安装LDAP整合SpringBoot
LDAP简介
LDAP(轻量级目录访问协议,Lightweight Directory Access Protocol)是实现提供被称为目录服务的信息服务。目录服务是一种特殊的数据库系统,其专门针对读取,浏览和搜索操作进行了特定的优化。目录一般用来包含描述性的,基于属性的信息并支持精细复杂的过滤能力。目录一般不支持通用数据库针对大量更新操作操作需要的复杂的事务管理或回卷策略。而目录服务的更新则一般都非常简单。这种目录可以存储包括个人信息、web链结、jpeg图像等各种信息。为了访问存储在目录中的信息,就需要使用运行在TCP/IP 之上的访问协议—LDAP。
LDAP目录中的信息是是按照树型结构组织,具体信息存储在条目(entry)的数据结构中。条目相当于关系数据库中表的记录;条目是具有区别名DN (Distinguished Name)的属性(Attribute),DN是用来引用条目的,DN相当于关系数据库表中的关键字(Primary Key)。属性由类型(Type)和一个或多个值(Values)组成,相当于关系数据库中的字段(Field)由字段名和数据类型组成,只是为了方便检索的需要,LDAP中的Type可以有多个Value,而不是关系数据库中为降低数据的冗余性要求实现的各个域必须是不相关的。LDAP中条目的组织一般按照地理位置和组织关系进行组织,非常的直观。LDAP把数据存放在文件中,为提高效率可以使用基于索引的文件数据库,而不是关系数据库。类型的一个例子就是mail,其值将是一个电子邮件地址。
LDAP的信息是以树型结构存储的,在树根一般定义国家(c=CN)或域名(dc=com),在其下则往往定义一个或多个组织 (organization)(o=Acme)或组织单元(organizational units) (ou=People)。一个组织单元可能包含诸如所有雇员、大楼内的所有打印机等信息。此外,LDAP支持对条目能够和必须支持哪些属性进行控制,这是有一个特殊的称为对象类别(objectClass)的属性来实现的。该属性的值决定了该条目必须遵循的一些规则,其规定了该条目能够及至少应该包含哪些属性。例如:inetorgPerson对象类需要支持sn(surname)和cn(common name)属性,但也可以包含可选的如邮件,电话号码等属性。
LDAP简称对应
- o:organization(组织-公司)
- ou:organization unit(组织单元-部门)
- c:countryName(国家)
- dc:domainComponent(域名)
- sn:surname(姓氏)
- cn:common name(常用名称)
安装LADP
参考:https://blog.csdn.net/woloqun/article/details/89216120
关闭selinux和防火墙【很重要】
sed -i '/SELINUX/s/enforcing/disabled/' /etc/selinux/config && setenforce 0&& systemctl disable firewalld.service && systemctl stop firewalld.service && shutdown -r now
安装OpenLdap
yum -y install openldap compat-openldap openldap-clients \
openldap-servers openldap-servers-sql openldap-devel migrationtools
查看版本OpenLdap版本
[root@kudu ~]# slapd -VV
@(#) $OpenLDAP: slapd 2.4.44 (Jan 29 2019 17:42:45) $
mockbuild@x86-01.bsys.centos.org:/builddir/build/BUILD/openldap-2.4.44/openldap-2.4.44/servers/slapd
配置管理员密码
这里明文密码设置成hadoop
[root@kudu ~]# slappasswd -s hadoop
{SSHA}RpuO1/rVtgStK4acAM3oqBu/YihUReq1
修改olcDatabase={2}hdb.ldif文件
vi /etc/openldap/slapd.d/cn=config/olcDatabase={2}hdb.ldif
末尾添加一行
olcRootPW: {SSHA}RpuO1/rVtgStK4acAM3oqBu/YihUReq1
修改
olcSuffix: dc=haohaozhu,dc=com
olcRootDN: cn=Manager,dc=haohaozhu,dc=com
完整文件
# AUTO-GENERATED FILE - DO NOT EDIT!! Use ldapmodify.
# CRC32 b9e69d7c
dn: olcDatabase={2}hdb
objectClass: olcDatabaseConfig
objectClass: olcHdbConfig
olcDatabase: {2}hdb
olcDbDirectory: /var/lib/ldap
olcSuffix: dc=haohaozhu,dc=com
olcRootDN: cn=Manager,dc=haohaozhu,dc=com
olcDbIndex: objectClass eq,pres
olcDbIndex: ou,cn,mail,surname,givenname eq,pres,sub
structuralObjectClass: olcHdbConfig
entryUUID: 46d0a66c-f07f-1038-8e63-7f8e33666833
creatorsName: cn=config
createTimestamp: 20190411082641Z
entryCSN: 20190411082641.038876Z#000000#000#000000
modifiersName: cn=config
modifyTimestamp: 20190411082641Z
olcRootPW: {SSHA}RpuO1/rVtgStK4acAM3oqBu/YihUReq1
修改olcDatabase={1}monitor.ldif文件
vi /etc/openldap/slapd.d/cn=config/olcDatabase\=\{1\}monitor.ldif
修改如下行
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=extern
al,cn=auth" read by dn.base="cn=Manager,dc=haohaozhu,dc=com" read by * none
完整文件
# AUTO-GENERATED FILE - DO NOT EDIT!! Use ldapmodify.
# CRC32 ffaba6ec
dn: olcDatabase={1}monitor
objectClass: olcDatabaseConfig
olcDatabase: {1}monitor
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=extern
al,cn=auth" read by dn.base="cn=Manager,dc=haohaozhu,dc=com" read by * none
structuralObjectClass: olcDatabaseConfig
entryUUID: 46d0a2f2-f07f-1038-8e62-7f8e33666833
creatorsName: cn=config
createTimestamp: 20190411082641Z
entryCSN: 20190411082641.038787Z#000000#000#000000
modifiersName: cn=config
modifyTimestamp: 20190411082641Z
验证配置文件是否正确
[root@kudu ~]# slaptest -u
5caefca6 ldif_read_file: checksum error on "/etc/openldap/slapd.d/cn=config/olcDatabase={1}monitor.ldif"
5caefca6 ldif_read_file: checksum error on "/etc/openldap/slapd.d/cn=config/olcDatabase={2}hdb.ldif"
config file testing succeeded
启动服务&&查看服务
systemctl enable slapd
systemctl start slapd
systemctl status slapd
输出
[root@kudu ~]# systemctl status slapd
● slapd.service - OpenLDAP Server Daemon
Loaded: loaded (/usr/lib/systemd/system/slapd.service; enabled; vendor preset: disabled)
Active: active (running) since 四 2019-04-11 16:38:08 CST; 5s ago
Docs: man:slapd
man:slapd-config
man:slapd-hdb
man:slapd-mdb
file:///usr/share/doc/openldap-servers/guide.html
Process: 12884 ExecStart=/usr/sbin/slapd -u ldap -h ${SLAPD_URLS} $SLAPD_OPTIONS (code=exited, status=0/SUCCESS)
Process: 12870 ExecStartPre=/usr/libexec/openldap/check-config.sh (code=exited, status=0/SUCCESS)
Main PID: 12886 (slapd)
CGroup: /system.slice/slapd.service
└─12886 /usr/sbin/slapd -u ldap -h ldapi:/// ldap:///
4月 11 16:38:08 kudu systemd[1]: Starting OpenLDAP Server Daemon...
4月 11 16:38:08 kudu runuser[12873]: pam_unix(runuser:session): session opened for user ldap by (uid=0)
4月 11 16:38:08 kudu slapd[12884]: @(#) $OpenLDAP: slapd 2.4.44 (Jan 29 2019 17:42:45) $
mockbuild@x86-01.bsys.centos.org:/builddir/build/BUILD/openldap-2.4.44/openldap-2.4.44/servers/slapd
4月 11 16:38:08 kudu slapd[12884]: ldif_read_file: checksum error on "/etc/openldap/slapd.d/cn=config/olcDatabase={1}monitor.ldif"
4月 11 16:38:08 kudu slapd[12884]: ldif_read_file: checksum error on "/etc/openldap/slapd.d/cn=config/olcDatabase={2}hdb.ldif"
4月 11 16:38:08 kudu slapd[12884]: tlsmc_get_pin: INFO: Please note the extracted key file will not be protected with a PIN any more, however it will be still protec...permissions.
4月 11 16:38:08 kudu slapd[12886]: hdb_db_open: warning - no DB_CONFIG file found in directory /var/lib/ldap: (2).
Expect poor performance for suffix "dc=haohaozhu,dc=com".
4月 11 16:38:08 kudu slapd[12886]: slapd starting
4月 11 16:38:08 kudu systemd[1]: Started OpenLDAP Server Daemon.
Hint: Some lines were ellipsized, use -l to show in full.
查看监听端口389
[root@kudu ~]# netstat -anpl|grep 389
tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 12886/slapd
tcp6 0 0 :::389 :::* LISTEN 12886/slapd
配置OpenLDAP数据库
cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
chown ldap:ldap -R /var/lib/ldap
chmod 700 -R /var/lib/ldap
ll /var/lib/ldap/
注意:/var/lib/ldap/就是BerkeleyDB数据库默认存储的路径。
导入基本Schema
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
输出
[root@kudu ~]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=cosine,cn=schema,cn=config"
[root@kudu ~]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=nis,cn=schema,cn=config"
[root@kudu ~]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=inetorgperson,cn=schema,cn=config"
修改migrate_common.ph文件
vi /usr/share/migrationtools/migrate_common.ph
修改如下变量
$DEFAULT_MAIL_DOMAIN = "haohaozhu.com";
$DEFAULT_BASE = "dc=haohaozhu,dc=com";
$EXTENDED_SCHEMA = 1;
添加用户及用户组
默认情况下OpenLDAP是没有普通用户的,但是有一个管理员用户。管理用户就是前面我们刚刚配置的root。
现在我们把系统中的用户,添加到OpenLDAP中。为了进行区分,我们现在新加两个用户ldapuser1和ldapuser2,和两个用户组ldapgroup1和ldapgroup2,如下:
添加用户组,使用如下命令:
groupadd ldapgroup1
groupadd ldapgroup2
添加用户并设置密码,使用如下命令
useradd -g ldapgroup1 ldapuser1
useradd -g ldapgroup2 ldapuser2
passwd ldapuser1
passwd ldapuser2
密码都设置为:hadoop
提取用户和组
grep ":10[0-9][0-9]" /etc/passwd > /root/users
grep ":10[0-9][0-9]" /etc/group > /root/groups
结果
[root@kudu ~]# cat users
ldapuser1:x:1000:1000::/home/ldapuser1:/bin/bash
ldapuser2:x:1001:1001::/home/ldapuser2:/bin/bash
[root@kudu ~]# cat groups
ldapgroup1:x:1000:
ldapgroup2:x:1001:
生成用户和组的ldif文件
/usr/share/migrationtools/migrate_passwd.pl /root/users > /root/users.ldif
/usr/share/migrationtools/migrate_group.pl /root/groups > /root/groups.ldif
cat /root/users.ldif
cat /root/groups.ldif
输出
[root@kudu ~]# cat /root/groups.ldif
dn: cn=ldapgroup1,ou=Group,dc=haohaozhu,dc=com
objectClass: posixGroup
objectClass: top
cn: ldapgroup1
userPassword: {crypt}x
gidNumber: 1000
dn: cn=ldapgroup2,ou=Group,dc=haohaozhu,dc=com
objectClass: posixGroup
objectClass: top
cn: ldapgroup2
userPassword: {crypt}x
gidNumber: 1001
导入用户及用户组到OpenLDAP数据库
配置openldap基础的数据库,如下:
cat > /root/base.ldif << EOF
dn: dc=haohaozhu,dc=com
o: haohaozhu com
dc: haohaozhu
objectClass: top
objectClass: dcObject
objectclass: organization
dn: cn=Manager,dc=haohaozhu,dc=com
cn: Manager
objectClass: organizationalRole
description: Directory Manager
dn: ou=People,dc=haohaozhu,dc=com
ou: People
objectClass: top
objectClass: organizationalUnit
dn: ou=Group,dc=haohaozhu,dc=com
ou: Group
objectClass: top
objectClass: organizationalUnit
EOF
导入基础数据库,使用如下命令:
ldapadd -x -w "hadoop" -D "cn=Manager,dc=haohaozhu,dc=com" -f /root/base.ldif
输出
[root@kudu ~]# ldapadd -x -w "hadoop" -D "cn=Manager,dc=haohaozhu,dc=com" -f /root/base.ldif
adding new entry "dc=haohaozhu,dc=com"
adding new entry "cn=Manager,dc=haohaozhu,dc=com"
adding new entry "ou=People,dc=haohaozhu,dc=com"
adding new entry "ou=Group,dc=haohaozhu,dc=com"
导入用户
ldapadd -x -w "hadoop" -D "cn=Manager,dc=haohaozhu,dc=com" -f /root/users.ldif
输出
[root@kudu ~]# ldapadd -x -w "hadoop" -D "cn=Manager,dc=haohaozhu,dc=com" -f /root/users.ldif
adding new entry "uid=ldapuser1,ou=People,dc=haohaozhu,dc=com"
adding new entry "uid=ldapuser2,ou=People,dc=haohaozhu,dc=com"
把OpenLDAP用户加入到用户组
尽管我们已经把用户和用户组信息,导入到OpenLDAP数据库中了。但实际上目前OpenLDAP用户和用户组之间是没有任何关联的。
如果我们要把OpenLDAP数据库中的用户和用户组关联起来的话,我们还需要做另外单独的配置。
现在我们要把ldapuser1用户加入到ldapgroup1用户组,需要新建添加用户到用户组的ldif文件,如下
cat > add_user_to_groups.ldif << "EOF"
dn: cn=ldapgroup1,ou=Group,dc=haohaozhu,dc=com
changetype: modify
add: memberuid
memberuid: ldapuser1
EOF
导入ldif
ldapadd -x -w "hadoop" -D "cn=Manager,dc=haohaozhu,dc=com" -f /root/add_user_to_groups.ldif
输出
[root@kudu ~]# ldapadd -x -w "hadoop" -D "cn=Manager,dc=haohaozhu,dc=com" -f /root/add_user_to_groups.ldif
modifying entry "cn=ldapgroup1,ou=Group,dc=haohaozhu,dc=com"
查询用户
ldapsearch -LLL -x -D 'cn=Manager,dc=haohaozhu,dc=com' -w "hadoop" -b 'dc=haohaozhu,dc=com' 'cn=ldapgroup1'
输出
[root@kudu ~]# ldapsearch -LLL -x -D 'cn=Manager,dc=haohaozhu,dc=com' -w "hadoop" -b 'dc=haohaozhu,dc=com' 'cn=ldapgroup1'
dn: cn=ldapgroup1,ou=Group,dc=haohaozhu,dc=com
objectClass: posixGroup
objectClass: top
cn: ldapgroup1
userPassword:: e2NyeXB0fXg=
gidNumber: 1000
memberUid: ldapuser1
开启OpenLDAP日志访问功能
默认情况下OpenLDAP是没有启用日志记录功能的,但是在实际使用过程中,我们为了定位问题需要使用到OpenLDAP日志。
新建日志配置ldif文件,如下
cat > /root/loglevel.ldif << "EOF"
dn: cn=config
changetype: modify
replace: olcLogLevel
olcLogLevel: stats
EOF
导入到OpenLDAP中,并重启OpenLDAP服务,如下:
ldapmodify -Y EXTERNAL -H ldapi:/// -f /root/loglevel.ldif
systemctl restart slapd
修改rsyslog配置文件,并重启rsyslog服务,如下:
cat >> /etc/rsyslog.conf << "EOF"
local4.* /var/log/slapd.log
EOF
systemctl restart rsyslog
安装和配置LDAP管理工具PHPldapadmin
[root@localhost ~]# yum -y install httpd php php-ldap php-gd php-mbstring php-pear php-bcmath php-xml
[root@localhost ~]# yum -y install epel-release
[root@localhost ~]# yum --enablerepo=epel -y install phpldapadmin
修改配置文件
[root@localhost ~]# vim /etc/phpldapadmin/config.php
#397行取消注释,398行添加注释
$servers->setValue('login','attr','dn');
// $servers->setValue('login','attr','uid');
[root@localhost ~]# vim /etc/httpd/conf.d/phpldapadmin.conf
// 修改配置
<IfModule mod_authz_core.c>
# Apache 2.4
Require local
#添加一行内容,指定可访问的ip段
Require ip 172.16.186.58
</IfModule>
注:我这里和参考博客不一样,具体如下
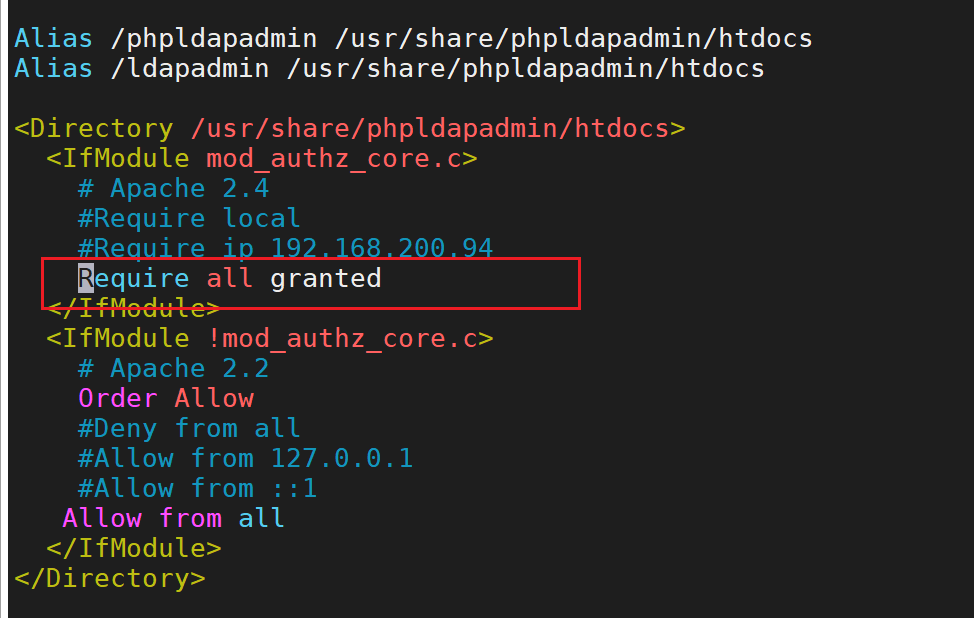
设置开机自启并启动Apache:
systemctl enable httpd
systemctl start httpd
登陆web控制台
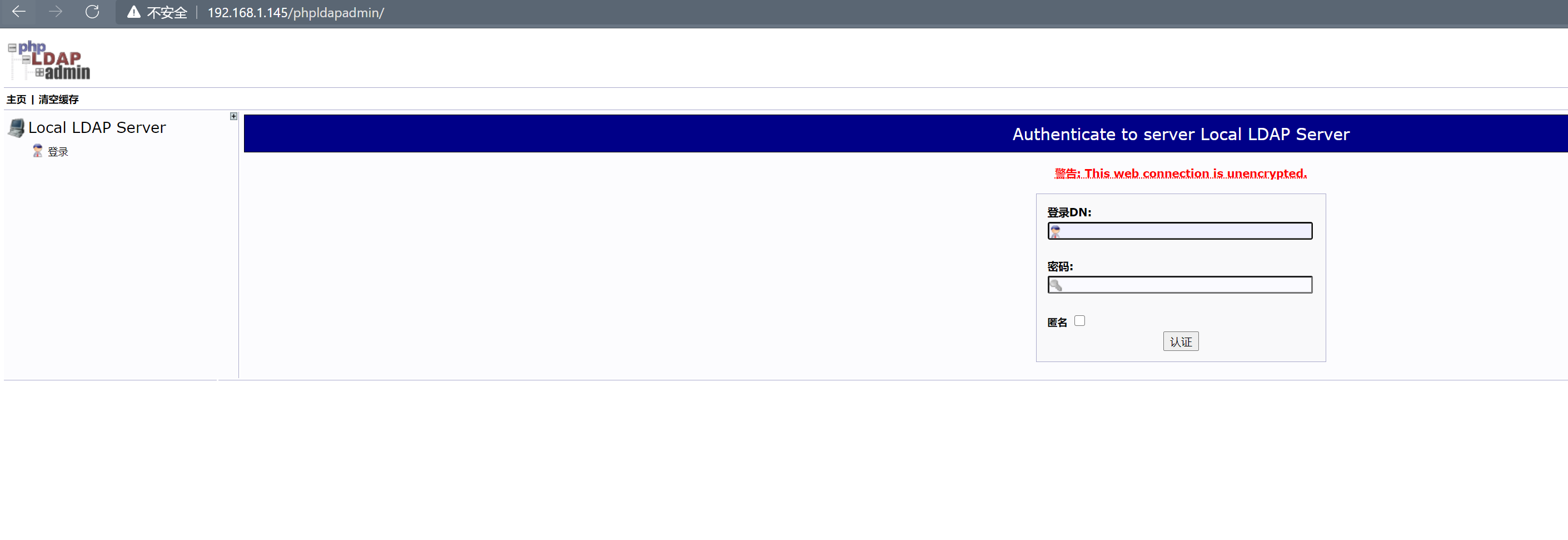
用户名:cn=Manager,dc=haohaozhu,dc=com
密码:hadoop
整合SpringBoot
配置
spring:
ldap:
urls: ldap://192.168.1.145:389
base: dc=haohaozhu,dc=com
username: uid=ldapuser1,ou=People,dc=haohaozhu,dc=com
password: hadoop
#username: cn=Manager,dc=haohaozhu,dc=com
类
package com.dalinpai.springbootldap.bo;
import org.springframework.ldap.odm.annotations.Attribute;
import org.springframework.ldap.odm.annotations.DnAttribute;
import org.springframework.ldap.odm.annotations.Entry;
import org.springframework.ldap.odm.annotations.Id;
import javax.naming.Name;
/**
* @author WGR
* @create 2021/4/16 -- 17:47
*/
@Entry(base = "ou=people,dc=didispace,dc=com", objectClasses = "inetOrgPerson")
public class Person {
@Id
private Name id;
@DnAttribute(value = "uid")
private String uid;
@Attribute(name = "cn")
private String commonName;
@Attribute(name = "sn")
private String suerName;
private String userPassword;
@Attribute(name="ou")
private String group;
public Name getId() {
return id;
}
public void setId(Name id) {
this.id = id;
}
public String getUid() {
return uid;
}
public void setUid(String uid) {
this.uid = uid;
}
public String getCommonName() {
return commonName;
}
public void setCommonName(String commonName) {
this.commonName = commonName;
}
public String getSuerName() {
return suerName;
}
public void setSuerName(String suerName) {
this.suerName = suerName;
}
public String getUserPassword() {
return userPassword;
}
public void setUserPassword(String userPassword) {
this.userPassword = userPassword;
}
public String getGroup() {
return group;
}
public void setGroup(String group) {
this.group = group;
}
@Override
public String toString() {
return "Person{" +
"id=" + id +
", uid='" + uid + '\'' +
", commonName='" + commonName + '\'' +
", suerName='" + suerName + '\'' +
", userPassword='" + userPassword + '\'' +
", group='" + group + '\'' +
'}';
}
}
/**
* @author WGR
* @create 2021/4/16 -- 19:29
*/
public interface PersonRepository extends CrudRepository<Person, Name> {
}
@Autowired
private PersonRepository personRepository;
@Autowired
private LdapTemplate template;
@Test
public void findAll() throws Exception {
personRepository.findAll().forEach(p -> {
System.out.println(p);
});
}
@Test
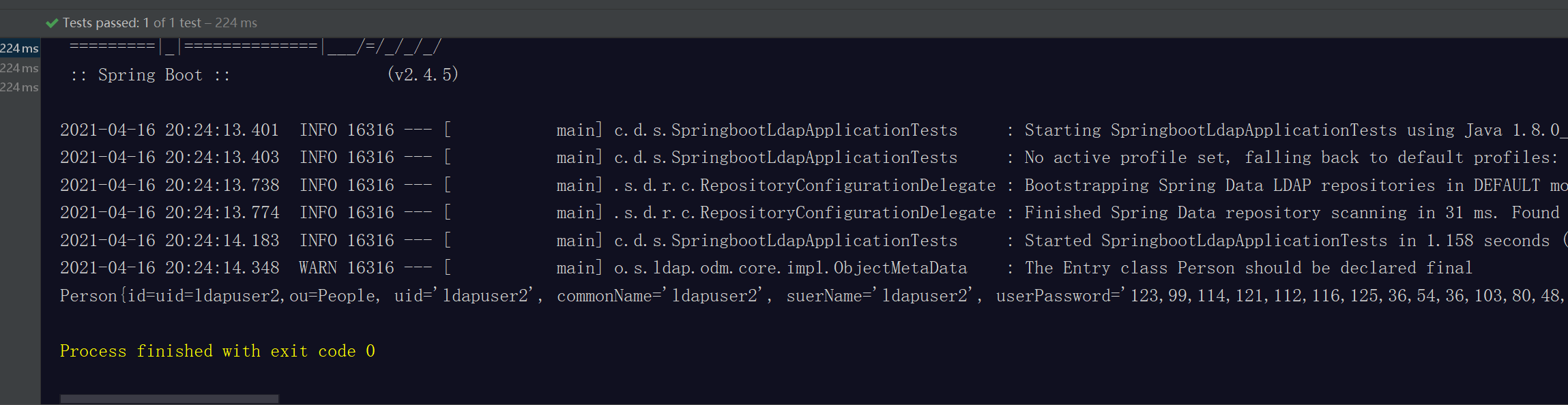
public void findAll2(){
Person person = template.findOne(query().where("uid").is("ldapuser2"), Person.class);
System.out.println(person);
}
测试结果:


 浙公网安备 33010602011771号
浙公网安备 33010602011771号