oracle 03-10 审计
Implementing Oracle Database Auditing 实现Oracle数据库审计
Objectives
After completing this lesson, you should be able to:
• Describe DBA responsibilities for security and auditing
• Enable unified auditing
• Create unified audit policies
• Maintain the audit trail
目标
完成本课程后,您应该能够:
•描述DBA对安全和审计的责任
•启用统一审核
•创建统一的审核策略
•保持审计跟踪
Database Security
A secure system ensures the confidentiality of the data that it contains. There are several aspects of security:
• Restricting access to data and services
• Authenticating users
• Monitoring for suspicious activity
数据库安全
一个安全的系统确保它所包含的数据的机密性。安全有几个方面:
•限制访问数据和服务
•认证用户
•监测可疑活动
Monitoring for Compliance
• Monitoring or auditing must be an integral part of your security procedures.
• Review the following:
– Mandatory auditing
– Standard database auditing
– Value-based auditing
– Fine-grained auditing (FGA)
合规性监测
•监控或审计必须是您安全程序的组成部分。
•审查以下内容:
–强制性审计
–标准数据库审计
–基于价值的审计
–细粒度审计(FGA)
Types of Activities to be Audited
You can audit the following types of activities:
• User accounts, roles, and privileges
• Object actions
• Application context values
• Oracle Data Pump
• Oracle Database Real Application Security
• Oracle Database Vault
• Oracle Label Security
• Oracle Recovery Manager
• Oracle SQL*Loader direct path events
待审计活动的类型
您可以审核以下类型的活动:
•用户帐户、角色和权限
•目标动作
•应用程序上下文值
•Oracle数据泵
•Oracle数据库真实应用程序安全
•Oracle数据库保险库
•Oracle标签安全
•Oracle恢复管理器
•Oracle SQL*加载程序直接路径事件
Mandatorily Audited Activities
The following activities are audited:
• CREATE/ALTER/DROP AUDIT POLICY
• AUDIT/NOAUDIT
• EXECUTE of:
– DBMS_FGA
– DBMS_AUDIT_MGMT
• ALTER TABLE against AUDSYS audit trail table
• Top-level statements by administrative users (SYS,
SYSDBA, SYSOPER, SYSASM, SYSBACKUP, SYSDG, and SYSKM) until the database opens
强制性审计活动
审计下列活动:
•创建/更改/删除审核策略
•审计/无审计
•执行:
–数据库管理系统
–数据库管理系统审计管理
•根据AUDSYS审计跟踪表修改表
•管理用户的顶级声明(SYS,
SYSDBA、SYSOPER、SYSASM、SYSBACKUP、SYSDG和SYSKM),直到数据库打开
Understanding Auditing Implementation
• Mixed mode auditing is the default when a new Oracle
Database 12c database is created.
• Mixed mode auditing enables the use of:
– Pre–Oracle Database 12c auditing features
– Unified auditing features of Oracle Database 12c
• The recommendation from Oracle is to migrate to unified auditing.
• Query V$OPTION to determine if the database has been migrated to unified auditing:
SELECT value FROM v$option WHERE parameter = 'Unified Auditing' 打开统一审计
了解审计实施
•当新的Oracle
数据库12c数据库已创建。
•混合模式审计允许使用:
–预Oracle数据库12c审计功能
–Oracle数据库12c的统一审计功能
•Oracle的建议是迁移到统一审计。
•查询V$选项以确定数据库是否已迁移到统一审核:
SELECT value FROM v$option
WHERE parameter = 'Unified Auditing'
Administering the Roles Required for Auditing
A user must be granted one of the following roles to perform auditing:
• AUDIT_ADMIN enables the user to:
– Create unified and fine-grained audit policies
– Execute the AUDIT and NOAUDIT SQL statements
– View audit data
– Manage the audit trail (table in the AUDSYS schema)
• AUDIT_VIEWER enables the user to:
– View and analyze audit data
管理审核所需的角色
必须授予用户以下角色之一才能执行审核:
•AUDIT_ADMIN允许用户:
–创建统一的细粒度审计策略
–执行AUDIT和NOAUDIT SQL语句
–查看审核数据
–管理审计跟踪(AUDSYS模式中的表)
•AUDIT_查看器允许用户:
–查看和分析审计数据
Database Auditing: Overview 数据库审核:概述
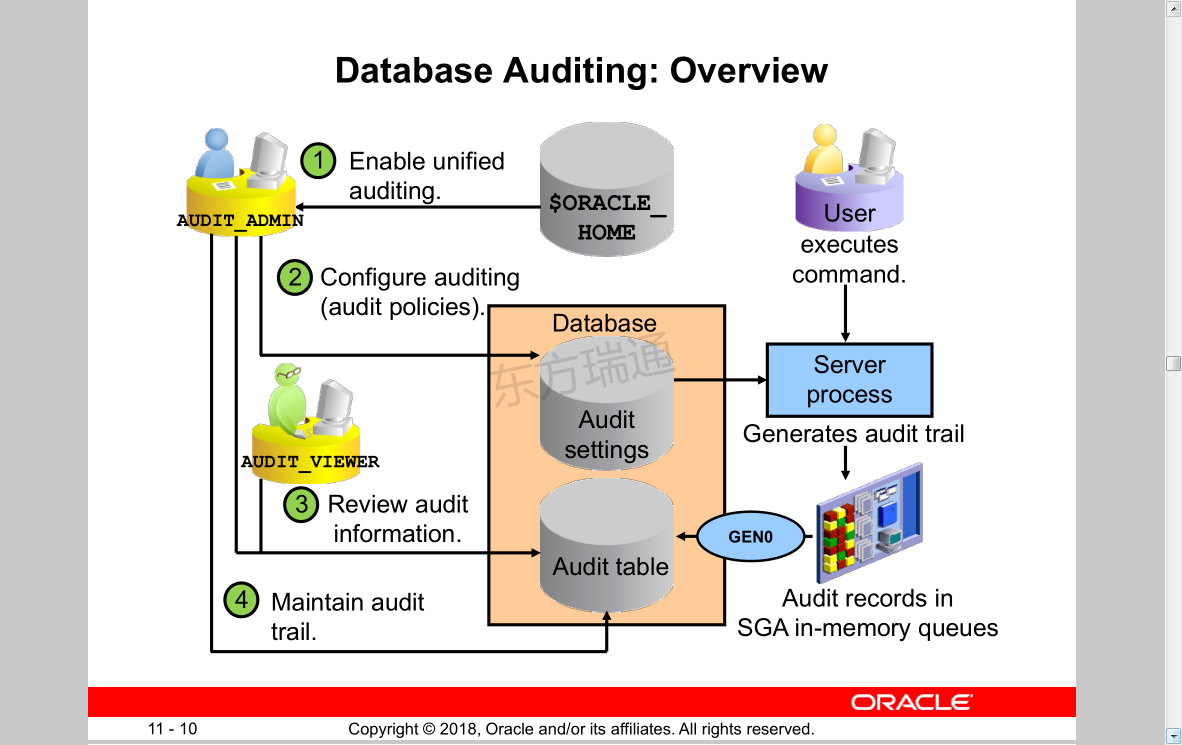
Understanding the Audit Architecture 了解审计架构

Enabling Unified Auditing
1. In SQL*Plus, shut down the database instance:
SQL> SHUTDOWN IMMEDIATE
2. Shut down the listener:
$ lsnrctl stop
3. At the operating system prompt, enable the unified auditing
executable:
$ cd $ORACLE_HOME/rdbms/lib
$ make –f ins_rdbms.mk uniaud_on ioracle ORACLE_HOME=$ORACLE_HOME
4. Restart the listener:
$ lsnrctl start
5. In SQL*Plus, restart the database instance:
SQL> STARTUP
启用统一审核
1、在SQL*Plus中,关闭数据库实例:
SQL>立即关闭
2、关闭侦听器:
$lsnrctl停止
3、在操作系统提示下,启用统一审核
可执行文件:
$cd$ORACLE_主页/rdbms/lib
$make-f英寸_关系数据库管理系统.mkuniaud_on ioracle ORACLE_HOME=$ORACLE_HOME
4、重新启动侦听器:
$lsnrctl开始
5个。在SQL*Plus中,重新启动数据库实例:
SQL>启动
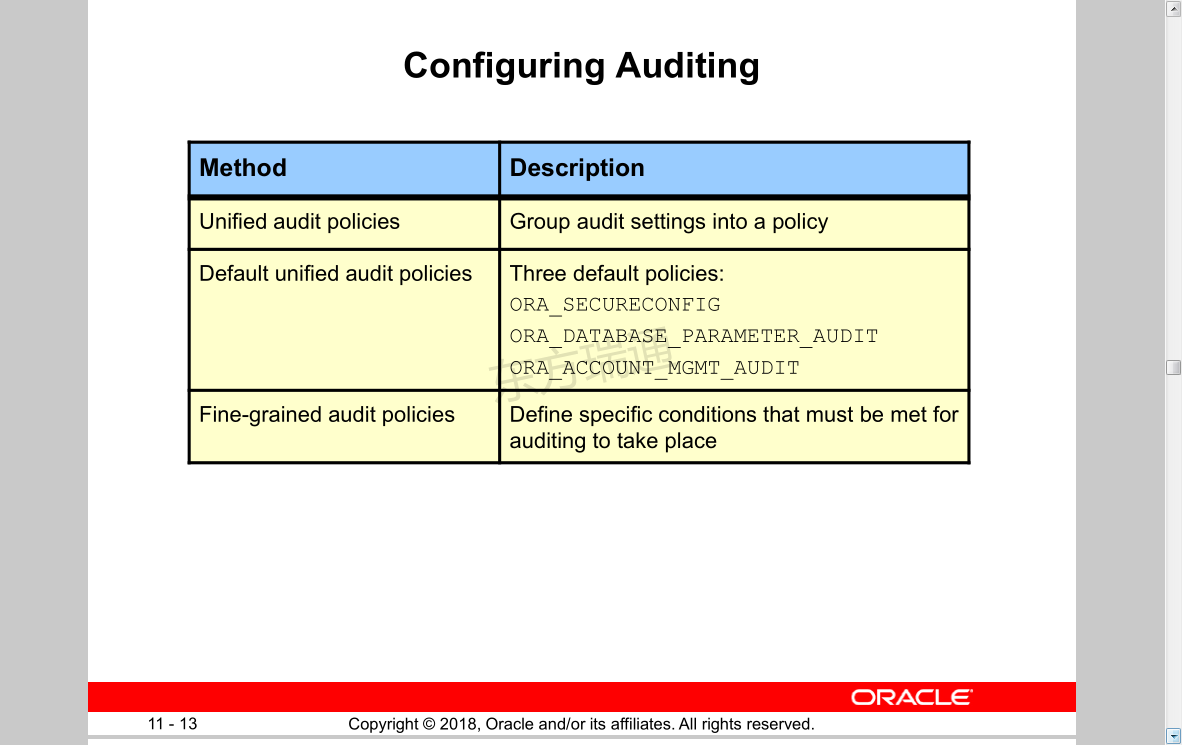
Configuring Auditing
Method Description
Unified audit policies Group audit settings into a policy
Default unified audit policies Three default policies:
ORA_SECURECONFIG
ORA_DATABASE_PARAMETER_AUDIT
ORA_ACCOUNT_MGMT_AUDIT
Fine-grained audit policies Define specific conditions that must be met for auditing to take place
配置审核
方法描述
统一审核策略将审核设置分组到策略中
默认统一审核策略三个默认策略:
安全配置
数据库参数审计
账户管理审计
细粒度的审计策略定义了进行审计必须满足的特定条件
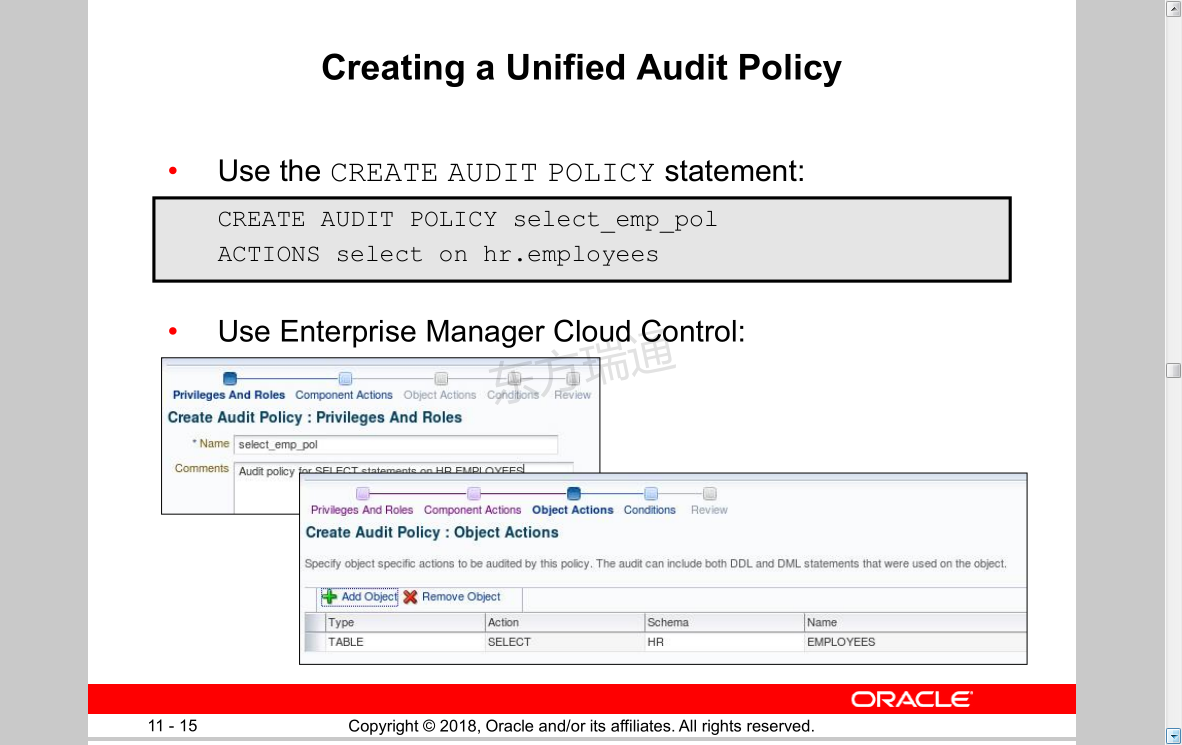
Creating a Unified Audit Policy 创建统一的审核策略
• Use the CREATE AUDIT POLICY statement:
CREATE AUDIT POLICY select_emp_pol
ACTIONS select on hr.employees
• Use Enterprise Manager Cloud Control:
•使用创建审核策略声明:
•使用Enterprise Manager云控制:
Creating an Audit Policy:
System-Wide Audit Options
• System privileges:
CREATE AUDIT POLICY audit_syspriv_pol1
PRIVILEGES SELECT ANY TABLE, CREATE LIBRARY
• Actions:
CREATE AUDIT POLICY audit_actions_pol2
ACTIONS AUDIT, ALTER TRIGGER
• Roles:
CREATE AUDIT POLICY audit_role_pol3
ROLES mgr_role
• System privileges, actions, and roles:
CREATE AUDIT POLICY audit_mixed_pol4
PRIVILEGES DROP ANY TABLE
ACTIONS CREATE TABLE, DROP TABLE, TRUNCATE TABLE
ROLES emp_role
创建审核策略:
全系统审计选项
•系统权限:
•行动:
•角色:
•系统特权、操作和角色:
Creating an Audit Policy:
Object-Specific Actions
Create audit policies based on object-specific options.
CREATE AUDIT POLICY audit_objpriv_pol5 ACTIONS SELECT, UPDATE, LOCK ON hr.employees
CREATE AUDIT POLICY audit_objpriv_pol6 ACTIONS ALL 不建议打开所有表的审计功能
CREATE AUDIT POLICY audit_objpriv_pol7 ACTIONS EXECUTE, GRANT ON hr.raise_salary_proc
创建审核策略:
特定于对象的操作
基于特定于对象的选项创建审核策略。
Creating an Audit Policy: Specifying Conditions
• Condition and evaluation PER SESSION
• Condition and evaluation PER STATEMENT
• Condition and evaluation PER INSTANCE
创建审核策略:指定条件
•每节课的条件和评估
•每个报表的条件和评估
•每个实例的条件和评估
CREATE AUDIT POLICY audit_mixed_pol5
ACTIONS RENAME ON hr.employees,ALTER ON hr.jobs,
WHEN 'SYS_CONTEXT (''USERENV'', ''SESSION_USER'')=''JIM'''
EVALUATE PER SESSION
CREATE AUDIT POLICY audit_objpriv_pol6
ACTIONS ALTER ON OE.ORDERS
WHEN 'SYS_CONTEXT(''USERENV'',''CLIENT_IDENTIFIER'')=''OE'''
EVALUATE PER STATEMENT
CREATE AUDIT POLICY audit_objpriv_pol7
ROLES dba
WHEN SYS_CONTEXT(''USERENV'',''INSTANCE_NAME'')=''sales'''
EVALUATE PER INSTANCE
Enabling and Disabling Audit Policies
Enable audit policies:
• Apply to all users.
SQL> AUDIT POLICY audit_syspriv_pol1;
• Apply only to some users.
SQL> AUDIT POLICY audit_pol2 BY scott, oe;
SQL> AUDIT POLICY audit_pol3 BY sys;
• Exclude some users.
SQL> AUDIT POLICY audit_pol4 EXCEPT jim, george;
• Audit the recording based on failed or succeeded actions.
SQL> AUDIT POLICY audit_syspriv_pol1 WHENEVER SUCCESSFUL ;
SQL> AUDIT POLICY audit_objpriv_pol2 WHENEVER NOT SUCCESSFUL ;
SQL> AUDIT POLICY auditpol5 BY joe WHENEVER SUCCESSFUL ;
Disable audit policies by using the NOAUDIT command.
启用和禁用审核策略
启用审核策略:
•适用于所有用户。
•仅适用于部分用户。
•排除一些用户。
•根据失败或成功的操作审核记录。
使用NOAUDIT命令禁用审核策略。
SQL>审计策略审计;
SQL>审计政策审计2,由scott,oe编写;
系统审计策略审计;
除jim,george外的审计政策审计;
SQL>AUDIT POLICY AUDIT_syspriv_pol1只要成功;
SQL>AUDIT POLICY AUDIT_objpriv_pol2,如果不成功;
成功时由joe审核策略auditpol5;
Altering a Unified Audit Policy
• Use the ALTER AUDIT POLICY statement:
ALTER AUDIT POLICY select_emp_pol
ADD ACTIONS select on hr.job_history
• Use Enterprise Manager Cloud Control:
更改统一审核策略
•使用ALTER AUDIT POLICY语句:
更改审核策略选择
添加操作选择打开人力资源工作历史
•使用Enterprise Manager云控制:
Viewing Audit Policy Information
SQL> SELECT policy_name, audit_option, condition_eval_opt
2 FROM audit_unified_policies;
POLICY_NAME AUDIT_OPTION CONDITION_EVAL_OPT
-------------------- ---------------- ----------------
POL1 DELETE INSTANCE
POL2 TRUNCATE TABLE NONE
POL3 RENAME SESSION
POL4 ALL ACTIONS STATEMENT
SQL> SELECT policy_name, enabled_opt, user_name, success, failure
2 FROM audit_unified_enabled_policies;
POLICY_NAME ENABLED_ USER_NAME SUC FAI
-------------------- -------- ---------- --- ---
POL3 BY PM NO YES
POL2 EXCEPT SYSTEM NO YES
POL4 BY SYS YES YES
POL6 BY ALL USERS YES NO
查看审核策略信息
SQL>选择策略名称、审核选项、条件评估选项
2来自审计统一政策;
策略名称审核选项条件评估选项
-------------------- ---------------- ----------------
POL1删除实例
POL2截断表无
POL3重命名会话
POL4所有行动声明
SQL>选择策略名称,启用选项,用户名,成功,失败
(二)来自统一的审计政策;
策略名称已启用用户名称SUC FAI
-------------------- -------- ---------- --- ---
下午POL3否是
POL2系统除外否是
POL4 BY SYS是的
所有用户提供POL6是否
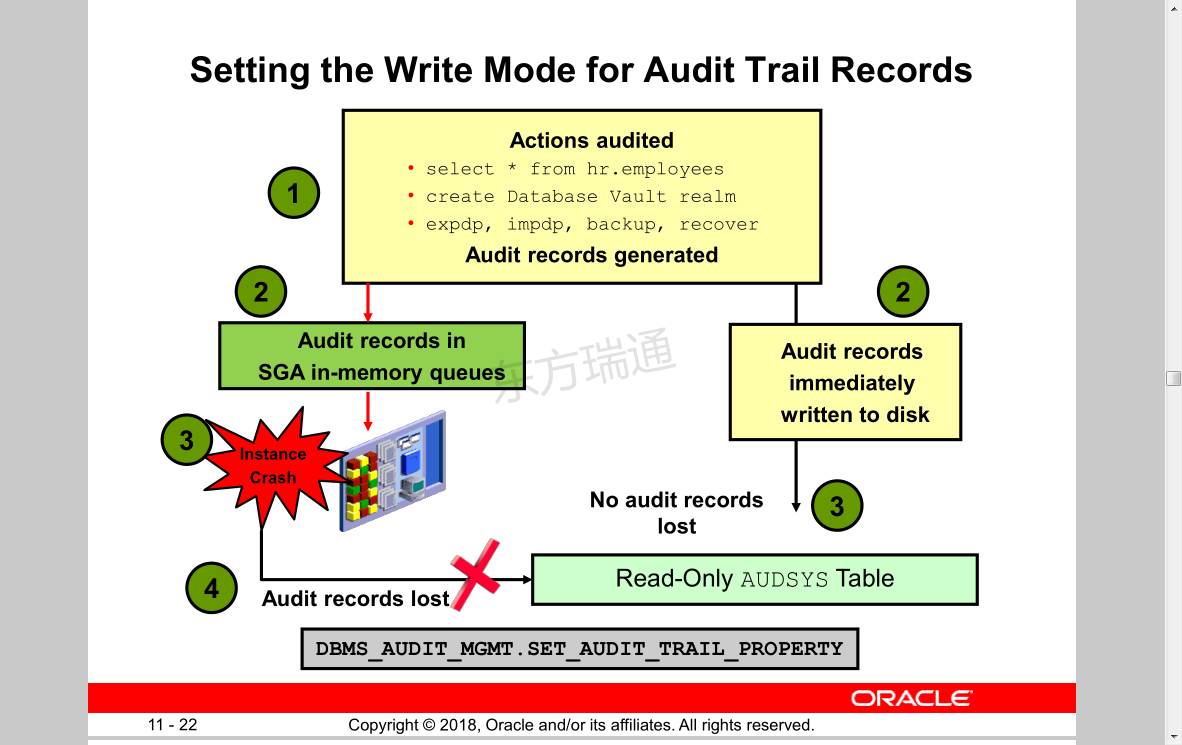
Setting the Write Mode for Audit Trail Records
Actions audited
• select * from hr.employees
• create Database Vault realm
• expdp, impdp, backup, recover
Audit records generated
Read-Only AUDSYS Table
2
4
Audit records in
SGA in-memory queues
Instance
Crash
1
Audit records lost
3
Audit records
immediately
written to disk
No audit records
lost
2
3
DBMS_AUDIT_MGMT.SET_AUDIT_TRAIL_PROPERTY
设置审核跟踪记录的写入模式
审计的行动
•从*中选择人力资源员工
•创建数据库保险库领域
•expdp、impdp、备份、恢复
生成的审核记录
只读AUDSYS表
2个
4个
审计记录
SGA内存队列
实例
撞车
1个
审计记录丢失
三
审计记录
立即
写入磁盘
无审计记录
迷路的
2个
三
数据库管理系统审计_管理集审计跟踪属性
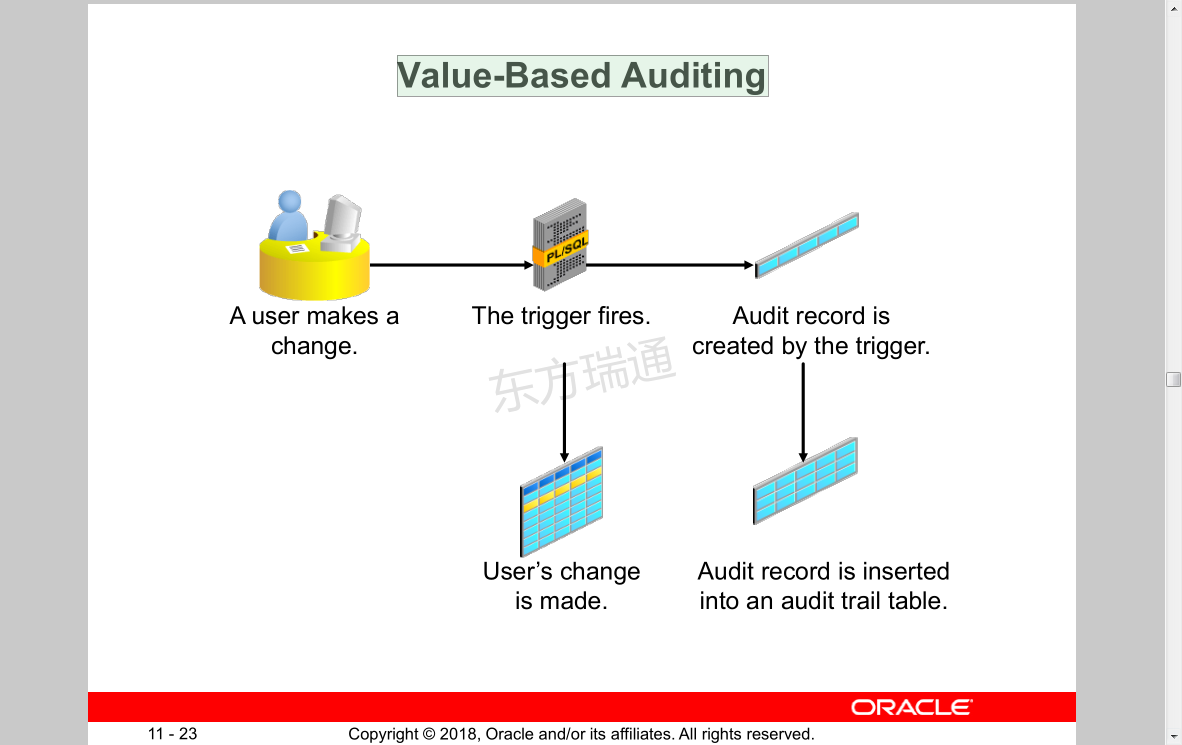
Value-Based Auditing 价值导向审计
The trigger fires.触发器
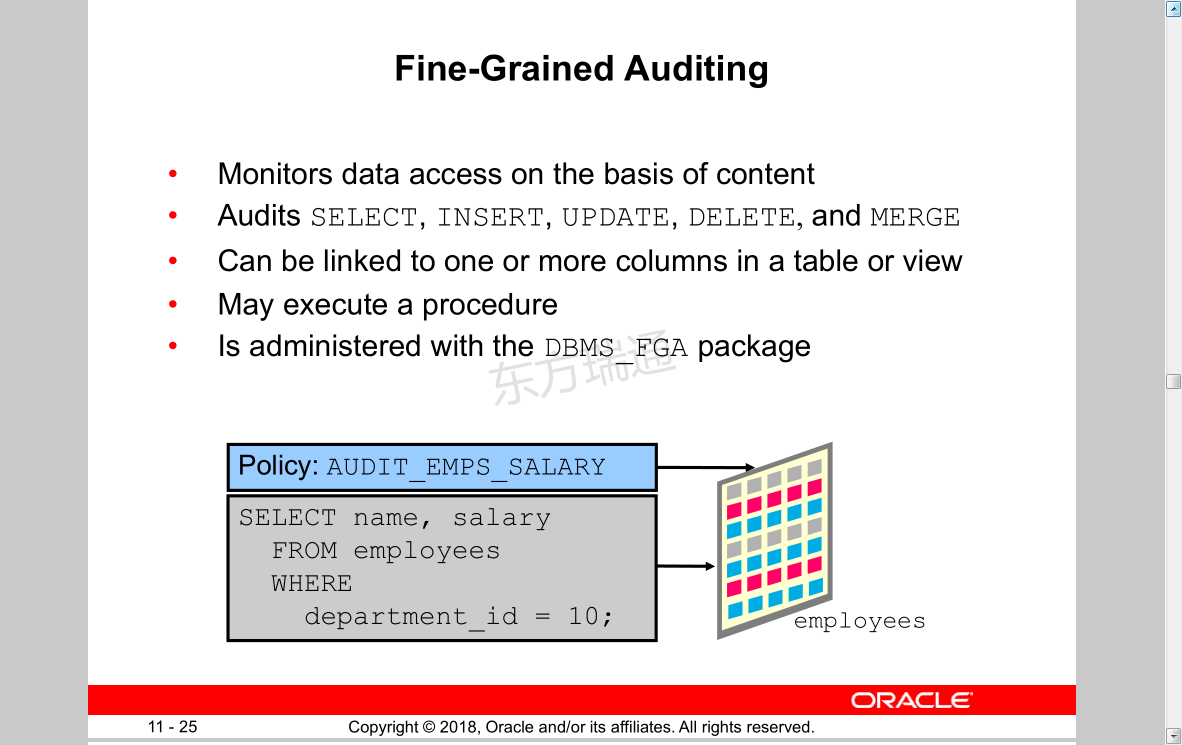
Fine-Grained Auditing
• Monitors data access on the basis of content
• Audits SELECT, INSERT, UPDATE, DELETE, and MERGE
• Can be linked to one or more columns in a table or view
• May execute a procedure
• Is administered with the DBMS_FGA package
employees
Policy: AUDIT_EMPS_SALARY
SELECT name, salary
FROM employees
WHERE
department_id = 10;
细粒度审计
•根据内容监控数据访问
•审核选择、插入、更新、删除和合并
•可以链接到表或视图中的一个或多个列
•可以执行程序
•与DBMS_FGA包一起管理
员工
政策:审计薪酬
选择姓名、薪资
来自员工
哪里
部门id=10;
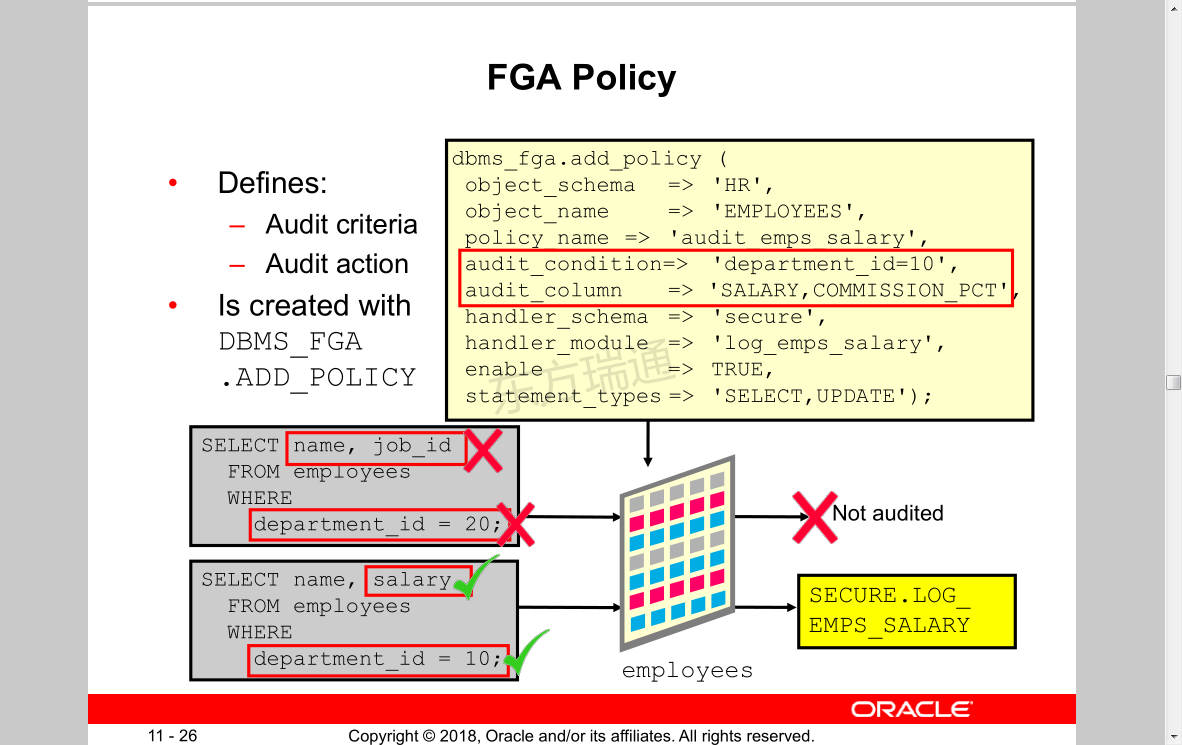
FGA Policy
• Defines:
– Audit criteria
– Audit action
• Is created with
DBMS_FGA
.ADD_POLICY
FGA政策
•定义:
–审计标准
–审计行动
•是用
数据库管理系统
.添加策略
将下图红框中的department_id=10限定命令改成department_id=null 即可对所有部门进行审计
handler_module 可对满足事件的条目进行处理,不如发送邮件等
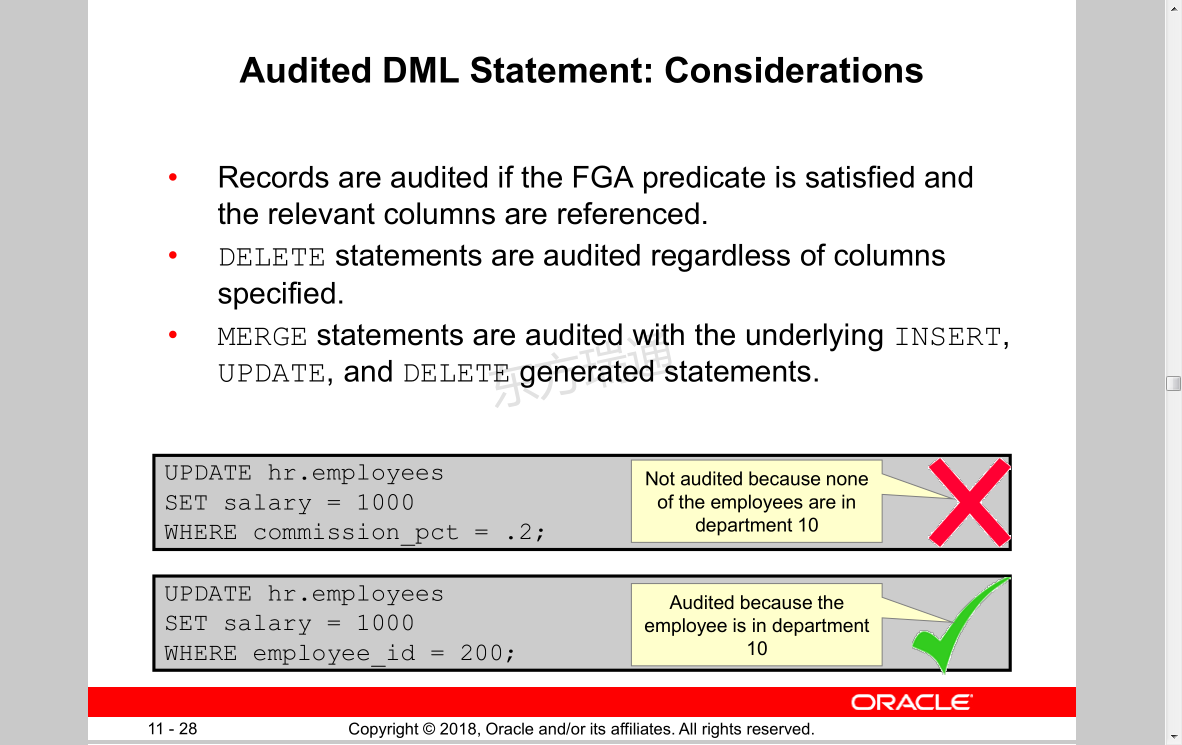
Audited DML Statement: Considerations
• Records are audited if the FGA predicate is satisfied and
the relevant columns are referenced.
• DELETE statements are audited regardless of columns
specified.
• MERGE statements are audited with the underlying INSERT,
UPDATE, and DELETE generated statements.
UPDATE hr.employees
SET salary = 1000
WHERE commission_pct = .2;
UPDATE hr.employees
SET salary = 1000
WHERE employee_id = 200;
Not audited because none
of the employees are in
department 10
Audited because the
employee is in department
经审计的DML报表:注意事项
•如果满足FGA谓词并
相关列被引用。
•不管列是什么,删除语句都会被审计
明确规定。
•合并报表通过底层插入进行审核,
更新和删除生成的语句。
更新人力资源员工
设定薪资=1000
其中佣金=0.2;
更新人力资源员工
设定薪资=1000
其中雇员id=200;
未审核,因为没有
员工的
部门10
因为
员工在部门
示例
SQL> shit immediate; 关闭数据库
SQL> exit
oracle@yf ~]$ lsnrctl stop 关闭监听
[oracle@yf ~]$ ps -ef|grep smon 查看后台数据库进程
oracle 64265 3426 0 21:49 pts/0 00:00:00 grep --color=auto smon
[oracle@yf ~]$ ps -ef|grep tns 查看监听进程
root 19 2 0 6月21 ? 00:00:00 [netns]
oracle 64350 3426 0 21:49 pts/0 00:00:00 grep --color=auto tns
[oracle@yf ~]$ cd $ORACLE_HOME/rdbms/lib
[oracle@yf lib]$ pwd
/u01/app/oracle/product/18c/rdbms/lib
[oracle@yf lib]$ make -f ins_rdbms.mk uniaud_on ioracle 打开数据库通用审计
[oracle@yf lib]$ lsnrctl start 重启监听
[oracle@yf lib]$ sqlplus / as sysdba
SQL> startup 重启数据库
SQL> SELECT value FROM v$option WHERE parameter = 'Unified Auditing'; 查看统一审计是否打开
VALUE
----------------------------------------------------------------
TRUE 至此说明统一审计已经打开
SQL> create user audmgr identified by oracle_4U default tablespace sysaux temporary tablespace temp; 创建审计超级用户 audmgr 权限identified 密码oracle_4U 默认表空间sysaux 临时表空间temp
User created.
SQL> conn / as sysdba
Connected.
SQL> grant connect to audmgr; 给用户授权
SQL> grant audit_admin to audmgr; 给用户授权
SQL> conn audmgr/oracle_4U 新用户登陆成功
Connected.
SQL> create user audvwr identified by oracle_4U default tablespace sysaux temporary tablespace temp; 创建审计查询用户 audvwr
登陆audmgr用户
SQL> ,object_name from audit_unified_policies;
SQL> l (查看上一条sql命令)
1* select audit_option,audit_option_type,object_schema ,object_name from audit_unified_policies
SQL> create audit policy jobs_audit_upd actions update on hr.jobs; 创建策略名jobs_audit_upd 行为是actions update on hr.jobs 意义:当对hr.jobs表进行修改时存放审计条件
Audit policy created.
SQL> select audit_option,audit_option_type,object_schema ,object_name from audit_unified_policies where policy_name='JOBS_AUDIT_UPD'; 在数据字典audit_unified_policies中查看policy_name的审计条件
AUDIT_OPTION
--------------------------------------------------------------------------------
AUDIT_OPTION_TYPE
------------------
OBJECT_SCHEMA
--------------------------------------------------------------------------------
OBJECT_NAME
--------------------------------------------------------------------------------
UPDATE 设计条件
OBJECT ACTION
HR
JOBS
SQL> audit policy JOBS_AUDIT_UPD; 打开JOBS_AUDIT_UPD审计策略
Audit succeeded.
SQL> select policy_name,enabled_opt,user_name,success,failure from audit_unified_enabled_policies; 查看设计策略是否打开
POLICY_NAME
--------------------------------------------------------------------------------
ENABLED
-------
USER_NAME
--------------------------------------------------------------------------------
SUC FAI
--- ---
ORA_SECURECONFIG
BY
ALL USERS
YES YES
POLICY_NAME
--------------------------------------------------------------------------------
ENABLED
-------
USER_NAME
--------------------------------------------------------------------------------
SUC FAI
--- ---
ORA_LOGON_FAILURES
BY
ALL USERS
NO YES
POLICY_NAME
--------------------------------------------------------------------------------
ENABLED
-------
USER_NAME
--------------------------------------------------------------------------------
SUC FAI
--- ---
JOBS_AUDIT_UPD 新建的策略名
BY
ALL USERS
YES YES
另起窗口登陆hr用户
SQL> desc hr.jobs 查看表结构命令
Name Null? Type
----------------------------------------- -------- ----------------------------
JOB_ID NOT NULL VARCHAR2(10)
JOB_TITLE NOT NULL VARCHAR2(35)
MIN_SALARY NUMBER(6)
MAX_SALARY NUMBER(6)
SQL> select * from hr.jobs where job_title='President';
JOB_ID JOB_TITLE MIN_SALARY MAX_SALARY
---------- ----------------------------------- ---------- ----------
AD_PRES President 20080 40000
SQL> update hr.jobs set max_salary=50000 where job_id='AD_PRES'; 修改了JOB_ID为AD_PRES的最大工资
1 row updated.
用sysdba查看审计记录
SQL> select unified_audit_policies,action_name,object_schema,object_name from unified_audit_trail where dbusername='HR';
UNIFIED_AUDIT_POLICIES
--------------------------------------------------------------------------------
ACTION_NAME
----------------------------------------------------------------
OBJECT_SCHEMA
--------------------------------------------------------------------------------
OBJECT_NAME
--------------------------------------------------------------------------------
JOBS_AUDIT_UPD 上面hr用户做的update记录在这里出现了
UPDATE
HR
JOBS
UNIFIED_AUDIT_POLICIES
--------------------------------------------------------------------------------
ACTION_NAME
----------------------------------------------------------------
OBJECT_SCHEMA
--------------------------------------------------------------------------------
OBJECT_NAME
--------------------------------------------------------------------------------
ORA_LOGON_FAILURES
LOGON
UNIFIED_AUDIT_POLICIES
--------------------------------------------------------------------------------
ACTION_NAME
----------------------------------------------------------------
OBJECT_SCHEMA
--------------------------------------------------------------------------------
OBJECT_NAME
--------------------------------------------------------------------------------
ORA_SECURECONFIG
CREATE DATABASE LINK
HR
DB_LINK2
FGA Guidelines
• To audit all rows, use a null audit condition.
• To audit all columns, use a null audit column.
• Policy names must be unique.
• The audited table or view must already exist when you create the policy.
• If the audit condition syntax is invalid, an ORA-28112 error is raised when the audited object is accessed.
• If the audited column does not exist in the table, no rows are audited.
• If the event handler does not exist, no error is returned and the audit record is still created.
FGA指南
•要审核所有行,请使用空审核条件。
•要审核所有列,请使用空审核列。
•策略名称必须唯一。
•创建策略时,已审核的表或视图必须已存在。
•如果审计条件语法无效,则在访问被审计对象时会引发ORA-28112错误。
•如果表中不存在已审核列,则不审核任何行。
•如果事件处理程序不存在,则不会返回错误,并且仍会创建审核记录。
Archiving and Purging the Audit Trail
• Periodically archive and purge the audit trail to prevent it from growing too large.
• Create an archive by:
– Copying audit trail records to a database table
– Using Oracle Audit Vault
• Purge the audit trail by:
– Creating and scheduling a purge job to run at a specified time by using the DBMS_AUDIT_MGMT.CREATE_PURGE_JOB
PL/SQL procedure
– Manually by using the
DBMS_AUDIT_MGMT.CLEAN_AUDIT_TRAIL PL/SQL procedure
存档和清除审核跟踪
•定期存档和清除审计跟踪,以防止其变得过大。
•通过以下方式创建存档:
–将审计跟踪记录复制到数据库表
–使用Oracle Audit Vault
•通过以下方式清除审计跟踪:
–使用DBMS_AUDIT创建并调度要在指定时间运行的清除作业_管理创建清除作业
PL/SQL过程
–使用
数据库管理系统审计_清洁审计跟踪管理PL/SQL过程
Purging Audit Trail Records
• Schedule an automatic purge job:
• Manually purge the audit records:
DBMS_AUDIT_MGMT.CLEAN_AUDIT_TRAIL(
AUDIT_TRAIL_TYPE => DBMS_AUDIT_MGMT.AUDIT_TRAIL_UNIFIED )
DBMS_AUDIT_MGMT.CREATE_PURGE_JOB
(AUDIT_TRAIL_TYPE=> DBMS_AUDIT_MGMT.AUDIT_TRAIL_UNIFIED,
AUDIT_TRAIL_PURGE_INTERVAL => 12,
AUDIT_TRAIL_PURGE_NAME => 'Audit_Trail_PJ',
USE_LAST_ARCH_TIMESTAMP => TRUE,
CONTAINER => DBMS_AUDIT_MGMT.CONTAINER_CURRENT);
清除审核跟踪记录
•安排自动清除作业:
•手动清除审核记录:
数据库管理系统审计_清洁审计跟踪管理(
AUDIT_TRAIL_TYPE=>数据库管理系统审计_统一审计追踪管理)
数据库管理系统审计_管理创建清除作业
(AUDIT_TRAIL_TYPE=>数据库管理系统审计_统一审计追踪管理,
审核跟踪清除间隔=>12,
AUDIT_TRAIL_PURGE_NAME=>“审计跟踪_PJ”,
使用最后一个时间戳=>TRUE,
容器=>数据库管理系统审计_管理容器电流);
Quiz
Top-level statements performed before the database opens by administrative users such as SYS and SYSDBA are mandatorily audited.
测验
SYS和SYSDBA等管理用户在打开数据库之前执行的顶级语句将被强制审核。 对的



 浙公网安备 33010602011771号
浙公网安备 33010602011771号