【ctfhub】crypto-1 wp
Rivest Shamir Adleman
题目给了e,n,c,n可分解,然后就是常规解rsa
from gmpy2 import *
from Crypto.Util.number import *
p = 15485863
q = 26384008867091745294633354547835212741691416673097444594871961708606898246191631284922865941012124184327243247514562575750057530808887589809848089461174100421708982184082294675500577336225957797988818721372546749131380876566137607036301473435764031659085276159909447255824316991731559776281695919056426990285120277950325598700770588152330565774546219611360167747900967511378709576366056727866239359744484343099322440674434020874200594041033926202578941508969596229398159965581521326643115137
e = 65537
n = 408579146706567976063586763758203051093687666875502812646277701560732347095463873824829467529879836457478436098685606552992513164224712398195503564207485938278827523972139196070431397049700119503436522251010430918143933255323117421712000644324381094600257291929523792609421325002527067471808992410166917641057703562860663026873111322556414272297111644069436801401012920448661637616392792337964865050210799542881102709109912849797010633838067759525247734892916438373776477679080154595973530904808231
c = 226582271940094442087193050781730854272200420106419489092394544365159707306164351084355362938310978502945875712496307487367548451311593283589317511213656234433015906518135430048027246548193062845961541375898496150123721180020417232872212026782286711541777491477220762823620612241593367070405349675337889270277102235298455763273194540359004938828819546420083966793260159983751717798236019327334525608143172073795095665271013295322241504491351162010517033995871502259721412160906176911277416194406909
Fai = (p-1)*(q-1)
d = invert(e,Fai)
m = pow(c,d,n)
print(long_to_bytes(m))
Modern Clueless Child
题目给了以下信息
Ciphertext = "52f41f58f51f47f57f49f48f5df46f6ef53f43f57f6cf50f6df53f53f40f58f51f6ef42f56f43f41f5ef5cf4e" (hex) Key = "12123"
发现f每2个字母就出现一次,flag开头是csictf{,转为16进制就是
63 73 69 63 74 66 7b
取该数组的前7位和上面的进行异或,得到
31 32 31 32 33 31 32
发现除去3就和密钥是对应的,写脚本处理一下
cipher = "52f41f58f51f47f57f49f48f5df46f6ef53f43f57f6cf50f6df53f53f40f58f51f6ef42f56f43f41f5ef5cf4e".split('f')
key = ['3'+i for i in "12123"]
res = []
for i,n in enumerate(cipher):
x = int(n,16)
y = int(key[i % len(key)],16)
res.append(hex(x^y)[2:])
res = ''.join(res)
print(bytes.fromhex(res).decode())
Quick Math
低加密广播攻击,比较简单
Mein Kampf
M4 UKW $ Gamma 2 4 $ 5 9 $ 14 3 $ 5 20 fv cd hu ik es op yl wq jm
"Ciphertext: zkrtwvvvnrkulxhoywoj" (Words in the flag are separated by underscores)
了解历史的就知道: enigma是二战时期纳粹德国使用的一系列相似的转子机械加解密机器 ,因此这个题题目的暗示,就是使用了这种加密,但是有一些我们不知道机器配置的地方有美元符号,因此使用暴力破解是最好的解法
附上国外大佬的wp
from enigma.machine import EnigmaMachine
ROTORS = ['I', 'II', 'III', 'IV', 'V', 'VI', 'VII', 'VIII', 'Beta', 'Gamma']
REFLECTORS = ['B', 'C', 'B-Thin', 'C-Thin']
state = 'M4 UKW $ Gamma 2 4 $ 5 9 $ 14 3 $ 5 20 fv cd hu ik es op yl wq jm'
enc = 'zkrtwvvvnrkulxhoywoj'
rings = '4 9 3 20'
plug = 'fv cd hu ik es op yl wq jm'.upper()
pos = '2 5 14 5'
pos = ''.join(chr(int(x) - 1 + ord('A')) for x in pos.split())
for rf in REFLECTORS:
for r2 in ROTORS:
for r3 in ROTORS:
for r4 in ROTORS:
rotors = ['Gamma', r2, r3, r4]
e = EnigmaMachine.from_key_sheet(rotors=rotors, ring_settings=rings,
reflector=rf, plugboard_settings=plug)
e.set_display(pos)
txt = e.process_text(enc).lower()
if 'csictf' in txt:
print(txt)
little RSA
题目给了
c=32949
n=64741
e=42667
以及一个加密的压缩包,这个n非常小,直接暴力破解跑出m,作为密码就能解开压缩包,得到flag
from gmpy2 import *
c=32949
n=64741
e=42667
for m in range(n):
temp = pow(m,e,n)
if temp == c:
print(m)
break
算法逆向
题目给出代码和密文
function encode( $str = '' ){
$strrev = strrev( $str );//逆序
$string = '';
for( $i=0; $i < strlen($strrev);$i++ ){
$char = substr( $strrev, $i, 1 );
$ordChar = ord( $char ) + 1;
$char = chr( $ordChar );
$string = $string.$char;//ascii加一
}
$string = base64_encode( $string );//base64加密
$string = strrev( $string );//倒序
$string = str_rot13( $string );//rot13加密
return $string;
}//==jEgWTn8kJrRyRFBuKJLuzH1LmDTAz
很简单,逆过程即可,部分代码如下
s = '~cFC65RhXYxNHIDyl|hbmG'
flag = ''
for i in s:
strs = chr((ord(i)-1))
flag += strs
print(flag[::-1])
回转13位
rot13解密后,再经过base64解密即可
滴答滴答
题目给了一个图片
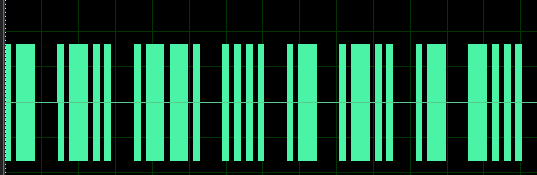
对应摩斯密码:.-/.-../.--./..../.-/.-../.-/-...,然后解密即可
栅栏解救
栅栏密码解密,栏数为5
rosb
2020-第五空间智能安全大赛
题目给出下列代码
from flag import flag
from Crypto.Util.number import long_to_bytes,bytes_to_long,getPrime
from os import urandom
def gen_arg():
p=getPrime(1024)
q=getPrime(1024)
open("log.txt","w").write(hex(p)+"\n"+hex(q))
n=p*q
e=getPrime(32)
return n,e,p,q
def mamacheck(c):
if long_to_bytes(c)[0:4]!="rose":
return False
return True
def babasay(m):
n,e,p,q=gen_arg()
c=pow(m,e,n)#一组加密
print hex(n)
print hex(e)
print hex(c)
if not mamacheck(c):
e=getPrime(32)
c = pow(m, e, n)#又是一组加密
print hex(e)
print hex(c)
m=bytes_to_long(flag+urandom(64))
babasay(m)
两组加密的数据,明文相同,n相同,因此可用共模攻击
from gmpy2 import invert
from Crypto.Util.number import *
def gongmogongji(n, c1, c2, e1, e2):
def egcd(a, b):
if b == 0:
return a, 0
else:
x, y = egcd(b, a % b)
return y, x - (a // b) * y
s = egcd(e1, e2)
s1 = s[0]
s2 = s[1]
if s1 < 0:
s1 = - s1
c1 = invert(c1, n)
elif s2 < 0:
s2 = - s2
c2 = invert(c2, n)
m = pow(c1, s1, n) * pow(c2, s2, n) % n
return long_to_bytes(m)
n = 0xa1d4d377001f1b8d5b2740514ce699b49dc8a02f12df9a960e80e2a6ee13b7a97d9f508721e3dd7a6842c24ab25ab87d1132358de7c6c4cee3fb3ec9b7fd873626bd0251d16912de1f0f1a2bba52b082339113ad1a262121db31db9ee1bf9f26023182acce8f84612bfeb075803cf610f27b7b16147f7d29cc3fd463df7ea31ca860d59aae5506479c76206603de54044e7b778e21082c4c4da795d39dc2b9c0589e577a773133c89fa8e3a4bd047b8e7d6da0d9a0d8a3c1a3607ce983deb350e1c649725cccb0e9d756fc3107dd4352aa18c45a65bab7772a4c5aef7020a1e67e6085cc125d9fc042d96489a08d885f448ece8f7f254067dfff0c4e72a63557
e1 = 0xf4c1158f
e2 = 0xf493f7d1
c1 = 0x2f6546062ff19fe6a3155d76ef90410a3cbc07fef5dff8d3d5964174dfcaf9daa003967a29c516657044e87c1cbbf2dba2e158452ca8b7adba5e635915d2925ac4f76312feb3b0c85c3b8722c0e4aedeaec2f2037cc5f676f99b7260c3f83ffbaba86cda0f6a9cd4c70b37296e8f36c3ceaae15b5bf0b290119592ff03427b80055f08c394e5aa6c45bd634c80c59a9f70a92dc70eebec15d4a5e256bf78775e0d3d14f3a0103d9ad8ea6257a0384091f14da59e52581ba2e8ad3adb9747435e9283e8064de21ac41ab2c7b161a3c072b7841d4a594a8b348a923d4cc39f02e05ce95a69c7500c29f6bb415c11e4e0cdb410d0ec2644d6243db38e893c8a3707
c2 = 0xd32dfad68d790022758d155f2d8bf46bb762ae5cc17281f2f3a8794575ec684819690b22106c1cdaea06abaf7d0dbf841ebd152be51528338d1da8a78f666e0da85367ee8c1e6addbf590fc15f1b2182972dcbe4bbe8ad359b7d15febd5597f5a87fa4c6c51ac4021af60aeb726a3dc7689daed70144db57d1913a4dc29a2b2ec34c99c507d0856d6bf5d5d01ee514d47c7477a7fb8a6747337e7caf2d6537183c20e14c7b79380d9f7bcd7cda9e3bfb00c2b57822663c9a5a24927bceec316c8ffc59ab3bfc19f364033da038a4fb3ecef3b4cb299f4b600f76b8a518b25b576f745412fe53d229e77e68380397eee6ffbc36f6cc734815cd4065dc73dcbcb
result = gongmogongji(n, c1, c2, e1, e2)
print(result)
rua
题目给了几组rsa对应的密文和n,但是并没有给出e,低指数加密广播攻击,并且爆破e
from Crypto.Util.number import *
from gmpy2 import *
import binascii
c = [8024667293310019199660855174436055144348010556139300886990767145319919733369837206849070207955417356957254331839203914525519504562595117422955140319552013305532068903324132309109484106720045613714716627620318471048195232209672212970269569790677144450501305289670783572919282909796765124242287108717189750662740283813981242918671472893126494796140877412502365037187659905034193901633516360208987731322599974612602945866477752340080783296268396044532883548423045471565356810753599618810964317690395898263698123505876052304469769153374038403491084285836952034950978098249299597775306141671935146933958644456499200221696, 17388575106047489057419896548519877785989670179021521580945768965101106268068805843720622749203590810185213416901978773748832854888898576822477243682874784689127705334243899967896321836688567602323551986980634884700045627950473546069670440078998428940082620044462222475031805594211784370238038168894827559017562364252406425134530719911057780692073760058203345936344269833206906999625580911856011564697811258009937314511410514416706482571471852503756675411177080916350899445106002226392895645443215522671155311715637759618276305217468892076287376401516124640727839779731609203202530346427613422430202271506248285086956, 5170826942130658374627267470548549396328896108666717036999395626588154882531377393671593939192779292151584678688653835775920356845071292462816417186595460417761844407911946323815187102170021222644920874070699813549492713967666736815947822200867353461264579419205756500926218294604616696969184793377381622818381733352202456524002876336304465082656612634304327627259494264840838687207529676882041997761204004549052900816658341867989593333356630311753611684503882509990853456022056473296726728969894815574884063807804354952314391764618179147583447848871220103094864884798102542377747761263052887894135796051521881179607]
n = [18856599160001833299560082802925753595735945621023660831294740454109973698430284916320395522883536507135735383517926050963512440162483065097256884040938259092582892259657340825971260278387406398529168309426241530551396056450450728728601248269612166083300938497235910244979946020059799495231539400114422748104072550004260736766137354572252872437140063474603268146956570787143010441293268321641092743010805639953103578977668248726500636191043930770036787317928372179939360510179438436665591755940224156131460271763912868322774604558314812111335691108887319827579162188169744014973478052491398688611046800951698773893393, 21996468204721630460566169654781925102402634427772676287751800587544894952838038401189546149401344752771866376882226876072201426041697882026653772987648569053238451992877808811034545463363146057879646485465730317977739706776287970278094261290398668538232727000322458605289913900919015380904209692398479885177984131014170652915222062267448446642158394150657058846328033404309210836219241651882903083719822769947131283541299760283547938795574020478852839044803553093825730447126796668238131579735916546235889726257184058908852902241422169929720898025622336508382492878690496154797198800699611812166851455110635853297883, 22182114562385985868993176463839749402849876738564142471647983947408274900941377521795379832791801082248237432130658027011388009638587979450937703029168222842849801985646044116463703409531938580410511097238939431284352109949200312466658018635489121157805030775386698514705824737070792739967925773549468095396944503293347398507980924747059180705269064441084577177316227162712249300900490014519213102070911105044792363935553422311683947941027846793608299170467483012199132849683112640658915359398437290872795783350944147546342693285520002760411554647284259473777888584007026980376463757296179071968120796742375210877789]
def CRT(mi,ai):
assert(reduce(gcd,mi)==1)
assert(isinstance(mi,list) and isinstance(ai,list))
M = reduce(lambda x,y:x*y,mi)
ai_ti_Mi = [a * (M / m) * invert(M / m, m) for (m, a) in zip(mi, ai)]
return reduce(lambda x,y:x+y,ai_ti_Mi) % M
'''
e = 3
m = iroot(CRT(n,c),e)[0]
#print(long_to_bytes(m))'''
for e in range(1,25):
print('Now the e is:',e)
try:
m = iroot(CRT(n,c),e)[0]
print(binascii.unhexlify(hex(m)[2:].strip("L")))
except:
pass
simple
题目给了
k1:123456 k2:321564 密文为:kgws{m8u8cm65-ue9k-44k5-8361-we225m76eeww}
仿射密码,但是没有给模数,爆破
from gmpy2 import *
import string
table = string.ascii_lowercase
enc = 'kgws{m8u8cm65-ue9k-44k5-8361-we225m76eeww}'
k1 = 123456
k2 = 321564
flag = ''
for j in range(1,26):
for i in enc:
if i in table:
a = ord(i)-97
try:
inv = invert(k1,j)
flag += chr(((a-k2)*inv)%j+97)
if 'flag{' in flag:
print(flag)
except:
pass
else:
flag += i
if 'flag{' in flag:
print(flag)
b64
题目给出信息
密文:uLdAuO8duojAFLEKjIgdpfGeZoELjJp9kSieuIsAjJ/LpSXDuCGduouz
泄露的密文:pTjMwJ9WiQHfvC+eFCFKTBpWQtmgjopgqtmPjfKfjSmdFLpeFf/Aj2ud3tN7u2+enC9+nLN8kgdWo29ZnCrOFCDdFCrOFoF=
泄露的明文:ashlkj!@sj1223%^&*Sd4564sd879s5d12f231a46qwjkd12J;DJjl;LjL;KJ8729128713
可以看出来是个换表的base64,但是仔细会发现很多字符并没有映射关系,在此断了思路,大佬wp献上,是爆破两个表的映射关系
from base64 import *
from string import *
def check(s):
for i in s:
if i not in "flag{-1234567890abcdef}":
return False
return True
flag = 'uLdAuO8duojAFLEKjIgdpfGeZoELjJp9kSieuIsAjJ/LpSXDuCGduouz'
a='pTjMwJ9WiQHfvC+eFCFKTBpWQtmgjopgqtmPjfKfjSmdFLpeFf/Aj2ud3tN7u2+enC9+nLN8kgdWo29ZnCrOFCDdFCrOFoF='
b='YXNobGtqIUBzajEyMjMlXiYqU2Q0NTY0c2Q4NzlzNWQxMmYyMzFhNDZxd2prZDEySjtESmpsO0xqTDtLSjg3MjkxMjg3MTM='
alpha = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789abcdefABCDEF+/'
FLAG=''
print("fail words")
for i in flag:
if i in a:
index = a.index(i)
FLAG+=b[index]
else:
FLAG+='!'
print i,
print "\nFLAG cipher"
print FLAG
#'ZmxhZ3sxZTNhMm!lN!0xYz!yLT!mNGYtOWIyZ!!hNGFmYW!kZj!xZTZ!'
print "alternative words"
aw=""
for i in alpha:
if i not in b:
aw += i
print aw
'@#$%^&'
table = 'ACHJKPRVefnuvw156789efAC+/'
print("for z")
for i in table:
if b64decode("ZTZ"+i)[-1] == '}':
FLAG = FLAG.replace("ZTZ!","ZTZ9")
table = table.replace(i,"")
#print FLAG
print("for G")
for i in table:
if check(b64decode("Zj"+i+"x")) and check(b64decode("Yz"+i+"y")):
#print b64decode("Zj"+i+"x")
FLAG = FLAG.replace("Zj!x","Zj"+i+"x").replace("Yz!y","Yz"+i+"y")
table = table.replace(i,"")
#print i
#print FLAG
print("for I and s")
for i in table:
for j in table:
if check(b64decode("N"+i+"0x")) and check(b64decode("Z"+i+j+"h")):
#print b64decode("N"+i+"0x"),b64decode("Z"+i+j+"h")
FLAG = FLAG.replace("N!0x","N"+i+"0x").replace("Z!!h","Z"+i+j+"h")
table = table.replace(i,"").replace(j,"")
#print i,j
#print FLAG
print("for X and E")
for i in table:
for j in table:
if j == i:
continue
s = b64decode(FLAG.replace("Mm!l","Mm"+i+"l").replace("LT!m","LT"+i+"m").replace("YW!k","YW"+j+'k'))
if check(s):
print s
最后得到的多个flag,依次提交,正确的即为flag
you raise me up
给出以下代码
from Crypto.Util.number import *
import random
n = 2 ** 512
m = random.randint(2, n-1) | 1
c = pow(m, bytes_to_long(flag), n)
print 'm = ' + str(m)
print 'c = ' + str(c)
# m = 391190709124527428959489662565274039318305952172936859403855079581402770986890308469084735451207885386318986881041563704825943945069343345307381099559075
# c = 6665851394203214245856789450723658632520816791621796775909766895233000234023642878786025644953797995373211308485605397024123180085924117610802485972584499
flag被转为长整数然后参与了运算,其实就是离散对数问题
m = 391190709124527428959489662565274039318305952172936859403855079581402770986890308469084735451207885386318986881041563704825943945069343345307381099559075
c = 6665851394203214245856789450723658632520816791621796775909766895233000234023642878786025644953797995373211308485605397024123180085924117610802485972584499
n = 2 ** 512
m = Mod(m,n)
c = Mod(c,n)
d = discrete_log(c,m)
print(d)
解出d,然后转为字符串就可以
boom
第一步的md5解密得到: en5oy
剩下的都是解方程,最后拼接得到flag
GM
2020-数字中国创新大赛虎符网络安全赛道
题目给了代码和结果,部分代码如下
def make_key( nbit):
while True:
p, q = getPrime(nbit), getPrime(nbit)
N, phi = p * q, (p-1)*(q-1)
x = random.randint(1, N)#随机数
if (N % 8 == 1) and (phi % 8 == 4) and (p != q):
if pow(q ** 2 * x, (p-1)/2, p) + pow(p ** 2 * x, (q-1)/2, q) == N - phi - 1:#重要条件
break
return (x, N), phi
def encrypt(msg, pkey):
msg, cipher = bin(bytes_to_long(msg))[2:], []
x, N = pkey
for bi in msg:
while True:
r = random.randint(1, N)
if gcd(r, N) == 1:
br = bin(r)[2:]
c = (pow(x, int(br + bi, 2), N) * r ** 2) % N#加密部分
cipher.append(c)
break
return cipher
nbit = 1024
pkey,phi = make_key( nbit)
enc = encrypt(flag, pkey)
print phi
print pkey[1]
print enc
代码中的重要条件如下(其中这部分不需要关注)
pow(q ** 2 * x, (p-1)/2, p) + pow(p ** 2 * x, (q-1)/2, q) == N - phi - 1
加密的代码如下
c = (pow(x, int(br + bi, 2), N) * r ** 2) % N#加密部分
注意加密部分,bi是明文的二进制形式,因此可取0,可取1
当bi为1时有ci=x*ri^2(mod N)
当bi为0时有ci=ri*2(mod N)
很明显是具有不同的表达式,那么可以根据是否可以开方来判断bi的取值,而x是随机数(其实没啥用,因为不影响判断明文是0是1),N是两个大素数相乘,如果得到这两个大素数,那么就很容易破解出,明文,我们知道n和phi,很容易根据关系式得到
p=√((n-phi+1-((n-phi+1)^2-4*n))//2
得到p后,可以将n分解,有限域变为p,然后判断出明文内容,转文本即可
phi =
n =
flag =
p=(n-phi+1-((n-phi+1)^2-4*n).nth_root(2))//2
Fp=Integers(p)
flag_bit=[0 if Fp(f).is_square() else 1 for f in flag]
flag_bit = '0'+''.join(str(i) for i in flag_bit)
flag_hex = hex(int(flag_bit,2))[2:-1]
print(flag_hex.decode('hex'))
rsa_output
共模攻击
EasyRSA
题目给的代码中最重要的一个是
z=Fraction(1,Derivative(arctan(p),p))-Fraction(1,Derivative(arth(q),q))
其实这个就是表示p2+q = z,然后我们知道n,c,简单数学公式推一下就得到p,然后解rsa即可
from gmpy2 import *
from Crypto.Util.number import *
c = 7922547866857761459807491502654216283012776177789511549350672958101810281348402284098310147796549430689253803510994877420135537268549410652654479620858691324110367182025648788407041599943091386227543182157746202947099572389676084392706406084307657000104665696654409155006313203957292885743791715198781974205578654792123191584957665293208390453748369182333152809882312453359706147808198922916762773721726681588977103877454119043744889164529383188077499194932909643918696646876907327364751380953182517883134591810800848971719184808713694342985458103006676013451912221080252735948993692674899399826084848622145815461035
z = 32115748677623209667471622872185275070257924766015020072805267359839059393284316595882933372289732127274076434587519333300142473010344694803885168557548801202495933226215437763329280242113556524498457559562872900811602056944423967403777623306961880757613246328729616643032628964072931272085866928045973799374711846825157781056965164178505232524245809179235607571567174228822561697888645968559343608375331988097157145264357626738141646556353500994924115875748198318036296898604097000938272195903056733565880150540275369239637793975923329598716003350308259321436752579291000355560431542229699759955141152914708362494482
n = 15310745161336895413406690009324766200789179248896951942047235448901612351128459309145825547569298479821101249094161867207686537607047447968708758990950136380924747359052570549594098569970632854351825950729752563502284849263730127586382522703959893392329333760927637353052250274195821469023401443841395096410231843592101426591882573405934188675124326997277775238287928403743324297705151732524641213516306585297722190780088180705070359469719869343939106529204798285957516860774384001892777525916167743272419958572055332232056095979448155082465977781482598371994798871917514767508394730447974770329967681767625495394441
e=65537
p = (iroot(z+2*n,2)[0]+iroot(z-2*n,2)[0])//2
q = n//p
Fai = (p-1)*(q-1)
d = invert(e,Fai)
m = pow(c,d,n)
print(long_to_bytes(m))
rsa
这个题有个hint,e=52361,并给出代码
lag=open("flag","rb").read()
p=getPrime(1024)
q=getPrime(1024)
assert(e<100000)
n=p*q
m=bytes_to_long(flag)
c=pow(m,e,n)
print c,n
print pow(294,e,n)
p=getPrime(1024)
n=p*q
m=bytes_to_long("BJD"*32)
c=pow(m,e,n)
print c,n
发现两组数据共用了q,那么就可以解了
from gmpy2 import *
from Crypto.Util.number import *
n1 = 13508774104460209743306714034546704137247627344981133461801953479736017021401725818808462898375994767375627749494839671944543822403059978073813122441407612530658168942987820256786583006947001711749230193542370570950705530167921702835627122401475251039000775017381633900222474727396823708695063136246115652622259769634591309421761269548260984426148824641285010730983215377509255011298737827621611158032976420011662547854515610597955628898073569684158225678333474543920326532893446849808112837476684390030976472053905069855522297850688026960701186543428139843783907624317274796926248829543413464754127208843070331063037
n2 = 12806210903061368369054309575159360374022344774547459345216907128193957592938071815865954073287532545947370671838372144806539753829484356064919357285623305209600680570975224639214396805124350862772159272362778768036844634760917612708721787320159318432456050806227784435091161119982613987303255995543165395426658059462110056431392517548717447898084915167661172362984251201688639469652283452307712821398857016487590794996544468826705600332208535201443322267298747117528882985955375246424812616478327182399461709978893464093245135530135430007842223389360212803439850867615121148050034887767584693608776323252233254261047
e = 52361
q = gcd(n1,n2)
p = n1//q
Fai = (p-1)*(q-1)
d = invert(e,Fai)
m = pow(c,d,n1)
print(long_to_bytes(m))
base??
base64变表,新的映射关系,遇到挺多次了
import base64
dicts={0: 'J', 1: 'K', 2: 'L', 3: 'M', 4: 'N', 5: 'O', 6: 'x', 7: 'y', 8: 'U', 9: 'V', 10: 'z', 11: 'A', 12: 'B', 13: 'C', 14: 'D', 15: 'E', 16: 'F', 17: 'G', 18: 'H', 19: '7', 20: '8', 21: '9', 22: 'P', 23: 'Q', 24: 'I', 25: 'a', 26: 'b', 27: 'c', 28: 'd', 29: 'e', 30: 'f', 31: 'g', 32: 'h',33: 'i', 34: 'j', 35: 'k', 36: 'l', 37: 'm', 38: 'W', 39: 'X', 40: 'Y', 41: 'Z', 42: '0', 43: '1', 44: '2', 45: '3', 46: '4', 47: '5', 48: '6', 49: 'R', 50: 'S', 51: 'T', 52: 'n', 53: 'o', 54: 'p', 55: 'q', 56: 'r', 57: 's', 58: 't', 59: 'u', 60: 'v', 61: 'w', 62: '+', 63: '/', 64: '='}
base64_list = ['A', 'B', 'C', 'D', 'E', 'F', 'G', 'H', 'I', 'J', 'K', 'L', 'M', 'N', 'O', 'P','Q', 'R', 'S', 'T', 'U', 'V', 'W', 'X', 'Y', 'Z', 'a', 'b', 'c', 'd', 'e', 'f','g', 'h', 'i', 'j', 'k', 'l', 'm', 'n', 'o', 'p', 'q', 'r', 's', 't', 'u', 'v','w', 'x', 'y', 'z', '0', '1', '2', '3', '4', '5', '6', '7', '8', '9', '+', '/']#表可见百度百科
cipher='FlZNfnF6Qol6e9w17WwQQoGYBQCgIkGTa9w3IQKw'
res=''
for i in range(len(cipher)):
for j in range(64):
if(dicts[j]==cipher[i]):
res+=base64_list[j]
flag=base64.b64decode(res)
print(flag)
编码与调制
标准曼彻斯特编码解密即可
Polybius
题目已经告诉我们加密的算法了,但是加密表未知,直接爆破,寻找有意义的语句即可
import itertools
key = []
cipher = "ouauuuoooeeaaiaeauieuooeeiea"
for i in itertools.permutations('aeiou', 5):
key.append(''.join(i))
for each in key:
temp_cipher = ""
result = ""
for temp in cipher:
temp_cipher += str(each.index(temp))
for i in range(0,len(temp_cipher),2):
current_ascii = int(temp_cipher[i])*5+int(temp_cipher[i+1])+97
if current_ascii>ord('i'):
current_ascii+=1
result += chr(current_ascii)
if "flag" in result:
print(each,result)
sign in
16进制转字符串


 浙公网安备 33010602011771号
浙公网安备 33010602011771号