Linux8.2 网络管理
查看网络状态
Linux系统作为服务器,会运行许多服务,并且与客户端进行相互通信,要有对外通信和监听端口。netstat工具就是查看Tcp/ip通信状态。通常情况下,
查看监听端口和sockets。加上t选项可以只查看tcp/ip端口。
同一台服务器两个进程之间通信使用sockets文件
#查看监听端口 [root@chyuanliuNJ ~]# netstat -lnp Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 2901/httpd tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 3233/sshd tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN 2901/httpd tcp 0 0 127.0.0.1:15772 0.0.0.0:* LISTEN 1017/staragent-core tcp 0 0 127.0.0.1:32000 0.0.0.0:* LISTEN 1516/java tcp6 0 0 :::3306 :::* LISTEN 1861/mysqld udp 0 0 172.16.252.69:123 0.0.0.0:* 778/ntpd udp 0 0 127.0.0.1:123 0.0.0.0:* 778/ntpd udp 0 0 0.0.0.0:123 0.0.0.0:* 778/ntpd udp6 0 0 :::123 :::* 778/ntpd Active UNIX domain sockets (only servers) Proto RefCnt Flags Type State I-Node PID/Program name Path unix 2 [ ACC ] STREAM LISTENING 13806 1047/AliYunDun /tmp/Aegis-<Guid(5A2C30A2-A87D-490A-9281-6765EDAD7C BA)> unix 2 [ ACC ] STREAM LISTENING 13652 1018/staragent-ppf /home/staragent/data/ppf.sock unix 2 [ ACC ] STREAM LISTENING 13768 1017/staragent-core /home/staragent/data/core.sock unix 2 [ ACC ] STREAM LISTENING 11075 1/systemd /var/run/dbus/system_bus_socket unix 2 [ ACC ] STREAM LISTENING 15909 2891/php-fpm: maste /home/www/logs/php-fpm.sock unix 2 [ ACC ] STREAM LISTENING 9567 1/systemd /run/systemd/private unix 2 [ ACC ] STREAM LISTENING 15423 1861/mysqld /tmp/mysql.sock unix 2 [ ACC ] STREAM LISTENING 6802 1/systemd /run/systemd/journal/stdout unix 2 [ ACC ] SEQPACKET LISTENING 9623 1/systemd /run/udev/control unix 2 [ ACC ] STREAM LISTENING 13807 1047/AliYunDun /usr/local/aegis/Aegis-<Guid(5A2C30A2-A87D-490A-928 1-6765EDAD7CBA)>
查看网络链接状态
Netstat用于显示与IP、TCP、UDP和ICMP协议相关的统计数据,一般用于检验本机各端口的网络连接情况。 LISTEN:侦听来自远方的TCP端口的连接请求 链接状态 SYN-SENT:再发送连接请求后等待匹配的连接请求 SYN-RECEIVED:再收到和发送一个连接请求后等待对方对连接请求的确认 ESTABLISHED:代表一个打开的连接 FIN-WAIT-1:等待远程TCP连接中断请求,或先前的连接中断请求的确认 FIN-WAIT-2:从远程TCP等待连接中断请求 CLOSE-WAIT:等待从本地用户发来的连接中断请求 CLOSING:等待远程TCP对连接中断的确认 LAST-ACK:等待原来的发向远程TCP的连接中断请求的确认 TIME-WAIT:等待足够的时间以确保远程TCP接收到连接中断请求的确认 CLOSED:没有任何连接状态
[root@chyuanliuNJ ~]# netstat -an Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:15772 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:32000 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:32000 127.0.0.1:31000 ESTABLISHED tcp 0 0 127.0.0.1:31000 127.0.0.1:32000 ESTABLISHED tcp 0 0 172.16.252.69:37520 140.205.140.205:80 ESTABLISHED tcp 0 64 172.16.252.69:22 121.237.148.162:18497 ESTABLISHED tcp 0 0 172.16.252.69:35444 100.100.80.158:8000 ESTABLISHED tcp6 0 0 :::3306 :::* LISTEN udp 0 0 172.16.252.69:123 0.0.0.0:* udp 0 0 127.0.0.1:123 0.0.0.0:* udp 0 0 0.0.0.0:123 0.0.0.0:* udp6 0 0 :::123 :::* Active UNIX domain sockets (servers and established) Proto RefCnt Flags Type State I-Node Path unix 2 [ ACC ] STREAM LISTENING 13806 /tmp/Aegis-<Guid(5A2C30A2-A87D-490A-9281-6765EDAD7CBA)> ... ... [root@chyuanliuNJ ~]# netstat -ant Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:15772 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:32000 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:32000 127.0.0.1:31000 ESTABLISHED tcp 0 0 127.0.0.1:31000 127.0.0.1:32000 ESTABLISHED tcp 0 0 172.16.252.69:37520 140.205.140.205:80 ESTABLISHED tcp 0 64 172.16.252.69:22 121.237.148.162:18497 ESTABLISHED tcp 0 0 172.16.252.69:35444 100.100.80.158:8000 ESTABLISHED tcp6 0 0 :::3306 :::* LISTEN [root@chyuanliuNJ ~]# netstat -anu Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State udp 0 0 172.16.252.69:123 0.0.0.0:* udp 0 0 127.0.0.1:123 0.0.0.0:* udp 0 0 0.0.0.0:123 0.0.0.0:* udp6 0 0 :::123 :::*
查看各种状态个数,established是需要关注的状态,同一时间有多少客户端链接服务器保持通信,
[root@chyuanliuNJ ~]# netstat -an| awk '/^tcp/{++sta[$NF]}END{for(key in sta)print key,"\t",sta[key]}'
LISTEN 6
ESTABLISHED 5
ss -an与 netstat类似,但是不显示PID和进程名
[root@chyuanliuNJ ~]# ss -an |grep -i 'LISTEN' u_str LISTEN 0 5 /tmp/Aegis-<Guid(5A2C30A2-A87D-490A-9281-6765EDA D7CBA)> 13806 * 0 u_str LISTEN 0 100 /home/staragent/data/ppf.sock 13652 * 0 u_str LISTEN 0 30 /home/staragent/data/core.sock 13768 * 0 u_str LISTEN 0 128 /var/run/dbus/system_bus_socket 11075 * 0 u_str LISTEN 0 128 /home/www/logs/php-fpm.sock 15909 * 0 u_str LISTEN 0 128 /run/systemd/private 9567 * 0 u_str LISTEN 0 128 /tmp/mysql.sock 15423 * 0 u_str LISTEN 0 128 /run/systemd/journal/stdout 6802 * 0 u_seq LISTEN 0 128 /run/udev/control 9623 * 0 u_str LISTEN 0 5 /usr/local/aegis/Aegis-<Guid(5A2C30A2-A87D-490A- 9281-6765EDAD7CBA)> 13807 * 0 tcp LISTEN 0 128 *:80 *:* tcp LISTEN 0 128 *:22 *:* tcp LISTEN 0 128 *:443 *:* tcp LISTEN 0 10 127.0.0.1:15772 *:* tcp LISTEN 0 1 127.0.0.1:32000 *:* tcp LISTEN 0 128 :::3306 :::*
tcpdump抓包
遇到攻击,网卡流量异常,进入服务器包量大,查看进入包的信息。
#-nn显示IP而不是主机名, -i 可以指定网卡 [root@chyuanliuNJ ~]# tcpdump -nn tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 12:57:41.563268 IP 172.16.252.69.22 > 121.237.148.162.18497: Flags [P.], seq 3055059848:3055060056, ack 1056013360, win 260, length 208 12:57:41.563402 IP 172.16.252.69.22 > 121.237.148.162.18497: Flags [P.], seq 208:400, ack 1, win 260, length 192 12:57:41.563426 IP 172.16.252.69.22 > 121.237.148.162.18497: Flags [P.], seq 400:576, ack 1, win 260, length 176 12:57:41.563446 IP 172.16.252.69.22 > 121.237.148.162.18497: Flags [P.], seq 576:752, ack 1, win 260, length 176 ... ... #不加n则显示主机名 [root@chyuanliuNJ ~]# tcpdump tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 12:58:20.946549 IP chyuanliuNJ.ssh > 121.237.148.162.18497: Flags [P.], seq 3055071128:3055071336, ack 1056013744, win 260, length 208 12:58:20.946841 IP chyuanliuNJ.40461 > 100.100.2.138.domain: 4829+ PTR? 162.148.237.121.in-addr.arpa. (46) 12:58:20.946996 IP 100.100.2.138.domain > chyuanliuNJ.40461: 4829 NXDomain 0/1/0 (116) 12:58:20.947624 IP chyuanliuNJ.32948 > 100.100.2.136.domain: 20023+ PTR? 69.252.16.172.in-addr.arpa. (44) 12:58:20.947792 IP 100.100.2.136.domain > chyuanliuNJ.32948: 20023 NXDomain* 0/1/0 (98) 12:58:20.947884 IP chyuanliuNJ.44941 > 100.100.2.138.domain: 34442+ PTR? 138.2.100.100.in-addr.arpa. (44) 12:58:20.947910 IP chyuanliuNJ.ssh > 121.237.148.162.18497: Flags [P.], seq 208:400, ack 1, win 260, length 192 ... ...
查看数据流向,length长度,DDos -> udp flood攻击。
可以指定端口网卡host。
[root@chyuanliuNJ ~]# tcpdump -nn -i eth0 not port 22 and host chyuanliuNJ tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 15:21:22.901762 IP 172.16.252.69.58159 > 100.100.2.138.53: 9206+ A? chyuanliuNJ. (29) 15:21:22.901890 IP 100.100.2.138.53 > 172.16.252.69.58159: 9206 NXDomain 0/1/0 (104) 15:21:22.902214 IP 172.16.252.69.58225 > 100.100.2.138.53: 21512+ AAAA? chyuanliuNJ. (29) 15:21:22.902343 IP 100.100.2.138.53 > 172.16.252.69.58225: 21512 NXDomain 0/1/0 (104) 15:21:24.092005 IP 140.205.140.205.80 > 172.16.252.69.37520: Flags [P.], seq 3003656447:3003656457, ack 3246881788, win 65535, length 10 15:21:24.131218 IP 172.16.252.69.37520 > 140.205.140.205.80: Flags [.], ack 10, win 65280, length 0 15:21:24.166388 IP 172.16.252.69.37520 > 140.205.140.205.80: Flags [P.], seq 1:7, ack 10, win 65280, length 6 15:21:24.171532 IP 140.205.140.205.80 > 172.16.252.69.37520: Flags [.], ack 7, win 65535, length 0 ^C 8 packets captured 8 packets received by filter 0 packets dropped by kernel
指定包数量及保存到的文件
# 1.cap就是系统从网卡里捕获的数据包信息 [root@chyuanliuNJ ~]# tcpdump -nn -c 100 -w 1.cap tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes 100 packets captured 100 packets received by filter 0 packets dropped by kernel #用cat命令看不了,用read返回的还是数据流 [root@chyuanliuNJ ~]# tcpdump -r 1.cap reading from file 1.cap, link-type EN10MB (Ethernet) 16:21:46.609879 IP chyuanliuNJ.ssh > 121.237.148.162.51681: Flags [P.], seq 1118231845:1118231989, ack 3986578950, win 260, length 144 16:21:46.626063 IP 121.237.148.162.51681 > chyuanliuNJ.ssh: Flags [.], ack 144, win 251, length 0 16:21:47.898812 IP chyuanliuNJ.37520 > 140.205.140.205.http: Flags [.], seq 3247351066:3247355086, ack 3003657277, win 65280, length 4020 16:21:47.898826 IP chyuanliuNJ.37520 > 140.205.140.205.http: Flags [P.], seq 4020:7750, ack 1, win 65280, length 3730 ... ...
tshark
也可以用来抓包
[root@chyuanliuNJ ~]# yum install -y wireshark [root@chyuanliuNJ ~]# tshark -n -t a -R http.request -T fields -e "frame.time" -e "ip.src" -e "http.host" -e "http.request.method" -e "http.request.uri" tshark: -R without -2 is deprecated. For single-pass filtering use -Y. Running as user "root" and group "root". This could be dangerous. Capturing on 'eth0' "Nov 27, 2017 17:36:51.498389910 CST" 172.16.252.69 POST /agent/metrics/putLines "Nov 27, 2017 17:37:06.557838621 CST" 172.16.252.69 POST /agent/metrics/putLines "Nov 27, 2017 17:37:21.592079438 CST" 172.16.252.69 POST /agent/metrics/putLines "Nov 27, 2017 17:37:28.997146600 CST" 121.237.148.51 47.96.170.152 GET / "Nov 27, 2017 17:37:29.094248280 CST" 121.237.148.51 47.96.170.152 GET /favicon.ico "Nov 27, 2017 17:37:29.186289000 CST" 121.237.148.51 47.96.170.152 GET /favicon.ico "Nov 27, 2017 17:37:36.629509620 CST" 172.16.252.69 POST /agent/metrics/putLines "Nov 27, 2017 17:37:38.112915894 CST" 101.226.33.224 47.96.170.152 GET / ... ... #打印http协议流相关信息,查看指定网卡80端口的web访问情况,在提供web服务的前提下,类似web访问日志。记录时间、域名、访问IP、状态、访问的链接。
Linux网络相关
[root@chyuanliuNJ ~]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.16.252.69 netmask 255.255.255.0 broadcast 172.16.252.255
ether 00:16:3e:04:0d:4f txqueuelen 1000 (Ethernet)
RX packets 518 bytes 70981 (69.3 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 627 bytes 109992 (107.4 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1 (Local Loopback)
RX packets 60 bytes 7973 (7.7 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 60 bytes 7973 (7.7 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
#ifup 网卡 ifdown 网卡
# 启动网卡 关闭网卡
#设置虚拟网卡类似配置IP
#查看网线是否正确链接到网卡
如果mii-tool eth0不支持,用下面的
[root@chyuanliuNJ ~]# ethtool eth0
Settings for eth0:
Link detected: yes
#修改hostname,需要重启服务器才能显示,配置文件/etc/hostname
[root@chyuanliuNJ ~]# hostnamectl set-hostname chyuanliu
#DNS配置文件
[root@chyuanliuNJ ~]# cat /etc/resolv.conf
options timeout:2 attempts:3 rotate single-request-reopen
; generated by /usr/sbin/dhclient-script
nameserver 100.100.2.138
nameserver 100.100.2.136
#hosts文件,只在本机生效,支持一个IP配多个域名,空格分隔,最下面配置的优先级越高
[root@chyuanliuNJ ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
如果一台服务器需要设置多个ip,但又不想添加多块网卡,那就需要配置虚拟网卡。
[root@chy002 ~]# cd /etc/sysconfig/network-scripts/
[root@chy002 network-scripts]# cp ifcfg-eno16777736 ifcfg-eno16777736\:0
[root@chy002 network-scripts]# vi !$
... ...
NAME=eno16777736:0
ONBOOT=yes
IPADDR=192.168.212.138
NETMASK=255.255.255.0
#修改NAME IPADDR 删除DNS
[root@chy002 network-scripts]# ifdown eno16777736 && ifup eno16777736
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/1)
[root@chy002 network-scripts]# ifconfig
eno16777736: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.212.130 netmask 255.255.255.0 broadcast 192.168.212.255
inet6 fe80::20c:29ff:fe0e:39dc prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:0e:39:dc txqueuelen 1000 (Ethernet)
RX packets 267 bytes 28452 (27.7 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 260 bytes 37013 (36.1 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eno16777736:0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.212.138 netmask 255.255.255.0 broadcast 192.168.212.255
ether 00:0c:29:0e:39:dc txqueuelen 1000 (Ethernet)
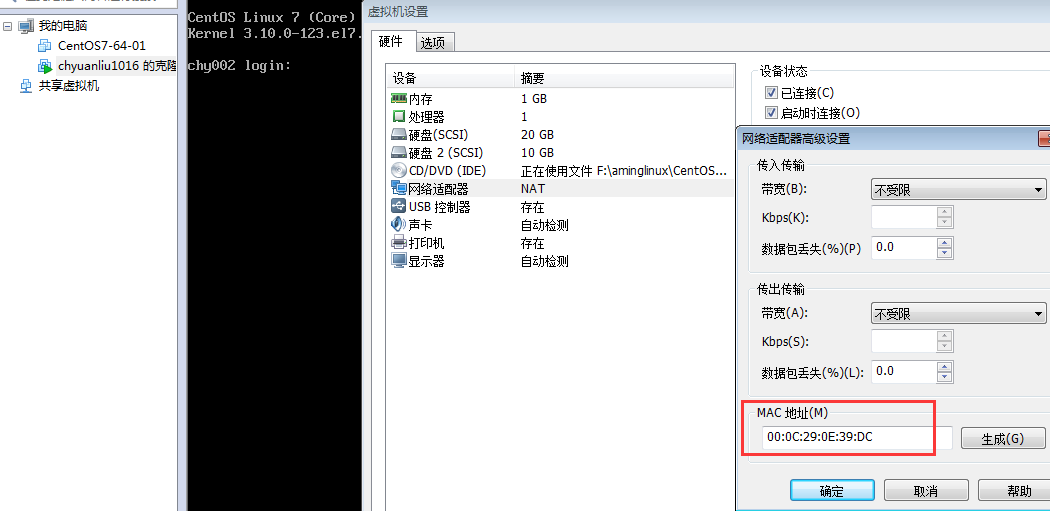
中间出现一个小问题,系统配置文件的HWADDR与vmware中配置的不一样,导致出现错误 eno16777736: unknown interface: No such device.
导致该网卡只能关闭,不能重启。把配置文件中的mac地址修改为vmware中网卡的硬件地址即可。