19-K8S Basic-Dashboard认证访问
一、Kubernetes Dashboard介绍
- Dashboard Kubernetes Web GUI ,可用于在 Kubernetes 集群上部署容器化应用应用排障、管理集群本身及其附加的资源等 它常被管理员用于集群及应用速览 创建或修改单个资源(如 Deployments Jobs DaemonSets 等),以及扩展 Deployment 、启动滚动更新、重启 Pod 或使用部署向导部署一个新应用等
- Dashboard 的认证和授权均可由 Kubernetes 集群实现,它自身仅是一个代理,所有的相关操作都将发给 API Server 进行,而非由 Dashboard 自行完成 目前它支持使用的认证方式有承载令牌( bear token )和 kubeconfig 两种,在访问之前需要准备好相应的认证凭证
- Dashboard基于web的图形界面控制面板
- web ui
- 以Pod形式运行于k8s之上
- k8s自身的管理接口
- 权限
- 多用户,通过不同的用户登陆分别获取不同的权限,但是Dashboard不会做任何用户的认证,仅将认证请求代理至kubernetes
- 用户账号 : 必须是Service account账号
- Web UI一般需要集群外部进行访问
- 一般使用Node Port类型的Service或者ingress将其开放至集群外部
- 权限
- Kubernetes Dashboard Github托管地址:https://github.com/kubernetes/dashboard
- 部署参考文档 :https://kuboard.cn/install/install-k8s-dashboard.html#安装
二、Kubernetes Dashboard部署
2.1、创建认证私钥
~]# cd /etc/kubernetes/pki/
1、创建私钥
pki]# openssl genrsa -out dashboard.key 2048
Generating RSA private key, 2048 bit long modulus
..................................................+++
..+++
e is 65537 (0x10001)
2、生成证书签署请求
/0 一定是互联网上解析的域名
pki]# openssl req -new -key dashboard.key -out dashboard.csr -subj "/O=Daizhe/CN=dashboard"
3、使用自建ca认证
pki]# openssl x509 -req -in dashboard.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out dashboard.crt -days 3650
Signature ok
subject=/O=Daizhe/CN=dashboard
Getting CA Private Key
2.2、创建generic类型的secrets用于存放证书信息
pki]# kubectl create secret generic kubernetes-dashboard-certs -n kube-system --from-file=dashboard.crt --from-file=dashboard.key
secret/kubernetes-dashboard-certs created
pki]# kubectl get secret -n kube-system
pki]# kubectl get secret kubernetes-dashboard-certs -n kube-system
NAME TYPE DATA AGE
kubernetes-dashboard-certs Opaque 2 69s
pki]# kubectl get secret kubernetes-dashboard-certs -n kube-system -o yaml
apiVersion: v1
data:
dashboard.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUN0akNDQVo0Q0NRRHhQQ2FIemt6QTZEQU5CZ2txaGtpRzl3MEJBUXNGQURBVk1STXdFUVlEVlFRREV3cHIKZFdKbGNtNWxkR1Z6TUI0WERUSXdNRFV5TlRBM01qUXdPRm9YRFRNd01EVXlNekEzTWpRd09Gb3dKVEVQTUEwRwpBMVVFQ2d3R1JHRnBlbWhsTVJJd0VBWURWUVFEREFsa1lYTm9ZbTloY21Rd2dnRWlNQTBHQ1NxR1NJYjNEUUVCCkFRVUFBNElCRHdBd2dnRUtBb0lCQVFETG5ocEF5eDBzcFpJZXZNZ0V0NmhZRVgyVDNhdGdzanJwdjdGRWY1NmcKTzJHUEFBUzBuaEJyaWdzN2xvK2l6Vkp5MkkyemlzYzNQQjV5d0R2TEpvQlhCTmUrbDFROG52WGh0a0Q5MElESgpkVFJQaDJmZmFYMTJWcGxHbFViTVhHeCt3d2RCa2tEVU5YcGIwWWt2bWVvU2RJVWlKVlhlZGtNVjNLZnFlWUFlClRESU5zcUEyRzRGMVdiOXh3bXByNWJwS3pLVzIzRytRUkY3R3UvSGRiUmFWVGphL3Z5OCtnNE4rWG03U1JkeGoKdEE4UHhwNFpET0RtMENpR3Y4WGRuUUpNZFNPUmVwMGxBT0NlakgrM0N0Q1pJa1FvenUxeGMxbDhPdVB5eFZjegpUMi9ZZTdGM0l5VjUxNnlwVkgvbzl3VUdjS1RNa0o4T2taQWxkOXkyWXkvOUFnTUJBQUV3RFFZSktvWklodmNOCkFRRUxCUUFEZ2dFQkFJOU1JM1hMN1lER3N2U09ONmxzdFhNYVJWNEFDejRiY2dHUTVnaCs2QU1nVi9qUkdLUVMKME9scGRYcktqZUwrNm0xdCtDbnNnNCtudlhpWTJuNkFCRklLeU5jYTd2aXV2ZDVnZEg2TDJWU3JqMVV5UklBdwpBY0pYdXN2Rzg1L0lnNE9yTnZnczI5alJhUnhIbXdvMmU0WVNvdnQ1VTFiYTJnWWltNkg2YkZMTWJScFY0SHUzCjU4bklCbmsra3VaT1l0VlN0cVNNWENIZVNaUHIvUGJvVW1uTW0yc0dRbnhSb1dyWkcxWFAzSVVNM1VrODgwTTYKUGExSjJLWTZKM2NXcjljUkVvT0FtSFlvbDJzaThrd0FEOTZDM2MvdlhuVFVqTURQMDN2L2tIemFKYXQxa0hPNwpOUU9FUHlMZW5hUXA3SlZRclU4Rmk2VVI0SGZLbXZybmpOdz0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
dashboard.key: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb3dJQkFBS0NBUUVBeTU0YVFNc2RMS1dTSHJ6SUJMZW9XQkY5azkycllMSTY2Yit4UkgrZW9EdGhqd0FFCnRKNFFhNG9MTzVhUG9zMVNjdGlOczRySE56d2Vjc0E3eXlhQVZ3VFh2cGRVUEo3MTRiWkEvZENBeVhVMFQ0ZG4KMzJsOWRsYVpScFZHekZ4c2ZzTUhRWkpBMURWNlc5R0pMNW5xRW5TRklpVlYzblpERmR5bjZubUFIa3d5RGJLZwpOaHVCZFZtL2NjSnFhK1c2U3N5bHR0eHZrRVJleHJ2eDNXMFdsVTQydjc4dlBvT0RmbDV1MGtYY1k3UVBEOGFlCkdRemc1dEFvaHIvRjNaMENUSFVqa1hxZEpRRGdub3gvdHdyUW1TSkVLTTd0Y1hOWmZEcmo4c1ZYTTA5djJIdXgKZHlNbGVkZXNxVlIvNlBjRkJuQ2t6SkNmRHBHUUpYZmN0bU12L1FJREFRQUJBb0lCQUhOQnptaUkwTDNhQndsQgpJUk9TaGtjN3QxTEE4bVpzM080OXBQRTZNQ2RSRlpzbGpvUlN5TWFtd0U3OW5kYXcxSS9QeHY0dmV5N241L0JhCm9qNFBVQ3h4d0ZIUlJVeC9TbjEyZGZsMlVjQTNpT0hQcXR1SzBncnZZQm5WRzl0SUlkM3JOYXRIUjAwWDdHZ1gKQnNtY0hTUlBNcUV1Y3huVzVZaDFlOU04N1dtNEFvNEhFQ25DNUw1U1R6WkdiYjVTQXlmRnIwVE5MV1NMOXZlaQpuZlVLcE9ZcUROaGJDd0lUT2R6UExZdFZESHBxdnRlSWZZS2ltYUQ3T2RqNjdLRnhXMnlMU2pzL29jM3JzZFlIClc1SGZmNW9neU9nYmlsK3JKZlY4SGxqUUFWRHhYZjVmeXZ2VG92UXhjRFAvZGVDNUtVU1lGcDFFaklBbk1qN0gKUnlIYXZQMENnWUVBOW5rN3ZDbkplcGw0SWlGdW90a3BCY3RNb0gyZmtvSVZnWTdwODg3c0VucW5UM0FMYkhwSwpLU3plRk9ZOVFkQUMyQ3d5UHJUTkhmcUZ3cTZDckNUNXBKVmdXaHd3WjZYK0hMR2o0cHRUVXZlOStwdzk5ekJtCkpaME10eUJ6TTdtOWVUM3BqUUhFV2t3WDBRREU0Yk5BZS9ld1VvMlMrdWRRMFlRWkMzRFpJT2NDZ1lFQTAzelQKSjAvTDIzL2hEVWFTYk5mRWpnL2FTak51V3RvODhmYjJWNFYyazFOQXZsOXhtWjIxZW5uWnFNbTlRd3NxSzVxdApURkVjd0c5SWV3ZGZkbDZGTkJjTmtEWkxETzNqelpGYW9jZE9MSWNQK3NwcVVHQ2lFQjArOGZ4UFdZbE1vWkVSCjVSeUxvd0thVHRMR2s3bm5ydUg3cmtYbHUwQ2hIS2xFcWZoemQzc0NnWUFQT2tRL2h0RmsyckI2WTFoamhVa3MKaTNmcmZuZHFaTkVSVlJRTk5SNk9zYmMraUN5Y2doMnMxNUhNOXNDWUhWTGZxak5jZm0waHlnV1RscGFLTGlxaQpTWHhQZE9oa3J2TzVNQnh3OXFtNk9ZWXFRcGJ0ZTdjRDRlVVVOMVFHd1JYOHRKK0dUN0tpNVlxZkpnNEQ1OEEzCktJRmpTRTNwWkhzd3hwbUpoR3BWeHdLQmdRQ2pNaE9PcGxqZERKVVJ0WCtRVmYvcXovaldnVkdLOGhWTmNoRXUKQUdNNzFHYUZnUWtjVFVLWlBDWGx4YWN5Y1E4ZGpzSmp2Y08rQ3lHWExsMVA3aWhEeGZaRmJtQURuaDdIcG42VgprRUtXd2JKbkNJTjVldGdVTHowL1pqK2xDL29DUXZ2WUhHcjBZekhIMllZNndKNHpxVmFaYUg2YVBJa1dvTmZICmdWMDR1UUtCZ0ZRcitBN3ZQZVNsKzZmME1kY1poa0c0YUxCbTMxeHNRbFRqSU90NHhLUWxWaVhHTmlkNjNMaUkKRWhXUG1Tc3lTMC9wSWIyRGYzWTUvZXZkVkhrb09rTFJaSmFuL2txN1RNb0NLZEVCZDcwWjlOeEZ1UFVTOHlyVQpGell6Y04xTW1vbThpQWxCNG9Ealh1b1I4Y3ZqN2gyUFpQNGJjV1h5S2RYckdESDg4WXZNCi0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==
kind: Secret
metadata:
creationTimestamp: "2020-05-25T08:36:11Z"
managedFields:
- apiVersion: v1
fieldsType: FieldsV1
fieldsV1:
f:data:
.: {}
f:dashboard.crt: {}
f:dashboard.key: {}
f:type: {}
manager: kubectl
operation: Update
time: "2020-05-25T08:36:11Z"
name: kubernetes-dashboard-certs
namespace: kube-system
resourceVersion: "6352335"
selfLink: /api/v1/namespaces/kube-system/secrets/kubernetes-dashboard-certs
uid: 8aa81516-7473-4998-a8b2-54cc8b2dcdb6
type: Opaque
2.3、应用安装kubernetes dashboard的yaml文件
- kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.1/aio/deploy/recommended.yaml
dashboard]# cat recommended.yaml
# Copyright 2017 The Kubernetes Authors.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
# You may obtain a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS,
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
apiVersion: v1
kind: Namespace
metadata:
name: kubernetes-dashboard
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
ports:
- port: 443
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kubernetes-dashboard
type: Opaque
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-csrf
namespace: kubernetes-dashboard
type: Opaque
data:
csrf: ""
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-key-holder
namespace: kubernetes-dashboard
type: Opaque
---
kind: ConfigMap
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-settings
namespace: kubernetes-dashboard
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
rules:
# Allow Dashboard to get, update and delete Dashboard exclusive secrets.
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"]
verbs: ["get", "update", "delete"]
# Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
# Allow Dashboard to get metrics.
- apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster", "dashboard-metrics-scraper"]
verbs: ["proxy"]
- apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"]
verbs: ["get"]
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
rules:
# Allow Metrics Scraper to get metrics from the Metrics server
- apiGroups: ["metrics.k8s.io"]
resources: ["pods", "nodes"]
verbs: ["get", "list", "watch"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
containers:
- name: kubernetes-dashboard
image: kubernetesui/dashboard:v2.0.1
imagePullPolicy: Always
ports:
- containerPort: 8443
protocol: TCP
args:
- --auto-generate-certificates
- --namespace=kubernetes-dashboard
# Uncomment the following line to manually specify Kubernetes API server Host
# If not specified, Dashboard will attempt to auto discover the API server and connect
# to it. Uncomment only if the default does not work.
# - --apiserver-host=http://my-address:port
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
# Create on-disk volume to store exec logs
- mountPath: /tmp
name: tmp-volume
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard
nodeSelector:
"kubernetes.io/os": linux
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kubernetes-dashboard
spec:
ports:
- port: 8000
targetPort: 8000
selector:
k8s-app: dashboard-metrics-scraper
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kubernetes-dashboard
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: dashboard-metrics-scraper
template:
metadata:
labels:
k8s-app: dashboard-metrics-scraper
annotations:
seccomp.security.alpha.kubernetes.io/pod: 'runtime/default'
spec:
containers:
- name: dashboard-metrics-scraper
image: kubernetesui/metrics-scraper:v1.0.4
ports:
- containerPort: 8000
protocol: TCP
livenessProbe:
httpGet:
scheme: HTTP
path: /
port: 8000
initialDelaySeconds: 30
timeoutSeconds: 30
volumeMounts:
- mountPath: /tmp
name: tmp-volume
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
serviceAccountName: kubernetes-dashboard
nodeSelector:
"kubernetes.io/os": linux
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
volumes:
- name: tmp-volume
emptyDir: {}
# 创建清单中的资源
[root@k8s dashboard]# ls
recommended.yaml
[root@k8s dashboard]# pwd
/root/mainfests/dashboard
dashboard]# kubectl apply -f recommended.yaml
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper created
# 为了实现可以支持通过集群外部进行访问将service改称为NodePort类型
dashboard]# kubectl edit service/kubernetes-dashboard -n kubernetes-dashboard
....
spec:
clusterIP: 10.98.179.163
ports:
- port: 443
protocol: TCP
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
sessionAffinity: None
type: NodePort
.....
dashboard]# kubectl get service -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.96.109.157 <none> 8000/TCP 6m10s
kubernetes-dashboard NodePort 10.98.179.163 <none> 443:30459/TCP 6m11s
dashboard]# kubectl get pods -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
dashboard-metrics-scraper-6b4884c9d5-jncbh 1/1 Running 0 6m42s
kubernetes-dashboard-7bfbb48676-z4pr6 1/1 Running 0 6m42s
- 访问测试(访问node节点的任意主机):
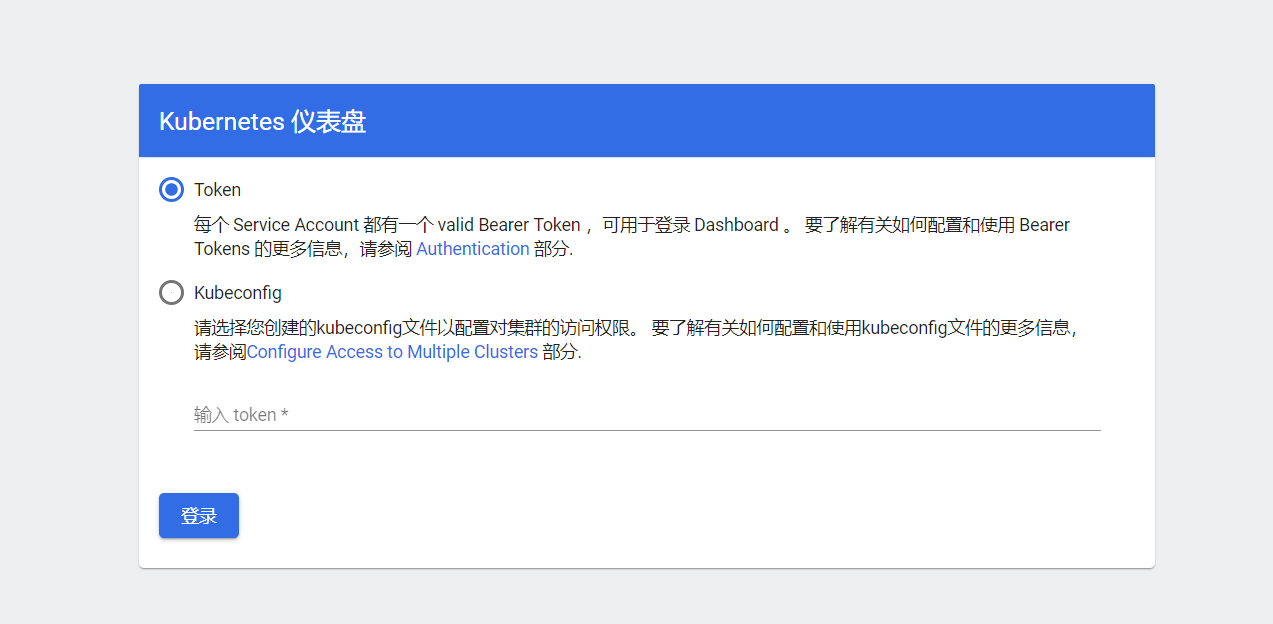
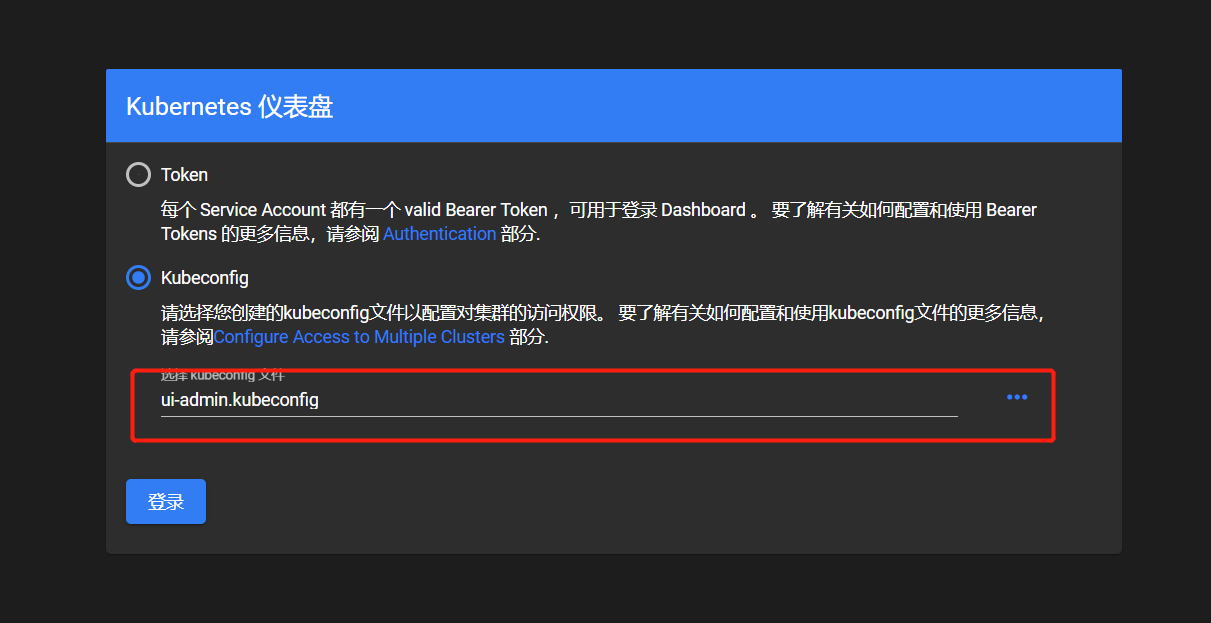
2.4、k8s中 dashboard可以有两种访问方式:kubeconfig(HTTPS)和token(http)
- 如果想实现用户通过dashborad访问整个集群的所有名称空间就需要将证书绑定在clusteradmin之上
2.4.1、Token认证
2.4.1.1、管理员-all
# 管理员
~]# kubectl create serviceaccount ui-admin -n kube-system
serviceaccount/ui-admin created
~]# kubectl create clusterrolebinding cluster-ui-admin --clusterrole=cluster-admin --serviceaccount=kube-system:ui-admin
clusterrolebinding.rbac.authorization.k8s.io/cluster-ui-admin created
# 获取token
~]# kubectl get sa ui-admin -n kube-system
NAME SECRETS AGE
ui-admin 1 3m24s
~]# kubectl get sa ui-admin -n kube-system -o yaml
apiVersion: v1
kind: ServiceAccount
metadata:
creationTimestamp: "2020-05-25T08:53:20Z"
name: ui-admin
namespace: kube-system
resourceVersion: "6355001"
selfLink: /api/v1/namespaces/kube-system/serviceaccounts/ui-admin
uid: 7a9a14b7-270d-4f4e-9bf1-5100ec76a5c4
secrets: # secret名称
- name: ui-admin-token-22qh2
# 获取secret中保存的Tocken
~]# kubectl get secret ui-admin-token-22qh2 -n kube-system
NAME TYPE DATA AGE
ui-admin-token-22qh2 kubernetes.io/service-account-token 3 5m5s
~]# kubectl get secret ui-admin-token-22qh2 -n kube-system -o yaml
apiVersion: v1
data:
ca.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUN5RENDQWJDZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJd01EUXlOREUyTkRrd05Gb1hEVE13TURReU1qRTJORGt3TkZvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTkhKCjE4WTNjcCtUNSsrRnBzWnZuVmNwejhIalpuV0Z4TzNvRXpyRDBYd1gxN01rSkxOQjNySGlSenp3blZvRVppKzMKZE5rOGRPem5XOCtlV0U1UjNQOFhlUDRkUEFab0FlT1Nvc1JIYnpqMGsydlFiSHJuV0dlZDhQZ001R015em82UQorRUFKeTBvd0tZeXBET1VERjViQ1NyYjFxY3NTUWZzZHlFQXFlL2VNY3B6UDhZR3pscCt1bGhsUTlNeTBINWtHCmV0bDBYTG5wNm9SVDlyaVlSZEE3NFhCcjhlRExGZ3RjVVpDdWVSM0c1akQyZjBneDhmTmcxcnZBc1FNOWcxWUsKczdlZDE2bDJHZGpFWUxWQ3N6Q01IZXVCeEE1Z2EwNzNhUG9hZWNtcU5NK0FsemZrTVNnZ29qQnVoMFdzbTQ2MQpZczhLM1RYY1VpaTVObG41L0pjQ0F3RUFBYU1qTUNFd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFGWXdWS3VTNjRGVHZaTzJFM2ZPTGZvYVBZRWQKUXg3SDdYbnNkZVRRR2ROd2JzMzhFRU91bDJzYVBRY0xCdjZNS1VQWVlNUjNJdTBkZ0hBRFZtRkwrQkdZajhqSQpYSkh0VlovY3VzV3dPY3FkUGRmaUlJektNNnlpdDJ2WnJieDJ0Nm5mdXVPM1lwZUtVUVJ5aXhxbitoTDVsTVJUCldya0dMcUhYSy9oc1kvdkl1dFMzdk9CVlR4ZUhPSk9VVDdESytuL09FNGs2anFmTGNqY3dKTVNOZ0hZOGc1YmcKYnRhcWlRZFpNajBrMkRkdDA0VGZmaWNNdlJpTVVDUHJRQmM5TS9LUGpKcHV3Z0hkZUhrd1pIMXRrcVZWMzgxKwpTem1pUS9xS1ViSWZad3FSYitpclpWMFp3SnRXQWU5Y0dzYTYyeGpTVkF0YmN6cWF5ZDllRWJ2a1RXTT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
namespace: a3ViZS1zeXN0ZW0=
# token信息但是是base64编码后的
token: ZXlKaGJHY2lPaUpTVXpJMU5pSXNJbXRwWkNJNklrZGxWa1ZwV1hJd1UwRkVWbVZEVDJwd2JHdHJhVGxoV0RZMlVtRkNkMlpoVUhNM2VtdHFZMFZxVDBVaWZRLmV5SnBjM01pT2lKcmRXSmxjbTVsZEdWekwzTmxjblpwWTJWaFkyTnZkVzUwSWl3aWEzVmlaWEp1WlhSbGN5NXBieTl6WlhKMmFXTmxZV05qYjNWdWRDOXVZVzFsYzNCaFkyVWlPaUpyZFdKbExYTjVjM1JsYlNJc0ltdDFZbVZ5Ym1WMFpYTXVhVzh2YzJWeWRtbGpaV0ZqWTI5MWJuUXZjMlZqY21WMExtNWhiV1VpT2lKMWFTMWhaRzFwYmkxMGIydGxiaTB5TW5Gb01pSXNJbXQxWW1WeWJtVjBaWE11YVc4dmMyVnlkbWxqWldGalkyOTFiblF2YzJWeWRtbGpaUzFoWTJOdmRXNTBMbTVoYldVaU9pSjFhUzFoWkcxcGJpSXNJbXQxWW1WeWJtVjBaWE11YVc4dmMyVnlkbWxqWldGalkyOTFiblF2YzJWeWRtbGpaUzFoWTJOdmRXNTBMblZwWkNJNklqZGhPV0V4TkdJM0xUSTNNR1F0TkdZMFpTMDVZbVl4TFRVeE1EQmxZemMyWVRWak5DSXNJbk4xWWlJNkluTjVjM1JsYlRwelpYSjJhV05sWVdOamIzVnVkRHByZFdKbExYTjVjM1JsYlRwMWFTMWhaRzFwYmlKOS5pWFd3dGxIMkRVS2lOVFY2VG51VkcybnlLdHBZNEQ4anlrRnVpUVJZcDR4dC13aC00Z04yLUtZSl9UcFNKczNNNk52YmtKLWRmV1hUaGl1em5TWkVubzlBeTdWbmh4djYzdkFXOVFveURLOXROZlVsU01rakdPbG5rdFQwWDduWnZ1Y01XZkc1M1JfSTdxVS1FeGpZSUdSM0oxVXJfTWxnaWE3ZWpreFZQM0RkN1FoVHF5X193SzZSQlpwMmNJSDBhR1VKYk1BSEVhOHljSTZia016ZUY1VjZLNkdFVnhVTTZuYWRXdlZ0RU1LczRFa0VaRC1YdlRlYU5UeU53ckxjYndTMGQ4eS1GQ01YWElxSE1ZdnVOazNTSTdGX012eXVCdHRRWUhUTkduRTlHVGx5RnlBRDlUUDhOVHNncFo1aElndTNrOFVVWHY1ZlE5OUhCNFhiTUE=
kind: Secret
metadata:
annotations:
kubernetes.io/service-account.name: ui-admin
kubernetes.io/service-account.uid: 7a9a14b7-270d-4f4e-9bf1-5100ec76a5c4
creationTimestamp: "2020-05-25T08:53:20Z"
managedFields:
- apiVersion: v1
fieldsType: FieldsV1
fieldsV1:
f:data:
.: {}
f:ca.crt: {}
f:namespace: {}
f:token: {}
f:metadata:
f:annotations:
.: {}
f:kubernetes.io/service-account.name: {}
f:kubernetes.io/service-account.uid: {}
f:type: {}
manager: kube-controller-manager
operation: Update
time: "2020-05-25T08:53:20Z"
name: ui-admin-token-22qh2
namespace: kube-system
resourceVersion: "6355000"
selfLink: /api/v1/namespaces/kube-system/secrets/ui-admin-token-22qh2
uid: 7ad3f82d-0bc6-4514-8a5b-be632147e2ff
type: kubernetes.io/service-account-token
# base64解码后的token使用describe方式查看
~]# kubectl describe secret ui-admin-token-22qh2 -n kube-system
Name: ui-admin-token-22qh2
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: ui-admin
kubernetes.io/service-account.uid: 7a9a14b7-270d-4f4e-9bf1-5100ec76a5c4
Type: kubernetes.io/service-account-token
Data
====
# 解码后的token信息
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IkdlVkVpWXIwU0FEVmVDT2pwbGtraTlhWDY2UmFCd2ZhUHM3emtqY0VqT0UifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJ1aS1hZG1pbi10b2tlbi0yMnFoMiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJ1aS1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjdhOWExNGI3LTI3MGQtNGY0ZS05YmYxLTUxMDBlYzc2YTVjNCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTp1aS1hZG1pbiJ9.iXWwtlH2DUKiNTV6TnuVG2nyKtpY4D8jykFuiQRYp4xt-wh-4gN2-KYJ_TpSJs3M6NvbkJ-dfWXThiuznSZEno9Ay7Vnhxv63vAW9QoyDK9tNfUlSMkjGOlnktT0X7nZvucMWfG53R_I7qU-ExjYIGR3J1Ur_Mlgia7ejkxVP3Dd7QhTqy__wK6RBZp2cIH0aGUJbMAHEa8ycI6bkMzeF5V6K6GEVxUM6nadWvVtEMKs4EkEZD-XvTeaNTyNwrLcbwS0d8y-FCMXXIqHMYvuNk3SI7F_MvyuBttQYHTNGnE9GTlyFyAD9TP8NTsgpZ5hIgu3k8UUXv5fQ99HB4XbMA
ca.crt: 1025 bytes
namespace: 11 bytes
You have new mail in /var/spool/mail/root
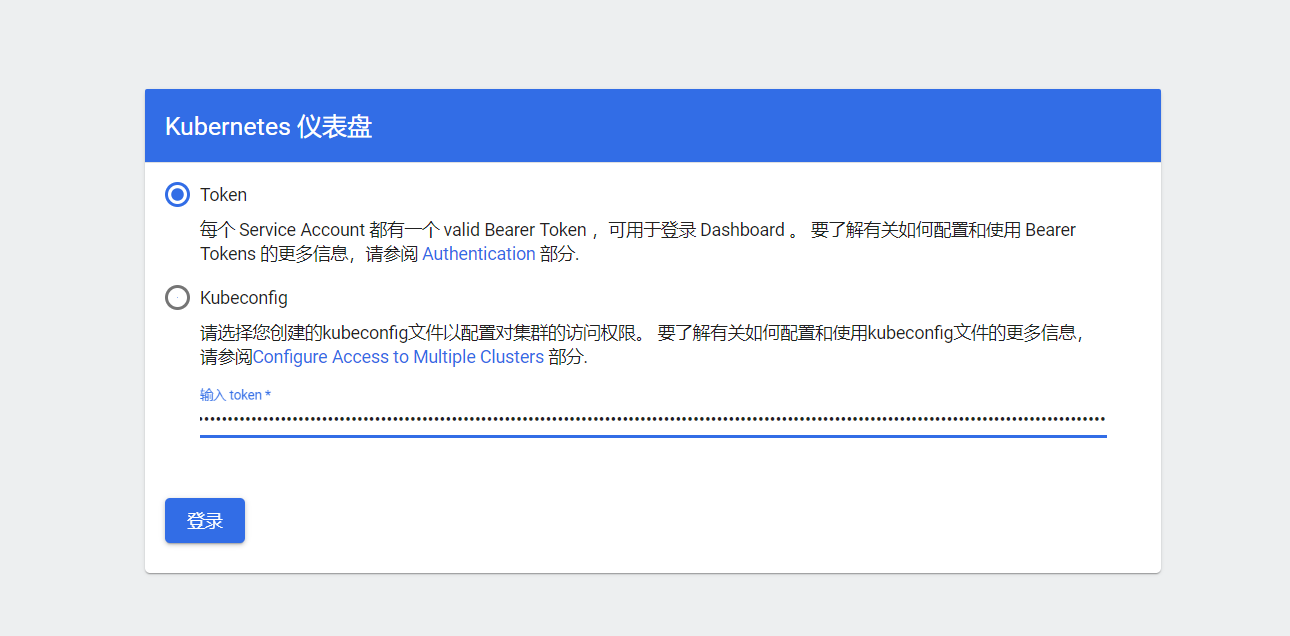
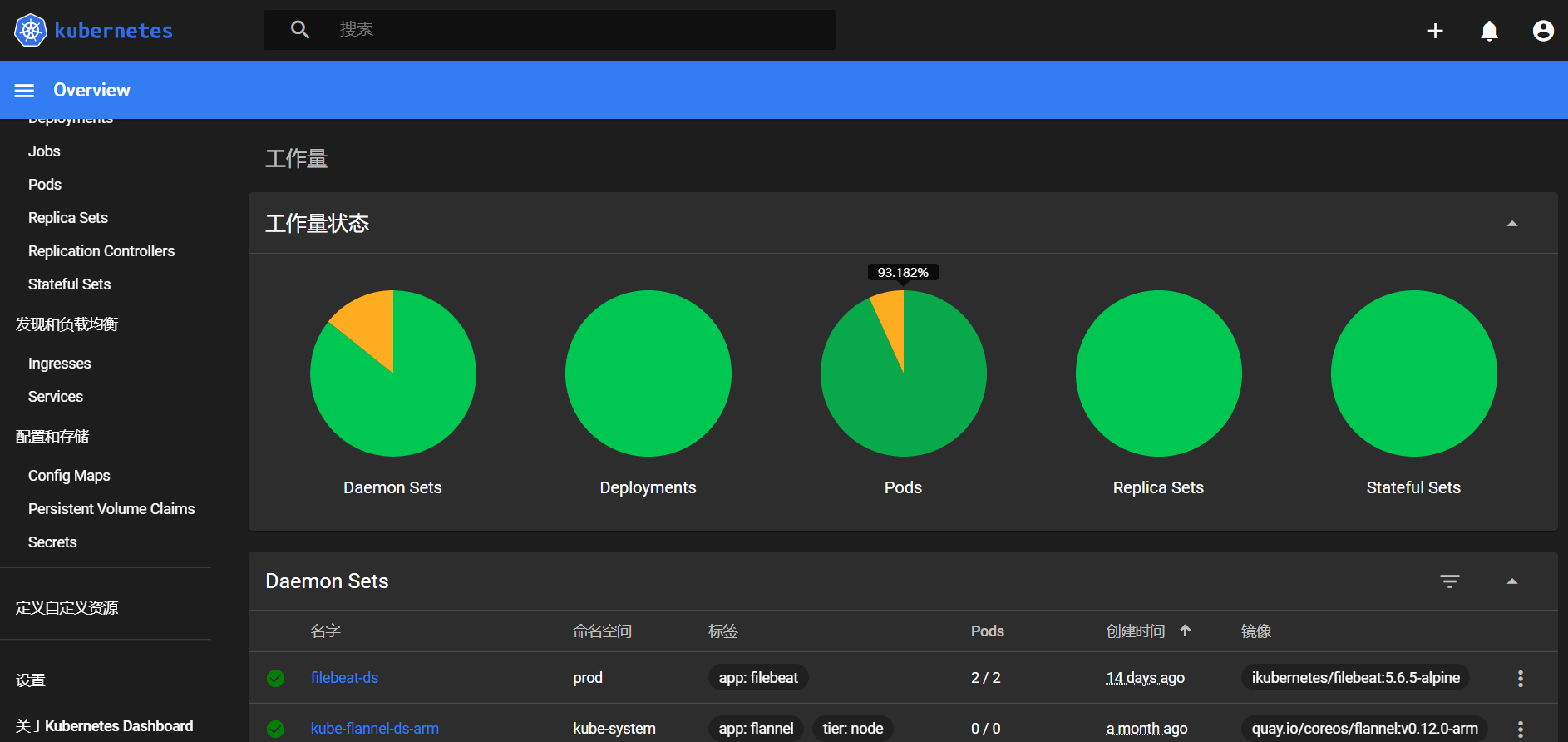
2.4.1.2、创建一个仅能管理一个名称空间下资源的用户
1、创建一个ns,授权用户仅能管理此名称空间下的资源
~]# kubectl create ns dev
namespace/dev created
2、账户创建
# 用户为dev-admin
~]# kubectl create serviceaccount dev-admin -n dev
serviceaccount/dev-admin created
3、将此用户绑定到集群角色上
~]# kubectl create rolebinding dev-admin --clusterrole=admin --serviceaccount=dev:dev-admin --namespace=dev
rolebinding.rbac.authorization.k8s.io/dev-admin created
4、查看创建的sa
~]# kubectl get sa -n dev
NAME SECRETS AGE
default 1 3m45s
dev-admin 1 2m52s
5、获取此sa的secrite
~]# kubectl get sa -n dev -o yaml
apiVersion: v1
items:
- apiVersion: v1
kind: ServiceAccount
metadata:
creationTimestamp: "2020-05-25T09:43:19Z"
name: default
namespace: dev
resourceVersion: "6362556"
selfLink: /api/v1/namespaces/dev/serviceaccounts/default
uid: a9e62105-b337-4a7e-bc4b-8e1e2d3c2ab2
secrets:
- name: default-token-fdhpq
- apiVersion: v1
kind: ServiceAccount
metadata:
creationTimestamp: "2020-05-25T09:44:12Z"
name: dev-admin
namespace: dev
resourceVersion: "6362695"
selfLink: /api/v1/namespaces/dev/serviceaccounts/dev-admin
uid: cc505d29-ad91-4d6c-b9d5-686cf3aae807
secrets:
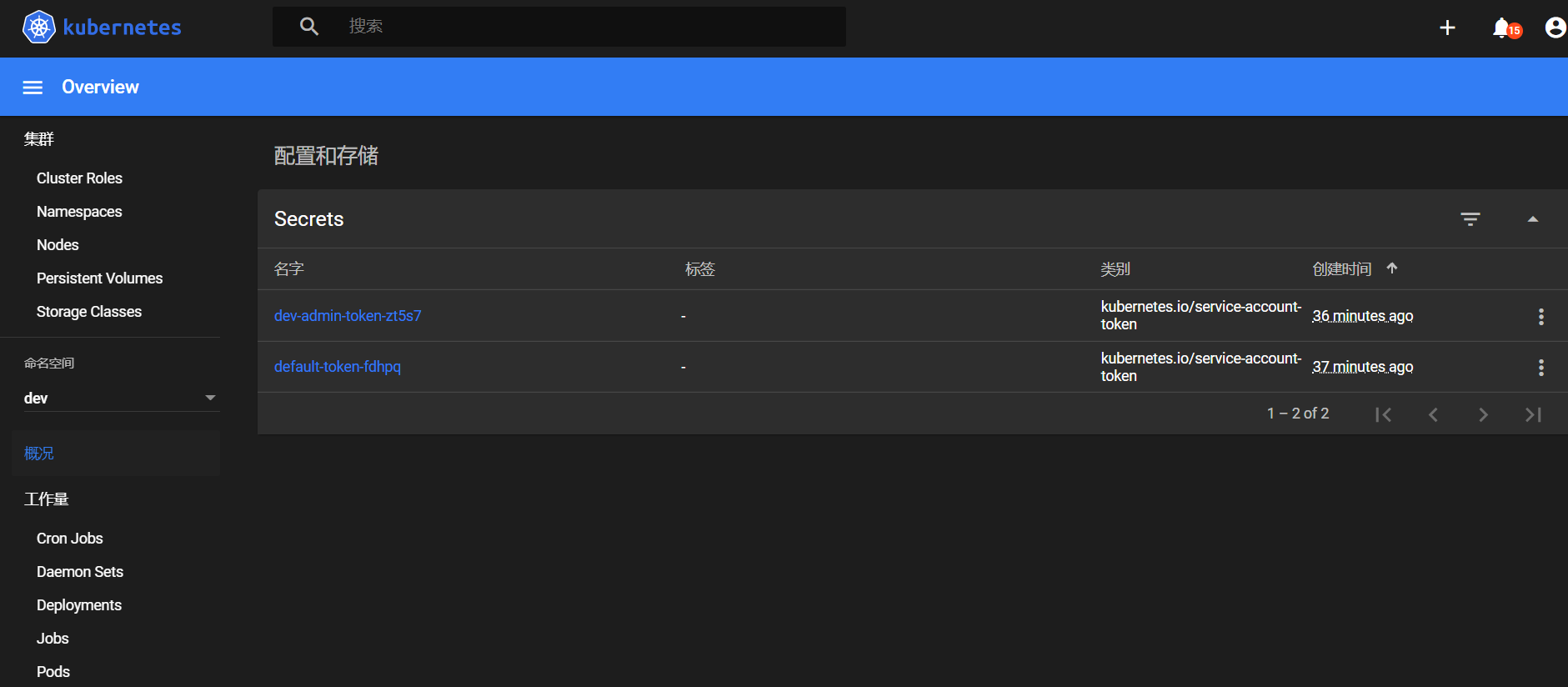
- name: dev-admin-token-zt5s7
kind: List
metadata:
resourceVersion: ""
selfLink: ""
6、获取此secret的Token信息
~]# kubectl describe secret dev-admin-token-zt5s7 -n dev
Name: dev-admin-token-zt5s7
Namespace: dev
Labels: <none>
Annotations: kubernetes.io/service-account.name: dev-admin
kubernetes.io/service-account.uid: cc505d29-ad91-4d6c-b9d5-686cf3aae807
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 3 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IkdlVkVpWXIwU0FEVmVDT2pwbGtraTlhWDY2UmFCd2ZhUHM3emtqY0VqT0UifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZXYiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlY3JldC5uYW1lIjoiZGV2LWFkbWluLXRva2VuLXp0NXM3Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImRldi1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImNjNTA1ZDI5LWFkOTEtNGQ2Yy1iOWQ1LTY4NmNmM2FhZTgwNyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZXY6ZGV2LWFkbWluIn0.msB0InfoF1jmUiQtHahBaxVE21FVYw8gVwDoZZI9ulj2oiY6bO9QJtaPMRD4J_ShL3S3uVfTOFoOaMgrcMd9dVpyISJ2ujNyZuLkbdXvHcS6e5wBHu_XDi8oz9hlJdYO-qysl1zsPsiGBmTUQlD_UrGRhj9l3T4Kf7kDzla3LDBzIQxxHfvqZaLluZFMlXUqxbyE-dc6_w-g2WSlxl98ZrRgYB-u5eo9sUjLRTko7LAXFOgbfceQR4-7eh42btMpmePagEVPBTocy4nTet2iLCeMQtz7f6iAJDMKhoeNTCVW94flLYiKJp3iNy8f6xj93PQCHZfHzUycFLvu_B4yzQ
2.4.2、Kubeconfig认证
- 管理员和仅控制单一名称空间下的用户步骤和下面一样仅是token一样
## 获取上面创建的用户的管理员的Token
1、
# 管理员
~]# kubectl create serviceaccount ui-admin -n kube-system
serviceaccount/ui-admin created
~]# kubectl create clusterrolebinding cluster-ui-admin --clusterrole=cluster-admin --serviceaccount=kube-system:ui-admin
clusterrolebinding.rbac.authorization.k8s.io/cluster-ui-admin created
2、
# 获取token
~]# kubectl get sa ui-admin -n kube-system
NAME SECRETS AGE
ui-admin 1 3m24s
~]# kubectl get sa ui-admin -n kube-system -o yaml
apiVersion: v1
kind: ServiceAccount
metadata:
creationTimestamp: "2020-05-25T08:53:20Z"
name: ui-admin
namespace: kube-system
resourceVersion: "6355001"
selfLink: /api/v1/namespaces/kube-system/serviceaccounts/ui-admin
uid: 7a9a14b7-270d-4f4e-9bf1-5100ec76a5c4
secrets: # secret名称
- name: ui-admin-token-22qh2
# 获取secret中保存的Tocken
~]# kubectl get secret ui-admin-token-22qh2 -n kube-system
NAME TYPE DATA AGE
ui-admin-token-22qh2 kubernetes.io/service-account-token 3 5m5s
3、
~]# kubectl get secret ui-admin-token-22qh2 -n kube-system -o yaml
apiVersion: v1
data:
ca.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUN5RENDQWJDZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJd01EUXlOREUyTkRrd05Gb1hEVE13TURReU1qRTJORGt3TkZvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTkhKCjE4WTNjcCtUNSsrRnBzWnZuVmNwejhIalpuV0Z4TzNvRXpyRDBYd1gxN01rSkxOQjNySGlSenp3blZvRVppKzMKZE5rOGRPem5XOCtlV0U1UjNQOFhlUDRkUEFab0FlT1Nvc1JIYnpqMGsydlFiSHJuV0dlZDhQZ001R015em82UQorRUFKeTBvd0tZeXBET1VERjViQ1NyYjFxY3NTUWZzZHlFQXFlL2VNY3B6UDhZR3pscCt1bGhsUTlNeTBINWtHCmV0bDBYTG5wNm9SVDlyaVlSZEE3NFhCcjhlRExGZ3RjVVpDdWVSM0c1akQyZjBneDhmTmcxcnZBc1FNOWcxWUsKczdlZDE2bDJHZGpFWUxWQ3N6Q01IZXVCeEE1Z2EwNzNhUG9hZWNtcU5NK0FsemZrTVNnZ29qQnVoMFdzbTQ2MQpZczhLM1RYY1VpaTVObG41L0pjQ0F3RUFBYU1qTUNFd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFGWXdWS3VTNjRGVHZaTzJFM2ZPTGZvYVBZRWQKUXg3SDdYbnNkZVRRR2ROd2JzMzhFRU91bDJzYVBRY0xCdjZNS1VQWVlNUjNJdTBkZ0hBRFZtRkwrQkdZajhqSQpYSkh0VlovY3VzV3dPY3FkUGRmaUlJektNNnlpdDJ2WnJieDJ0Nm5mdXVPM1lwZUtVUVJ5aXhxbitoTDVsTVJUCldya0dMcUhYSy9oc1kvdkl1dFMzdk9CVlR4ZUhPSk9VVDdESytuL09FNGs2anFmTGNqY3dKTVNOZ0hZOGc1YmcKYnRhcWlRZFpNajBrMkRkdDA0VGZmaWNNdlJpTVVDUHJRQmM5TS9LUGpKcHV3Z0hkZUhrd1pIMXRrcVZWMzgxKwpTem1pUS9xS1ViSWZad3FSYitpclpWMFp3SnRXQWU5Y0dzYTYyeGpTVkF0YmN6cWF5ZDllRWJ2a1RXTT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
namespace: a3ViZS1zeXN0ZW0=
# token信息但是是base64编码后的
token: ZXlKaGJHY2lPaUpTVXpJMU5pSXNJbXRwWkNJNklrZGxWa1ZwV1hJd1UwRkVWbVZEVDJwd2JHdHJhVGxoV0RZMlVtRkNkMlpoVUhNM2VtdHFZMFZxVDBVaWZRLmV5SnBjM01pT2lKcmRXSmxjbTVsZEdWekwzTmxjblpwWTJWaFkyTnZkVzUwSWl3aWEzVmlaWEp1WlhSbGN5NXBieTl6WlhKMmFXTmxZV05qYjNWdWRDOXVZVzFsYzNCaFkyVWlPaUpyZFdKbExYTjVjM1JsYlNJc0ltdDFZbVZ5Ym1WMFpYTXVhVzh2YzJWeWRtbGpaV0ZqWTI5MWJuUXZjMlZqY21WMExtNWhiV1VpT2lKMWFTMWhaRzFwYmkxMGIydGxiaTB5TW5Gb01pSXNJbXQxWW1WeWJtVjBaWE11YVc4dmMyVnlkbWxqWldGalkyOTFiblF2YzJWeWRtbGpaUzFoWTJOdmRXNTBMbTVoYldVaU9pSjFhUzFoWkcxcGJpSXNJbXQxWW1WeWJtVjBaWE11YVc4dmMyVnlkbWxqWldGalkyOTFiblF2YzJWeWRtbGpaUzFoWTJOdmRXNTBMblZwWkNJNklqZGhPV0V4TkdJM0xUSTNNR1F0TkdZMFpTMDVZbVl4TFRVeE1EQmxZemMyWVRWak5DSXNJbk4xWWlJNkluTjVjM1JsYlRwelpYSjJhV05sWVdOamIzVnVkRHByZFdKbExYTjVjM1JsYlRwMWFTMWhaRzFwYmlKOS5pWFd3dGxIMkRVS2lOVFY2VG51VkcybnlLdHBZNEQ4anlrRnVpUVJZcDR4dC13aC00Z04yLUtZSl9UcFNKczNNNk52YmtKLWRmV1hUaGl1em5TWkVubzlBeTdWbmh4djYzdkFXOVFveURLOXROZlVsU01rakdPbG5rdFQwWDduWnZ1Y01XZkc1M1JfSTdxVS1FeGpZSUdSM0oxVXJfTWxnaWE3ZWpreFZQM0RkN1FoVHF5X193SzZSQlpwMmNJSDBhR1VKYk1BSEVhOHljSTZia016ZUY1VjZLNkdFVnhVTTZuYWRXdlZ0RU1LczRFa0VaRC1YdlRlYU5UeU53ckxjYndTMGQ4eS1GQ01YWElxSE1ZdnVOazNTSTdGX012eXVCdHRRWUhUTkduRTlHVGx5RnlBRDlUUDhOVHNncFo1aElndTNrOFVVWHY1ZlE5OUhCNFhiTUE=
kind: Secret
metadata:
annotations:
kubernetes.io/service-account.name: ui-admin
kubernetes.io/service-account.uid: 7a9a14b7-270d-4f4e-9bf1-5100ec76a5c4
creationTimestamp: "2020-05-25T08:53:20Z"
managedFields:
- apiVersion: v1
fieldsType: FieldsV1
fieldsV1:
f:data:
.: {}
f:ca.crt: {}
f:namespace: {}
f:token: {}
f:metadata:
f:annotations:
.: {}
f:kubernetes.io/service-account.name: {}
f:kubernetes.io/service-account.uid: {}
f:type: {}
manager: kube-controller-manager
operation: Update
time: "2020-05-25T08:53:20Z"
name: ui-admin-token-22qh2
namespace: kube-system
resourceVersion: "6355000"
selfLink: /api/v1/namespaces/kube-system/secrets/ui-admin-token-22qh2
uid: 7ad3f82d-0bc6-4514-8a5b-be632147e2ff
type: kubernetes.io/service-account-token
4、
# base64解码后的token使用describe方式查看
~]# kubectl describe secret ui-admin-token-22qh2 -n kube-system
Name: ui-admin-token-22qh2
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: ui-admin
kubernetes.io/service-account.uid: 7a9a14b7-270d-4f4e-9bf1-5100ec76a5c4
Type: kubernetes.io/service-account-token
Data
====
# 解码后的token信息
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IkdlVkVpWXIwU0FEVmVDT2pwbGtraTlhWDY2UmFCd2ZhUHM3emtqY0VqT0UifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJ1aS1hZG1pbi10b2tlbi0yMnFoMiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJ1aS1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjdhOWExNGI3LTI3MGQtNGY0ZS05YmYxLTUxMDBlYzc2YTVjNCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTp1aS1hZG1pbiJ9.iXWwtlH2DUKiNTV6TnuVG2nyKtpY4D8jykFuiQRYp4xt-wh-4gN2-KYJ_TpSJs3M6NvbkJ-dfWXThiuznSZEno9Ay7Vnhxv63vAW9QoyDK9tNfUlSMkjGOlnktT0X7nZvucMWfG53R_I7qU-ExjYIGR3J1Ur_Mlgia7ejkxVP3Dd7QhTqy__wK6RBZp2cIH0aGUJbMAHEa8ycI6bkMzeF5V6K6GEVxUM6nadWvVtEMKs4EkEZD-XvTeaNTyNwrLcbwS0d8y-FCMXXIqHMYvuNk3SI7F_MvyuBttQYHTNGnE9GTlyFyAD9TP8NTsgpZ5hIgu3k8UUXv5fQ99HB4XbMA
ca.crt: 1025 bytes
namespace: 11 bytes
-----------------------------------------------------
# 将Tocken放置到kube-config中
5、集群创建
# 获取API Server的ip
~]# kubectl get pods -n kube-system -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
coredns-7ff77c879f-2sn2f 1/1 Running 1 31d 10.244.0.5 k8s.master1 <none> <none>
coredns-7ff77c879f-8qqdb 1/1 Running 2 31d 10.244.0.6 k8s.master1 <none> <none>
etcd-k8s.master1 1/1 Running 1 31d 192.168.20.236 k8s.master1 <none> <none>
kube-apiserver-k8s.master1 1/1 Running 2 31d 192.168.20.236 k8s.master1 <none> <none>
# 创建config
~]# kubectl config set-cluster mukube --server="https://192.168.20.236:6443" --certificate-authority=/etc/kubernetes/pki/ca.crt --embed-certs=true --kubeconfig=/tmp/ui-admin.kubeconfig
Cluster "mukube" set.
6、创建用户名
~]# kubectl config set-credentials ui-admin \
--token=eyJhbGciOiJSUzI1NiIsImtpZCI6IkdlVkVpWXIwU0FEVmVDT2pwbGtraTlhWDY2UmFCd2ZhUHM3emtqY0VqT0UifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJ1aS1hZG1pbi10b2tlbi0yMnFoMiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJ1aS1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjdhOWExNGI3LTI3MGQtNGY0ZS05YmYxLTUxMDBlYzc2YTVjNCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTp1aS1hZG1pbiJ9.iXWwtlH2DUKiNTV6TnuVG2nyKtpY4D8jykFuiQRYp4xt-wh-4gN2-KYJ_TpSJs3M6NvbkJ-dfWXThiuznSZEno9Ay7Vnhxv63vAW9QoyDK9tNfUlSMkjGOlnktT0X7nZvucMWfG53R_I7qU-ExjYIGR3J1Ur_Mlgia7ejkxVP3Dd7QhTqy__wK6RBZp2cIH0aGUJbMAHEa8ycI6bkMzeF5V6K6GEVxUM6nadWvVtEMKs4EkEZD-XvTeaNTyNwrLcbwS0d8y-FCMXXIqHMYvuNk3SI7F_MvyuBttQYHTNGnE9GTlyFyAD9TP8NTsgpZ5hIgu3k8UUXv5fQ99HB4XbMA \
--kubeconfig=/tmp/ui-admin.kubeconfig
User "ui-admin" set.
7、创建context
~]# kubectl config set-context ui-admin@mykube --cluster=mykube --user=ui-admin --kubeconfig=/tmp/ui-admin.kubeconfig
Context "ui-admin@mykube" created.
~]# kubectl config view --kubeconfig=/tmp/ui-admin.kubeconfig
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.20.236:6443
name: mukube
contexts:
- context:
cluster: mykube
user: ui-admin
name: ui-admin@mykube
current-context: ""
kind: Config
preferences: {}
users:
- name: ui-admin
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IkdlVkVpWXIwU0FEVmVDT2pwbGtraTlhWDY2UmFCd2ZhUHM3emtqY0VqT0UifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJ1aS1hZG1pbi10b2tlbi0yMnFoMiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJ1aS1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjdhOWExNGI3LTI3MGQtNGY0ZS05YmYxLTUxMDBlYzc2YTVjNCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTp1aS1hZG1pbiJ9.iXWwtlH2DUKiNTV6TnuVG2nyKtpY4D8jykFuiQRYp4xt-wh-4gN2-KYJ_TpSJs3M6NvbkJ-dfWXThiuznSZEno9Ay7Vnhxv63vAW9QoyDK9tNfUlSMkjGOlnktT0X7nZvucMWfG53R_I7qU-ExjYIGR3J1Ur_Mlgia7ejkxVP3Dd7QhTqy__wK6RBZp2cIH0aGUJbMAHEa8ycI6bkMzeF5V6K6GEVxUM6nadWvVtEMKs4EkEZD-XvTeaNTyNwrLcbwS0d8y-FCMXXIqHMYvuNk3SI7F_MvyuBttQYHTNGnE9GTlyFyAD9TP8NTsgpZ5hIgu3k8UUXv5fQ99HB4XbMA
8、设置current-context
~]# kubectl config use-context ui-admin@mykube --kubeconfig=/tmp/ui-admin.kubeconfig
Switched to context "ui-admin@mykube".
9、复制config到本机电脑登陆测试
~]# sz /tmp/ui-admin.kubeconfig
- 登陆测试(访问集群node节点的任意主机IP)
向往的地方很远,喜欢的东西很贵,这就是我努力的目标。

