root@Kylin-V10-sp3 ~]# lsof -nPi :22
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
sshd 854 root 5u IPv4 26990 0t0 TCP *:22 (LISTEN)
sshd 854 root 6u IPv6 26992 0t0 TCP *:22 (LISTEN)
sshd 1199 root 5u IPv4 29892 0t0 TCP 10.0.0.36:22->10.0.0.1:64370 (ESTABLISHED)
sshd 1221 root 5u IPv4 29892 0t0 TCP 10.0.0.36:22->10.0.0.1:64370 (ESTABLISHED)
sshd 1570 root 5u IPv4 35514 0t0 TCP 10.0.0.36:22->10.0.0.1:54940 (ESTABLISHED)
sshd 1580 root 5u IPv4 35514 0t0 TCP 10.0.0.36:22->10.0.0.1:54940 (ESTABLISHED)
[root@Kylin-V10-sp3 ~]#
# lsof -n 不要把ip反向解析为主机名、域名。
# lsof -P 不要把端口解析为对应的服务。3.1.2 检查是否可以访问22端口
不在对应的服务器上。(是否可以连接,是否存在.)
查看代码
#方法01
telnet 10.0.0.36 22 #命令行中推荐使用,检查是否有connected 标记。
#方法02
# nmap 网络扫描工具。
[root@ubuntu2204 ~]# nmap -p22 10.0.0.36
Starting Nmap 7.80 ( https://nmap.org ) at 2024-09-18 21:13 CST
Nmap scan report for 10.0.0.36
Host is up (0.00027s latency).
PORT STATE SERVICE
22/tcp open ssh
MAC Address: 00:0C:29:8C:FF:3D (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.14 seconds
[root@ubuntu2204 ~]#
[root@ubuntu2204 ~]#
[root@ubuntu2204 ~]# nmap -p80,443,22 baidu.com jd.com 10.0.0.36
Starting Nmap 7.80 ( https://nmap.org ) at 2024-09-18 21:13 CST
Nmap scan report for baidu.com (39.156.66.10)
Host is up (0.0029s latency).
Other addresses for baidu.com (not scanned): 110.242.68.66
PORT STATE SERVICE
22/tcp filtered ssh
80/tcp open http
443/tcp open https
Nmap scan report for jd.com (211.144.27.126)
Host is up (0.0018s latency).
Other addresses for jd.com (not scanned): 211.144.24.218 111.13.149.108 106.39.171.134
PORT STATE SERVICE
22/tcp filtered ssh
80/tcp open http
443/tcp open https
Nmap scan report for 10.0.0.36
Host is up (0.00028s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp filtered http
443/tcp filtered https
MAC Address: 00:0C:29:8C:FF:3D (VMware)
Nmap done: 3 IP addresses (3 hosts up) scanned in 1.50 seconds
[root@ubuntu2204 ~]#
PORT STATE SERVICE
22/tcp open ssh #nmap结果中只要有 端口 open就是开启 。
#nmap进阶使用
[root@Kylin-V10-sp3 ~]# nmap -p1-1024 10.0.0.37
Starting Nmap 7.92 ( https://nmap.org ) at 2024-09-18 21:15 CST
Nmap scan report for 10.0.0.37
Host is up (0.00012s latency).
Not shown: 1023 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
MAC Address: 00:0C:29:95:37:E0 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.12 seconds
[root@Kylin-V10-sp3 ~]#
[root@Kylin-V10-sp3 ~]# nmap -p22 10.0.0.0/24 jd.com taobao.com
Starting Nmap 7.92 ( https://nmap.org ) at 2024-09-18 21:15 CST
Nmap scan report for 10.0.0.1
Host is up (0.0038s latency).
PORT STATE SERVICE
22/tcp closed ssh
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 10.0.0.2
Host is up (0.00011s latency).
PORT STATE SERVICE
22/tcp closed ssh
MAC Address: 00:50:56:FE:5A:C2 (VMware)
Nmap scan report for 10.0.0.37
Host is up (0.00034s latency).
PORT STATE SERVICE
22/tcp closed ssh
MAC Address: 00:0C:29:95:37:E0 (VMware)
Nmap scan report for 10.0.0.36
Host is up (0.000041s latency).
PORT STATE SERVICE
22/tcp open ssh
Nmap scan report for jd.com (211.144.24.218)
Host is up (0.00049s latency).
Other addresses for jd.com (not scanned): 106.39.171.134 211.144.27.126 111.13.149.108
PORT STATE SERVICE
22/tcp filtered ssh
Nmap scan report for taobao.com (59.82.122.130)
Host is up (0.00048s latency).
Other addresses for taobao.com (not scanned): 59.82.44.240 59.82.122.165 59.82.43.234 59.82.122.140 59.82.43.239 59.82.43.238 59.82.121.163 2401:b180:7003::25 2401:b180:7003::6b 2401:b180:7003::ed 2408:4001:f00::3c 2408:4001:f00::87 2408:4001:f10::6f 2408:4001:f10::5e 2401:b180:7003::aa
PORT STATE SERVICE
22/tcp filtered ssh
Nmap done: 258 IP addresses (6 hosts up) scanned in 3.17 seconds
[root@Kylin-V10-sp3 ~]#
#方法03 nc netcat ncat
nc -v 10.0.0.37 22 #这个一般用于shell脚本中检查端口是否开启。
[root@Kylin-V10-sp3 ~]# nc -v 10.0.0.37 22
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Connection refused.
[root@Kylin-V10-sp3 ~]# nc -v 10.0.0.36 22
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Connected to 10.0.0.36:22.
SSH-2.0-OpenSSH_8.2
^C
[root@Kylin-V10-sp3 ~]# ^C
[root@Kylin-V10-sp3 ~]#3.1.3 企业面试题: 如何检查端口是否存在
ss -lntup
netstat -lntup
lsof -i:22
telnet 10.0.0.200 22
nmap -p22 10.0.0.200
nc 10.0.0.200 223.2 检查tcp连接状态
ss -ant
netstat -ant
root@iZ2zei5cw2j6q770mgp5kvZ:~/packages# ss -ant
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
LISTEN 0 511 0.0.0.0:80 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 511 127.0.0.1:9000 0.0.0.0:*
LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
ESTAB 0 0 172.28.157.228:22 221.218.208.28:50185
TIME-WAIT 0 0 172.28.157.228:51370 100.100.18.120:80
ESTAB 0 52 172.28.157.228:22 221.218.208.28:62721
ESTAB 0 0 172.28.157.228:42796 100.100.30.26:80
LISTEN 0 128 [::]:22 [::]:*
root@iZ2zei5cw2j6q770mgp5kvZ:~/packages#
未来统计:
企业案例: 每种状态的次数. sort+uniq
企业案例: 网站并发情况
并发: 同一时间内,用户连接数量.
方法:统计estab状态的连接数量(一般是80/443)端口.
root@iZ2zei5cw2j6q770mgp5kvZ:~/packages# ss -ant |awk 'NR>1{print $1}' |sort |uniq -c |sort -rn
6 LISTEN
3 ESTAB
1 TIME-WAIT
1 SYN-RECV
root@iZ2zei5cw2j6q770mgp5kvZ:~/packages# awk 'NR>2 && /^tcp/{print $NF}' netstat.log |sort |uniq -c |sort -rn3.3 网络速度
总体速度
查看代码
# 添加额外的源
wget -O /etc/yum.repos.d/epel.repo https://mirrors.aliyun.com/repo/epel-7.repo
# 下载iftop
yum install -y iftop
top/htop
iotop
# iftop 2s 10s 40s数据传输平均速度
iftop -n #ip反向解析为域名/主机名
iftop -i 指定网卡. 默认eth0 第1个网卡.
iftop -P 显示端口
iftop -N 不要把端口解析为服务名字
# 最终使用
iftop -nNP -i eth0 #显示端口号,不要把ip解析为域名,不要把端口解析为服务, 监视指定网卡eth0
#iftop非交互模式 方便进行过滤与处理.
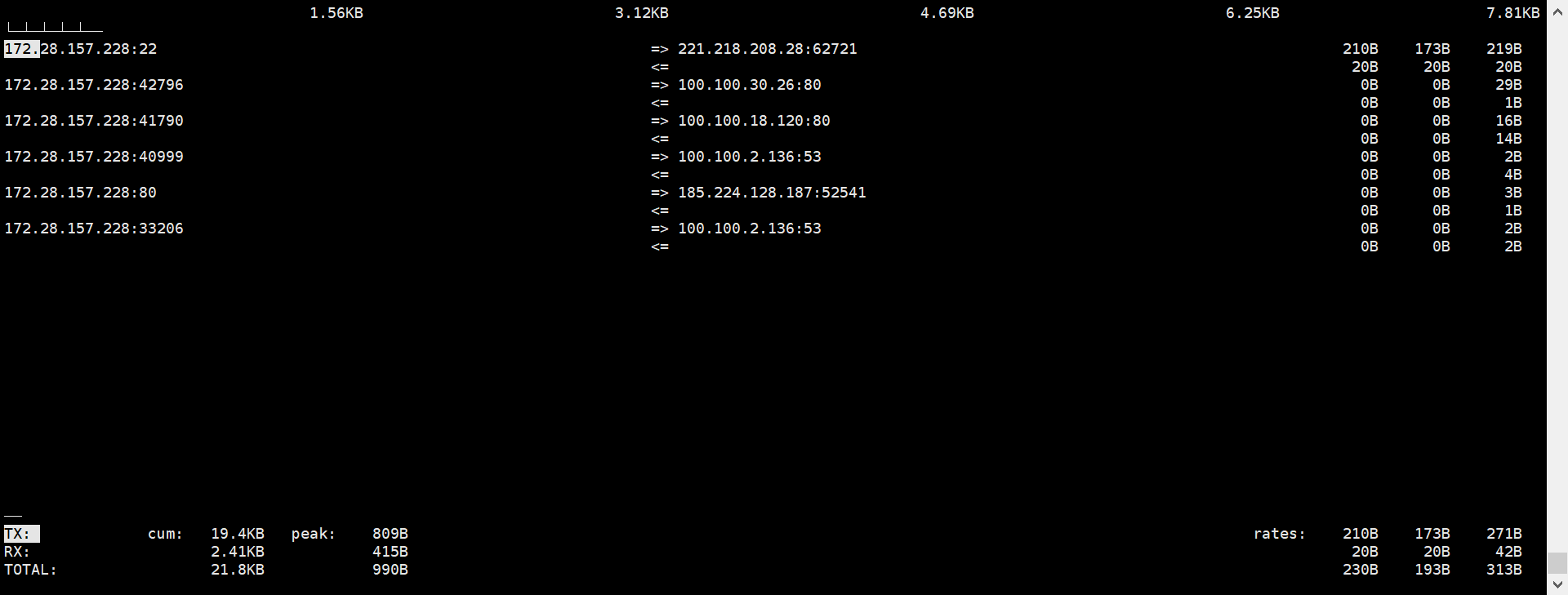
root@iZ2zei5cw2j6q770mgp5kvZ:~/packages# iftop -nNP -Bt -s 1
interface: eth0
IP address is: 172.28.157.228
MAC address is: 00:16:3e:39:38:2e
Listening on eth0
# Host name (port/service if enabled) last 2s last 10s last 40s cumulative
--------------------------------------------------------------------------------------------
1 172.28.157.228:42796 => 1.62KB 1.62KB 1.62KB 3.25KB
100.100.30.26:80 <= 60B 60B 60B 120B
2 172.28.157.228:22 => 54B 54B 54B 108B
221.218.208.28:62721 <= 20B 20B 20B 40B
--------------------------------------------------------------------------------------------
Total send rate: 1.68KB 1.68KB 1.68KB
Total receive rate: 80B 80B 80B
Total send and receive rate: 1.75KB 1.75KB 1.75KB
--------------------------------------------------------------------------------------------
Peak rate (sent/received/total): 1.68KB 80B 1.75KB
Cumulative (sent/received/total): 3.35KB 160B 3.51KB
============================================================================================
root@iZ2zei5cw2j6q770mgp5kvZ:~/packages#
# -B以字节为单位进行显示,默认是位
root@iZ2zei5cw2j6q770mgp5kvZ:~/packages# iftop -nNBP -i eth0 -t -s 1
interface: eth0
IP address is: 172.28.157.228
MAC address is: 00:16:3e:39:38:2e
Listening on eth0
# Host name (port/service if enabled) last 2s last 10s last 40s cumulative
--------------------------------------------------------------------------------------------
1 172.28.157.228:42796 => 1.04KB 1.04KB 1.04KB 2.09KB
100.100.30.26:80 <= 40B 40B 40B 80B
2 172.28.157.228:22 => 54B 54B 54B 108B
221.218.208.28:62721 <= 20B 20B 20B 40B
--------------------------------------------------------------------------------------------
Total send rate: 1.10KB 1.10KB 1.10KB
Total receive rate: 60B 60B 60B
Total send and receive rate: 1.16KB 1.16KB 1.16KB
--------------------------------------------------------------------------------------------
Peak rate (sent/received/total): 1.10KB 60B 1.16KB
Cumulative (sent/received/total): 2.19KB 120B 2.31KB
============================================================================================
root@iZ2zei5cw2j6q770mgp5kvZ:~/packages# root@iZ2zei5cw2j6q770mgp5kvZ:~/packages# iftop -nNBP -i eth0
进程流量
精确到进程的网络速度
# 查看进程的流量情况.
# 方法01: iftop,ss,ps 一起使用
iftop找出端口.
ss找出端口对应的进程号(pid)
ps根据pid过滤进程名字.
# 方法02: nethogs
nethogs
# 方法03:ntop 可以用docker部署或二进制
https://www.ntop.org/get-started/download/
.......
3.4 DNS解析
dig dns解析查询
host
nslookup
whois 查看域名信息. jwhois/whois 过滤 expir
dig www.baidu.com
host www.baidu.com
nslookup www.baidu.com
#方法01 dig
[root@Kylin-V10-sp3 ~]# dig baidu.com
; <<>> DiG 9.11.21-9.11.21-18.ky10 <<>> baidu.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 65434
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;baidu.com. IN A
;; ANSWER SECTION:
baidu.com. 34 IN A 110.242.68.66
baidu.com. 34 IN A 39.156.66.10
;; Query time: 53 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: 三 9月 18 21:41:23 CST 2024
;; MSG SIZE rcvd: 70
[root@Kylin-V10-sp3 ~]#
#方法02
[root@Kylin-V10-sp3 ~]# host jd.com
jd.com has address 211.144.27.126
jd.com has address 111.13.149.108
jd.com has address 211.144.24.218
jd.com has address 106.39.171.134
jd.com mail is handled by 30 mx1.jd.com.
jd.com mail is handled by 5 mx.jd.com.
[root@Kylin-V10-sp3 ~]#
#方法03
[root@Kylin-V10-sp3 ~]# nslookup www.baidu.com
Server: 8.8.8.8
Address: 8.8.8.8#53
Non-authoritative answer:
www.baidu.com canonical name = www.a.shifen.com.
Name: www.a.shifen.com
Address: 110.242.68.3
Name: www.a.shifen.com
Address: 110.242.68.4
Name: www.a.shifen.com
Address: 2408:871a:2100:3:0:ff:b025:348d
Name: www.a.shifen.com
Address: 2408:871a:2100:2:0:ff:b09f:237
[root@Kylin-V10-sp3 ~]#3.5 追踪命令
检查线路是否通畅. ping
批量检查是否可以ping通. fping
访问云服务器失败,怀疑是阿里云的问题,阿里云那边就会让你发出路由追踪的结果. tracert(windows) traceroute (linux ) 路径追踪
#01 两点之间.
ping baidu.com
#02
tracert(windows) traceroute (linux yum install -y traceroute)
traceroute -nI www.baidu.com #默认使用udp协议,-I使用icmp协议
icmp表示使用ping.
[root@Kylin-V10-sp3 ~/test]# traceroute -nI www.baidu.com
traceroute to www.baidu.com (110.242.68.4), 30 hops max, 60 byte packets
1 10.0.0.2 0.477 ms 0.433 ms 0.413 ms
2 192.168.15.1 1.593 ms 1.576 ms 1.555 ms
3 192.168.201.1 1.532 ms 1.512 ms 2.527 ms
4 221.218.208.1 9.184 ms 9.192 ms 9.172 ms
5 * * *
6 * * *
7 * * *
8 * 110.242.66.170 12.383 ms 12.367 ms
9 221.194.45.134 14.279 ms 14.204 ms 14.150 ms
10 * * *
11 * * *
12 * * *
13 110.242.68.4 13.963 ms 13.996 ms 13.978 ms
[root@Kylin-V10-sp3 ~/test]#
[c:\~]$ tracert -d www.baidu.com
通过最多 30 个跃点跟踪
到 www.a.shifen.com [110.242.68.3] 的路由:
1 <1 毫秒 1 ms <1 毫秒 192.168.17.1
2 <1 毫秒 <1 毫秒 <1 毫秒 192.168.1.1
3 7 ms 2 ms 3 ms 125.33.244.1
4 5 ms 3 ms 3 ms 123.126.26.57
5 8 ms 6 ms 8 ms 202.106.34.17
6 5 ms 4 ms 4 ms 61.49.214.5
7 * 6 ms * 219.158.11.66
8 11 ms 11 ms 11 ms 110.242.66.182
9 * * * 请求超时。
10 * * * 请求超时。
11 * * * 请求超时。
12 * * * 请求超时。
13 14 ms 12 ms 12 ms 110.242.68.3
#03 fping批量检查ip或域名
[root@Kylin-V10-sp3 ~]fping 10.0.0.2 baidu.com jd.com taobao.com 12306.cn
cctv.cn
cat url.txt
[root@Kylin-V10-sp3 ~]# cat url.txt
10.0.0.2
baidu.com
jd.com
taobao.com
12306.cn
cctv.cn
[root@Kylin-V10-sp3 ~/test]# fping -f url.txt
jd.com is alive
12306.cn is alive
taobao.com is alive
cctv.cn is alive
10.0.0.1 is alive
10.0.0.36 is alive
idu.com is alive
[root@Kylin-V10-sp3 ~/test]# 3.6 命令小结
|
网络命令 |
linux |
windows |
|
查询ip地址 |
ip/ifconfig |
ipconfig |
|
检查端口号 |
ss/netstat/lsof / nc/telnet/nmap |
netstat -ant |
|
检查连接情况 |
ss -ant /netstat -ant |
netstat -ant |
|
检查速度 |
iftop /nethogs |
|
|
dns解析 |
dig/host/nslookup |
nslookup |
|
域名信息 |
nslookup |
网站查看 |
|
路径追踪 |
traceroute, -nI tracert |
tracert |
|
检查链路是否通畅 |
ping,fping |
ping |
|
查询当前系统配置的网关/路由 信息 |
ip ro /route -n |
route print |
[root@Kylin-V10-sp3 ~/test]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 10.0.0.2 0.0.0.0 UG 100 0 0 eth0
10.0.0.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0
[root@Kylin-V10-sp3 ~/test]#
[root@Kylin-V10-sp3 ~/test]# ip route
default via 10.0.0.2 dev eth0 proto static metric 100
10.0.0.0/24 dev eth0 proto kernel scope link src 10.0.0.36 metric 100
[root@Kylin-V10-sp3 ~/test]#4. IP-了解
4.1 格式与分类
点分十进制ip(ipv4) 32位 2^32 点分十进制 xxx.xxx.xxx.xxx
ipv6,128位 2^128
ip地址组成:网络位(居住的校区),主机位(楼房间)
通过子网掩码划分网络位.
根据网络位不同划分ip地址分类

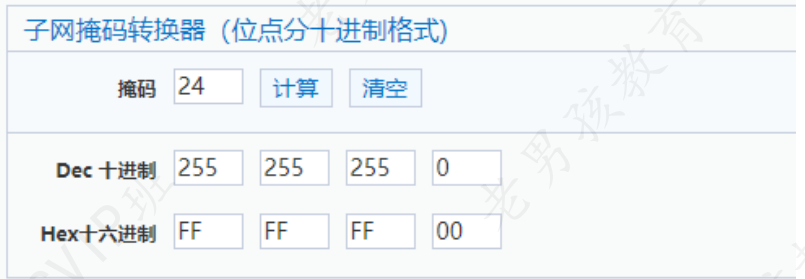
4.2 子网掩码
子网掩码: 用来绝对局域网(网段中)最多有多少台机器.
子网掩码控制:网络位,主机位
PREFIX=24
NETMASK=255.255.255.0
子网掩码计算器:https://www.sojson.com/convert/subnetmask.html
子网掩码计算器:https://www.36130.com/subnetmask/





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY
· 【自荐】一款简洁、开源的在线白板工具 Drawnix
2020-09-18 PostgreSQL允许远程连接
2019-09-18 obj + mtl 格式说明
2019-09-18 3D中OBJ文件格式详解
2019-09-18 wampserver环境配置局域网访问