H3C V7防火墙ipsec配置-两端对等模式
H3C V7防火墙ipsec配置
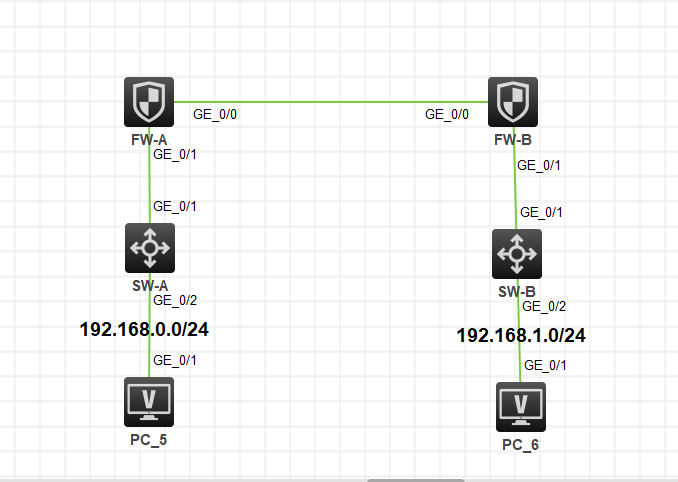
拓扑图
简单示意图。
两端固定ip配置
FW-A配置:
# 配置acl本段内网地址192.168.0.0/24,对端为192.168.1.0/24
# acl 3000用于nat过滤,拒绝感兴趣流量
acl advanced 3000
rule 5 deny ip soure 192.168.0.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 10 permit ip
# acl 3001 匹配感兴趣流量
acl advanced 3000
rule 5 permit ip soure 192.168.0.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
IKE 阶段
# 1.创建ike keychain,作为与对端的认证,地址为对端地址,协商密码需要两端一致
ike keychain CJ
pre-shared-key address 218.17.21.25 255.255.255.255 key simple 12345678
# 2.创建ike proposal 设置加解密类型
ike proposal 1
encryption-algorithm 3des-cbc
authentication-algorithm md5
# 3.创建ike profile,与对端协商,将前面的keychain 和proposal,以及配置本段地址和对端地址进行调用
ike profile CJ
keychain CJ
local-identity address 183.62.141.212
match remote identity address 218.17.21.25 255.255.255.255
match local address GigabitEthernet1/0/0
proposal 1
IPSEC 阶段:
# 配置transform 加解密
ipsec transform-set JT
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
# 配置ipsec策略,策略名称ipsec-cj ,1代表第一条策略,调用transform和acl,配置两端地址,再调用第一阶段ike-profile
ipsec policy ipsec-cj 1 isakmp
transform-set JT
security acl 3001
local-address 183.62.141.242
remote-address 218.17.21.2
description TO_CJ
ike-profile CJ
在接口调用策略和nat
interface GigabitEthernet1/0/0
ip address 183.62.141.212 255.255.255.252
ipsec apply policy ipsec-cj
nat outbound 3000
FW-B配置:
两端配置是相对的。
# 配置acl本段内网地址192.168.1.0/24,对端为192.168.0.0/24
# acl 3000用于nat过滤,拒绝感兴趣流量
acl advanced 3000
rule 5 deny ip soure 192.168.1.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
rule 10 permit ip
# acl 3001 匹配感兴趣流量
acl advanced 3000
rule 5 permit ip soure 192.168.1.0 0.0.0.255 destination 192.168.0.0 0.0.0.255
IKE 阶段
# 1.创建ike keychain,作为与对端的认证,地址为对端地址,协商密码需要两端一致
ike keychain JT
pre-shared-key address 183.62.141.212 255.255.255.255 key simple 12345678
# 2.创建ike proposal 设置加解密类型
ike proposal 1
encryption-algorithm 3des-cbc
authentication-algorithm md5
# 3.创建ike profile,与对端协商,将前面的keychain 和proposal,以及配置本段地址和对端地址进行调用
ike profile JT
keychain JT
local-identity address 218.17.21.25
match remote identity address 183.62.141.212 255.255.255.255
match local address GigabitEthernet1/0/0
proposal 1
IPSEC 阶段:
# 配置transform 加解密
ipsec transform-set CJ
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
# 配置ipsec策略,策略名称ipsec-jt ,1代表第一条策略,调用transform和acl,配置两端地址,再调用第一阶段ike-profile
ipsec policy ipsec-jt 1 isakmp
transform-set JT
security acl 3001
local-address 218.17.21.25
remote-address 183.62.141.212
description TO_JT
ike-profile JT
在接口调用策略和nat
interface GigabitEthernet1/0/0
ip address 218.17.21.25 255.255.255.252
ipsec apply policy ipsec-jt
nat outbound 3000
最后在两端内网终端ping测试对端终端。
查询ike、ipsec信息传输
# 查询sa建立情况
dis ike sa
# 查询sa流量
dis ike sa verbpse
# 查询ipsec阶段信息
dis ipsec policy
点点滴滴,积少成多,终有一日能发挥用处。


 H3C V7防火墙ipsec配置-两端对等模式
H3C V7防火墙ipsec配置-两端对等模式

 浙公网安备 33010602011771号
浙公网安备 33010602011771号