第八周作业
1、创建私有CA并进行证书申请。
创建CA相关目录和文件
[root@test1 ~]# mkdir /etc/pki/CA/{certs,crl,newcerts,private} -p
[root@test1 ~]# touch /etc/pki/CA/index.txt
[root@test1 ~]# echo 0F > /etc/pki/CA/serial
创建CA私钥,指定私钥长度是2048,权限为600
[root@test1 CA]# (umask 066; openssl genrsa -out private/cakey.pem 2048) Generating RSA private key, 2048 bit long modulus ...............................................................................+++ ...............................................................................................................................+++ e is 65537 (0x10001)
交互式界面使用刚刚创建的私钥给CA颁发自签名证书,指定有效期为10年,证书保存路径为/etc/pki/CA/ 证书名称为cacert.pem
[root@test1 CA]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pem You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:china string is too long, it needs to be less than 2 bytes long Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:jiangsu Locality Name (eg, city) [Default City]:wuxi Organization Name (eg, company) [Default Company Ltd]:mh Organizational Unit Name (eg, section) []:it Common Name (eg, your name or your server's hostname) []:10.0.6.100 Email Address []:
通过命令查看申请的自签名证书详细信息
[root@test1 CA]# openssl x509 -in /etc/pki/CA/cacert.pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
91:1e:ff:c2:75:ca:b8:af
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=jiangsu, L=wuxi, O=mh, OU=it, CN=10.0.6.100
Validity
Not Before: May 9 11:10:01 2022 GMT
Not After : May 6 11:10:01 2032 GMT
Subject: C=CN, ST=jiangsu, L=wuxi, O=mh, OU=it, CN=10.0.6.100
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:bd:c5:9d:23:e9:c5:9c:8f:93:0d:ca:d1:b3:ad:
e3:aa:40:50:0c:ba:25:46:b3:c0:5a:42:4b:70:be:
61:9e:e5:15:18:4d:1f:ef:5c:d2:da:5b:65:b9:93:
c1:3d:06:9d:66:00:d4:19:22:59:f3:f4:21:48:c6:
63:d9:81:25:00:43:02:04:cd:8d:51:cc:48:f3:72:
0f:13:f9:b1:8e:db:c8:60:c6:7b:51:9d:e7:1f:23:
29:56:fd:0e:19:17:67:6e:54:0b:31:13:d4:ea:dd:
c9:e9:25:c6:1c:8d:06:3e:59:b0:b9:8b:3c:94:5c:
30:bf:51:8a:b6:67:6f:da:4f:9c:a4:19:37:10:1b:
4d:06:a3:a4:28:51:d8:9e:58:e5:bf:15:02:4f:e1:
8e:cd:79:30:02:da:02:4e:1b:c6:62:cf:9c:71:cb:
49:3d:ec:89:1f:66:ff:d4:fc:fe:93:7d:32:70:04:
80:06:d0:52:6e:f5:88:60:04:2b:43:55:b9:f7:8a:
6f:2b:bd:55:0b:47:9a:82:7f:4b:cb:82:08:f8:1e:
c4:10:fe:c1:db:61:36:d0:cc:3d:e9:1c:f0:0d:36:
21:eb:77:be:e3:ce:e8:f6:75:d5:c8:3c:e9:9a:39:
e0:a7:a8:d4:ea:d0:52:af:43:9b:a2:2e:4e:5a:ed:
d5:f1
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
FD:7E:85:89:6C:9C:C4:E6:5B:BE:04:E7:68:26:98:8A:3A:91:05:6B
X509v3 Authority Key Identifier:
keyid:FD:7E:85:89:6C:9C:C4:E6:5B:BE:04:E7:68:26:98:8A:3A:91:05:6B
X509v3 Basic Constraints:
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
53:19:17:70:88:94:d7:2b:84:30:e2:a1:ee:7a:31:20:62:21:
1a:50:d7:0c:c0:79:de:17:2e:c1:4d:e9:9f:42:e5:18:5e:77:
c7:39:7e:f5:05:32:ee:ed:cd:a3:d1:00:c8:73:16:f5:af:1e:
85:aa:58:f6:16:96:f6:37:71:63:60:3f:79:83:6c:25:71:fd:
25:dd:8b:af:90:4f:f5:15:bb:5f:f0:4a:cc:ec:4d:07:68:ec:
be:09:f1:f4:2b:5c:6a:5b:37:15:21:ad:23:2f:8b:53:0d:78:
89:8d:8d:36:ed:e4:05:63:13:57:c3:74:10:aa:ab:30:33:08:
ed:9b:b9:0b:ac:b1:a6:82:38:b0:4e:0b:6e:3e:7a:3b:2d:96:
63:b7:62:4a:fb:62:b2:78:10:8f:50:dc:8b:51:87:b1:9c:b1:
78:7a:ef:26:b0:bb:80:46:7b:9d:64:45:9a:68:c5:8a:08:11:
27:c7:48:a0:40:68:74:c1:f3:d9:00:fb:56:6a:a5:7f:12:d3:
41:ec:3e:4a:88:35:f7:6c:40:ec:f8:8a:bf:48:a2:25:a8:cb:
f9:01:c7:ff:fd:2b:fa:7a:d9:6a:0c:5e:c1:a9:0d:e1:54:77:
c5:5c:75:6b:1d:5b:7a:8a:ee:44:3d:f0:29:ed:18:ae:75:8e:
7c:d6:44:76
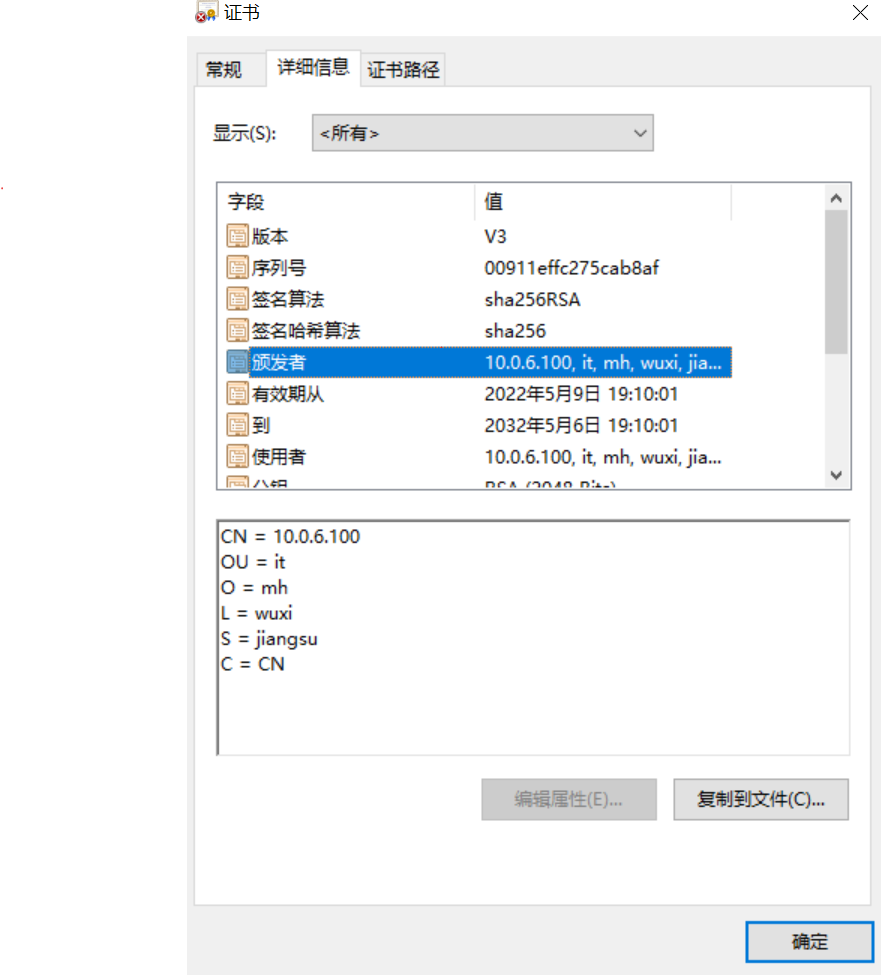
将证书文件拷贝至WINDOWS电脑,修改后缀为crt可以更直观的看到证书颁发的详细信息,自签名证书颁发成功
生成用户私钥 命名为app1.key,有效期700天,保存在/data/app1目录下
[root@test1 ~]# mkdir /data/app1 [root@test1 ~]# (umask 066;openssl genrsa -out /data/app1/app1.key 2048 -days 700) Generating RSA private key, 2048 bit long modulus ......................................................+++ .......+++ e is 65537 (0x10001)
生成证书申请文件需要注意查看“/etc/pki/tls“目录下的openssl.cnf文件,若策略为match,则”countryName “ ”stateOrProvinceName“ ”organizationName“ 三个选项需要和自签名证书保持一致
[root@test1 ~]# openssl req -new -key /data/app1/app1.key -out /data/app1/app1.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:jiangsu Locality Name (eg, city) [Default City]:wuxi Organization Name (eg, company) [Default Company Ltd]:mh Organizational Unit Name (eg, section) []:it Common Name (eg, your name or your server's hostname) []:mingheng.com Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
CA颁发证书
[root@test1 ~]# openssl ca -in /data/app1/app1.csr -out /etc/pki/CA/certs/app1.crt -days 1000
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 15 (0xf)
Validity
Not Before: May 9 11:44:05 2022 GMT
Not After : Feb 2 11:44:05 2025 GMT
Subject:
countryName = CN
stateOrProvinceName = jiangsu
organizationName = mh
organizationalUnitName = it
commonName = mingheng.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
63:E0:74:8B:20:8D:5B:CA:CE:FB:C4:95:04:E7:25:B8:65:CE:25:55
X509v3 Authority Key Identifier:
keyid:FD:7E:85:89:6C:9C:C4:E6:5B:BE:04:E7:68:26:98:8A:3A:91:05:6B
Certificate is to be certified until Feb 2 11:44:05 2025 GMT (1000 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
颁发后查看serial序号变为10
[root@test1 ~]# cat /etc/pki/CA/serial 10
[root@test1 ~]# tree /etc/pki/CA/ /etc/pki/CA/ ├── cacert.pem ├── certs │ └── app1.crt ├── crl ├── index.txt ├── index.txt.attr ├── index.txt.old ├── newcerts │ └── 0F.pem ├── private │ └── cakey.pem ├── serial └── serial.old
2 总结ssh常用参数,用法
ssh -p 连接ssh服务端时跟上端口 ssh -o 后面跟上菜单,比较常用的有”StrictHostKeyChecking=no“ 跟上这个参数,可以跳过首次登陆需要验证指纹的选项 在使用sshpass和scp命令时也可以跟上此命令,避免交互式操作 sshpass -p 跟上密码,避免交互式输入密码,配合scp -o参数使用for循环,可以实现批量拷贝文件至局域网内主机 ssh -L 本地端口转发 ssh -R 远程端口转发 sshfs ip:目录 可以实现挂载远程目录
3 总结sshd服务常用参数
ssh服务器配置文件位于 /etc/ssh/sshd_config
比较常用的参数有:
Port #生产建议修改 ListenAddress ip LoginGraceTime 2m PermitRootLogin yes #默认ubuntu不允许root远程ssh登录 StrictModes yes #检查.ssh/文件的所有者,权限等 MaxAuthTries 6 #pecifies the maximum number of authentication attempts permitted per connection. Once the number of failures reaches half this value, additional failures are logged. The default is 6. MaxSessions 10 #同一个连接最大会话 PubkeyAuthentication yes #基于key验证 PermitEmptyPasswords no #空密码连接 PasswordAuthentication yes #基于用户名和密码连接 GatewayPorts no ClientAliveInterval 10 #单位:秒 ClientAliveCountMax 3 #默认3 UseDNS yes #提高速度可改为no GSSAPIAuthentication yes #提高速度可改为no MaxStartups #未认证连接最大值,默认值10 Banner /path/file #以下可以限制可登录用户的办法: AllowUsers user1 user2 user3 DenyUsers user1 user2 user3 AllowGroups g1 g2 DenyGroups g1 g2
4、搭建dhcp服务,实现ip地址申请分发
安装DHCP服务 [root@ansible ~]# yum install -y dhcp 已加载插件:fastestmirror Repository base is listed more than once in the configuration Loading mirror speeds from cached hostfile docker-ce-stable | 3.5 kB 00:00:00 docker-ce-stable/7/x86_64/primary_db | 76 kB 00:00:00 正在解决依赖关系 --> 正在检查事务 ---> 软件包 dhcp.x86_64.12.4.2.5-82.el7.centos 将被 安装 --> 解决依赖关系完成 依赖关系解决 ============================================================================================================================== Package 架构 版本 源 大小 ============================================================================================================================== 正在安装: dhcp x86_64 12:4.2.5-82.el7.centos base 515 k 事务概要 ============================================================================================================================== 安装 1 软件包 总下载量:515 k 安装大小:1.4 M Downloading packages: Running transaction check Running transaction test Transaction test succeeded Running transaction 正在安装 : 12:dhcp-4.2.5-82.el7.centos.x86_64 1/1 验证中 : 12:dhcp-4.2.5-82.el7.centos.x86_64 1/1 已安装: dhcp.x86_64 12:4.2.5-82.el7.centos 完毕!
制作DHCP文件
[root@ansible ~]# cp /usr/share/doc/dhcp-4.2.5/dhcpd.conf.example /etc/dhcp/dhcpd.conf
修改DHCP文件
配置DNS
# option definitions common to all supported networks...
option domain-name "example.org";
option domain-name-servers 10.0.6.26;
子网配置(next-server和pxelinux.0为制作pxe启动时需要配置,若只作为DHCP服务器不需要)
# DHCP server to understand the network topology.
subnet 10.1.81.0 netmask 255.255.255.0 {
range 10.1.81.20 10.1.81.28;
option routers 10.1.81.254;
next-server 10.1.81.126;
filename "pxelinux.0";
}
配置完成启动DHCP服务
[root@ansible ~]# systemctl start dhcpd
[root@ansible ~]# systemctl status dhcpd
● dhcpd.service - DHCPv4 Server Daemon
Loaded: loaded (/usr/lib/systemd/system/dhcpd.service; disabled; vendor preset: disabled)
Active: active (running) since 一 2022-05-09 20:16:15 CST; 8min ago
Docs: man:dhcpd(8)
man:dhcpd.conf(5)
Main PID: 9149 (dhcpd)
Status: "Dispatching packets..."
Tasks: 1
CGroup: /system.slice/dhcpd.service
└─9149 /usr/sbin/dhcpd -f -cf /etc/dhcp/dhcpd.conf -user dhcpd -group dhcpd --no-pid
5月 09 20:23:04 ansible dhcpd[9149]: DHCPDISCOVER from 00:50:56:a4:65:48 via eth1
5月 09 20:23:04 ansible dhcpd[9149]: DHCPOFFER on 10.0.6.121 to 00:50:56:a4:65:48 via eth1
5月 09 20:23:24 ansible dhcpd[9149]: DHCPDISCOVER from 00:50:56:a4:65:48 via eth1
5月 09 20:23:24 ansible dhcpd[9149]: DHCPOFFER on 10.0.6.121 to 00:50:56:a4:65:48 via eth1
5月 09 20:23:38 ansible dhcpd[9149]: DHCPDISCOVER from 00:50:56:a4:65:48 via eth1
5月 09 20:23:38 ansible dhcpd[9149]: DHCPOFFER on 10.0.6.121 to 00:50:56:a4:65:48 via eth1
5月 09 20:23:51 ansible dhcpd[9149]: DHCPDISCOVER from 00:50:56:a4:65:48 via eth1
5月 09 20:23:51 ansible dhcpd[9149]: DHCPOFFER on 10.0.6.121 to 00:50:56:a4:65:48 via eth1
5月 09 20:24:07 ansible dhcpd[9149]: DHCPDISCOVER from 00:50:56:a4:65:48 via eth1
5月 09 20:24:07 ansible dhcpd[9149]: DHCPOFFER on 10.0.6.121 to 00:50:56:a4:65:48 via eth1
在客户端使用命令测试能否正常获取IP
[root@test2 ~]# dhclient -s 10.0.6.25
[root@test2 ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:a4:0f:ac brd ff:ff:ff:ff:ff:ff
inet 10.0.6.101/24 brd 10.0.6.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet 10.0.6.123/24 brd 10.0.6.255 scope global secondary dynamic eth0
valid_lft 359998sec preferred_lft 359998sec
inet6 fe80::250:56ff:fea4:fac/64 scope link
valid_lft forever preferred_lft forever



 浙公网安备 33010602011771号
浙公网安备 33010602011771号