2021 东华杯 Reverse WP
不知道是博客园抽风了,还是我的博客的前端解析出了问题。将就看图片吧。
Hello
核心校验在native层,主要为一个异或和一个位交换运算。

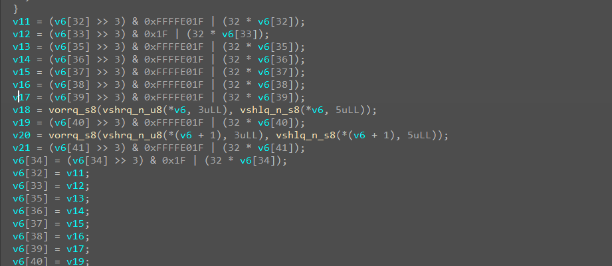
将v7和密文提取出来解密即可。
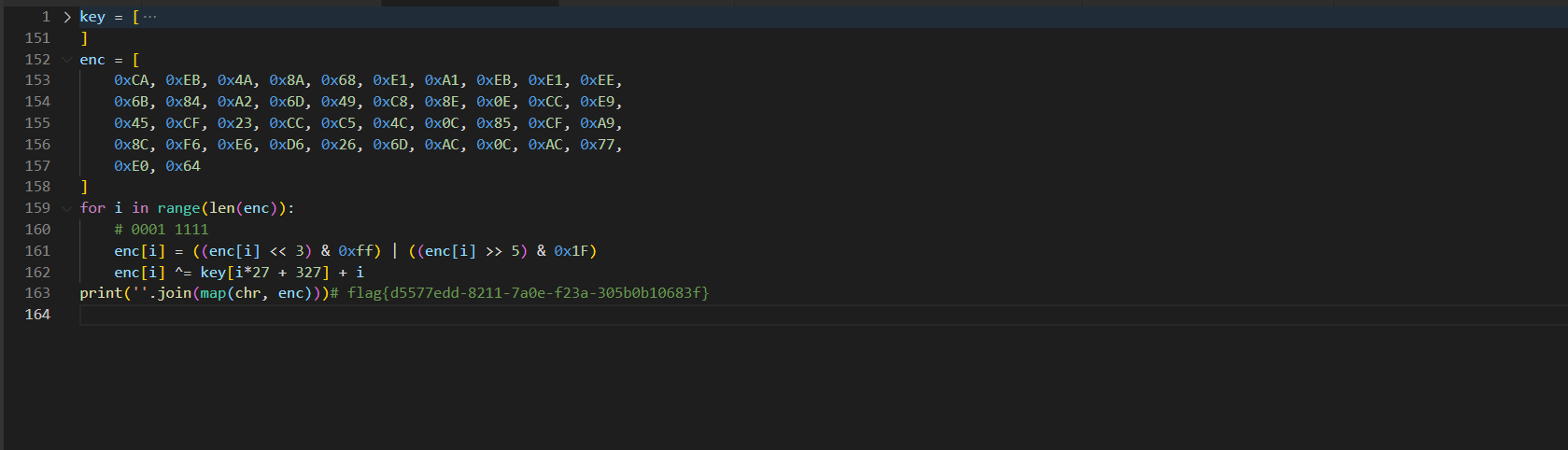
key = [
0x33, 0x30, 0x38, 0x32, 0x30, 0x32, 0x65, 0x34, 0x33, 0x30,
0x38, 0x32, 0x30, 0x31, 0x63, 0x63, 0x30, 0x32, 0x30, 0x31,
0x30, 0x31, 0x33, 0x30, 0x30, 0x64, 0x30, 0x36, 0x30, 0x39,
0x32, 0x61, 0x38, 0x36, 0x34, 0x38, 0x38, 0x36, 0x66, 0x37,
0x30, 0x64, 0x30, 0x31, 0x30, 0x31, 0x30, 0x35, 0x30, 0x35,
0x30, 0x30, 0x33, 0x30, 0x33, 0x37, 0x33, 0x31, 0x31, 0x36,
0x33, 0x30, 0x31, 0x34, 0x30, 0x36, 0x30, 0x33, 0x35, 0x35,
0x30, 0x34, 0x30, 0x33, 0x30, 0x63, 0x30, 0x64, 0x34, 0x31,
0x36, 0x65, 0x36, 0x34, 0x37, 0x32, 0x36, 0x66, 0x36, 0x39,
0x36, 0x34, 0x32, 0x30, 0x34, 0x34, 0x36, 0x35, 0x36, 0x32,
0x37, 0x35, 0x36, 0x37, 0x33, 0x31, 0x31, 0x30, 0x33, 0x30,
0x30, 0x65, 0x30, 0x36, 0x30, 0x33, 0x35, 0x35, 0x30, 0x34,
0x30, 0x61, 0x30, 0x63, 0x30, 0x37, 0x34, 0x31, 0x36, 0x65,
0x36, 0x34, 0x37, 0x32, 0x36, 0x66, 0x36, 0x39, 0x36, 0x34,
0x33, 0x31, 0x30, 0x62, 0x33, 0x30, 0x30, 0x39, 0x30, 0x36,
0x30, 0x33, 0x35, 0x35, 0x30, 0x34, 0x30, 0x36, 0x31, 0x33,
0x30, 0x32, 0x35, 0x35, 0x35, 0x33, 0x33, 0x30, 0x32, 0x30,
0x31, 0x37, 0x30, 0x64, 0x33, 0x32, 0x33, 0x31, 0x33, 0x30,
0x33, 0x33, 0x33, 0x30, 0x33, 0x36, 0x33, 0x31, 0x33, 0x34,
0x33, 0x33, 0x33, 0x30, 0x33, 0x34, 0x33, 0x38, 0x35, 0x61,
0x31, 0x38, 0x30, 0x66, 0x33, 0x32, 0x33, 0x30, 0x33, 0x35,
0x33, 0x31, 0x33, 0x30, 0x33, 0x32, 0x33, 0x32, 0x33, 0x37,
0x33, 0x31, 0x33, 0x34, 0x33, 0x33, 0x33, 0x30, 0x33, 0x34,
0x33, 0x38, 0x35, 0x61, 0x33, 0x30, 0x33, 0x37, 0x33, 0x31,
0x31, 0x36, 0x33, 0x30, 0x31, 0x34, 0x30, 0x36, 0x30, 0x33,
0x35, 0x35, 0x30, 0x34, 0x30, 0x33, 0x30, 0x63, 0x30, 0x64,
0x34, 0x31, 0x36, 0x65, 0x36, 0x34, 0x37, 0x32, 0x36, 0x66,
0x36, 0x39, 0x36, 0x34, 0x32, 0x30, 0x34, 0x34, 0x36, 0x35,
0x36, 0x32, 0x37, 0x35, 0x36, 0x37, 0x33, 0x31, 0x31, 0x30,
0x33, 0x30, 0x30, 0x65, 0x30, 0x36, 0x30, 0x33, 0x35, 0x35,
0x30, 0x34, 0x30, 0x61, 0x30, 0x63, 0x30, 0x37, 0x34, 0x31,
0x36, 0x65, 0x36, 0x34, 0x37, 0x32, 0x36, 0x66, 0x36, 0x39,
0x36, 0x34, 0x33, 0x31, 0x30, 0x62, 0x33, 0x30, 0x30, 0x39,
0x30, 0x36, 0x30, 0x33, 0x35, 0x35, 0x30, 0x34, 0x30, 0x36,
0x31, 0x33, 0x30, 0x32, 0x35, 0x35, 0x35, 0x33, 0x33, 0x30,
0x38, 0x32, 0x30, 0x31, 0x32, 0x32, 0x33, 0x30, 0x30, 0x64,
0x30, 0x36, 0x30, 0x39, 0x32, 0x61, 0x38, 0x36, 0x34, 0x38,
0x38, 0x36, 0x66, 0x37, 0x30, 0x64, 0x30, 0x31, 0x30, 0x31,
0x30, 0x31, 0x30, 0x35, 0x30, 0x30, 0x30, 0x33, 0x38, 0x32,
0x30, 0x31, 0x30, 0x66, 0x30, 0x30, 0x33, 0x30, 0x38, 0x32,
0x30, 0x31, 0x30, 0x61, 0x30, 0x32, 0x38, 0x32, 0x30, 0x31,
0x30, 0x31, 0x30, 0x30, 0x63, 0x62, 0x66, 0x32, 0x62, 0x30,
0x39, 0x65, 0x34, 0x33, 0x30, 0x38, 0x65, 0x62, 0x62, 0x34,
0x35, 0x39, 0x65, 0x38, 0x38, 0x34, 0x31, 0x65, 0x35, 0x61,
0x37, 0x62, 0x39, 0x32, 0x30, 0x34, 0x39, 0x37, 0x66, 0x65,
0x66, 0x32, 0x62, 0x33, 0x34, 0x39, 0x65, 0x38, 0x30, 0x36,
0x34, 0x38, 0x66, 0x37, 0x65, 0x62, 0x33, 0x35, 0x66, 0x34,
0x38, 0x64, 0x34, 0x30, 0x61, 0x37, 0x35, 0x65, 0x37, 0x63,
0x65, 0x37, 0x39, 0x34, 0x35, 0x62, 0x38, 0x62, 0x34, 0x32,
0x64, 0x31, 0x39, 0x37, 0x62, 0x65, 0x63, 0x30, 0x62, 0x66,
0x31, 0x37, 0x37, 0x65, 0x36, 0x63, 0x39, 0x38, 0x39, 0x39,
0x65, 0x64, 0x37, 0x30, 0x37, 0x64, 0x63, 0x63, 0x34, 0x61,
0x37, 0x32, 0x36, 0x63, 0x62, 0x31, 0x34, 0x63, 0x31, 0x61,
0x36, 0x39, 0x62, 0x30, 0x63, 0x34, 0x61, 0x30, 0x32, 0x34,
0x37, 0x34, 0x38, 0x30, 0x36, 0x66, 0x61, 0x37, 0x33, 0x63,
0x66, 0x62, 0x31, 0x30, 0x65, 0x31, 0x30, 0x66, 0x37, 0x62,
0x31, 0x36, 0x36, 0x35, 0x30, 0x32, 0x31, 0x63, 0x32, 0x34,
0x37, 0x36, 0x32, 0x62, 0x36, 0x65, 0x64, 0x61, 0x64, 0x36,
0x35, 0x63, 0x61, 0x36, 0x33, 0x63, 0x65, 0x61, 0x33, 0x63,
0x37, 0x32, 0x65, 0x30, 0x64, 0x34, 0x65, 0x34, 0x63, 0x61,
0x33, 0x66, 0x39, 0x38, 0x33, 0x30, 0x31, 0x31, 0x37, 0x33,
0x65, 0x65, 0x63, 0x33, 0x32, 0x35, 0x34, 0x33, 0x33, 0x37,
0x61, 0x66, 0x31, 0x66, 0x35, 0x61, 0x31, 0x31, 0x66, 0x37,
0x37, 0x39, 0x65, 0x63, 0x62, 0x65, 0x30, 0x34, 0x64, 0x31,
0x62, 0x37, 0x34, 0x64, 0x35, 0x33, 0x66, 0x35, 0x38, 0x33,
0x35, 0x65, 0x30, 0x31, 0x31, 0x32, 0x32, 0x32, 0x31, 0x35,
0x35, 0x61, 0x35, 0x36, 0x66, 0x39, 0x37, 0x65, 0x30, 0x30,
0x64, 0x37, 0x35, 0x33, 0x37, 0x34, 0x63, 0x64, 0x39, 0x33,
0x30, 0x38, 0x30, 0x64, 0x66, 0x61, 0x30, 0x38, 0x37, 0x63,
0x64, 0x33, 0x35, 0x36, 0x61, 0x39, 0x39, 0x66, 0x65, 0x31,
0x65, 0x65, 0x62, 0x66, 0x35, 0x64, 0x36, 0x64, 0x35, 0x65,
0x33, 0x31, 0x38, 0x34, 0x36, 0x61, 0x61, 0x64, 0x35, 0x32,
0x35, 0x32, 0x63, 0x33, 0x61, 0x31, 0x37, 0x61, 0x34, 0x36,
0x35, 0x36, 0x65, 0x32, 0x65, 0x32, 0x31, 0x30, 0x63, 0x65,
0x31, 0x63, 0x37, 0x61, 0x61, 0x34, 0x64, 0x31, 0x34, 0x37,
0x66, 0x62, 0x38, 0x63, 0x66, 0x34, 0x34, 0x30, 0x61, 0x35,
0x30, 0x61, 0x64, 0x64, 0x36, 0x31, 0x62, 0x62, 0x62, 0x32,
0x65, 0x63, 0x32, 0x39, 0x39, 0x61, 0x32, 0x65, 0x30, 0x64,
0x61, 0x62, 0x30, 0x62, 0x34, 0x35, 0x30, 0x34, 0x37, 0x39,
0x36, 0x61, 0x63, 0x33, 0x61, 0x38, 0x39, 0x39, 0x64, 0x61,
0x35, 0x35, 0x33, 0x61, 0x62, 0x31, 0x64, 0x38, 0x33, 0x35,
0x37, 0x36, 0x36, 0x39, 0x31, 0x61, 0x62, 0x32, 0x33, 0x34,
0x30, 0x39, 0x64, 0x31, 0x38, 0x33, 0x39, 0x38, 0x30, 0x31,
0x34, 0x62, 0x33, 0x62, 0x35, 0x65, 0x61, 0x66, 0x31, 0x32,
0x65, 0x38, 0x33, 0x66, 0x34, 0x64, 0x39, 0x39, 0x61, 0x61,
0x30, 0x39, 0x65, 0x31, 0x65, 0x34, 0x65, 0x34, 0x63, 0x61,
0x65, 0x31, 0x33, 0x33, 0x35, 0x33, 0x30, 0x37, 0x33, 0x30,
0x63, 0x31, 0x31, 0x33, 0x33, 0x64, 0x61, 0x32, 0x62, 0x33,
0x64, 0x65, 0x65, 0x33, 0x37, 0x62, 0x35, 0x38, 0x65, 0x62,
0x31, 0x61, 0x35, 0x37, 0x39, 0x35, 0x62, 0x32, 0x32, 0x31,
0x65, 0x63, 0x35, 0x61, 0x38, 0x38, 0x33, 0x30, 0x37, 0x33,
0x31, 0x61, 0x34, 0x31, 0x31, 0x36, 0x37, 0x64, 0x32, 0x39,
0x35, 0x66, 0x39, 0x65, 0x31, 0x62, 0x30, 0x32, 0x30, 0x33,
0x30, 0x31, 0x30, 0x30, 0x30, 0x31, 0x33, 0x30, 0x30, 0x64,
0x30, 0x36, 0x30, 0x39, 0x32, 0x61, 0x38, 0x36, 0x34, 0x38,
0x38, 0x36, 0x66, 0x37, 0x30, 0x64, 0x30, 0x31, 0x30, 0x31,
0x30, 0x35, 0x30, 0x35, 0x30, 0x30, 0x30, 0x33, 0x38, 0x32,
0x30, 0x31, 0x30, 0x31, 0x30, 0x30, 0x30, 0x65, 0x34, 0x37,
0x34, 0x30, 0x32, 0x33, 0x35, 0x65, 0x39, 0x63, 0x66, 0x32,
0x62, 0x65, 0x33, 0x33, 0x64, 0x65, 0x33, 0x65, 0x30, 0x36,
0x64, 0x37, 0x37, 0x37, 0x31, 0x33, 0x39, 0x63, 0x62, 0x62,
0x63, 0x35, 0x63, 0x66, 0x30, 0x36, 0x32, 0x32, 0x32, 0x38,
0x35, 0x63, 0x31, 0x37, 0x64, 0x61, 0x30, 0x34, 0x36, 0x39,
0x37, 0x62, 0x38, 0x30, 0x36, 0x37, 0x33, 0x31, 0x38, 0x61,
0x61, 0x66, 0x38, 0x64, 0x66, 0x30, 0x66, 0x62, 0x62, 0x34,
0x64, 0x33, 0x31, 0x36, 0x36, 0x66, 0x32, 0x39, 0x33, 0x65,
0x61, 0x31, 0x35, 0x61, 0x61, 0x32, 0x35, 0x39, 0x32, 0x66,
0x30, 0x36, 0x65, 0x62, 0x36, 0x39, 0x32, 0x39, 0x61, 0x66,
0x30, 0x36, 0x33, 0x37, 0x32, 0x32, 0x61, 0x63, 0x39, 0x66,
0x33, 0x30, 0x61, 0x64, 0x38, 0x35, 0x65, 0x32, 0x63, 0x30,
0x38, 0x37, 0x35, 0x36, 0x34, 0x39, 0x33, 0x31, 0x64, 0x36,
0x61, 0x63, 0x36, 0x35, 0x66, 0x63, 0x64, 0x35, 0x66, 0x62,
0x63, 0x38, 0x36, 0x34, 0x62, 0x33, 0x64, 0x63, 0x39, 0x38,
0x34, 0x31, 0x65, 0x30, 0x33, 0x39, 0x63, 0x36, 0x65, 0x31,
0x64, 0x35, 0x66, 0x62, 0x63, 0x35, 0x63, 0x32, 0x66, 0x38,
0x61, 0x64, 0x66, 0x39, 0x30, 0x61, 0x35, 0x34, 0x37, 0x62,
0x63, 0x34, 0x65, 0x62, 0x63, 0x30, 0x37, 0x64, 0x33, 0x38,
0x37, 0x39, 0x31, 0x34, 0x64, 0x62, 0x32, 0x34, 0x34, 0x35,
0x31, 0x63, 0x32, 0x63, 0x63, 0x38, 0x39, 0x39, 0x32, 0x35,
0x33, 0x35, 0x39, 0x62, 0x64, 0x33, 0x62, 0x62, 0x30, 0x37,
0x35, 0x30, 0x63, 0x37, 0x61, 0x61, 0x62, 0x66, 0x39, 0x64,
0x37, 0x34, 0x33, 0x62, 0x31, 0x38, 0x39, 0x33, 0x65, 0x39,
0x38, 0x62, 0x62, 0x63, 0x38, 0x66, 0x66, 0x37, 0x34, 0x62,
0x32, 0x34, 0x66, 0x63, 0x30, 0x62, 0x34, 0x62, 0x65, 0x32,
0x64, 0x62, 0x61, 0x61, 0x66, 0x31, 0x63, 0x39, 0x31, 0x37,
0x62, 0x62, 0x61, 0x30, 0x31, 0x34, 0x39, 0x36, 0x64, 0x30,
0x36, 0x31, 0x37, 0x66, 0x66, 0x63, 0x33, 0x61, 0x34, 0x61,
0x38, 0x62, 0x37, 0x61, 0x36, 0x65, 0x37, 0x39, 0x61, 0x33,
0x30, 0x33, 0x36, 0x32, 0x39, 0x38, 0x61, 0x36, 0x65, 0x62,
0x66, 0x35, 0x37, 0x62, 0x62, 0x30, 0x30, 0x30, 0x30, 0x31,
0x65, 0x34, 0x33, 0x61, 0x30, 0x62, 0x32, 0x34, 0x32, 0x38,
0x36, 0x34, 0x65, 0x65, 0x62, 0x62, 0x30, 0x66, 0x63, 0x65,
0x63, 0x39, 0x65, 0x33, 0x32, 0x33, 0x31, 0x34, 0x34, 0x64,
0x34, 0x34, 0x34, 0x37, 0x63, 0x38, 0x37, 0x38, 0x34, 0x33,
0x30, 0x66, 0x31, 0x38, 0x65, 0x36, 0x65, 0x33, 0x35, 0x38,
0x61, 0x64, 0x39, 0x37, 0x35, 0x36, 0x36, 0x66, 0x61, 0x30,
0x34, 0x64, 0x31, 0x66, 0x30, 0x37, 0x62, 0x31, 0x37, 0x31,
0x63, 0x31, 0x34, 0x37, 0x36, 0x63, 0x39, 0x61, 0x66, 0x35,
0x61, 0x31, 0x65, 0x62, 0x61, 0x30, 0x62, 0x66, 0x36, 0x36,
0x31, 0x36, 0x65, 0x32, 0x31, 0x39, 0x63, 0x30, 0x62, 0x39,
0x65, 0x31, 0x32, 0x39, 0x39, 0x64, 0x30, 0x39, 0x66, 0x65,
0x63, 0x64, 0x65, 0x64, 0x32, 0x34, 0x61, 0x38, 0x38, 0x30,
0x33, 0x39, 0x37, 0x66, 0x39, 0x32, 0x65, 0x30, 0x66, 0x39,
0x39, 0x64, 0x38, 0x39, 0x35, 0x31, 0x32, 0x32, 0x38, 0x63,
0x37, 0x37, 0x37, 0x30, 0x63, 0x31, 0x38, 0x34, 0x66, 0x64,
0x37, 0x37, 0x61, 0x64, 0x66, 0x66, 0x39, 0x34, 0x33, 0x62,
0x66, 0x63, 0x38, 0x62, 0x36, 0x61, 0x61, 0x35, 0x32, 0x34,
0x63, 0x35, 0x66, 0x30, 0x61, 0x36, 0x64, 0x37, 0x36, 0x38,
0x36, 0x66, 0x65, 0x33, 0x35, 0x34, 0x38, 0x36, 0x00
]
enc = [
0xCA, 0xEB, 0x4A, 0x8A, 0x68, 0xE1, 0xA1, 0xEB, 0xE1, 0xEE,
0x6B, 0x84, 0xA2, 0x6D, 0x49, 0xC8, 0x8E, 0x0E, 0xCC, 0xE9,
0x45, 0xCF, 0x23, 0xCC, 0xC5, 0x4C, 0x0C, 0x85, 0xCF, 0xA9,
0x8C, 0xF6, 0xE6, 0xD6, 0x26, 0x6D, 0xAC, 0x0C, 0xAC, 0x77,
0xE0, 0x64
]
for i in range(len(enc)):
# 0001 1111
enc[i] = ((enc[i] << 3) & 0xff) | ((enc[i] >> 5) & 0x1F)
enc[i] ^= key[i*27 + 327] + i
print(''.join(map(chr, enc)))# flag{d5577edd-8211-7a0e-f23a-305b0b10683f}
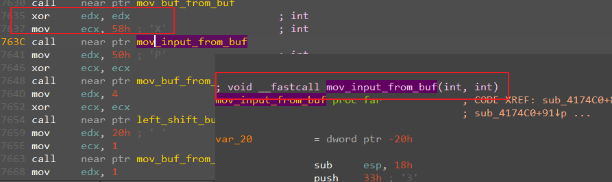
Hell's Gate
最初以为是到常规加解密题目,但后面发现有装载VEH异常函数,真正的校验逻辑在VEH函数中。
继续分析发现花指令中通过retf切换了CS段,CS:23->CS:33,在x64的保护模式下,CPU将从32位切换至64位执行指令,而该题目的数据运算都在64位模式下进行,数据交换和验证在32位下进行。
由于函数是32位调用,在64位进行运算,因此传参必须统一使用fastcall,并且参数不超过两个,IDA对函数调用约定的识别在这种特殊的环境下识别出错,这点需要手动修正一下。
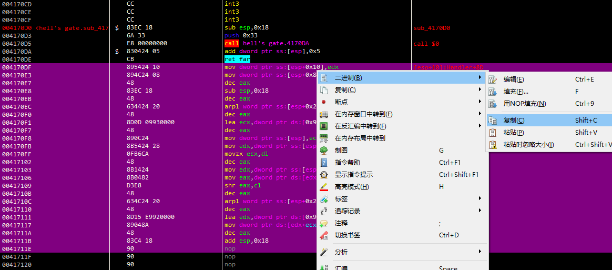
目前的主流调试器中,仅有windbg支持追踪调试32位和64位的自由切换。这个我个人目前是没有什么太好的分析方法,但因为指令量不是很大,我个人是直接将程序中64位指令的硬编码直接cpy进x64中进行分析。
对汇编指令进行分析,发现特征运算,右移5位,左移4位,异或等,显然是tea系加密函数。
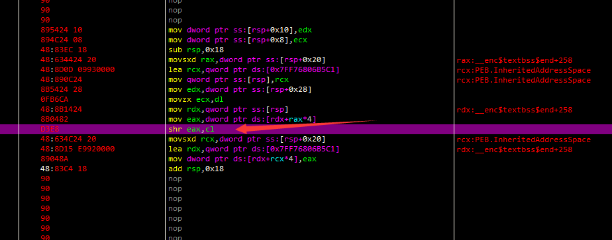
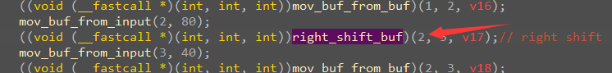
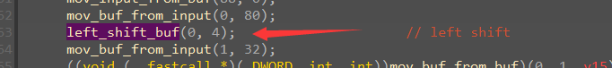
经过验证,是改了delta和迭代次数的tea算法。
#include <stdio.h>
#include <stdint.h>
void TeaDecrypt(uint32_t* v, uint32_t* k) {
uint32_t v0 = v[0], v1 = v[1], sum = 0xB879379E*16, i;
uint32_t delta = 0xB879379E;
uint32_t k0 = k[0], k1 = k[1], k2 = k[2], k3 = k[3];
for (i = 0; i < 16; i++) {
v1 -= ((v0 << 4) + k2) ^ (v0 + sum) ^ ((v0 >> 5) + k3);
v0 -= ((v1 << 4) + k0) ^ (v1 + sum) ^ ((v1 >> 5) + k1);
sum -= delta;
}
v[0] = v0; v[1] = v1;
}
int main()
{
unsigned char enc[] = {
0x0B, 0x65, 0x94, 0x2C, 0x9E, 0x4E, 0x49, 0x78, 0x44, 0xCF,
0xFA, 0xE7, 0xFB, 0xDB, 0xF9, 0x48, 0x45, 0xB1, 0x7B, 0x54,
0x42, 0x25, 0x5D, 0x92, 0xC4, 0xF4, 0xA9, 0x69, 0xD8, 0xA1,
0x96, 0x9A, 0
};
uint32_t key[] = { 0x12345678 , 0x87654321 ,0x13243546 ,0x64534231 };
uint32_t* ptr = (uint32_t*)enc;
for (int i = 0; i != 8; i+=2)
{
TeaDecrypt(ptr + i, key);
}
puts((char*)enc); //0f4d0db3668dd58cabb9eb409657eaa8
// D5C11A6D 3B6B320A
return 0;
}
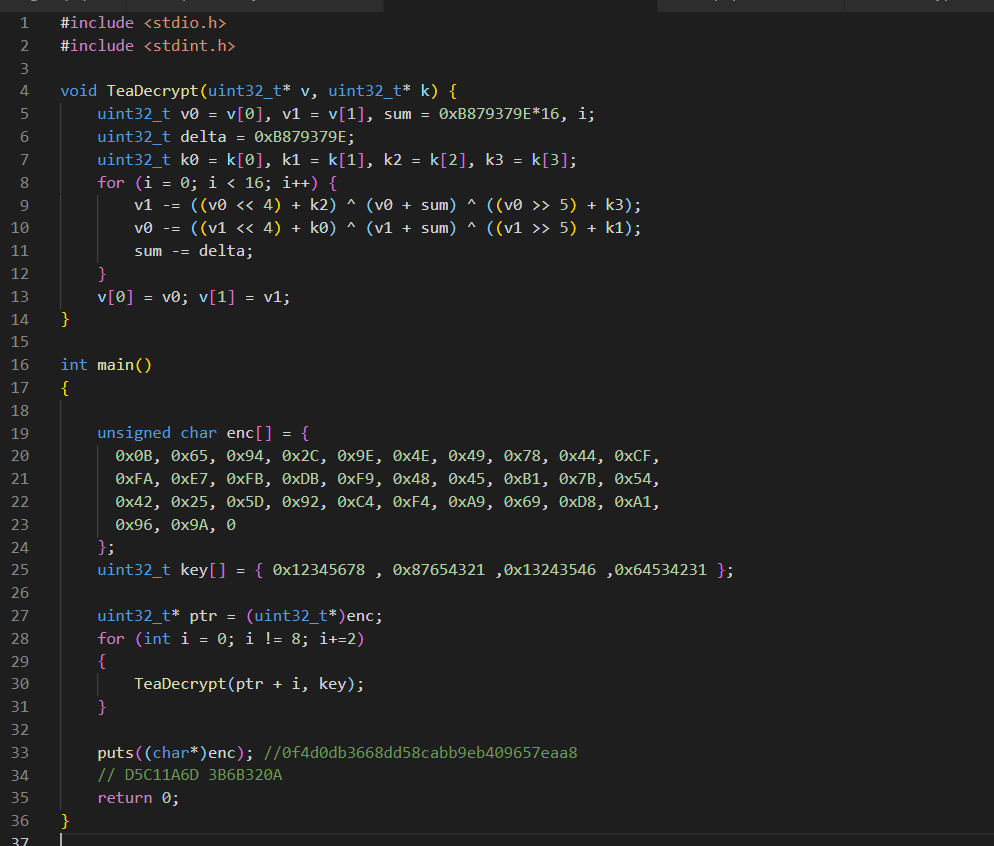
to be or not to be, is a question.



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 如何编写易于单元测试的代码
· 10年+ .NET Coder 心语,封装的思维:从隐藏、稳定开始理解其本质意义
· .NET Core 中如何实现缓存的预热?
· 从 HTTP 原因短语缺失研究 HTTP/2 和 HTTP/3 的设计差异
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 地球OL攻略 —— 某应届生求职总结
· 周边上新:园子的第一款马克杯温暖上架
· Open-Sora 2.0 重磅开源!
· 提示词工程——AI应用必不可少的技术
· .NET周刊【3月第1期 2025-03-02】