6.Ingress及Ingress控制器
Service是工作在四层,当使用service时,如何实现HTTPS?每个应用服务器是否配置相同的HTTPS证书?
七层负载均衡,七层调度:
创建共享节点网络命名空间的Pod。
Client --> 外部LB --> 共享命名空间的Pod --> 后端应用Pod
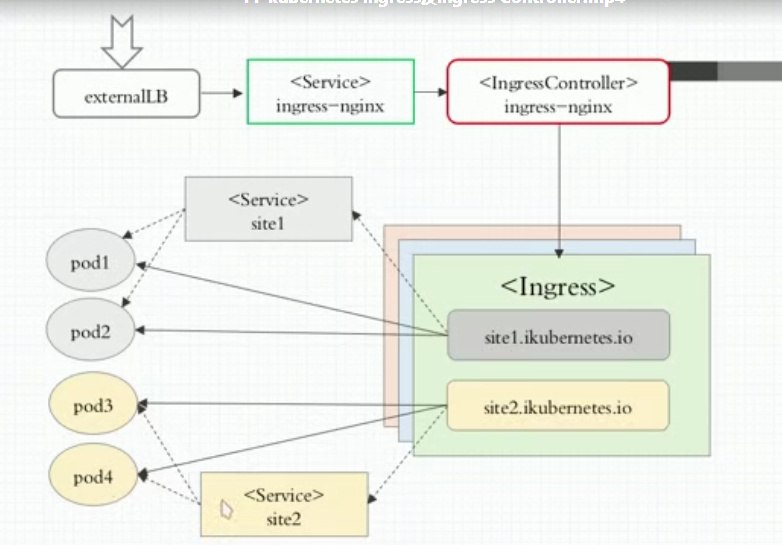
Ingress:一种资源类型。
Ingress Controller七层调度控制器:
独立运行的一组Pod资源,不属于Controller Manager的子组件,属于核心附件之一。
Nginx EnVoy Traefik
安装Ingress controller:
[kubelet@master static]$ kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/master/deploy/static/mandatory.yaml [kubelet@master baremetal]$ ll /tmp/soft/ingress-nginx/ingress-nginx-nginx-0.25.0/deploy/static/provider/baremetal/service-nodeport.yaml [kubelet@master baremetal]$ kubectl apply -f service-nodeport.yaml
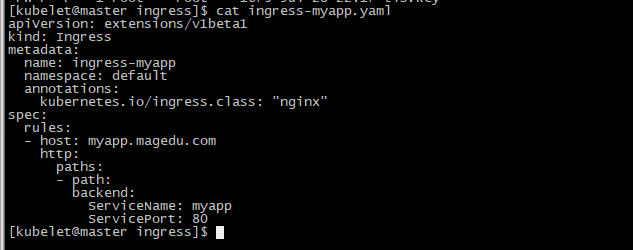
定义ingress的资源清单:
[kubelet@master ~]$ kubectl explain ingress.spec.rules
https:
自签证书:
[root@master ~]# openssl genrsa -out tls.key 2048 [root@master ~]# openssl req -new -x509 -key tls.key -out tls.crt -subj /C=CN/ST=Beijing/L=Beijing/O=DevOps/CN=myapp.magedu.com [kubelet@master ingress]$ kubectl create secret tls myapp-ingress-secret --cert=tls.crt --key=tls.key
[root@Python CA]# openssl genrsa -out server.key 1024
[root@Python CA]# openssl rsa -in server.key -pubout -out server.pem
[root@Python CA]# openssl genrsa -out client.key 1024
[root@Python CA]# openssl rsa -in client.key -pubout -out client.pem
[root@Python CA]# openssl genrsa -out ca.key 1024
[root@Python CA]# openssl req -new -key ca.key -out ca.csr
[root@Python CA]# openssl x509 -req -in ca.csr -signkey ca.key -out ca.crt
[root@Python CA]# openssl req -new -key server.key -out server.csr
[root@Python CA]# openssl x509 -req -CA ca.crt -CAkey ca.key -CAcreateserial -in server.csr -out server.crt
[root@Python CA]# openssl req -new -key client.key -out client.csr
[root@Python CA]# openssl x509 -req -CA ca.crt -CAkey ca.key -CAcreateserial -in client.csr -out client.crt
[root@Python CA]# ls
ca.crt ca.csr ca.key ca.srl client.crt client.csr client.key client.pem server.crt server.csr server.key server.pem






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 从 HTTP 原因短语缺失研究 HTTP/2 和 HTTP/3 的设计差异
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· winform 绘制太阳,地球,月球 运作规律
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 上周热点回顾(3.3-3.9)
· AI 智能体引爆开源社区「GitHub 热点速览」