编译安装Kubernetes 1.29 高可用集群(8)--Dashboard和Traefik安装部署
1.部署Dashboard
1.1 在任意k8s-master节点上安装dashboard
# helm repo add kubernetes-dashboard https://kubernetes.github.io/dashboard/
# helm upgrade --install kubernetes-dashboard kubernetes-dashboard/kubernetes-dashboard --create-namespace --namespace kubernetes-dashboard
Release "kubernetes-dashboard" does not exist. Installing it now.
NAME: kubernetes-dashboard
LAST DEPLOYED: Mon Jul 8 16:16:08 2024
NAMESPACE: kubernetes-dashboard
STATUS: deployed
REVISION: 1
TEST SUITE: None
NOTES:
*************************************************************************************************
*** PLEASE BE PATIENT: Kubernetes Dashboard may need a few minutes to get up and become ready ***
*************************************************************************************************
Congratulations! You have just installed Kubernetes Dashboard in your cluster.
To access Dashboard run:
kubectl -n kubernetes-dashboard port-forward svc/kubernetes-dashboard-kong-proxy 8443:443
NOTE: In case port-forward command does not work, make sure that kong service name is correct.
Check the services in Kubernetes Dashboard namespace using:
kubectl -n kubernetes-dashboard get svc
Dashboard will be available at:
https://localhost:84431.2 更改dashboard的svc为NodePort
# kubectl edit svc kubernetes-dashboard-kong-proxy -n kubernetes-dashboard
###第34行
nodePort:
修改为nodePort:30000
###第43行
type: ClusterIP
修改为type: LoadBalancer
# kubectl get serviceAccount,svc,deploy,pod -n kubernetes-dashboard
NAME SECRETS AGE
serviceaccount/default 0 3h2m
serviceaccount/kubernetes-dashboard-api 0 38m
serviceaccount/kubernetes-dashboard-kong 0 38m
serviceaccount/kubernetes-dashboard-metrics-scraper 0 38m
serviceaccount/kubernetes-dashboard-web 0 38m
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubernetes-dashboard-api ClusterIP 10.66.213.106 <none> 8000/TCP 18h
service/kubernetes-dashboard-auth ClusterIP 10.66.242.177 <none> 8000/TCP 18h
service/kubernetes-dashboard-kong-manager NodePort 10.66.97.228 <none> 8002:31851/TCP,8445:32487/TCP 18h
service/kubernetes-dashboard-kong-proxy LoadBalancer 10.66.156.15 <pending> 443:30000/TCP 18h
service/kubernetes-dashboard-metrics-scraper ClusterIP 10.66.179.209 <none> 8000/TCP 18h
service/kubernetes-dashboard-web ClusterIP 10.66.252.176 <none> 8000/TCP 18h
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/kubernetes-dashboard-api 1/1 1 1 38m
deployment.apps/kubernetes-dashboard-auth 1/1 1 1 38m
deployment.apps/kubernetes-dashboard-kong 1/1 1 1 38m
deployment.apps/kubernetes-dashboard-metrics-scraper 1/1 1 1 38m
deployment.apps/kubernetes-dashboard-web 1/1 1 1 38m
NAME READY STATUS RESTARTS AGE
pod/kubernetes-dashboard-api-6dbd5dc685-n6vl2 1/1 Running 0 38m
pod/kubernetes-dashboard-auth-7f697c4d47-5gzlg 1/1 Running 0 38m
pod/kubernetes-dashboard-kong-75bb76dd5f-kz9x5 1/1 Running 0 38m
pod/kubernetes-dashboard-metrics-scraper-555758b9bf-ppxrc 1/1 Running 0 38m
pod/kubernetes-dashboard-web-846f5f49b-5xwgf 1/1 Running 0 38m1.3 创建登录用户并生成token
# kubectl apply -f - <<EOF
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kubernetes-dashboard
EOF
# kubectl apply -f - <<EOF
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kubernetes-dashboard
EOF
获取短期token
# kubectl -n kubernetes-dashboard create token admin-user
创建长期token
# kubectl apply -f - <<EOF
apiVersion: v1
kind: Secret
metadata:
name: admin-user
namespace: kubernetes-dashboard
annotations:
kubernetes.io/service-account.name: "admin-user"
type: kubernetes.io/service-account-token
EOF
查看登录token
# kubectl get secret admin-user -n kubernetes-dashboard -o jsonpath={".data.token"} | base64 -d
或者
# kubectl describe secret admin-user -n kubernetes-dashboard1.4 使用任意k8s-node节点IP访问dashboard
https://192.168.83.221:30000
1.5 删除ServiceAccount和ClusterRoleBinding
kubectl -n kubernetes-dashboard delete serviceaccount admin-user
kubectl -n kubernetes-dashboard delete clusterrolebinding admin-user2.部署Traefik(在任意k8s-master几点上执行)
2.1 创建ClusterRole资源的角色文件
cat > role.yml << EOF
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: traefik-role
rules:
- apiGroups:
- ""
resources:
- services
- endpoints
- secrets
verbs:
- get
- list
- watch
- apiGroups:
- extensions
- networking.k8s.io
resources:
- ingresses
- ingressclasses
verbs:
- get
- list
- watch
- apiGroups:
- extensions
- networking.k8s.io
resources:
- ingresses/status
verbs:
- update
EOF2.2 为traefik创建专用服务帐户
cat > account.yml << EOF
apiVersion: v1
kind: ServiceAccount
metadata:
name: traefik-account
EOF2.3 将traefik的角色与服务账号绑定
cat > role-binding.yml << EOF
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: traefik-role-binding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: traefik-role
subjects:
- kind: ServiceAccount
name: traefik-account
namespace: default
EOF2.4 创建traefik dashboard文件
cat > traefik.yml << EOF
kind: Deployment
apiVersion: apps/v1
metadata:
name: traefik-deployment
labels:
app: traefik
spec:
replicas: 1
selector:
matchLabels:
app: traefik
template:
metadata:
labels:
app: traefik
spec:
serviceAccountName: traefik-account
containers:
- name: traefik
image: traefik:v3.0
args:
- --api.insecure
- --providers.kubernetesingress
ports:
- name: web
containerPort: 80
- name: dashboard
containerPort: 8080
EOF2.5 创建反向代理文件
cat > traefik-services.yml << EOF
apiVersion: v1
kind: Service
metadata:
name: traefik-dashboard-service
spec:
type: LoadBalancer
ports:
- port: 8080
targetPort: dashboard
selector:
app: traefik
---
apiVersion: v1
kind: Service
metadata:
name: traefik-web-service
spec:
type: LoadBalancer
ports:
- targetPort: web
port: 80
selector:
app: traefik
EOF2.6 在k8s集群部署traefik
# kubectl apply -f role.yml \
-f account.yml \
-f role-binding.yml \
-f traefik.yml \
-f traefik-services.yml
clusterrole.rbac.authorization.k8s.io/traefik-role created
serviceaccount/traefik-account created
clusterrolebinding.rbac.authorization.k8s.io/traefik-role-binding created
deployment.apps/traefik-deployment created
service/traefik-dashboard-service created
service/traefik-web-service created2.7 查看部署状况
# kubectl get pod -A -o wide | grep traefik
default traefik-deployment-8478c7684c-kq7ct 1/1 Running 0 25m 172.31.0.59 k8s-node01 <none> <none>
# kubectl get svc -o wide | grep traefik
traefik-dashboard-service LoadBalancer 10.66.125.39 <pending> 8080:31680/TCP 25m app=traefik
traefik-web-service LoadBalancer 10.66.182.2 <pending> 80:30330/TCP 25m app=traefik2.8 修改dashboard-service和web-service访问端口
# kubectl edit svc traefik-dashboard-service
### 修改27行为
- nodePort: 30001
# kubectl edit svc traefik-web-service
### 修改27行为
- nodePort: 30002
# kubectl get svc -o wide | grep traefik
traefik-dashboard-service LoadBalancer 10.66.125.39 <pending> 8080:30001/TCP 25m app=traefik
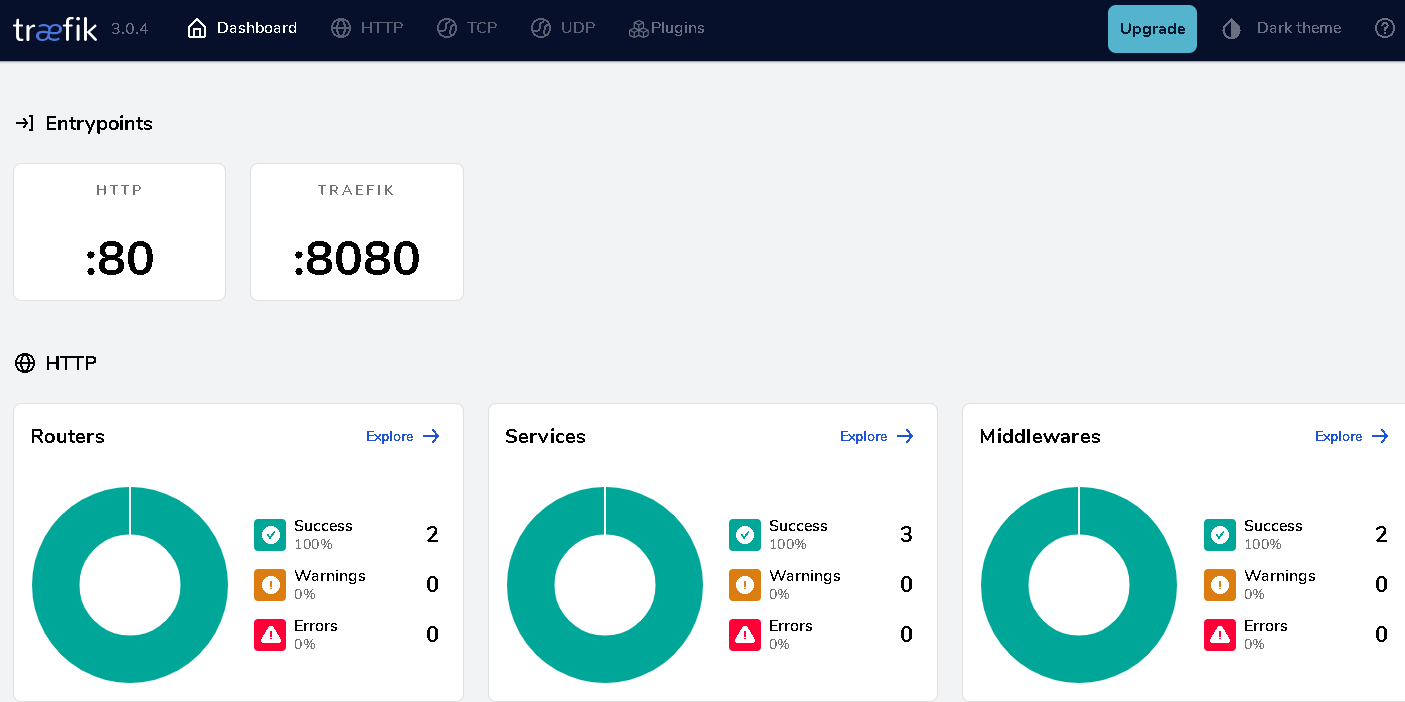
traefik-web-service LoadBalancer 10.66.182.2 <pending> 80:30002/TCP 25m app=traefik2.9.1 使用任意k8s-node节点IP访问traefik dashboard
http://192.168.83.221:30001
2.9.2 创建反向代理测试文件
# cat > whoami.yml << EOF
kind: Deployment
apiVersion: apps/v1
metadata:
name: whoami
labels:
app: whoami
spec:
replicas: 1
selector:
matchLabels:
app: whoami
template:
metadata:
labels:
app: whoami
spec:
containers:
- name: whoami
image: traefik/whoami
ports:
- name: web
containerPort: 80
EOF
# cat > whoami-services.yml << EOF
apiVersion: v1
kind: Service
metadata:
name: whoami
spec:
ports:
- name: web
port: 80
targetPort: web
selector:
app: whoami
EOF
# cat > whoami-ingress.yml << EOF
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: whoami-ingress
spec:
rules:
- http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: whoami
port:
name: web
EOF
# kubectl apply -f whoami.yml \
-f whoami-services.yml \
-f whoami-ingress.yml
deployment.apps/whoami created
service/whoami created
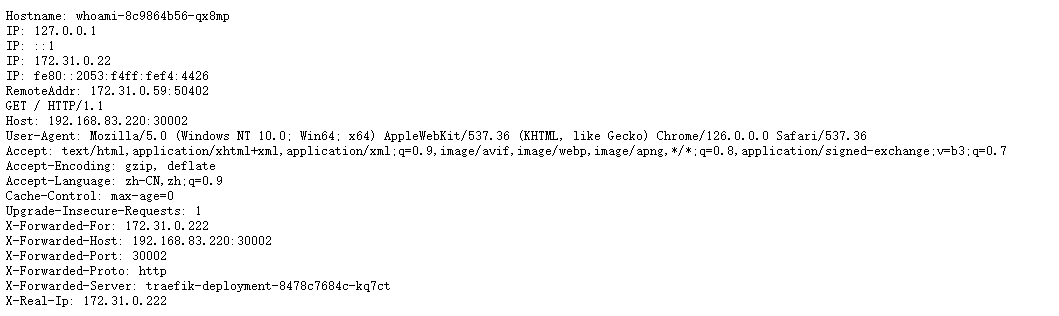
ingress.networking.k8s.io/whoami-ingress createdhttp://{任意k8s-node节点IP}:30002
少壮不努力,老大干IT。
一入运维深似海,从此不见彼岸花。
分类:
容器化技术
标签:
kubernetes



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 被坑几百块钱后,我竟然真的恢复了删除的微信聊天记录!
· 没有Manus邀请码?试试免邀请码的MGX或者开源的OpenManus吧
· 【自荐】一款简洁、开源的在线白板工具 Drawnix
· 园子的第一款AI主题卫衣上架——"HELLO! HOW CAN I ASSIST YOU TODAY
· Docker 太简单,K8s 太复杂?w7panel 让容器管理更轻松!