zookeeper的权限控制
zookeeper的acl权限控制
概述
zookeeper 类似文件系统,client 可以创建节点、更新节点、删除节点,那么如何做到节点的权限的控制呢?zookeeper的access control list 访问控制列表可以做到acl 权限控制,使用scheme:id:permission 来标识,主要涵盖 3 个方面:
- 权限模式(scheme):授权的策略
- 授权对象(id):授权的对象
- 权限(permission):授予的权限
其特性如下:
zooKeeper的权限控制是基于每个znode节点的,需要对每个节点设置权限每个znode支持设置多种权限控制方案和多个权限子节点不会继承父节点的权限,客户端无权访问某节点,但可能可以访问它的子节点
setAcl /test2 ip:192.168.60.130:crwda // 将节点权限设置为Ip:192.168.60.130
权限模式
采用何种方式授权
| 方案 | 描述 |
| world | 只有一个用户: anyone, 代表登录zokeeper所有人(默认) |
| ip | 对客户端使用IP地址认证 |
| auth | 使用已添加认证的用户认证 |
| digest | 使用“用户名:密码”方式认证 |
授权的对象
授权对象ID是指,权限赋予的实体,例如:IP 地址或用户。
授予的权限
world: 它下面只有一个id, 叫anyone, world:anyone代表任何人,zookeeper中对所有人有权限的结点就是属于world:anyone的
auth: 它不需要id, 只要是通过authentication的user都有权限(zookeeper支持通过kerberos来进行authencation, 也支持username/password形式的authentication)
digest: 它对应的id为username:BASE64(SHA1(password)),它需要先通过username:password形式的authentication
ip: 它对应的id为客户机的IP地址,设置的时候可以设置一个ip段,比如ip:192.168.1.0/16, 表示匹配前16个bit的IP段
super: 在这种scheme情况下,对应的id拥有超级权限,可以做任何事情(cdrwa)
CREATE(c): 创建权限,可以在在当前node下创建child node
DELETE(d): 删除权限,可以删除当前的node
READ(r): 读权限,可以获取当前node的数据,可以list当前node所有的child nodes
WRITE(w): 写权限,可以向当前node写数据
ADMIN(a): 管理权限,可以设置当前node的permission
这5种权限简写为cdrwa,注意:这5种权限中,delete是指对子节点的删除权限,其它4种
权限指对自身节点的操作权限
| 权限 | ACL简写 | 描述 |
| create | c | 可以创建子节点 |
| delete | d | 可以删除子节点(仅下一级节点) |
| read | r | 可以读取节点数据及显示子节点列表 |
| write | w | 可以设置节点数据 |
| admin | a | 可以设置节点访问控制列表权限 |
授权的相关命令
| 命令 | 使用方式 | 描述 |
| getAcl | getAcl | 读取ACL权限 |
| setAcl | setAcl | 设置ACL权限 |
| addauth | addauth | 添加认证用户 |
案例
world授权模式:
命令
[zk: localhost:2181(CONNECTED) 3] create /node1 "node1" Created /node1 [zk: localhost:2181(CONNECTED) 5] getAcl /node1 'world,'anyone : cdrwa [zk: localhost:2181(CONNECTED) 6] setAcl /node1 world:anyone:cdraw cZxid = 0x37 ctime = Tue Apr 21 20:34:49 CST 2020 mZxid = 0x37 mtime = Tue Apr 21 20:34:49 CST 2020 pZxid = 0x37 cversion = 0 dataVersion = 0 aclVersion = 1 ephemeralOwner = 0x0 dataLength = 5 numChildren = 0 [zk: localhost:2181(CONNECTED) 7]
IP授权模式:
命令
setAcl <path> ip:<ip>:<acl>
案例
注意:远程登录zookeeper命令:./zkCli.sh -server ip
[zk: 47.231.431.657(CONNECTED) 0] create /node2 "node2" Created /node2 [zk: 47.231.431.657(CONNECTED) 3] getAcl /node2 'world,'anyone : cdrwa [zk: 47.231.431.657(CONNECTED) 4] setAcl /node2 ip:192.168.60.129:cdrwa cZxid = 0x3a ctime = Tue Apr 21 20:39:09 CST 2020 mZxid = 0x3a mtime = Tue Apr 21 20:39:09 CST 2020 pZxid = 0x3a cversion = 0 dataVersion = 0 aclVersion = 1 ephemeralOwner = 0x0 dataLength = 5 numChildren = 0 [zk: 47.231.431.657(CONNECTED) 5] getAcl /node2 'ip,'192.168.60.129 : cdrwa
[zk: 47.231.431.657(CONNECTED) 6] get /node2
Authentication is not valid : /node2
[zk: 47.231.431.657(CONNECTED) 7]
Auth授权模式:
命令
addauth digest <user>:<password> #添加认证用户
setAcl <path> auth:<user>:<acl>
案例
[zk: localhost:2181(CONNECTED) 7] create /node3 "node3" Created /node3 [zk: localhost:2181(CONNECTED) 8] addauth digest dalianpai:123456 [zk: localhost:2181(CONNECTED) 9] setAcl /node3 auth:dalianpai:cdrwa cZxid = 0x3d ctime = Tue Apr 21 20:45:20 CST 2020 mZxid = 0x3d mtime = Tue Apr 21 20:45:20 CST 2020 pZxid = 0x3d cversion = 0 dataVersion = 0 aclVersion = 1 ephemeralOwner = 0x0 dataLength = 5 numChildren = 0 [zk: localhost:2181(CONNECTED) 10] getAcl /node3 'digest,'dalianpai:A7v7a7NwQ63ZrUvGjVLuE0PHZmQ= : cdrwa [zk: localhost:2181(CONNECTED) 11] get /node3 node3 cZxid = 0x3d ctime = Tue Apr 21 20:45:20 CST 2020 mZxid = 0x3d mtime = Tue Apr 21 20:45:20 CST 2020 pZxid = 0x3d cversion = 0 dataVersion = 0 aclVersion = 1 ephemeralOwner = 0x0 dataLength = 5 numChildren = 0 [zk: localhost:2181(CONNECTED) 12]
Digest授权模式:
命令
setAcl <path> digest:<user>:<password>:<acl>
这里的密码是经过SHA1及BASE64处理的密文,在SHELL中可以通过以下命令计算:
echo -n <user>:<password> | openssl dgst -binary -sha1 | openssl base64
先来计算一个密文
[root@iZ1la3d1xbmukrZ bin]# echo -n wgr:12345 | openssl dgst -binary -sha1 | openssl base64 sfWvAOV+8UWBCBQJ3dDPaHw2f+Q= [root@iZ1la3d1xbmukrZ bin]#
[zk: localhost:2181(CONNECTED) 16] create /node5 "node5" Created /node5 [zk: localhost:2181(CONNECTED) 17] setAcl /node node4 node5 node2 node3 node1 [zk: localhost:2181(CONNECTED) 17] setAcl /node5 digest:wgr:sfWvAOV+8UWBCBQJ3dDPaHw2f+Q=:cdrwa cZxid = 0x43 ctime = Tue Apr 21 20:57:34 CST 2020 mZxid = 0x43 mtime = Tue Apr 21 20:57:34 CST 2020 pZxid = 0x43 cversion = 0 dataVersion = 0 aclVersion = 1 ephemeralOwner = 0x0 dataLength = 5 numChildren = 0 [zk: localhost:2181(CONNECTED) 18] getAcl /node5 'digest,'wgr:sfWvAOV+8UWBCBQJ3dDPaHw2f+Q= : cdrwa [zk: localhost:2181(CONNECTED) 19] get /node5 Authentication is not valid : /node5 [zk: localhost:2181(CONNECTED) 20] addauth digest wgr:12345 [zk: localhost:2181(CONNECTED) 21] get /node5 node5 cZxid = 0x43 ctime = Tue Apr 21 20:57:34 CST 2020 mZxid = 0x43 mtime = Tue Apr 21 20:57:34 CST 2020 pZxid = 0x43 cversion = 0 dataVersion = 0 aclVersion = 1 ephemeralOwner = 0x0 dataLength = 5 numChildren = 0 [zk: localhost:2181(CONNECTED) 22]
多种模式授权:
同一个节点可以同时使用多种模式授权
[zk: localhost:2181(CONNECTED) 0] create /node5 "node5" Created /node5 [zk: localhost:2181(CONNECTED) 1] addauth digest itcast:123456 #添加认证用户 [zk: localhost:2181(CONNECTED) 2] setAcl /node5 ip:192.168.60.129:cdra,auth:wgr:cdrwa,digest:wgr:sfWvAOV+8UWBCBQJ3dDPaHw2f+Q=:cdrwa
acl 超级管理员
zookeeper的权限管理模式有一种叫做super,该模式提供一个超管可以方便的访问任何权限的节点
假设这个超管是:super:admin,需要先为超管生成密码的密文
[root@iZ1la3d1xbmukrZ bin]# echo -n super:super | openssl dgst -binary -sha1 | openssl base64 gG7s8t3oDEtIqF6DM9LlI/R+9Ss= [root@iZ1la3d1xbmukrZ bin]#
那么打开zookeeper目录下的/bin/zkServer.sh服务器脚本文件,找到如下一行:
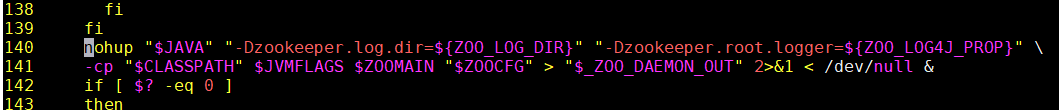
这就是脚本中启动zookeeper的命令,默认只有以上两个配置项,我们需要加一个超管的配置项:
"-Dzookeeper.DigestAuthenticationProvider.superDigest=super:xQJmxLMiHGwaqBvst5y6rkB6HQs="
[zk: localhost:2181(CONNECTED) 22] addauth digest super:super [zk: localhost:2181(CONNECTED) 23] get /node3 node3 cZxid = 0x3d ctime = Tue Apr 21 20:45:20 CST 2020 mZxid = 0x3d mtime = Tue Apr 21 20:45:20 CST 2020 pZxid = 0x3d cversion = 0 dataVersion = 0 aclVersion = 1 ephemeralOwner = 0x0 dataLength = 5 numChildren = 0 [zk: localhost:2181(CONNECTED) 24] get /node4 node4 cZxid = 0x40 ctime = Tue Apr 21 20:50:14 CST 2020 mZxid = 0x40 mtime = Tue Apr 21 20:50:14 CST 2020 pZxid = 0x40 cversion = 0 dataVersion = 0 aclVersion = 1 ephemeralOwner = 0x0 dataLength = 5 numChildren = 0 [zk: localhost:2181(CONNECTED) 25] get /node5 node5 cZxid = 0x43 ctime = Tue Apr 21 20:57:34 CST 2020 mZxid = 0x43 mtime = Tue Apr 21 20:57:34 CST 2020 pZxid = 0x43 cversion = 0 dataVersion = 0 aclVersion = 1 ephemeralOwner = 0x0 dataLength = 5 numChildren = 0