istio 1.15.2安装部署
一、官方脚本安装部署
[root@alicound-rocky-8-6 ~]# curl -L https://istio.io/downloadIstio | ISTIO_VERSION=1.15.2 TARGET_ARCH=x86_64 sh - % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 100 101 100 101 0 0 3884 0 --:--:-- --:--:-- --:--:-- 3884 100 4856 100 4856 0 0 107k 0 --:--:-- --:--:-- --:--:-- 107k Downloading istio-1.15.2 from https://github.com/istio/istio/releases/download/1.15.2/istio-1.15.2-linux-amd64.tar.gz ... Istio 1.15.2 Download Complete! Istio has been successfully downloaded into the istio-1.15.2 folder on your system. Next Steps: See https://istio.io/latest/docs/setup/install/ to add Istio to your Kubernetes cluster. To configure the istioctl client tool for your workstation, add the /root/istio-1.15.2/bin directory to your environment path variable with: export PATH="$PATH:/root/istio-1.15.2/bin" Begin the Istio pre-installation check by running: istioctl x precheck Need more information? Visit https://istio.io/latest/docs/setup/install/ [root@alicound-rocky-8-6 ~]#
二、下载tar安装
[root@easzlab-k8s-master-01 ~]# mkdir istio [root@easzlab-k8s-master-01 istio]# [root@easzlab-k8s-master-01 istio]# wget https://github.com/istio/istio/releases/download/1.15.2/istio-1.15.2-linux-amd64.tar.gz [root@easzlab-k8s-master-01 istio]# tar -xf istio-1.15.2-linux-amd64.tar.gz [root@easzlab-k8s-master-01 istio-1.15.2]# cp bin/istioctl /usr/local/bin/ [root@easzlab-k8s-master-01 istio-1.15.2]# istioctl install --set profile=demo -y ✔ Istio core installed ✔ Istiod installed ✔ Egress gateways installed ✔ Ingress gateways installed ✔ Installation complete Making this installation the default for injection and validation. Thank you for installing Istio 1.15. Please take a few minutes to tell us about your install/upgrade experience! https://forms.gle/SWHFBmwJspusK1hv6 [root@easzlab-k8s-master-01 istio-1.15.2]#
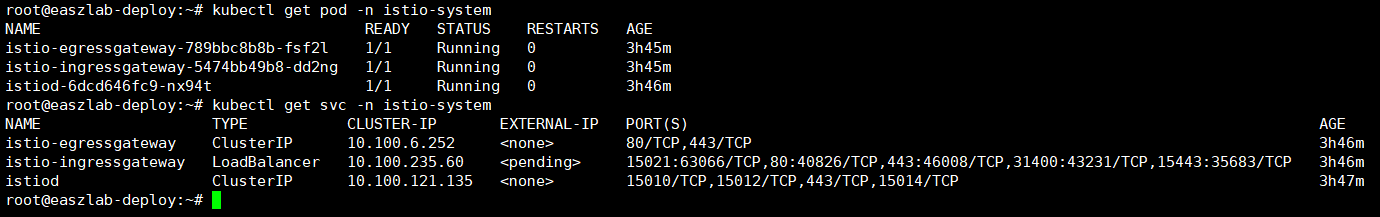
三、部署应用
官方参考文档:https://istio.io/latest/docs/setup/getting-started/
部署相应插件
[root@easzlab-k8s-master-01 ~]# cd istio-1.15.2/ [root@easzlab-k8s-master-01 samples]# ls addons/ README.md extras grafana.yaml jaeger.yaml kiali.yaml prometheus.yaml [root@easzlab-k8s-master-01 samples]# kubectl apply -f addons/ serviceaccount/grafana created configmap/grafana created service/grafana created deployment.apps/grafana created configmap/istio-grafana-dashboards created configmap/istio-services-grafana-dashboards created deployment.apps/jaeger created service/tracing created service/zipkin created service/jaeger-collector created serviceaccount/kiali created configmap/kiali created clusterrole.rbac.authorization.k8s.io/kiali-viewer created clusterrole.rbac.authorization.k8s.io/kiali created clusterrolebinding.rbac.authorization.k8s.io/kiali created role.rbac.authorization.k8s.io/kiali-controlplane created rolebinding.rbac.authorization.k8s.io/kiali-controlplane created service/kiali created deployment.apps/kiali created serviceaccount/prometheus created configmap/prometheus created clusterrole.rbac.authorization.k8s.io/prometheus created clusterrolebinding.rbac.authorization.k8s.io/prometheus created service/prometheus created deployment.apps/prometheus created [root@easzlab-k8s-master-01 samples]#
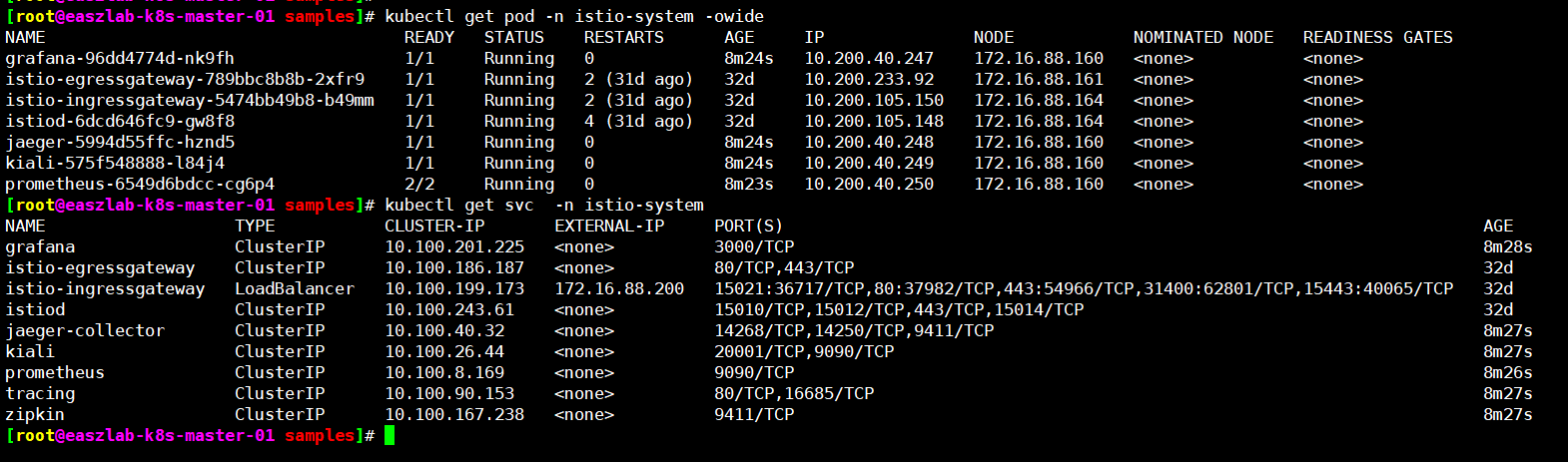 查看可以通过istio ingressgateway转发代理资源
查看可以通过istio ingressgateway转发代理资源
[root@easzlab-deploy nerdctl-1]# kubectl get crds |grep istio.io authorizationpolicies.security.istio.io 2022-10-18T16:21:52Z destinationrules.networking.istio.io 2022-10-18T16:21:52Z envoyfilters.networking.istio.io 2022-10-18T16:21:52Z gateways.networking.istio.io 2022-10-18T16:21:52Z istiooperators.install.istio.io 2022-10-18T16:21:52Z peerauthentications.security.istio.io 2022-10-18T16:21:52Z proxyconfigs.networking.istio.io 2022-10-18T16:21:52Z requestauthentications.security.istio.io 2022-10-18T16:21:52Z serviceentries.networking.istio.io 2022-10-18T16:21:52Z sidecars.networking.istio.io 2022-10-18T16:21:52Z telemetries.telemetry.istio.io 2022-10-18T16:21:53Z virtualservices.networking.istio.io 2022-10-18T16:21:53Z wasmplugins.extensions.istio.io 2022-10-18T16:21:53Z workloadentries.networking.istio.io 2022-10-18T16:21:53Z workloadgroups.networking.istio.io 2022-10-18T16:21:53Z [root@easzlab-deploy nerdctl-1]#
[root@easzlab-deploy nerdctl-1]# kubectl api-resources --api-group=networking.istio.io NAME SHORTNAMES APIVERSION NAMESPACED KIND destinationrules dr networking.istio.io/v1beta1 true DestinationRule envoyfilters networking.istio.io/v1alpha3 true EnvoyFilter gateways gw networking.istio.io/v1beta1 true Gateway proxyconfigs networking.istio.io/v1beta1 true ProxyConfig serviceentries se networking.istio.io/v1beta1 true ServiceEntry sidecars networking.istio.io/v1beta1 true Sidecar virtualservices vs networking.istio.io/v1beta1 true VirtualService workloadentries we networking.istio.io/v1beta1 true WorkloadEntry workloadgroups wg networking.istio.io/v1beta1 true WorkloadGroup [root@easzlab-deploy nerdctl-1]# [root@easzlab-k8s-master-01 samples]# istioctl proxy-status NAME CLUSTER CDS LDS EDS RDS ECDS ISTIOD VERSION details-v1-7d4d9d5fcb-c4dbn.istio Kubernetes SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-6dcd646fc9-gw8f8 1.15.2 istio-egressgateway-789bbc8b8b-2xfr9.istio-system Kubernetes SYNCED SYNCED SYNCED NOT SENT NOT SENT istiod-6dcd646fc9-gw8f8 1.15.2 istio-ingressgateway-5474bb49b8-b49mm.istio-system Kubernetes SYNCED SYNCED SYNCED NOT SENT NOT SENT istiod-6dcd646fc9-gw8f8 1.15.2 productpage-v1-66756cddfd-vhtj4.istio Kubernetes SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-6dcd646fc9-gw8f8 1.15.2 ratings-v1-85cc46b6d4-4m9kx.istio Kubernetes SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-6dcd646fc9-gw8f8 1.15.2 reviews-v1-777df99c6d-2fl56.istio Kubernetes SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-6dcd646fc9-gw8f8 1.15.2 reviews-v2-cdd8fb88b-9pkcx.istio Kubernetes SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-6dcd646fc9-gw8f8 1.15.2 reviews-v3-58b6479b-4rqds.istio Kubernetes SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-6dcd646fc9-gw8f8 1.15.2 [root@easzlab-k8s-master-01 samples]#
克隆马哥istio项目到本地
[root@easzlab-k8s-master-01 ~]# git clone https://github.com/iKubernetes/istio-in-practise.git Cloning into 'istio-in-practise'... remote: Enumerating objects: 306, done. remote: Counting objects: 100% (306/306), done. remote: Compressing objects: 100% (181/181), done. remote: Total 306 (delta 156), reused 252 (delta 115), pack-reused 0 Receiving objects: 100% (306/306), 66.78 KiB | 663.00 KiB/s, done. Resolving deltas: 100% (156/156), done. [root@easzlab-k8s-master-01 ~]# [root@easzlab-k8s-master-01 Traffic-Management-Basics]# pwd /root/istio-in-practise/Traffic-Management-Basics [root@easzlab-k8s-master-01 Traffic-Management-Basics]# ll -h total 36K drwxr-xr-x 9 root root 4.0K Nov 20 19:03 ./ drwxr-xr-x 8 root root 4.0K Nov 20 19:03 ../ drwxr-xr-x 2 root root 4.0K Nov 20 19:03 grafana/ drwxr-xr-x 2 root root 4.0K Nov 20 19:03 kiali/ drwxr-xr-x 2 root root 4.0K Nov 20 19:03 kiali-port-80/ drwxr-xr-x 15 root root 4.0K Nov 20 19:03 ms-demo/ drwxr-xr-x 2 root root 4.0K Nov 20 19:03 prometheus/ drwxr-xr-x 2 root root 4.0K Nov 20 19:03 skywalking/ drwxr-xr-x 2 root root 4.0K Nov 20 19:03 tracing/ [root@easzlab-k8s-master-01 Traffic-Management-Basics]# [root@easzlab-k8s-master-01 Traffic-Management-Basics]# cd kiali-port-80/ [root@easzlab-k8s-master-01 kiali-port-80]# ls kiali-destinationrule.yaml kiali-gateway.yaml kiali-virtualservice.yaml [root@easzlab-k8s-master-01 kiali-port-80]# cat kiali-destinationrule.yaml apiVersion: networking.istio.io/v1beta1 kind: DestinationRule metadata: name: kiali namespace: istio-system spec: host: kiali trafficPolicy: tls: mode: DISABLE --- [root@easzlab-k8s-master-01 kiali-port-80]# cat kiali-gateway.yaml apiVersion: networking.istio.io/v1beta1 kind: Gateway metadata: name: kiali-gateway namespace: istio-system spec: selector: app: istio-ingressgateway servers: - port: number: 80 name: http-kiali protocol: HTTP hosts: - "kiali.magedu.com" --- [root@easzlab-k8s-master-01 kiali-port-80]# cat kiali-virtualservice.yaml apiVersion: networking.istio.io/v1beta1 kind: VirtualService metadata: name: kiali-virtualservice namespace: istio-system spec: hosts: - "kiali.magedu.com" gateways: - kiali-gateway http: - match: - uri: prefix: / route: - destination: host: kiali port: number: 20001 --- [root@easzlab-k8s-master-01 kiali-port-80]# [root@easzlab-k8s-master-01 kiali-port-80]# kubectl apply -f . destinationrule.networking.istio.io/kiali created gateway.networking.istio.io/kiali-gateway created virtualservice.networking.istio.io/kiali-virtualservice created [root@easzlab-k8s-master-01 kiali-port-80]# [root@easzlab-k8s-master-01 kiali-port-80]# kubectl get virtualservices.networking.istio.io -n istio-system NAME GATEWAYS HOSTS AGE kiali-virtualservice ["kiali-gateway"] ["kiali.magedu.com"] 64s [root@easzlab-k8s-master-01 kiali-port-80]#
配置扩展外部ip地址
[root@easzlab-deploy ~]# kubectl edit svc -n istio-system istio-ingressgateway #配置扩展IP地址 [root@easzlab-deploy ~]# kubectl get svc -n istio-system istio-ingressgateway -oyaml apiVersion: v1 kind: Service metadata: annotations: kubectl.kubernetes.io/last-applied-configuration: | {"apiVersion":"v1","kind":"Service","metadata":{"annotations":{},"labels":{"app":"istio-ingressgateway","install.operator.istio.io/owning-resource":"unknown","install.operator.istio.io/owning-resource-namespace":"istio-system","istio":"ingressgateway","istio.io/rev":"default","operator.istio.io/component":"IngressGateways","operator.istio.io/managed":"Reconcile","operator.istio.io/version":"1.15.2","release":"istio"},"name":"istio-ingressgateway","namespace":"istio-system"},"spec":{"ports":[{"name":"status-port","port":15021,"protocol":"TCP","targetPort":15021},{"name":"http2","port":80,"protocol":"TCP","targetPort":8080},{"name":"https","port":443,"protocol":"TCP","targetPort":8443},{"name":"tcp","port":31400,"protocol":"TCP","targetPort":31400},{"name":"tls","port":15443,"protocol":"TCP","targetPort":15443}],"selector":{"app":"istio-ingressgateway","istio":"ingressgateway"},"type":"LoadBalancer"}} creationTimestamp: "2022-10-18T16:22:42Z" labels: app: istio-ingressgateway install.operator.istio.io/owning-resource: unknown install.operator.istio.io/owning-resource-namespace: istio-system istio: ingressgateway istio.io/rev: default operator.istio.io/component: IngressGateways operator.istio.io/managed: Reconcile operator.istio.io/version: 1.15.2 release: istio name: istio-ingressgateway namespace: istio-system resourceVersion: "8397453" uid: 835853a5-1cad-4096-a0e0-521657319ccb spec: allocateLoadBalancerNodePorts: true clusterIP: 10.100.199.173 clusterIPs: - 10.100.199.173 externalIPs: - 172.16.88.210 #这里ip地址需要k8s集群节点同网段没有使用的IP地址 externalTrafficPolicy: Cluster internalTrafficPolicy: Cluster ipFamilies: - IPv4 ipFamilyPolicy: SingleStack ports: - name: status-port nodePort: 36717 port: 15021 protocol: TCP targetPort: 15021 - name: http2 nodePort: 37982 port: 80 protocol: TCP targetPort: 8080 - name: https nodePort: 54966 port: 443 protocol: TCP targetPort: 8443 - name: tcp nodePort: 62801 port: 31400 protocol: TCP targetPort: 31400 - name: tls nodePort: 40065 port: 15443 protocol: TCP targetPort: 15443 selector: app: istio-ingressgateway istio: ingressgateway sessionAffinity: None type: LoadBalancer status: loadBalancer: {} [root@easzlab-deploy ~]# [root@easzlab-deploy ~]# kubectl get svc -n istio-system NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE grafana ClusterIP 10.100.201.225 <none> 3000/TCP 4h46m istio-egressgateway ClusterIP 10.100.186.187 <none> 80/TCP,443/TCP 32d istio-ingressgateway LoadBalancer 10.100.199.173 172.16.88.210 15021:36717/TCP,80:37982/TCP,443:54966/TCP,31400:62801/TCP,15443:40065/TCP 32d istiod ClusterIP 10.100.243.61 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 32d jaeger-collector ClusterIP 10.100.40.32 <none> 14268/TCP,14250/TCP,9411/TCP 4h46m kiali ClusterIP 10.100.26.44 <none> 20001/TCP,9090/TCP 4h46m prometheus ClusterIP 10.100.8.169 <none> 9090/TCP 4h46m tracing ClusterIP 10.100.90.153 <none> 80/TCP,16685/TCP 4h46m zipkin ClusterIP 10.100.167.238 <none> 9411/TCP 4h46m [root@easzlab-deploy ~]#
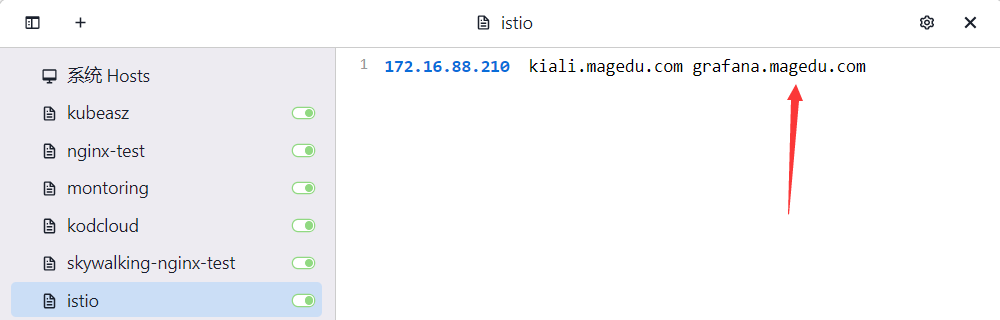
本地添加hosts
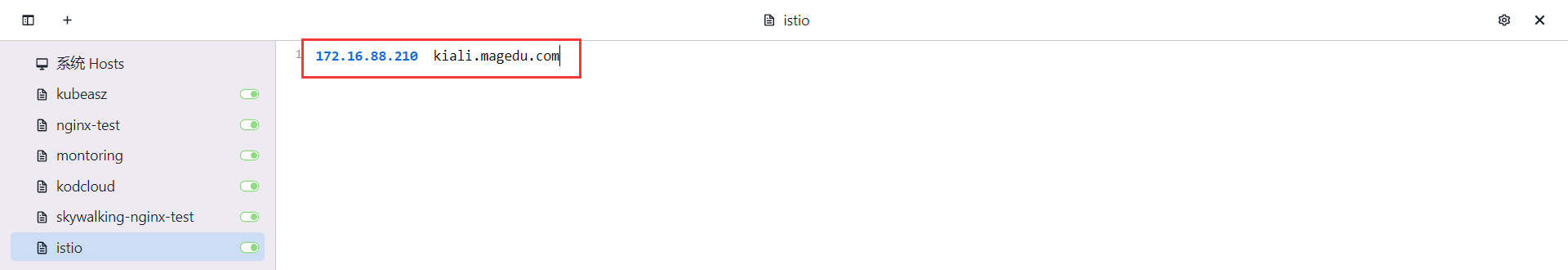
验证kiail http://kiali.magedu.com
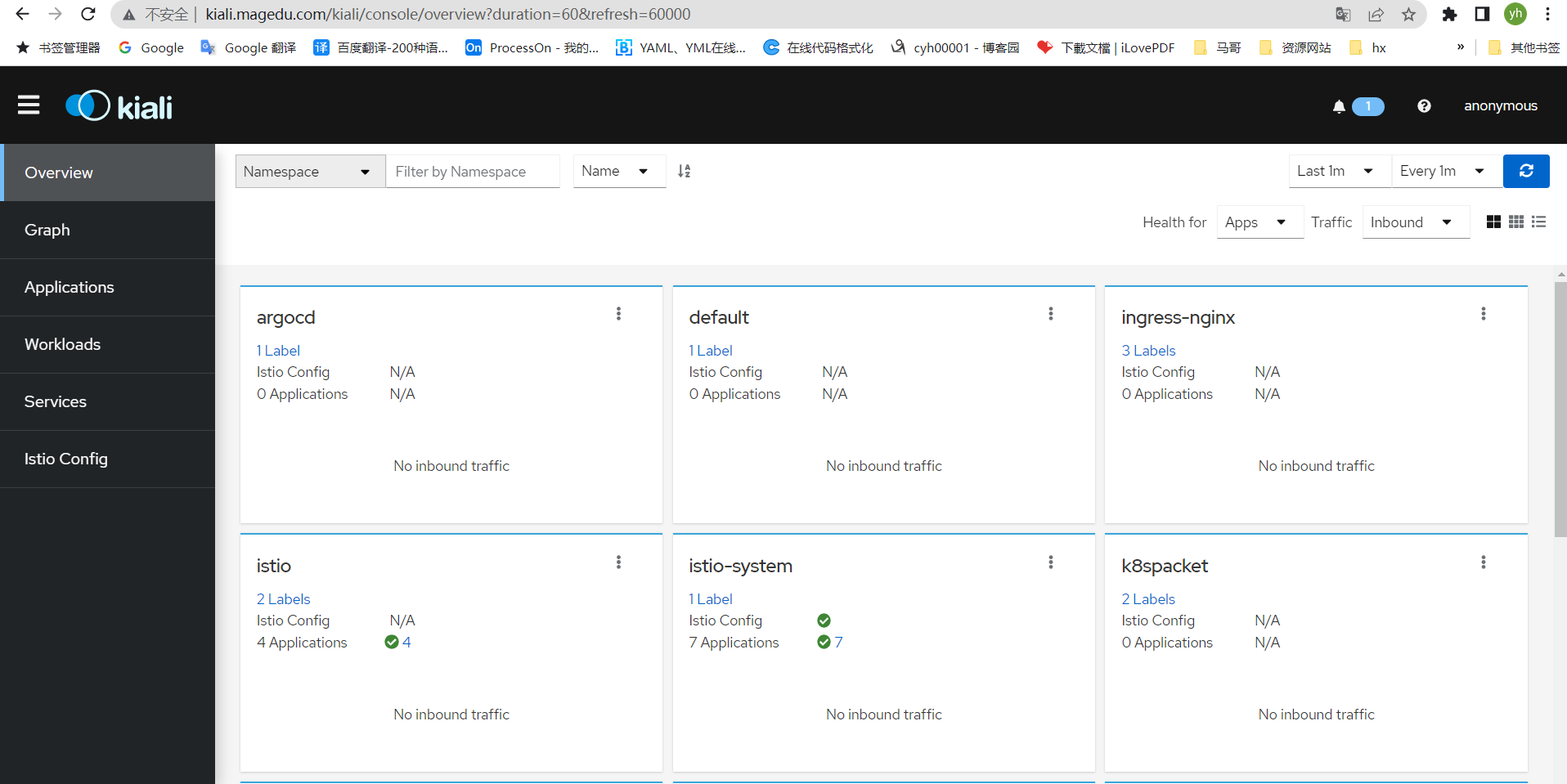
安装bookinfo
[root@easzlab-k8s-master-01 istio-1.15.2]# kubectl create ns istio
namespace/istio created
[root@easzlab-k8s-master-01 istio-1.15.2]# kubectl label namespace istio istio-injection=enabled
namespace/istio labeled
[root@easzlab-k8s-master-01 istio-1.15.2]#
[root@easzlab-k8s-master-01 istio-1.15.2]# kubectl apply -f samples/bookinfo/platform/kube/bookinfo.yaml
service/details created
serviceaccount/bookinfo-details created
deployment.apps/details-v1 created
service/ratings created
serviceaccount/bookinfo-ratings created
deployment.apps/ratings-v1 created
service/reviews created
serviceaccount/bookinfo-reviews created
deployment.apps/reviews-v1 created
deployment.apps/reviews-v2 created
deployment.apps/reviews-v3 created
service/productpage created
serviceaccount/bookinfo-productpage created
deployment.apps/productpage-v1 created
[root@easzlab-k8s-master-01 istio-1.15.2]#
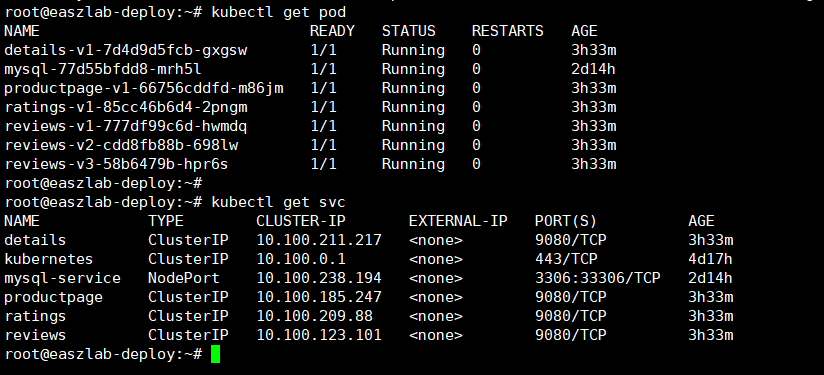
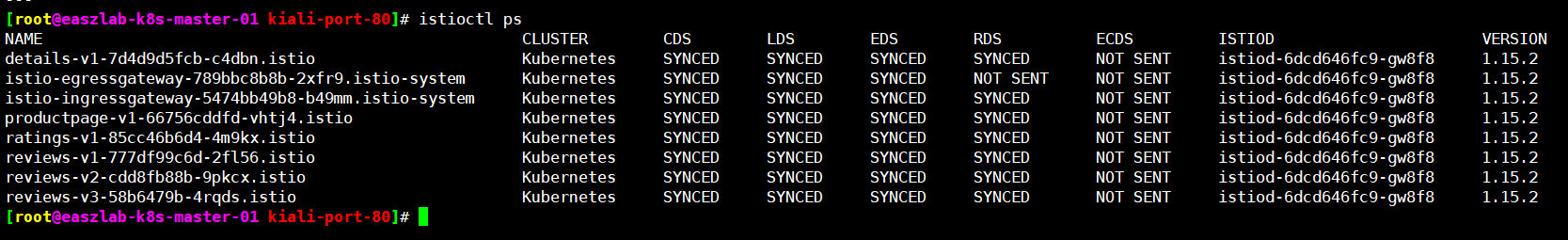
安装istio集群内部访问客户端
[root@easzlab-k8s-master-01 sleep]# pwd /root/istio-1.15.2/samples/sleep [root@easzlab-k8s-master-01 sleep]# [root@easzlab-k8s-master-01 sleep]# kubectl apply -f sleep.yaml serviceaccount/sleep created service/sleep created deployment.apps/sleep created [root@easzlab-k8s-master-01 sleep]# [root@easzlab-k8s-master-01 sleep]# kubectl get pod -owide NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES details-v1-7d4d9d5fcb-c4dbn 2/2 Running 4 (31d ago) 32d 10.200.104.210 172.16.88.163 <none> <none> productpage-v1-66756cddfd-vhtj4 2/2 Running 4 (31d ago) 32d 10.200.245.29 172.16.88.165 <none> <none> ratings-v1-85cc46b6d4-4m9kx 2/2 Running 4 (31d ago) 32d 10.200.245.30 172.16.88.165 <none> <none> reviews-v1-777df99c6d-2fl56 2/2 Running 4 (31d ago) 32d 10.200.233.97 172.16.88.161 <none> <none> reviews-v2-cdd8fb88b-9pkcx 2/2 Running 4 (31d ago) 32d 10.200.105.153 172.16.88.164 <none> <none> reviews-v3-58b6479b-4rqds 2/2 Running 4 (31d ago) 32d 10.200.233.93 172.16.88.161 <none> <none> sleep-69cfb4968f-6sjld 2/2 Running 0 4m32s 10.200.40.195 172.16.88.160 <none> <none> [root@easzlab-k8s-master-01 sleep]# [root@easzlab-k8s-master-01 sleep]# kubectl get svc NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE details ClusterIP 10.100.204.76 <none> 9080/TCP 32d productpage ClusterIP 10.100.8.125 <none> 9080/TCP 32d ratings ClusterIP 10.100.70.85 <none> 9080/TCP 32d reviews ClusterIP 10.100.18.76 <none> 9080/TCP 32d sleep ClusterIP 10.100.47.97 <none> 80/TCP 6m22s [root@easzlab-k8s-master-01 sleep]#
验证服务访问
[root@easzlab-k8s-master-01 sleep]# kubectl exec -it sleep-69cfb4968f-6sjld sh kubectl exec [POD] [COMMAND] is DEPRECATED and will be removed in a future version. Use kubectl exec [POD] -- [COMMAND] instead. / $ curl productpage:9080 <!DOCTYPE html> <html> <head> <title>Simple Bookstore App</title> <meta charset="utf-8"> <meta http-equiv="X-UA-Compatible" content="IE=edge"> <meta name="viewport" content="width=device-width, initial-scale=1"> <!-- Latest compiled and minified CSS --> <link rel="stylesheet" href="static/bootstrap/css/bootstrap.min.css"> <!-- Optional theme --> <link rel="stylesheet" href="static/bootstrap/css/bootstrap-theme.min.css"> </head> <body> <p> <h3>Hello! This is a simple bookstore application consisting of three services as shown below</h3> </p> <table class="table table-condensed table-bordered table-hover"><tr><th>name</th><td>http://details:9080</td></tr><tr><th>endpoint</th><td>details</td></tr><tr><th>children</th><td><table class="table table-condensed table-bordered table-hover"><tr><th>name</th><th>endpoint</th><th>children</th></tr><tr><td>http://details:9080</td><td>details</td><td></td></tr><tr><td>http://reviews:9080</td><td>reviews</td><td><table class="table table-condensed table-bordered table-hover"><tr><th>name</th><th>endpoint</th><th>children</th></tr><tr><td>http://ratings:9080</td><td>ratings</td><td></td></tr></table></td></tr></table></td></tr></table> <p> <h4>Click on one of the links below to auto generate a request to the backend as a real user or a tester </h4> </p> <p><a href="/productpage?u=normal">Normal user</a></p> <p><a href="/productpage?u=test">Test user</a></p> <!-- Latest compiled and minified JavaScript --> <script src="static/jquery.min.js"></script> <!-- Latest compiled and minified JavaScript --> <script src="static/bootstrap/js/bootstrap.min.js"></script> </body> </html> / $
配置productpage集群外部访问
[root@easzlab-k8s-master-01 networking]# pwd /root/istio-1.15.2/samples/bookinfo/networking [root@easzlab-k8s-master-01 networking]# kubectl apply -f bookinfo-gateway.yaml gateway.networking.istio.io/bookinfo-gateway created virtualservice.networking.istio.io/bookinfo created [root@easzlab-k8s-master-01 networking]#
按F5可以跳转到不同页面
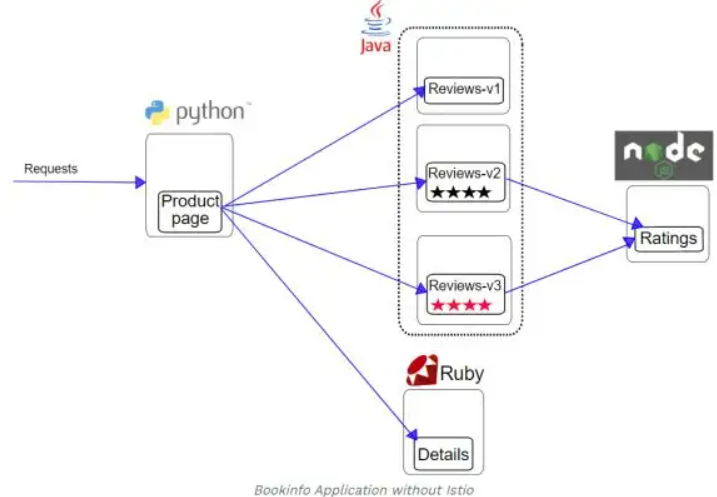
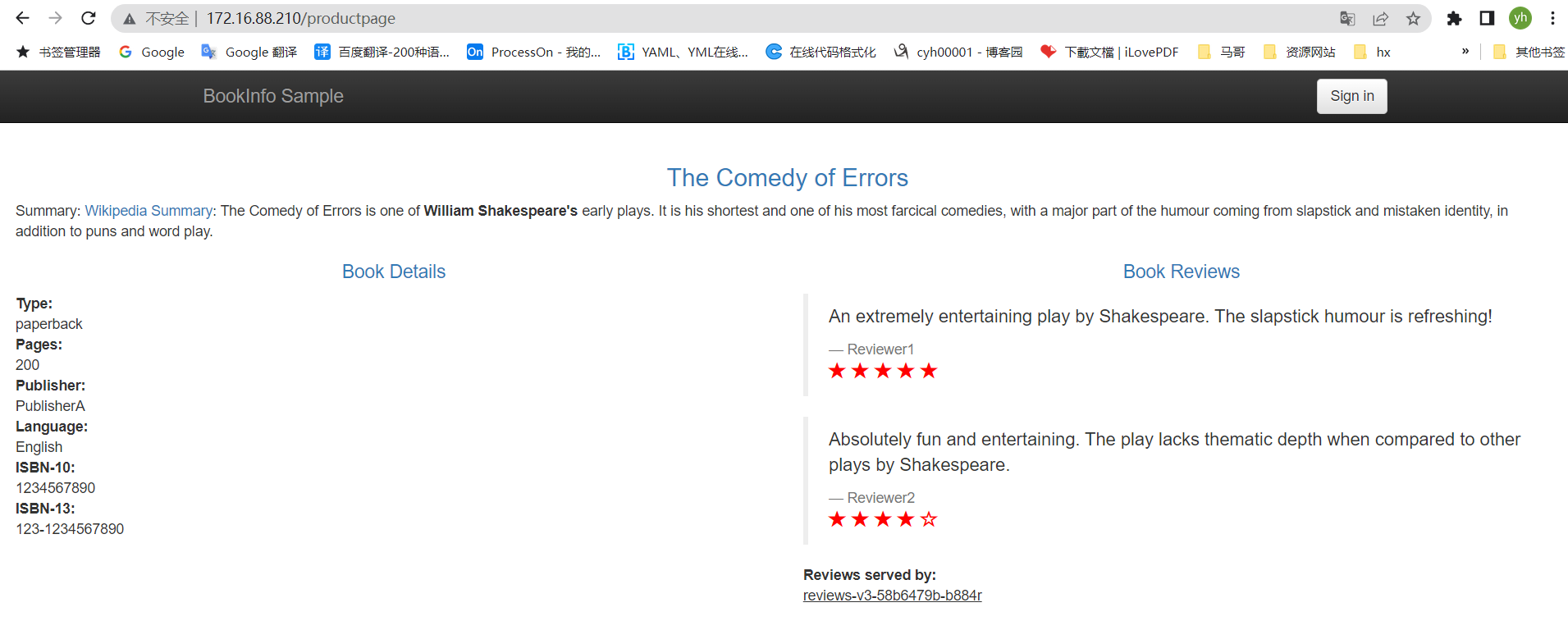
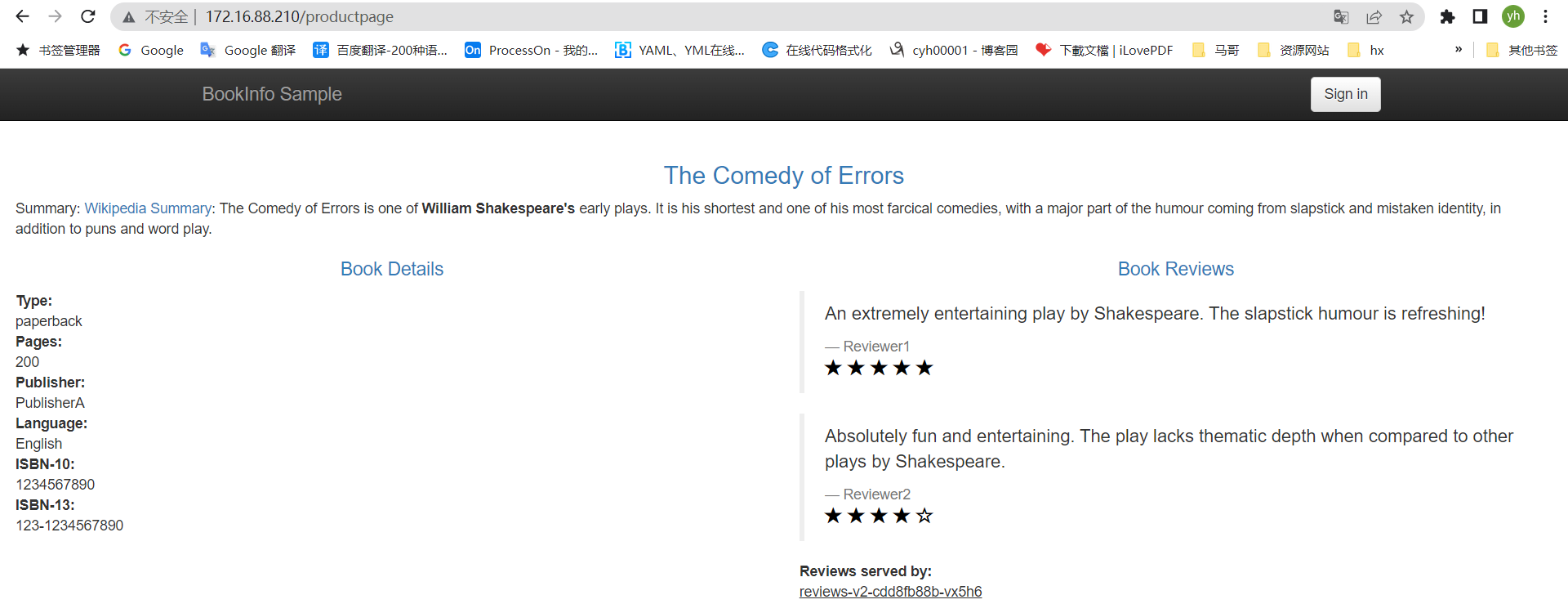
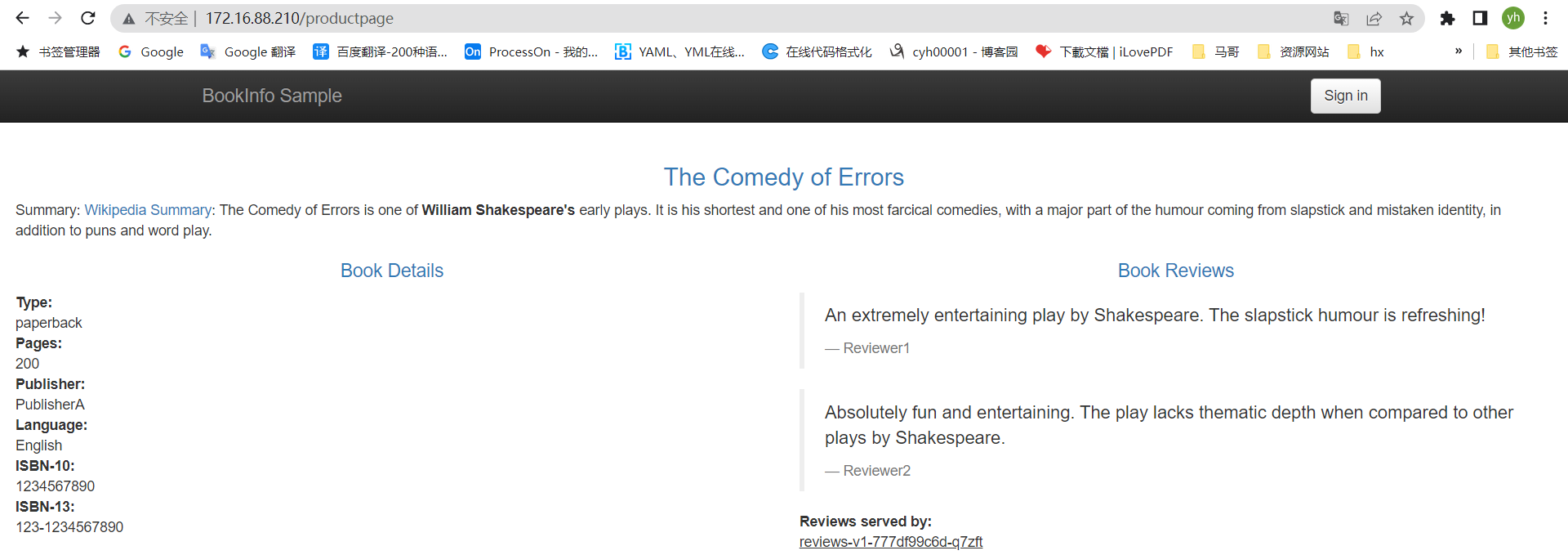
通过shell命令持续不断范文页面,产生kiali数据
[root@easzlab-deploy ~]# while true; do elinks --dump 172.16.88.210/productpage;sleep 0.$RANDOM;done
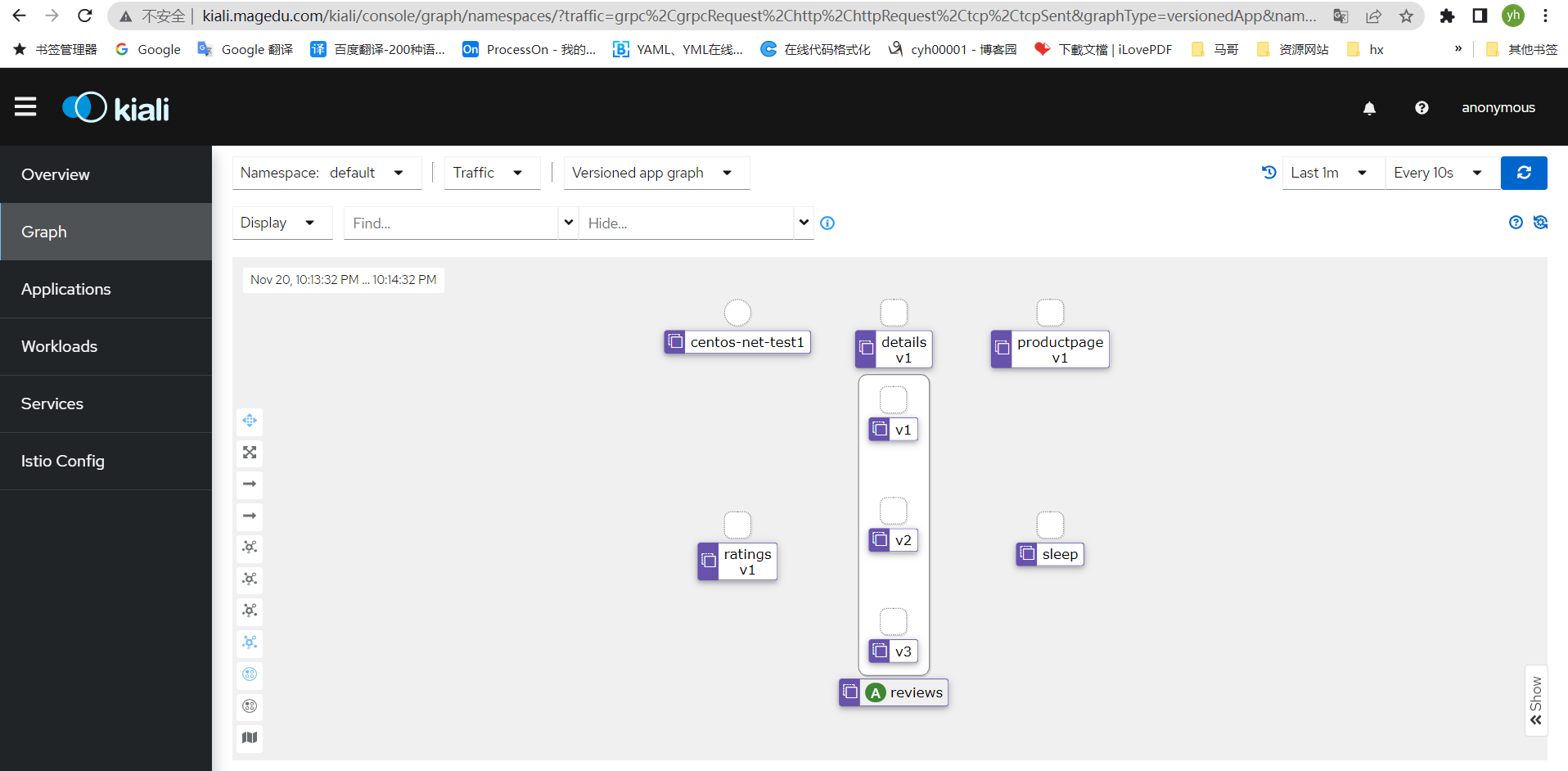
此时kiali会有相应数据流量产生
安装配置grafana
[root@easzlab-k8s-master-01 grafana]# pwd /root/istio-in-practise/Traffic-Management-Basics/grafana [root@easzlab-k8s-master-01 grafana]# [root@easzlab-k8s-master-01 grafana]# cat grafana-destinationrule.yaml apiVersion: networking.istio.io/v1beta1 kind: DestinationRule metadata: name: grafana namespace: istio-system spec: host: grafana trafficPolicy: tls: mode: DISABLE --- [root@easzlab-k8s-master-01 grafana]# cat grafana-gateway.yaml apiVersion: networking.istio.io/v1beta1 kind: Gateway metadata: name: grafana-gateway namespace: istio-system spec: selector: app: istio-ingressgateway servers: - port: number: 80 name: http protocol: HTTP hosts: - "grafana.magedu.com" --- [root@easzlab-k8s-master-01 grafana]# cat grafana-virtualservice.yaml apiVersion: networking.istio.io/v1beta1 kind: VirtualService metadata: name: grafana-virtualservice namespace: istio-system spec: hosts: - "grafana.magedu.com" gateways: - grafana-gateway http: - match: - uri: prefix: / route: - destination: host: grafana port: number: 3000 --- [root@easzlab-k8s-master-01 grafana]# [root@easzlab-k8s-master-01 grafana]# kubectl apply -f . destinationrule.networking.istio.io/grafana created gateway.networking.istio.io/grafana-gateway created virtualservice.networking.istio.io/grafana-virtualservice created [root@easzlab-k8s-master-01 grafana]#
分类:
istio






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· C#/.NET/.NET Core优秀项目和框架2025年2月简报
· 什么是nginx的强缓存和协商缓存
· 一文读懂知识蒸馏
· Manus爆火,是硬核还是营销?